It has been about seven months since Norton Healthcare — a leading United States healthcare organization serving Greater Louisville, Southern Indiana, and Kentucky — first reported a security incident in May. Now, in December, the healthcare provider confirmed that the attack ended up compromising data from 2.5 million people.
Data from current and former patients, employees, and dependents was stolen in the Norton Healthcare ransomware attack. As the media breaks down the ransomware saga and healthcare ransomware trends in the US, those impacted by the attack are rushing to understand what was stolen and what they can do to protect themselves.
A ransomware attack perpetrated by BlackCat
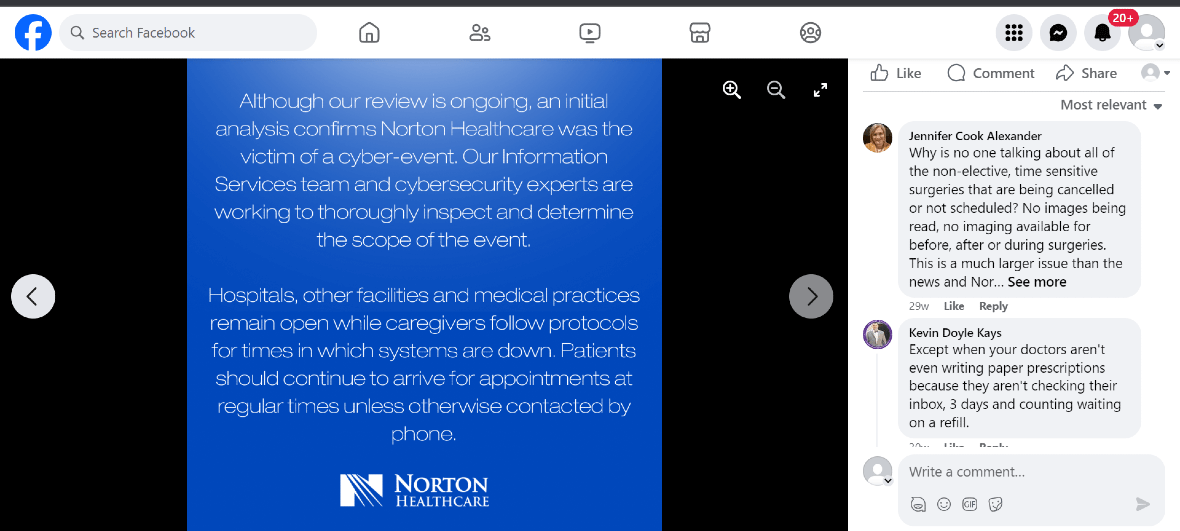
On May 12, Louisville Public Media reported that Norton Healthcare, through a communication, disclosed that they had notified law enforcement after suffering from a “cybersecurity incident.”
According to the report, Norton’s security team took systems offline and shut down internet and email access after noticing “suspicious communications.” Days later, the health organization added that they were restoring operations to normal and would be investigating the security breach.
At that time, Norton Healthcare failed to disclose that the attack was, in fact, a ransomware attack. But the ALPHV/BlackCat ransomware gang made sure the record was set straight from the start by claiming responsibility.
Data Breaches reported on the communication released by BlackCat, along with a sample of the stolen data. The criminal group stated they had stolen 4.7 TB of data. This massive amount of data signals the severity of the breach.
Analysis of the exfiltrated sample made public by BlackCat revealed that Norton Healthcare’s compromised data included personal and sensitive information of patients, images of checks and bank statements, and files with employees’ personnel information such as names, dates of birth, and social security numbers.
No patient photos were included in the sample. However, Data Breaches reported that “the reference to the photos (in the sample) is a somewhat chilling reminder of what BlackCat did to Lehigh Valley Health Network breast cancer patients whose nude images were dumped.”
BlackCat and Norton Healthcare exchange words
The criminal group, BlackCat, had strong words for Norton Healthcare as it pressured them to pay the ransom.
“We have provided more than enough time to Norton’s Executive and Board Members but they’ve failed to show bravery to protect the privacy of their clients and employees,” BackCat said in May.
“They failed to protect confidential data and they’re making false statements in the recent news and lying to people… we’ll release very interesting data, images belonging to all patients, and millions of SSN records… and 25k employees!”
Norton Healthcare took its time to respond and did so officially once its investigation was concluded. On December 9, as the copy of the notice to affected Maine residents featured by the Office of the Maine Attorney General reads, Norton Healthcare claims to have determined at a later date that the attack was ransomware. They had also notified the FBI and were beginning investigations with the assistance of outside legal counsel and a respected forensic security provider.
“Norton did not make any ransom payment,” the healthcare provider said.
What data was stolen?
Norton Healthcare claims that the attack did not access Norton Healthcare’s medical record system or Norton MyChart, adding that due to an “abundance of caution,” it would be efficient to notify of the breach the following:
- Current and former patients
- Employees
- Employee dependents and beneficiaries
The Office of the Maine Attorney General’s official data reveals that a total of 2.5 million people were affected by the ransomware attack, including approximately 385 of residents from Maine.
Data that was potentially stolen includes:
- Name
- Contact information
- Social security number
- Date of birth
- Health information
- Insurance information
- Medical identification numbers
- Driver’s license numbers
- Other government ID numbers
- Financial account numbers
- Digital signatures
Are you affected by the Norton Healthcare breach? You will want to read this
Norton Healthcare’s letter of notice of the data breach, sent to those impacted, assures that they are enhancing security safeguards. The letter also adds that Norton Healthcare hired Kroll Monitoring, a provider of risk and financial solutions, to provide those impacted by the breach with 2 years of identity monitoring services at no cost.
The Kroll Monitoring services included in this offer are:
- Credit monitoring
- Fraud consultation
- Identity theft restoration
Norton Healthcare advised that those impacted by the breach visit Kroll Monitoring to activate their free identity monitoring services. Users have a specific deadline to meet and must use a Membership Number (both established and provided by Norton Healthcare in a personal letter of notice or communication).
What else should you do if impacted by the Norton Healthcare breach?
If you are affected by this breach or a similar ransomware attack on your healthcare provider, we strongly encourage you to take a proactive approach to immediately secure and protect your accounts, digital information, and other resources.
Change passwords: Immediately change your passwords for online accounts associated with the healthcare provider, including your patient portal and any other accounts that used the same password. Consider using a password manager to create strong, unique passwords for each account.
Monitor credit: Place a fraud alert on your credit reports with the three major credit bureaus. This will make it harder for criminals to open new accounts in your name. You can also consider credit monitoring services to be proactively notified of any suspicious activity.
Review statements: Carefully review your bank and credit card statements for unauthorized charges. Report any suspicious activity to your financial institution immediately.
Be cautious of phishing: Scammers may try to capitalize on the data theft by sending phishing emails or texts pretending to be your healthcare provider or a legitimate authority. Be wary of any unsolicited communication, and never click on suspicious links or download attachments.
Additionally, under the HIPAA Act, healthcare providers and health organizations are responsible — and liable — for your data security. We recommend that you contact a specialized attorney, keep in contact with the healthcare provider, and follow professional legal advice.






