When KnowBe4 hired its latest Principal Software Engineer, things didn’t turn out exactly as planned.
The company had checked all the right boxes. They posted the job, received CVs, did interviews and background checks, and verified references. The HR department even had 4 different video conference interviews with their potential hire and visually confirmed his identity.
However, as soon as KnowBe4 sent the new hire the company’s Mac workstation, the coin flipped. Immediately, their new hire began loading malware on the company-provided Mac.
Hiring a North Korean hacker isn’t that uncommon — and that’s a big problem
KnowBe4 learned the hard way that the person they had hired belonged to an army of remote tech workers run by the Democratic People’s Republic of Korea (DPRK, aka North Korea).
Unfortunately — and as strange as it may sound — what KnowBe4 experienced is not an isolated case. Since 2022, the United States Department of Justice (DoJ) has warned that North Korea dispatches thousands of highly skilled IT and tech workers to work around the world with the goal of funding sanctioned North Korean programs, such as the development of ballistic missiles, weapons of mass destruction, and its nuclear program.
According to the DoJ, this threat should not be underestimated. Annually, the group of North Korean “workers” collectively send North Korea’s government more than $3 million every year.
Not a breach but a cautionary tale
In a move praised by cybersecurity leaders, KnowBe4 fully disclosed the incident. KnowBe4 said the attempt to load malware was immediately shut down and contained. The attacker never had access to any company data or company platforms or systems, as he had not finished his onboarding and, therefore, had very limited access.
Some media outlets mistakenly reported the news as a data breach. Consequently, while speaking to Moonlock, KnowBe4 felt the need to set the record straight again.
“We’d really like to reiterate, everything is fine at KB4,” KnowBe4 told Moonlock. “There was no breach, no info was lost. We caught it immediately and decided to use this to illustrate how important it is to be alert and it is part of our culture of radical transparency.”
“If it can happen to us,” said KnowBe4, “it can happen to others.”
How the North Korean hacker got through the door
The expert North Korean hackers who pose as legitimate IT workers are well organized. They are trained and are provided with resources and support by their government. They apply to a wide range of jobs around the world, including mobile and web developer positions, IT support, animation, blockchain-crypto roles, online gambling, hardware, biometrics, virtual reality, and now AI.
AI, software and hardware skills, info stealer knowledge, identity theft, and a deep understanding of the American job application processes were among the skills possessed by the North Korean attacker hired by KnowBe4. These are major skills. And they are not unique to this specific bad actor.
“This was a skillful North Korean IT worker,” KnowBe4 revealed in its new incident FAQ page, “supported by a state-backed criminal infrastructure, using the stolen identity of a US citizen participating in several rounds of video interviews and circumvented background check processes commonly used by companies.”
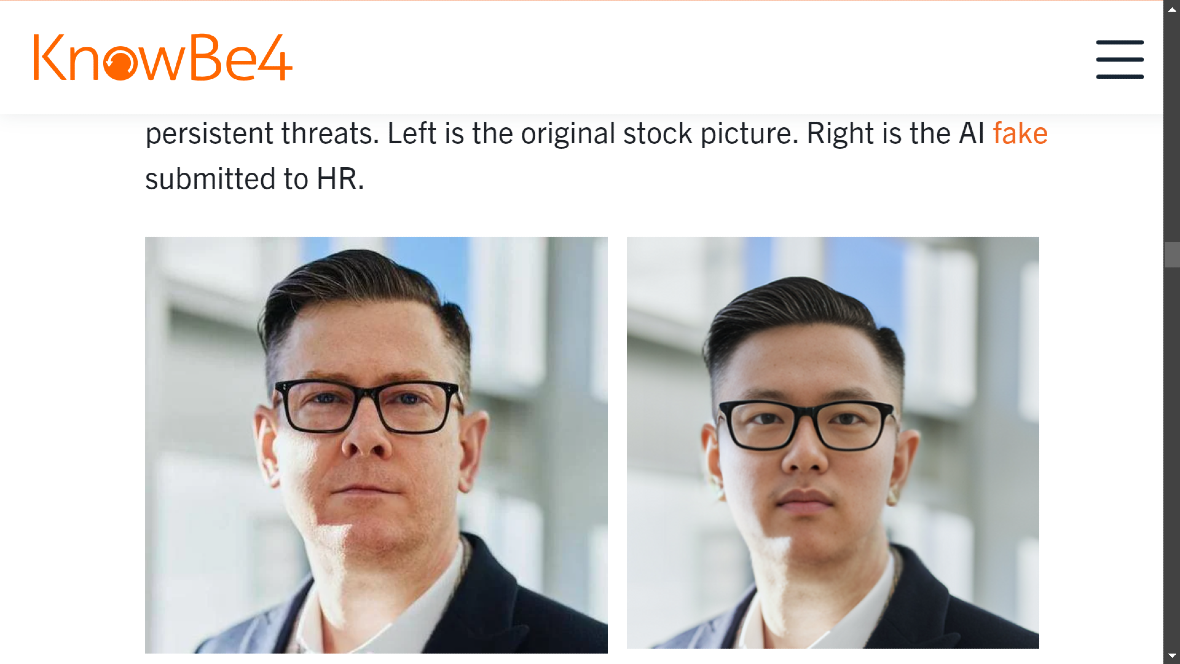
The hacker used a stock image, which he modified with AI deepfake technology when submitting his photograph to HR. The photograph was confirmed later through video interviews, proving the attacker was, in fact, a real person. The background checks KnowBe4 ran checked his identity and raised no red flags because the attacker used a US-based stolen identity, a fact that in itself is already worrying.
