Apple has issued new security updates for iOS, macOS, Safari, and Vision Pro. And unlike most security updates released this year by the company, these 2 vulnerabilities were likely being utilized in cyberattacks against Apple users.
Apple patches up zero-day malicious web content and injection exploits
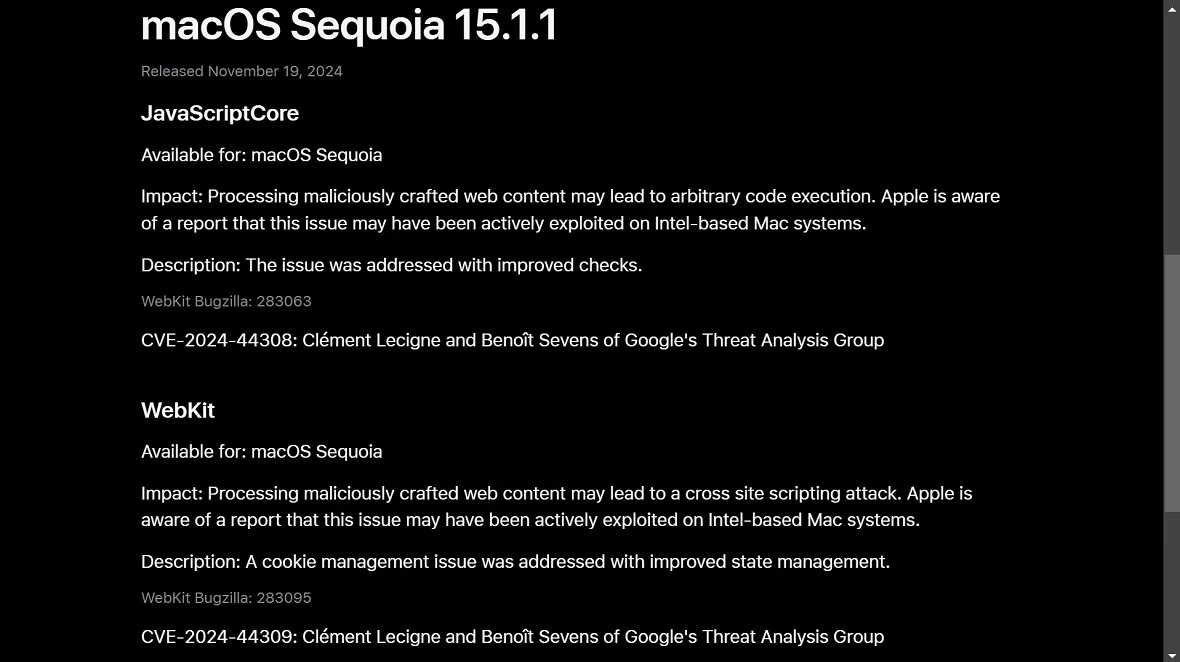
On November 19, Apple released updates to patch 2 vulnerabilities identified as CVE-2024-44308 and CVE-2024-44309. Both vulnerabilities were discovered by Clément Lecigne and Benoît Sevens of Google’s Threat Analysis Group, experts who work on nation-state threats.
Apple called for users to update their devices urgently, as the CVEs impacted iPhones, iPads, Macs, Vision Pro, and the Safari Web browser.
Apple does not release official details on the vulnerabilities they patch due to obvious security reasons. Therefore, it is unknown exactly who was exploiting these weaknesses or how.
Apple says that vulnerabilities have been addressed “with better checks and improved state management.” The only thing users have to do is make sure to update their devices immediately.
The patched bugs are considered zero-day vulnerabilities that were unknown to Apple. Researchers from the Google Threat Analysis Group disclosed the CVEs to Apple, who said these “may have been actively exploited on Intel-based Mac systems.”
As mentioned, it is unknown what type of cyberattacks used these zero-day vulnerabilities. However, given that the researchers who identified the bugs focus on nation-state-supported cyberattacks, spyware could have been involved.
A look into Apple’s zero-day CVE-2024-44308 and CVE-2024-44309 vulnerabilities
All Apple devices mentioned in this report are affected by the same 2 CVEs. In the section below, you can find the links to update each device. If you have not updated yours yet, we recommend you do so now.
CVE-2024-44308 is a vulnerability linked to malicious website content. By leveraging this vulnerability, attackers can breach an Apple device through maliciously crafted web content that triggers arbitrary code execution.
Apple said it was aware of reports that this issue may have already been actively exploited on Intel-based Mac systems.
