Recently, Anthropic, the AI company behind Claude, released a report claiming that Chinese nation-state hackers had used its model to automate most of a large-scale cyberespionage attack. While some cybersecurity researchers met the report with skepticism, the news of what would be the “first fully AI-driven cyberattack” attracted the attention of the global tech press.
In this report, we look into Anthropic’s report, break down why some researchers cast doubt on the AI company’s disclosure, and, more importantly, why this news matters for Apple and Mac users.
A closer look at the Anthropic AI-agent cyberattack
On November 13, Anthropic released a report claiming they had disrupted the first-ever reported AI-orchestrated cyber espionage campaign. According to the report, a new Chinese nation-state threat group, dubbed GTG-1002 by the AI company, targeted 30 companies, including large tech companies, financial institutions, chemical manufacturing companies, and government agencies.
Anthropic said that the group used Claude Code as an AI agent. Claude Code is an AI that developers download onto terminals to customize AI projects they are building. One notable characteristic of Claude Code is that it can connect to a wide range of software and apps, usually through the Model Context Protocol or MCP.

Using this feature, Anthropic claims that the black hat hackers connected Claude Code to different open-source tools that cybersecurity researchers (and cybercriminals) use to protect or launch attacks.
These tools have web capabilities and range from digital attack surface scanners to vulnerability scanners and exploitation tools used by penetration testers and ethical hackers.
Protect your Mac from AI-powered cyberattacks
How did the attack work?
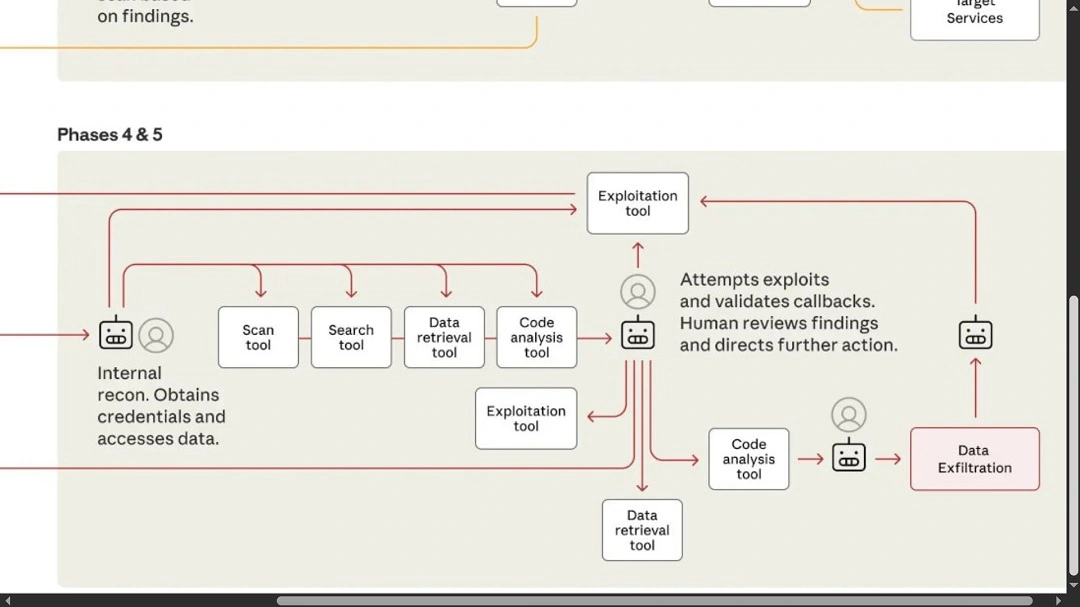
Assuming the Anthropic claims are accurate, this cyberattack worked in stages:
- Stage 1: The nation-state hackers gave Claude a set of carefully redacted prompts and instructions that allowed full automation and fooled the model’s abuse security guardrails.
- Step 2: Using open-source cybersecurity tools, Claude ran a digital attack surface scan on 30 different organizations and companies simultaneously. A digital attack surface scan is basically mapping out all the publicly facing digital resources a company has. This includes websites, networks, endpoints, servers, and other resources.
- Step 3: Following the attackers’ instructions, Claude began a vulnerability scan. Vulnerability scanners are pieces of software that allow cybersecurity researchers to search for known vulnerabilities using databases of vulnerabilities and cross-reference them with the inventory of the digital attack surface of a company. At this point, Claude was looking for a way into the non-public-facing digital infrastructure of a company, where valuable and sensitive data is stored. Claude finished this step by presenting the human operator(s) with a list of possible vulnerabilities that it could exploit.
