Educating yourself on various types of online threats can help keep you and your information safe. One type of online attack is credential stuffing, a method that threatens your online accounts and login credentials. Keep reading to learn all about credential stuffing, how it works, and how to detect and prevent it.
What is credential stuffing?
The credential stuffing definition, according to the Open Worldwide Application Security Project (OWASP), is as follows: “Credential stuffing is the automated injection of stolen username and password pairs (‘credentials’) into website login forms, in order to fraudulently gain access to user accounts.”
With credential stuffing, a hacker uses a victim’s known credentials (username/password combo) from one account to attempt to gain access to other accounts.
The unfortunate truth is that many user credentials have been stolen and leaked on the dark web. Some of this data may seem almost harmless. However, since many people use the same username and password combinations for multiple platforms, cybercriminals can use stolen credentials to gain unauthorized access to other accounts. Simply put, if you use the same password on multiple websites, your accounts are vulnerable.
Shield your passwords from malware
The difference between credential stuffing and brute-force attacks
In a brute-force attack, a bad actor uses sophisticated software to quickly input thousands of username/password combinations to try to break into an account. They use commonly used passwords, words taken from the dictionary, and other methods to attempt to find the right combination to breach an account.
In a credential stuffing attack, however, threat actors already possess your login information from at least one account. They then attempt to use those known credentials to gain access to other services, hoping to get lucky. In many cases, it works.

Understanding the process of credential stuffing attacks
Comparatively, credential stuffing has a very low success rate. That said, it is an easy, low-risk method of theft, so hackers still use it. If an attacker possesses a username/password combination that works on, say, a Netflix account, they can run that data through software that will input the same login information into financial institution login pages and other services, hoping to get in. Usually, only one in a thousand succeed. But because cybercriminals may use billions of stolen credentials at a time, they can still net 1,000 new accounts.
Once hackers have access to your other accounts, they log in and change the password, locking you out. If possible, they access private data like credit card numbers, or they drain money from your bank.
How to detect credential stuffing
Do you suspect that someone has been tampering with your accounts? Use the signs below to verify if your accounts are safe or if they’re being controlled by someone else.
1. You are locked out of your account
You use your regular login information and cannot get into your accounts. So, you try to initiate a password reset, but you never get the reset email. In this case, an attacker has probably accessed your account, changed your credentials, and switched the email account to their own.
2. Your logs show multiple failed login attempts
If you check your logs and see multiple failed logins for any of your accounts, it may indicate that someone is trying to break in.
3. You receive a bunch of password reset emails
If you receive password reset emails from one or more of your accounts that you didn’t initiate yourself, someone could have access to your accounts and is trying to change the passwords to lock you out. Immediately reset your password to stop the hacker from getting in.
4. Suspicious activity on your account
If you log in to your credit card or bank account and see suspicious transactions, someone could have access to your login credentials. Immediately change your password and safety questions. Contact your bank to report the abuse.
Credential stuffing prevention
Simply understanding credential stuffing and knowing how to prevent it is one of the best ways to keep your account safe. Follow the tips below on how to avoid a credential stuffing attack.
1. Turn on MFA (multi-factor authentication)
Multi-factor authentication requires that you provide two or more different types of information when logging in. For example, when you set up Face ID on iOS, the app stores your password and the biometrics of your face. No one can log in to your accounts without these two pieces of information.
Most accounts now allow you to turn on 2FA or MFA, so even if you provide the correct username and password, you must also enter a code sent to you via text. This prevents unwanted access to your accounts.
