Three years after a debate on the security of AirPods was ignited by the media reporting that United States Vice President Kamala Harris was “Bluetooth-phobic,” the story has come full circle.
The claims that cybercriminals could hack into Bluetooth environments, listen to conversations, and meddle with iPhones have turned out to be true. Apple recently released a security update that prevents hackers from spoofing your AirPods.
Apple AirPods vulnerability affects millions of users
On June 25, Apple released security firmware updates for AirPods (2nd generation and later), AirPods Pro (all models), AirPods Max, Powerbeats Pro, and Beats Fit Pro.
The company explained how the exploit worked.
“When your headphones are seeking a connection request to one of your previously paired devices, an attacker in Bluetooth range might be able to spoof the intended source device and gain access to your headphones.”
The authentication vulnerability CVE-2024-27867 was discovered by security researcher Jonas Dreßler.
In a blog post, Dreßler said that “anyone who knows the Bluetooth MAC address (which is somewhat public) can connect to your AirPods and listen to the microphone or play music.”
The attacker can even connect while victims are using their AirPods.

How a security researcher “stumbled” upon the AirPods vulnerability
Security researcher Jonas Dreßler wasn’t hunting for vulnerabilities when he discovered this one. After buying a pair of AirPods, setting them up, and testing them using a Mac and iOS, Dreßler decided to switch his OS to Linux. That was when he realized that while the AirPods worked with Linux, they would not connect to two devices at the same time.
Thinking that naturally, this was a Bluetooth pairing handshake problem, Dreßler took a look into several special Apple-specific protocols. That’s when he stumbled upon the vulnerability.
Apple’s Fast Connect feature is at the center of problems
The AirPods vulnerability is found in the AirPods “Fast Connect” feature. Fast Connect, a protocol patented by Apple in 2019, is designed to reduce the time it takes for Bluetooth connections between two Apple devices. While most Bluetooth connections can take an average of 10 to 15 seconds to connect a new device, Fast Connect does the same in one second or faster.
Normally, connecting Bluetooth devices takes a bit of time because there are restrictions on what information they can share initially. This is a good thing, as it helps keep your devices secure. But Apple wanted to speed things up for their devices, particularly AirPods.
Fast Connect “sneaks” extra information into regular Bluetooth messages that act like a check for connection (L2CAP pings). Think of it like sending a quick hello, but Apple hides some details about Fast Connect (their special way to connect quicker) within that hello message.
By exchanging these special pings, both devices can instantly confirm two things: they both speak the “Fast Connect language,” and they have the necessary details for a full connection (which they exchange in just three more messages).
Once this initial handshake is done, the devices can use the standard Bluetooth pairing process, but because they have already exchanged the Fast Connect information, the whole connection happens much faster.
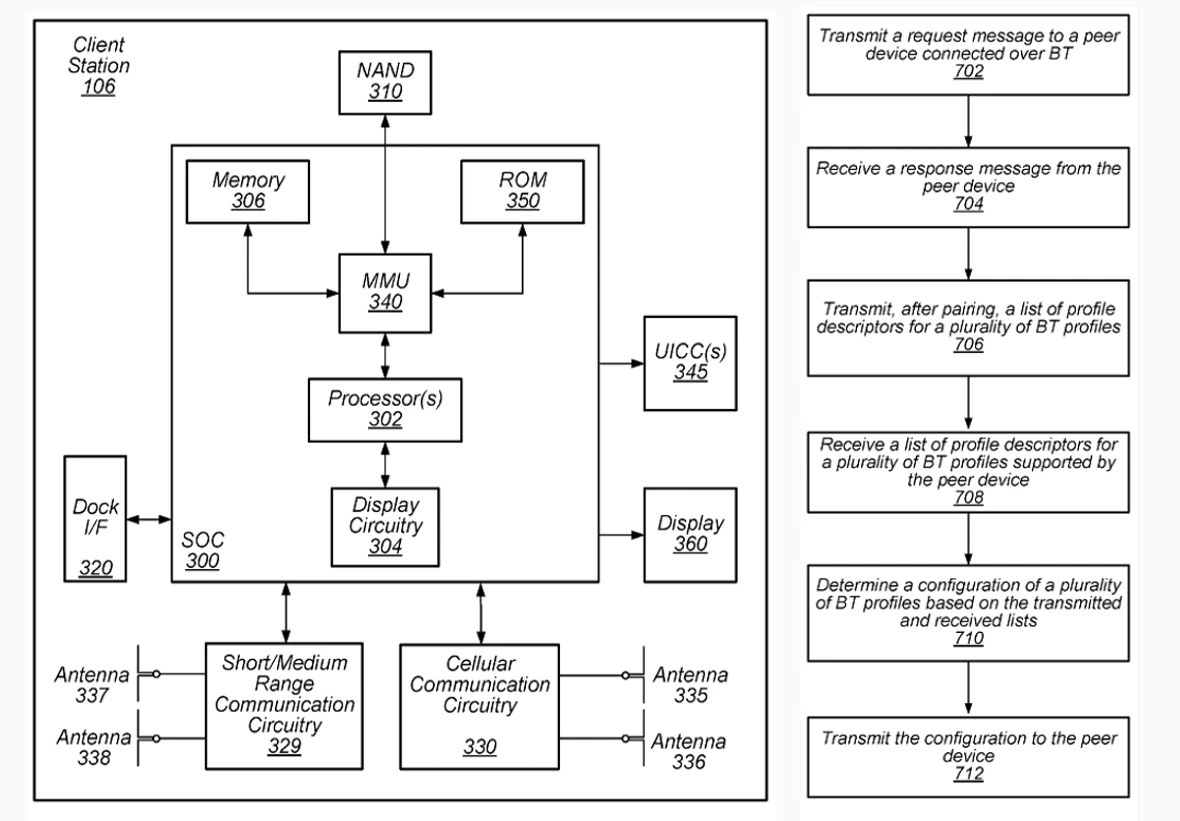
“The fact that this only takes 4 messages back-and-forth in total is what makes Fast Connect fancy, because usually in Bluetooth, the phase of wiring up the individual channels for a connection is quite a complex negotiation and involves sending various SDP descriptors that describe which protocols/features both sides support,” Dreßler wrote in his blog post.
Apple “forgot basic security code checks,” researcher says