- Step 4: After being given the go-ahead by human operators, Claude continued the cyberattack, this time leveraging or generating automated exploitation tools. This means it actually began exploiting the weakness it had identified to breach the systems. Anthropic did not reveal exactly what vulnerabilities the model exploited.
- Step 5: According to the report, Claude successfully breached several organizations and, at this stage, began searching for valuable information inside company systems. It then catalogued and presented the most valuable data it found to the human operator(s).
Inhuman attack speed
Anthropic claimed that most of the heavy lifting in this cyberattack, about 80 to 90% of it, was done by the AI acting as an agent without human intervention.
The company also claimed that in this cyberattack, Claude “made thousands of requests, often multiple per second — an attack speed that would have been, for human hackers, simply impossible to match.”
Besides reassuring its users and the public that they had taken mitigation actions, including banning threat actor accounts identified and notifying appropriate entities and authorities, the company said Claude was not always perfect during the attack. At times, the AI hallucinated credentials or claimed to have extracted secret information that was, in fact, publicly available.
Why security researchers aren’t buying into Anthropic’s claims
There are several elements that cybersecurity researchers and companies tend to disclose in their reports about cyber threats. These include indicators of compromise (IoC) such as websites, malware hashes, attackers’ IP addresses, domains, C2 attacker-controlled server data, and attribution details. The Antrophic report has none of those.
Additionally, threat reports, especially those that reveal large-scale cyber espionage operations conducted by nation-state hackers, also include digital forensic data. This means screenshots or analysis of the code used in the cyberattack. The Anthropic report has not a single line of code, nor prompts or any similar details.
The report spans just 14 pages, with absolutely none of the data or information that usually accompanies these types of cybersecurity reports. And another curious detail emerges — the alleged Chinese threat group behind this cyberattack.
There are numerous threat groups linked to the People’s Republic of China (PRC). These have been widely documented by US authorities and authorities in other countries, and they include groups like APT 41, APT 10, and Volt Typhoon, the latter of which targeted US mobile networks and critical infrastructure.
These nation-state groups are known for running sophisticated cyber espionage campaigns. However, Anthropic claims that a new group, which they called GTG-1002, is behind this new AI agent attack. Given that Chinese nation-state threat groups are well-structured and connected to the government, the rise to fame of a new and unknown group is rare.
These factors, compounded by the limited capabilities of AI Agents today — which are reported to fail 70% of the time, making more mistakes than getting things right — are some of the reasons why cybersecurity researchers such as Ali Alkhatib, Kevin Beaumont, and others believe the cyberattack did not happen.
Why does the AI cyberattack reported by Anthropic matter to Mac users?
While security researchers doubt that this cyberattack actually happened, Anthropic presents in its report a valid infrastructure thesis on how bad actors could use AI for live cyber attacks in the near future.
Connecting an AI Agent to open-source tools that ethical hackers, penetration testers, and others in the security community use to research, find, and exploit vulnerabilities is what hackers do manually. Automating these tasks using an AI agent is realistic in theory.
Given this information, if the first fully AI-driven cyberattack were ever to happen, it would likely take this form and not the malware intrusion path.
For Apple and Mac users, this news is a red flag showing how AI in cybercrime advances. As mentioned, cybercriminals are using AI more every day to accelerate and enhance their attacks. It is a matter of when, not if, these types of AI-agent cyberattacks are developed by bad actors who are financially driven and then target the general population and Mac users.
AI in cybercrime may be inevitable. However, Mac users can take action by informing themselves on how AI works and how cybercriminals are using it. They can also engage with tech companies and AI companies, express their concerns, and ask them to install policies and mitigation technologies that protect the end user.
Additionally, while local and federal governments actively play catch-up with AI security laws, Mac users can become actively engaged, raise awareness on the issue, or put pressure on their legislators to take action and enact AI protection laws.
Final thoughts
While Anthropic’s report reads more like a conceptual cyberattack than a real one, Mac users must understand that, unfortunately, AI is already in play and is used in live attacks targeting their computers. And more AI cyberattacks are guaranteed to occur soon. Staying informed and practicing safe online habits can help Mac users take ownership and control of their digital lives.







