Apple released patches for over 70 vulnerabilities previously found in macOS and iOS. While Apple devices are now safer due to these new patches, a significant portion of the work behind these security updates was done by external researchers.
Apple’s latest security sweep across all devices
On October 28, Apple released a number of security patches across all of its devices, including iPhones, iPads, Apple Watches, Macs, tvOS, and Vision Pro devices. Of these updates, the majority (50) were for macOS vulnerabilities, while 27 were for iPads and iPhones.
The good news for Apple users is that none of the over 70 vulnerability patches seem to be zero-day vulnerabilities already exploited in the wild. This means no bad actors were using these vulnerabilities to hack your macOS or iOS.
A closer look at the vulnerabilities addressed
Those who want to dig through the entire list of patches issued before they run updates can find them at the following sources:
Going through each and every vulnerability in this report is virtually impossible due to the length of the list — more than 70 in total.
Apple does not disclose information on the security patches they issue or investigations into CVEs. Therefore, even if we tracked down each CVE, most of the vital information on how each particular vulnerability works is closely guarded in the hands of Apple and those who reported the CVE.
Recent updates to iOS 18.1 and iPadOS 18.1 address several critical security vulnerabilities. These include issues that could potentially allow attackers with physical access to a locked device to view sensitive user information. Additionally, malicious apps could exploit vulnerabilities to run arbitrary shortcuts without user consent or access private information. Furthermore, parsing certain file types could lead to the disclosure of user data.
In contrast, for macOS Sequoia 15.1, one notable vulnerability could allow malicious apps to run arbitrary shortcuts without user interaction. Other issues include the potential for sandboxed processes to bypass restrictions, the unauthorized modification of protected file system areas, and access to user contact information. Additionally, attackers in privileged network positions could exploit vulnerabilities to leak sensitive user data.
How Apple’s collaborative security policy works
Almost all of these vulnerabilities share one thing in common: They were discovered not by Apple security teams but by researchers, cybersecurity companies, organizations, software developers, and even anonymous investigators.
The trend is not new. For the past several years, Apple has been collaborating more and more with developers and third parties to strengthen their capabilities. However, Apple is stepping on the gas when it comes to this type of convenient security work collaboration.
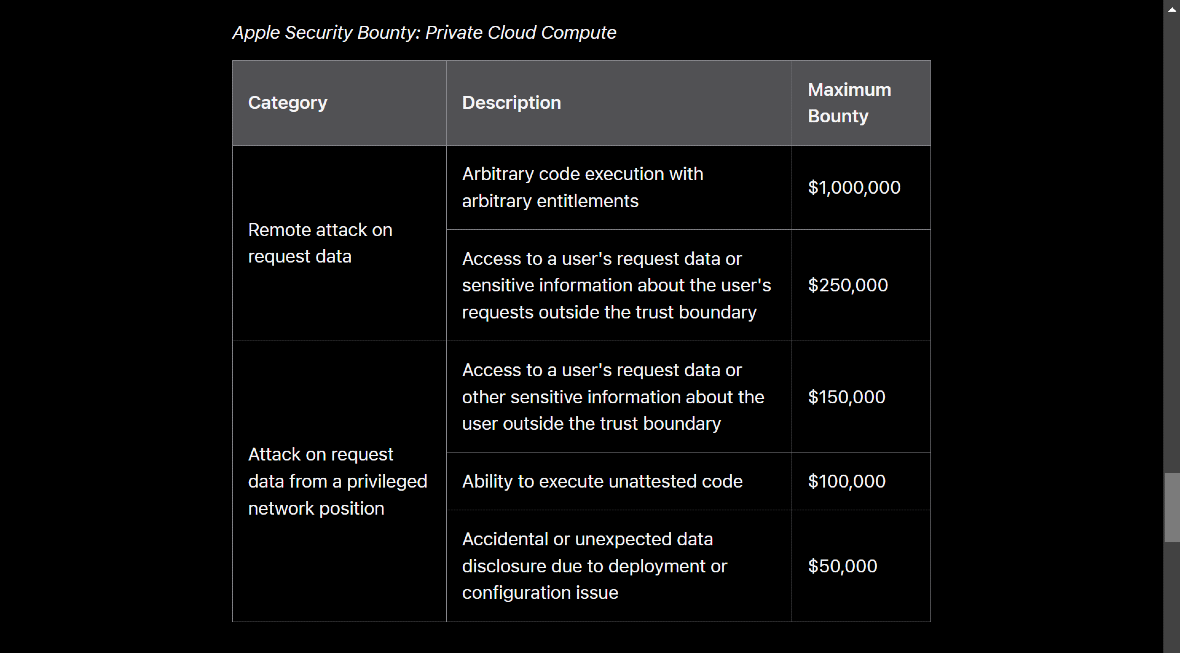
On October 24, Apple said that whoever finds and reports to them an exploit that would allow a threat actor to remotely run malicious code on its new Private Cloud Compute servers, used for its recently launched Apple Intelligence, will get $1 million.
Researchers who find a vulnerability that can be exploited to extract user data from the Private Cloud Compute environment get paid, too — up to $250,000.
Final thoughts on building stronger Apple security
Is an army of ethical hackers, researchers, and developers the solution against a global army of relentless cybercriminals? Many leading tech companies like Apple believe it’s at least part of the solution.
Vulnerability disclosure programs, bug bounty programs, and other similar initiatives are the norm in Apple security patches today.
Researchers, organizations, and companies that want to collaborate with Apple can do so through Apple Security Bounty, Apple on HackerOne, or simply report a vulnerability to the company.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. iOS, iPadOS, macOS, watchOS, tvOS, and visionOS are trademarks of Apple Inc.