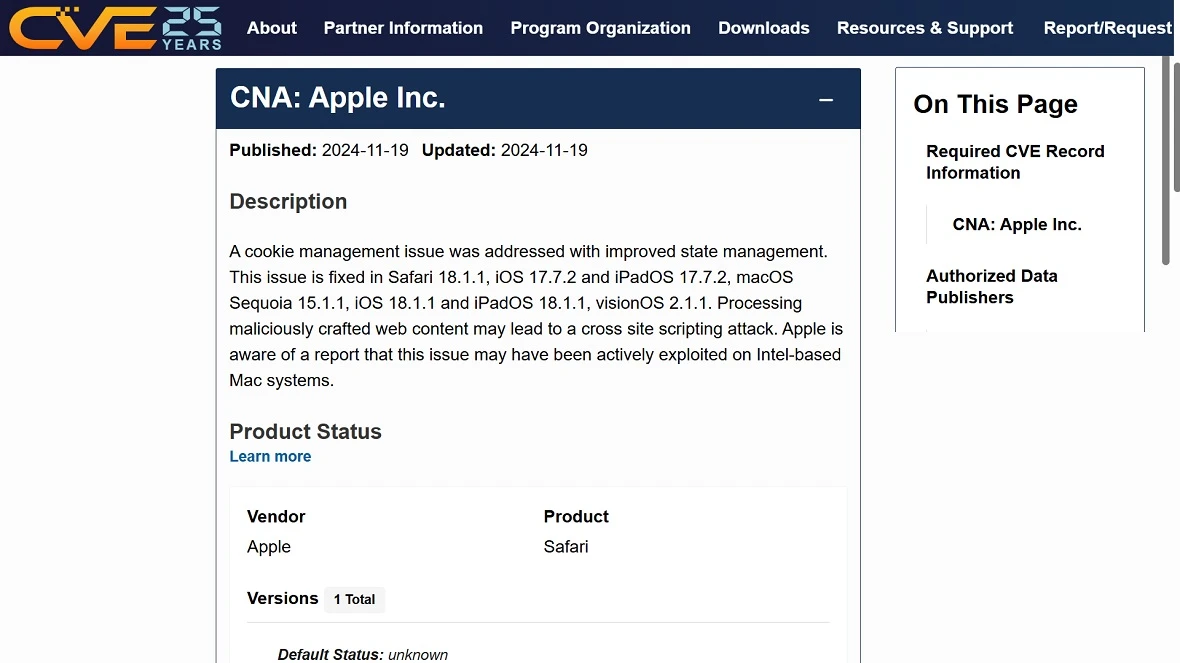
CVE-2024-44309 is also a vulnerability linked to malicious online web content. But, in this specific case, the vulnerability is not used to run arbitrary code but to execute a cross-scripting cyberattack. Apple says they have evidence that this technique may have already been exploited by threat actors.
Apple describes the fix as “a cookie management issue,” which was “addressed with improved state management.”
Protect yourself against malicious web content, arbitrary code, and cross-scripting attacks
Arbitrary code execution attacks usually use flaws in database languages to run malicious code. These cyberattacks can corrupt files, affect OSs, wipe out drives, and help cybercriminals load malware onto systems.
Besides infected malicious websites, malicious code can be spread through email attachments and by downloading files.
Cross-site scripting, also called XSS, is a security vulnerability that allows an attacker to inject malicious scripts into web pages viewed by clients. These attacks happen when an attacker uses a web application to send malicious code, generally in the form of a browser-side script.
Targeting legit websites and infecting them with malicious code or content — or creating new domains with malicious code — is not an uncommon technique among cybercriminals. From phishing to malware distribution or scam sites, web-driven attacks are a common practice in the underground criminal industry.
Using these techniques, attackers can:
- Steal sensitive data
- Deface websites
- Launch further attacks
- Steal user information
- Capture cookies and session tokens
- Redirect users to malicious websites
The difference between arbitrary code execution and XSS attacks is that XXS targets the users’ web browser or application itself, while arbitrary code execution allows the attacker to run code on the server.
To protect data and devices from malicious online content attacks, users should keep their OS, software, and apps updated, use a trusted and updated web browser, be cautious online, and always double-check URLs.
Update your Apple devices today
We recommend that users update their iPhones, Macs (if running on Sequoia), iPads, Safari, and Vision Pro.
Here’s a list of the specific device models that should be updated:
- iOS 18.1.1 and iPadOS 18.1.1: iPhone XS and later, iPad Pro 13-inch, iPad Pro 12.9-inch 3rd generation and later, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 7th generation and later, and iPad mini 5th generation and later
- iOS 17.7.2 and iPadOS 17.7.2: iPhone XS and later, iPad Pro 13-inch, iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later
- macOS Sequoia 15.1.1: Macs running macOS Sequoia
- visionOS 2.1.1: Apple Vision Pro
- Safari 18.1.1: Macs running macOS Ventura and macOS Sonoma
Final thoughts
Malicious web content, as mentioned, has always been a major cybersecurity threat. However, in the past years, cybercriminal infrastructure seems to have expanded to new levels, with hundreds of thousands of domains today identified in different attack campaigns.
Most fake and malicious sites push malware and drive phishing through impersonation or by creating attractive fake brands that leverage trending tech hype, such as AI. However, direct arbitrary code and cross-scripting techniques prove just how dangerous website-driven attacks have become.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iOS, macOS, Safari, and Vision Pro are trademarks of Apple Inc.






