Our digital world runs on data. And data needs to be constantly formatted, verified, and secured. Every day, your data is encoded, encrypted, or hashed when you go online to write an email, send a message, a video, or move money over the blockchain. But what exactly do these terms mean? In this hashing vs. encryption guide, we’ll explain the difference.
Hashing, encryption, and encoding: A closer look
Although the technical mechanisms of hashing, encryption, and encoding are complex and advanced, the general concepts are easy to understand. Furthermore, it’s essential to know the difference between each term. The security, integrity, and validity of your data depend on it.
Encoding is not a security tool and is simply the process of formatting data so that a specific system can use it. For example, when you type or read text on your computer, it has been previously encoded into specific numeric characters, which your computer “translates” into visible text. On the other hand, encryption is only used to conceal or secure data. Algorithms and keys are used to encrypt data. Finally, hashing is also used for security purposes, but in hashing, the data is not concealed or transformed in any way.
What is hashing?
Say you work in an investment firm and receive monthly invoices detailing payments for millions of dollars. How can you verify, in seconds, that the information in such a large file has not been modified? The answer: hashing.
Hashing ensures data integrity. When data is hashed, an algorithm generates a unique and fixed-length string of characters. This string can only be created with that specific data. When the receiver gets the information, they can conduct a hash check or cryptographic hash function (CHF) to verify that it hasn’t been modified.
When hashing:
- The same input data will always produce the same hash string.
- No other input data will produce the same hash string.
- Any modification, even the slightest, will change the hash string.
- No one can know the input data if they only have the hash. Therefore, hashing cannot be reversed.
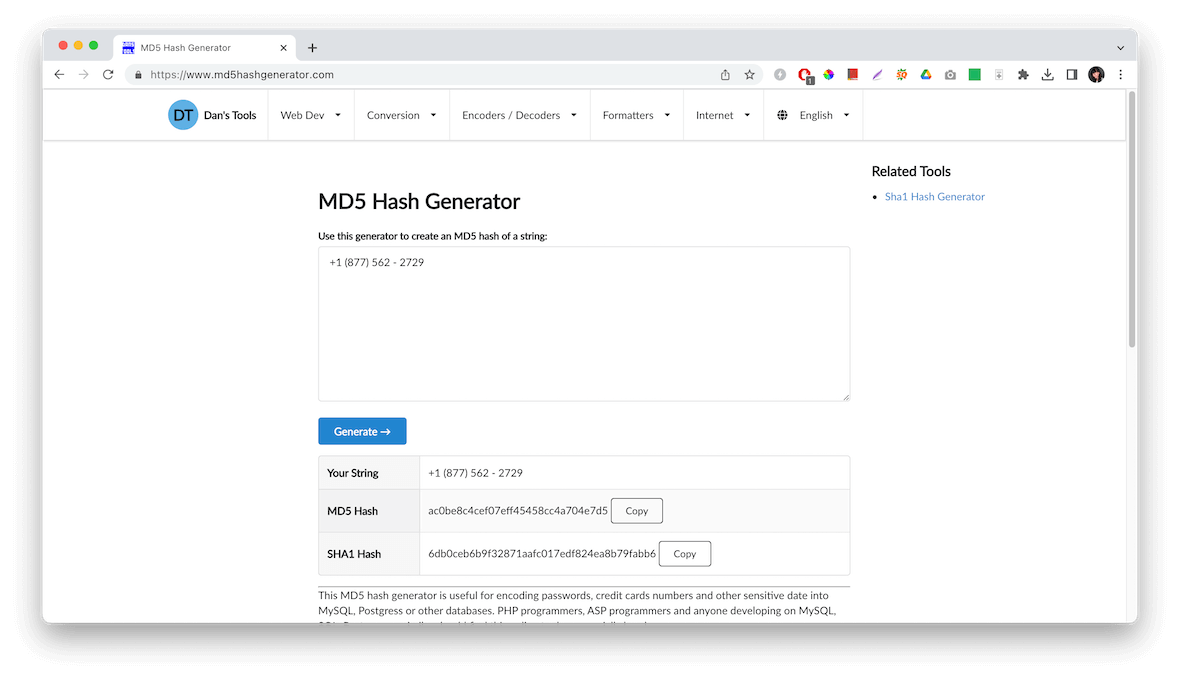
What is hashing used for?
The uses of hashing are extensive. When it comes to hashing vs. encryption, hashing is used by companies that need to check the integrity of data between two files. It is also used to verify blockchain transactions when you type in your passwords, browse the web, and do much more.
