Last month, we reported that Apple had sent warnings to hundreds of users, informing them that they were being targeted by spyware. At the time, Apple did not reveal any information on what exactly was happening. Through investigations and breaking news, we found out European journalists were being targeted by mercenary spyware.
Now, with Apple releasing a new security update, we have an even clearer picture of what happened and how a vulnerability allowed threat actors to distribute spyware among European journalists.
In this report, we look at the forensic side of the issue, how this cyberattack works, the Apple flaws it leverages, and how understanding the chain of attack can help users stay more protected.
Apple patches up “mercenary” malware vulnerability linked to European journalists spyware hack
On June 16, the National Vulnerability Database listed the vulnerability CVE-2025-43200 on its public listings. The vulnerability shows up as “addressed and improved with checks.” This means Apple fixed it or made a specific patch.
This vulnerability was used by an unknown threat actor to deploy spyware against European journalists. The spyware used was Paragon’s Graphite, which governments use for national security operations and which bad actors often abuse.
The vulnerability affected a wide range of Apple devices, including Apple Watches, Macs, iPhones, and iPads. So, download the latest updates for those if you have them.
A video, a zero-click attack, and your iPhone: Understand the domino effect that leaves you vulnerable
Like most spyware cyberattacks or intrusions, this was a zero-click attack. This means that the victim does not need to take any action for the attack to succeed. No downloading of files, no clicking on links, nothing.
In this case, the zero-click chain works when the victim receives a video from a user who has an iCloud account. The user doesn’t even have to play the video or interact with it in any way for the spyware to breach their iPhone.
How is this possible? That is exactly what we are going to answer.
Apple never gives out detailed technical information on security patches to avoid disclosing more information than necessary about proprietary cybersecurity technology. The company described this vulnerability as a “logic issue” and summarized the exploit in a single sentence.
“A logic issue existed when processing a maliciously crafted photo or video shared via an iCloud Link,” Apple said in a security update release.
This is enough for us to explain how this spyware attack works.
What is a logic process in Apple devices?
So, what is a logic process? Each time you receive a video from a user, you can think of it as getting a box of LEGO pieces. The box contains pieces of the end product, along with labels and instructions on how to put it together.
Similarly, videos are sent as “boxes of data,” coded and labeled for any device to parse the data using a “logic process.” This happens on your computer, on your smartphone, and on other devices.
Now, here’s where things get interesting. Spyware makers, which Apple describes as “sophisticated and advanced” malware developers, have found ways to abuse these “logic processes” to trigger malicious actions.
While we do not know the exact “logic process” that Apple devices use for parsing — a term that describes the process where software reads, analyzes, and interprets structured data (like a video or photo file) to understand its contents and how to handle them — we can assume that it does the following:
- Extracting data packets or frames: The video data is broken down into smaller pieces or frames, which need to be processed in order.
- Decoding each frame: The device uses the appropriate codec to decode (uncompress) each video frame from its encoded form.
- Checking for errors or anomalies: The parsing logic verifies the integrity and structure of the data to avoid corruption or malformed input.
- Reassembling frames into a continuous stream: The frames are put back together in the correct sequence to recreate the video for playback.
- Rendering the video: Finally, the decoded frames are displayed on the screen, synchronized with audio if present.
From parsing to logic errors to buffer overflows
The process of parsing is fully automated and happens on your device each time you get a video, an image, or another file type. The problem with parsing is that black hat hackers can trick devices by creating parsing instructions that lead to problems like buffer overflow.
Buffer overflow is a technique used by cybercriminals to “overflow” the limit of memory that the parsing instructions have assigned to a specific process, such as processing a video you have received. When this overflow happens, attackers can gain access to your device’s memory and resources.
Think of buffer overflow as emptying a gallon of water into a glass that’s too small to hold it. The data and memory are the water, and the glass is your iPhone.