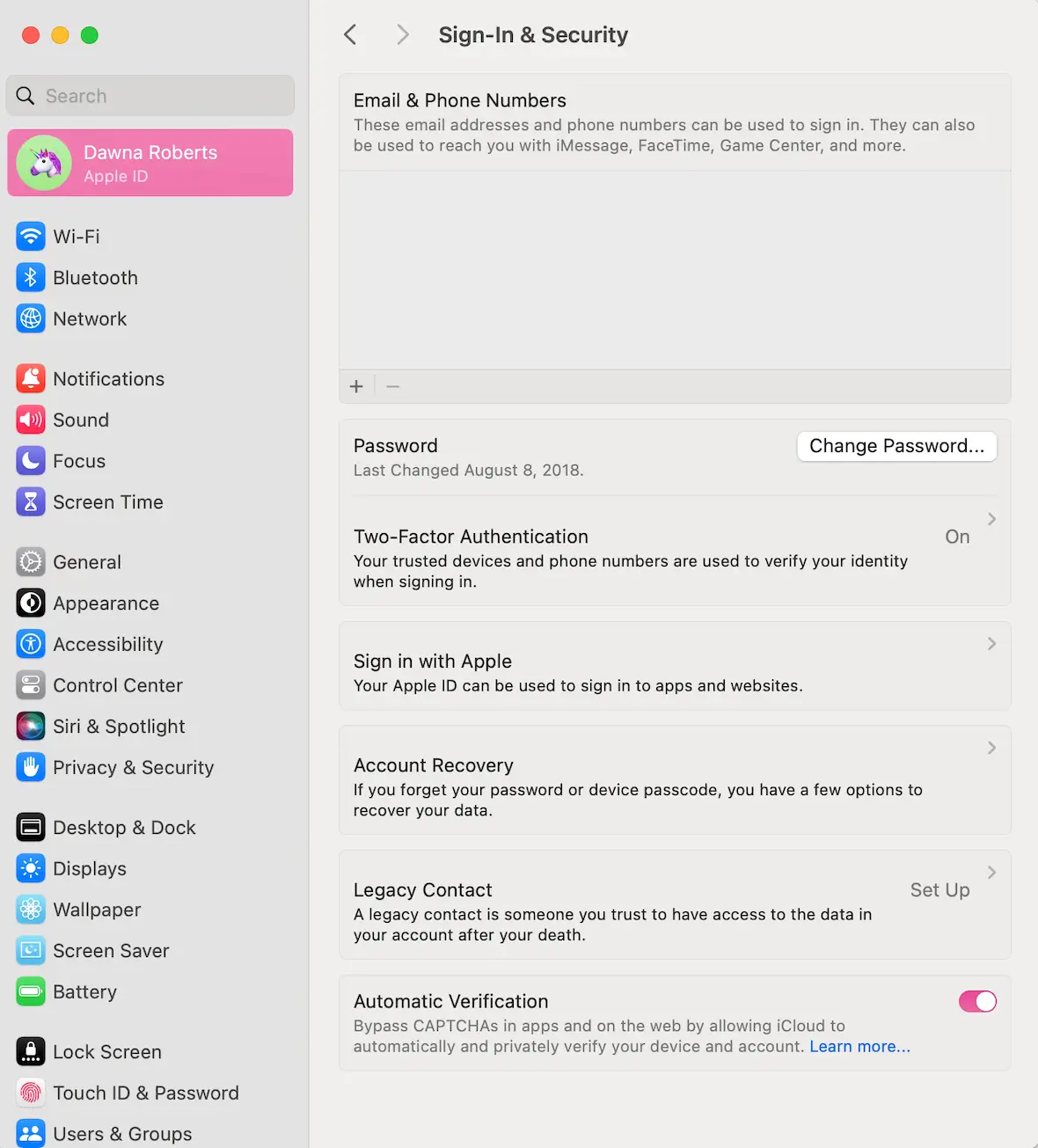
To turn on MFA on a Mac, navigate to the Apple menu. Select Settings, your name, and then Sign-In & Security. Use the toggle switch to turn on Two Factor Authentication.
2. Always use long, strong passwords
Always use long, strong passwords on all of your accounts. Change them regularly and keep them stored in a password vault.
3. Never reuse passwords
Never reuse passwords on multiple accounts. Doing so puts you at increased risk if you become the victim of a data breach, allowing attackers to potentially gain access to other accounts and exposing you to theft — or worse.
4. Do not share your login credentials
Never share your login information with anyone, even someone you know well. Your cybersecurity practices may be much different than those of your peers. Sharing your account login credentials, even with a well-meaning individual, could put your data in the hands of a ruthless hacker.
Real-life examples of credential stuffing attacks
Unfortunately, the world has seen numerous examples of credential stuffing, even within big companies with security measures in place. Some notable examples include:
- Zoom: In 2020, hackers accessed thousands of old Zoom accounts and used them in a massive credential stuffing attack. Some of the account credentials (found in data breaches dating back to 2013) were used in conjunction with bots to collect even more stolen accounts, which then ended up on the dark web.
- State Farm: In 2019, an attacker used login credentials from the dark web to break into millions of State Farm customer accounts. The attack affected 83 million State Farm customers.
- Spotify: One hundred thousand Spotify users were affected in a February 2021 credential stuffing attack. The goal of the attacker was to take over the stolen accounts and lock users out. At the time, it was the second attack in just a few months.
Credential stuffing costs companies more than $2 million per year. The good news is that you can prevent credential stuffing attacks by using cybersecurity best practices. If you change your passwords often, turn on multi-factor authentication, and are responsible with your login credentials, you can avoid this costly threat.