According to Dreßler, Apple “forgot” to run some basic code security checks in the process of prioritizing Bluetooth connectivity speed.
“Authentication and enabling encryption is a step that is supposed to happen after the initial Fast Connect message,” Dreßler said.
While iOS and macOS authenticate and enable encryption without a problem, if an attacker decides to skip that step when connecting, the AirPods will happily continue on with the Fast Connect.
The only thing an attacker would need to breach your AirPods exploiting this vulnerability is to know your fixed Bluetooth MAC address.
“This address is not exactly private information,” Dreßler wrote. “It’s advertised on the air when your Bluetooth device is in pairing mode, and it can be easily obtained on the air while the AirPods are active using hardware like the Ubertooth One.”
Exploiting AirPods: Potential consequences go beyond eavesdropping
You might think that breaching a pair of AirPods doesn’t leave much space for an attacker to do damage. But it turns out that hacking Apple’s Bluetooth can have nasty consequences for victims.
An attacker that connects using this technique could do the following:
- Eavesdrop on conversations: By connecting to your AirPods, the attacker could listen in on any conversations you’re having through the microphone. This is a serious privacy concern, especially if you use your AirPods for calls or meetings.
- Disrupt audio: The attacker could play music or other sounds through your AirPods, interrupting your listening experience or potentially masking their own actions.
- Limited control: In some cases, the attacker might be able to see and pause the music currently playing from another connected device (like your phone).
- Mess with settings: The vulnerability might allow the attacker to change some settings on your AirPods, though the extent of this control is unclear.
- Potentially crash AirPods: By sending corrupted messages, the attacker could attempt to crash your AirPods, rendering them temporarily unusable.
- Social engineering: An attacker with access to your AirPods (through the vulnerability) could listen to conversations and potentially use that information for social engineering attacks. They might trick you into downloading malware or clicking on malicious links on your phone.
What should users do to secure their AirPods?
Fortunately, the fix for this vulnerability is easy. Apple’s latest security update fixes the vulnerability. So, Apple’s automatic over-the-air update will do the trick.
AirPods update automatically while charging within Bluetooth range of your iPhone, iPad, or Mac as long as they are connected to Wi-Fi. However, it is also a good idea to check if your AirPods have the latest security update. You can do this using your iPhone, iPad, or Mac.
To use your iPhone or iPad to check your AirPods update status, go to Settings, navigate to Bluetooth, and then tap the Info button next to the name of your AirPods. Scroll down to the About section to find the firmware version.
To check your AirPods security updates using your Mac, press and hold the Option key while choosing the Apple menu and then System Information. Then tap the info button next to your headphones.
Those who use AirPods and do not have their Apple device nearby or use AirPods but run Windows, Linux, Android, or other non-Apple OS will be more challenged, as these setups do not support Apple’s over-the-air updates. The only solution if you happen to fall in this group of AirPods users is to physically take your AirPods to the nearest Apple Store and ask them to update your firmware.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. AirPods is a trademark of Apple Inc.