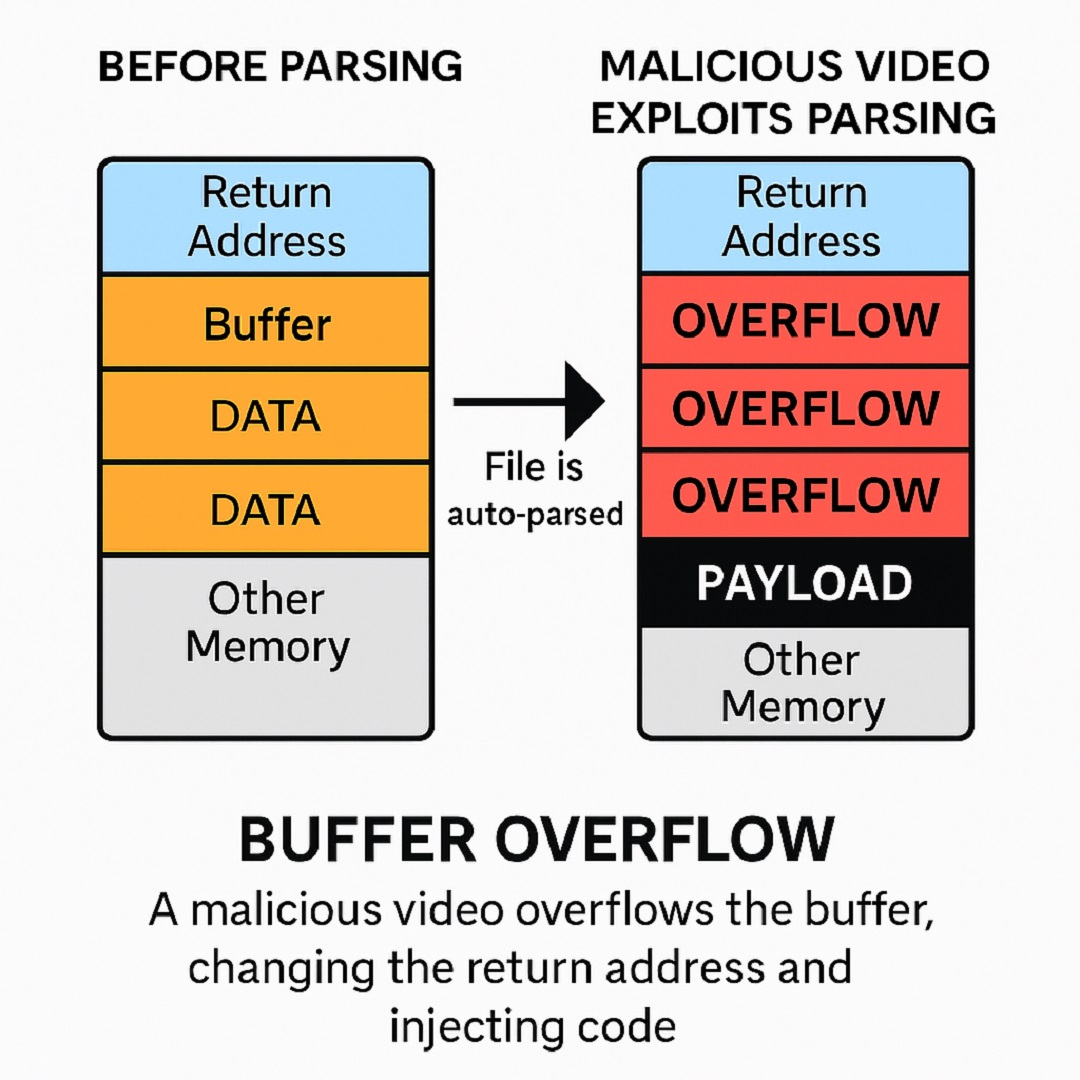
By precisely controlling what spills over, attackers can overwrite parts of memory and hijack a program’s behavior, for example, making it run malware instead of returning to the home screen.
Paragon’s Graphite spyware techniques exposed
Based on the information available online and what we explained above, we can conclude that the European journalists, targeted by an unknown actor with Paragon’s Graphite spyware, received a cleverly malicious video or photo that caused a buffer overflow by abusing Apple’s parsing logic process.
Interestingly, the threat actor used an iCloud account to send these videos or images. While we cannot confirm it, we assume that the process of using iCloud accounts to send videos does not have the same security guardrails as when videos are sent from users who do not have iCloud. This is likely the reason why the threat actor used an iCloud account.
Some vulnerabilities in Apple’s logic issue may include that the OS assumes a file is safe because it comes from iCloud and, therefore, skips deep checks. Or it may allow the OS to process a video without checking for hidden scripts or malformed metadata. Or it could fail to verify file size limits or frame headers properly.
From top-level users to average folks: What can you do to improve your spyware security?
As stated above, we do not know exactly what Apple’s parsing logic is because, for good reasons, these remain “secret.” What we do know is that Apple has already fixed this particular problem. There are other types of file parsing bugs and exploits, but we won’t go into these in this article.
You may be thinking, “Great, but how can I stay safe if, just by receiving a video, my device can be infected?” That is a very good question. Let’s answer it.
Actions any user can take to increase their security against spyware include:
- Update your devices now: This one is simple. If you have an iPhone, iPad, Apple Watch, or Mac, install the latest update. This patch fixes the flaw used in this attack.
- Turn off automatic link previews: Go to Settings > Messages > Shared with You and disable auto-sharing features. These might fetch media silently in the background.
- Review what apps have access to your media: Limit which apps can access your photos, videos, and messages. Go to Settings > Privacy & Security > Photos.
- Limit iCloud link usage: Be careful when sharing or receiving media via iCloud links, especially from unknown senders. If you don’t recognize the source, don’t open the media.
- Use Lockdown Mode if you’re at risk: Apple’s Lockdown Mode (available under Settings > Privacy & Security > Lockdown Mode) disables many features that spyware relies on — perfect for journalists or activists.
You can learn more about the geopolitical issues involved with this specific spyware at the Citizen Lab, read up on how this spyware targeted an Italian journalist, or learn more about the spyware global market in our report.
Final thoughts
As you can see, attackers who abuse parsing can launch dangerous attacks. And while these incidents are described by the industry as “the most advanced cybersecurity threats,” the mechanisms they leverage aren’t tricky to understand.
By raising awareness about how threat actors manage to bypass Apple security guardrails, your chances of avoiding this type of cyber intrusion or detecting it while it is happening increase significantly.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. MacBook, iPhone, Apple Watch, and iPad are trademarks of Apple Inc.