The hacker’s actions after he was hired
Usually, North Korean hires will lay low, do the job they were hired to do, and get paid for it. This money is then sent to the North Korean government to fund illegal programs. In some exceptions (when the data exceeds the pay), the scam workers will load malware onto company systems or steal information.
But, for some reason, this attacker’s first action after powering up KnowBe4’s shipped Mac was to attempt to start loading malware immediately. The scammer tried to manipulate session history files, transfer potentially harmful files, execute unauthorized software, and used a Raspberry Pi to try to load an infostealer.
KnowBe4 attempted to contact the worker, who soon became unresponsive. Less than 25 minutes later, the Security Operations Center (SOC) of Knowbe4 contained the Mac and put a final end to the attack before it even began.
“I don’t have to tell you about the severe risk of this,” Stu Sjouwerman, the founder and CEO of KnowBe4, wrote in a blog post that details the event. “It’s good we have new employees in a highly restricted area when they start, and have no access to production systems.”
“A learning moment”
The cybersecurity community grows stronger when organizations share information and details about incidents, new technologies, and vulnerabilities. Yet many companies will not disclose details of security incidents if they are not required to do so. This is done out of fear of reputational and economic damage.
However, KnowBe4 decided to share the incident with the entire world. “This is not a data breach notification, there was none,” Sjouwerman clarified in the blog post. “See it as an organizational learning moment I am sharing with you.”
Staying on top of your security when hiring
It is evident that standard hiring processes are now being challenged by nation-state-supported actors and new technologies like deepfakes and AI. Companies should consider the following tips and update their hiring and remote worker policies to better reflect the conditions of the global threat landscape.
To bolster security, a comprehensive review of employee vetting procedures is essential. This includes conducting more rigorous background checks, verifying employment history, and cross-referencing provided information across multiple sources.
Additionally, implementing enhanced monitoring of system access, particularly for remote employees, is crucial. This can be achieved through regular device scans to prevent unauthorized remote access, video verification of employee location, and close scrutiny of work patterns. Discrepancies such as mismatched shipping addresses for company-issued laptops or inconsistencies in resumes should be highlighted as potential red flags.
To further safeguard company assets, several security enhancements are recommended. These include implementing robust access controls, strengthening authentication processes, and conducting regular security awareness training for all employees with a focus on social engineering tactics. Furthermore, organizations should invest in advanced monitoring tools to detect and prevent unauthorized access attempts, malware execution, and data exfiltration.
Employees should be made aware of potential indicators of suspicious activity. These include the use of VOIP numbers without verifiable online presence, inconsistencies in personal information across different platforms, and excessive reliance on VPNs or virtual machines for accessing company systems. Moreover, any attempt to cover up suspicious activity should be reported to HR for further investigation.






