America’s big tech companies, including Amazon, Google, Meta, and even Apple, have all faced fines for breaching strong European laws designed to protect user data in the region.
Infractions have included moving data out of the European Union (which is banned), allegedly breaching monopoly safeguards, and failing to implement strong privacy and security. Other issues include failing to comply with the European Union’s General Data Protection Regulation (GDPR), the new Digital Markets Act (DMA), and the Digital Services Act (DSA).
Overall, meeting the requirements of Europe’s legal regulations can be challenging for any company. But no company has been fined more than Meta. In fact, Meta has paid over $2.76 billion (€2.5 billion) in fines for breaching the GDPR, including a record fine of $1.3 billion (€1.2 billion) in 2023. Now, the company is once again under scrutiny — this time, for storing passwords in unprotected plaintext.
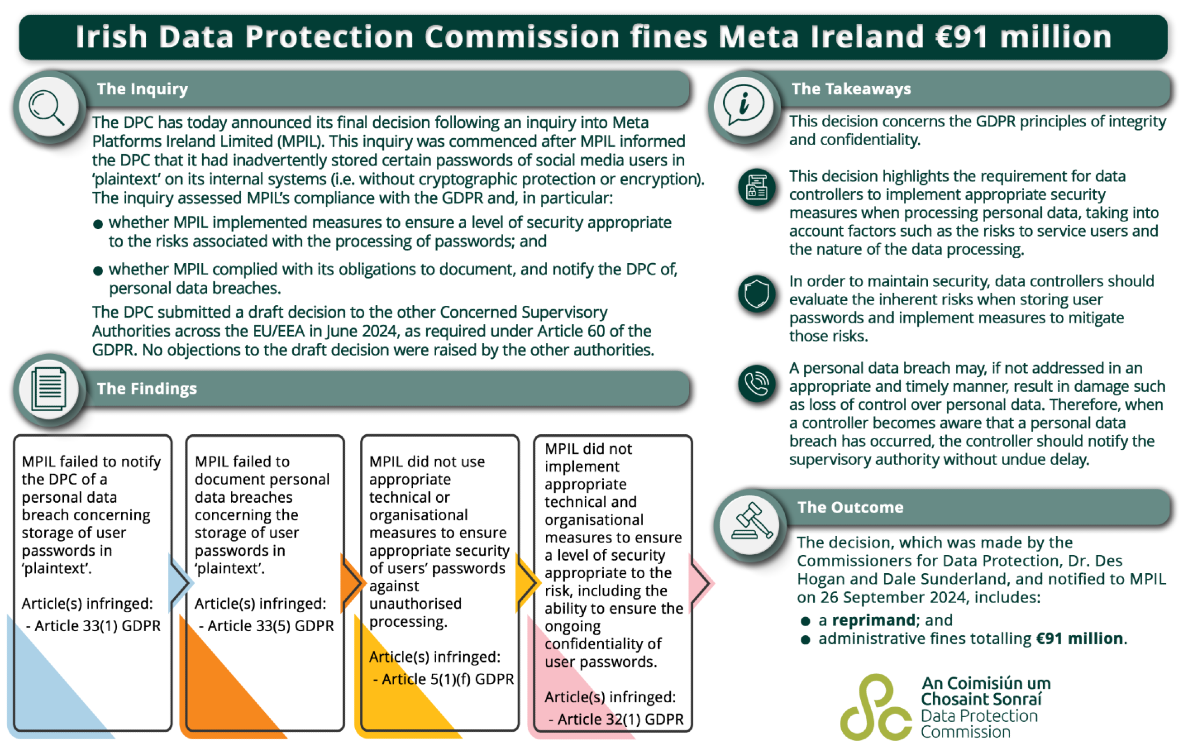
Irish Data Protection Commission issues final decision for a case which began in 2019
On September 27, the Irish Data Protection Commission (DPC) — the supervisory authority for the General Data Protection Regulation (GDPR) in Ireland — announced its final decision following an investigation that began in 2019 into Meta Platforms Ireland Limited (MPIL).
The DPC, no stranger to investigating Meta, has been looking into how certain passwords of social media users were inadvertently stored on Meta’s internal systems in plaintext, without any type of cryptographic protection or encryption.
What happened in 2019 with Instagram and Facebook passwords?