Examples of popular cryptographic hashing algorithms include MD2, MD4, MD5, and SHA-1. Message Digest 5 (MD5) uses a 128-bit hash, and Secure Hash Algorithm (SHA) uses a 60-bit hash.
What is encryption?
Encryption protects data by “scrambling” information using a particular key. And in theory, only the person with the key can “descramble” the message. Forms of encryption have existed since ancient times. In our modern digital world, the concept remains the same.
Digital encryption is the process of encoding data using keys and algorithms. Only authorized users holding a key or password can decrypt the data. In some cases, even those with the decryption key have restricted functions. For example, they might be able to see the data but not modify it. Encrypted data is known as plain text, and the secret key is known as a cipher. Finally, the result, or encrypted message, is called cipher text.
There are two types of encryptions:
- Symmetric key encryption: The same key is used to encrypt works to decrypt.
- Asymmetric key encryption: A public encryption key is used to encrypt, while a different private key can decrypt the message.
What is encryption used for?
Whether checking financial accounts, transferring money, or applying for loans online, people worldwide use encryption every day without knowing it. For example, when you send a message over WhatsApp, it is automatically end-to-end encrypted. This means no one but the sender and the receiver with the keys can read the message. However, if a hacker were to hack your WhatsApp account, they would get access to the messages, because they would be acting as you, the receiver.
Encryption is a key cybersecurity tool for combating ransomware. Encrypting data at rest, in transit, or in use is the only way organizations can truly prevent data exfiltration, theft, leakages, or extortion. A hacker who gains access to a system still can’t “see” or use the data if it’s effectively encrypted. Even if a hacker leaks the data, it will be nothing but gibberish and nonsensical characters.
Blowfish, AES RC4, RC5, and RC6 are some examples of popular encryption algorithms in use today.
What is encoding?
Encoding is the process of transforming or formatting data so that it can be effectively used in a particular system. Data is encoded using schemes that are public — known to everyone.
The purpose of encoding isn’t to keep information secret. Encoding can be easily reversed. For example, encoding schemes are used to view characters in different languages. Encoding is also used to compress and decompress large files.
What is encoding used for?
EBCDIC, ASCII, and Unicode are common encoding schemes used to represent characters in web pages or text files. Additionally, HTML encoding is used in websites, URL encoding is for site addresses, and languages like C, C++, Java, Python, and others are used to encode computer commands.
The differences between encoding, encryption, and hashing
As we have seen, these three terms are not interchangeable. Encoding is applied in data usability, encryption is used for data security, and hashing is used for data integrity. The technical mechanics of hashing vs. encryption, for example, are substantial.
Encoding vs. encryption
Encryption and encoding are both irreversible. However, when encoding, the scheme used to transform the data is publicly available for anyone online. Furthermore, the schemes are well known. Therefore, encoded data can be decoded easily and rapidly reverted to its original state.
In contrast, while encrypted data is also reversible, only authorized users with the key can revert it to the original state.
Hashing vs. encryption
Encryption and hashing share common ground. They are both techniques used in data security. The difference is that hashing does not protect data from being read but from being manipulated or altered. Hashing is an excellent approach for ensuring that information received can be trusted and is truthful to its origin.
Encryption comes into play when users do not want their data exposed in any way to anyone other than themselves or others authorized. The combination of encryption and hashing can be an effective way to keep data safe, secret, unreadable, and verifiable.
The following is a rundown of the major differences between these three terms.
| Hashing | Encryption | Encoding | |
|---|---|---|---|
| Used for | Data integrity | Data security | Data usability |
| Reversible or irreversible | Irreversible | Reversible only with secret keys | Easily Reversible |
| Types | Uses one main type or process | Symmetric and assymetric | Different types (text, HTML, URL, Java) |
| Algorithms | MD5, SHA-1, SHA-2, NTLM, and LANMAN | 3DES, Blowfish, AES, RSA, and others | Does not usually use algorithms, uses schemes |
| Keys or schemes | May or may not use keys | Uses keys | Uses schemes |
| State of data | Not modified | Ciphered | Formatted |
| Keeps data secret? | No | Yes | No |
In conclusion, there are clear differences between encryption, encoding, and hashing. While all these techniques are applied to data, each is specific to certain fields. With encoding, data can be used. But with encryption, information remains safe. And hashing adds a new layer of integrity. Mix them up, and you have a robust foundation for most aspects of data management.