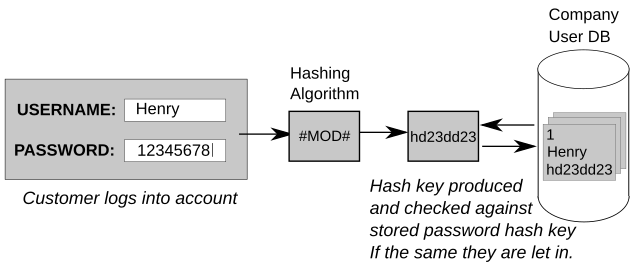
In March of 2019, and again in an April update, Meta informed thousands of millions of Facebook and Instagram users that their passwords had been stored on their internal systems without any protection or encryption and in plaintext. Meta claims that no external party ever accessed the data.
Usually, companies deploy different technologies when they store the password a user creates. Protective measures are taken to prevent the password from being seen by anyone, including people who work inside the company.
If a company chooses to store passwords without protections, it makes the work of a threat actor very easy. A threat actor only needs to access a specific internal infrastructure location and copy-paste thousands or even millions of users’ passwords.
Much has changed since this incident took place back in 2019. Meta has come up with a fix to this issue, which they downplayed as a bug or glitch. In the cybersecurity industry, however, Meta’s 2019 “mistake” has not been forgotten.
Meta failed to deploy measures to protect the users’ passwords
Fast-forward to the present day, and the DPC — the ones who actually found out that Meta was storing passwords in plaintext and notified the company — have finally announced their final decision.
Meta is to be “reprimanded” and must pay a fine of $100.53 million (€91 million).
The DPC claims that Meta failed to meet the standards of several GDPR articles, including Article 33 (1-5), Article 5 (1) (f), and Article 32 (1). This translates to a failure to notify authorities and document a personal data breach concerning the storage of user passwords in plaintext and a lack of measures taken to secure users’ passwords.
“It is widely accepted that user passwords should not be stored in plaintext, considering the risks of abuse that arise from persons accessing such data,” Deputy Commissioner at the DPC, Graham Doyle, said in the press release.
Security experts weigh in on Meta’s password incident
Moonlock spoke to Darren James, a Senior Product Manager at Specops Software, an Outpost24 company that provides password management and authentication solutions to help protect business data.
“This is another horrendous example of the mishandling of user passwords that can cause huge financial damage to organizations as well as the affected end users of the platform,” James said.
“Firstly, it is incredible that in the first instance, the developers even considered allowing passwords to be stored in plaintext — this is a fundamental rule of system security, let alone flouting of the GDPR laws.”
Credential stuffing: How many times do you reuse your password?
One of the biggest dangers with plaintext passwords is credential stuffing — a criminal technique in which attackers use passwords they buy in bulk on the dark web across different sites, accounts, and platforms. This technique capitalizes on users who use the same login credentials on multiple platforms.

In 2024, Google found that 52% of Americans used the same password in multiple places. Bitdefender’s 2024 Consumer Cybersecurity Assessment Report revealed that 18.7% use the same password for 3 or more accounts, 15.8% use the same password for at least 2 accounts, and 21.7% use autofill features of their web browsers or operating system (OS).
“We all know that people have so many passwords to remember these days, and it’s more than likely that many of the revealed plaintext passwords are also being used on other accounts belonging to the affected users — exposing them to even greater risk of account takeover,” Darren James from Specops Software told Moonlock.
We all know that people have so many passwords to remember these days, and it’s more than likely that many of the revealed plaintext passwords are also being used on other accounts belonging to the affected users — exposing them to even greater risk of account takeover.
Darren James, Senior Product Manager at Specops Software
“The password reuse problem is an issue that we all face today, so it’s imperative that organizations implement solutions that encourage the use of strong, unique passwords, and have the ability to continuously scan and detect when a password becomes breached and take action accordingly.”
The role of a strong cybersecurity culture beyond technology
Javvad Malik, Lead Security Awareness Advocate at KnowBe4, a cybersecurity culture and training company, also spoke to Moonlock.
“What is particularly troubling about this incident is not just the storage of sensitive information in an insecure manner, but also the apparent delay in notifying the relevant regulators and impacted users,” Malik said.
Malik added that incidents like these may be easy to fix and patch up from a technical perspective, but it’s the culture of the company that worries him.
“It doesn’t address the cultural perspective which organizations need to bear in mind in order to be effective in cultivating security responsibility throughout the organization,” Malik said.
Final thoughts
The final decisions of the DPC from Ireland, which is likely to be appealed by Meta, may mark the end of the 2019 investigation. Nevertheless, the issues it deals with remain relevant today. This case is a strong reminder for companies, organizations, and users of the risks that exist today and still drive cyberattacks.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Meta Platforms, Inc. Facebook and Meta are trademarks of Meta Platforms, Inc.






