Have you ever noticed that Safari, unlike Chrome or Firefox, does not display a message when you go full screen? Well, you might not have noticed, but cybercriminals have. And they are using this “flaw” to their advantage to steal your credentials and passwords. Let’s break down this new cyberattack technique.
It’s not your browser, it’s an attacker’s remote browser that you are seeing
Recently, SquareX Labs reported that a Safari vulnerability allows attackers to steal your credentials using what they called a “fullscreen browser-in-the-middle (BitM)” technique.
Browser-in-the-middle attacks are not new. They are used by cybercriminals to lead victims to malicious fake sites. There, victims click on a “Sign in” or “Claim Gift” button and are prompted to enter sensitive information or login credentials.
Make your Safari immune to hacker attacks
From the victim’s perspective, remote browsers go unnoticed. They assume they are using their own browser. In reality, it’s a browser created by attackers in a virtual machine cloud environment.
These malicious remote browser environments are usually automated to extract your username and password and record all data you exchange with the browser.
Why is this BitM different from others and harder to spot?
BitM attacks are usually easy to spot because they require users to navigate to a specific URL. This usually raises suspicion among users due to misspellings in the URL.
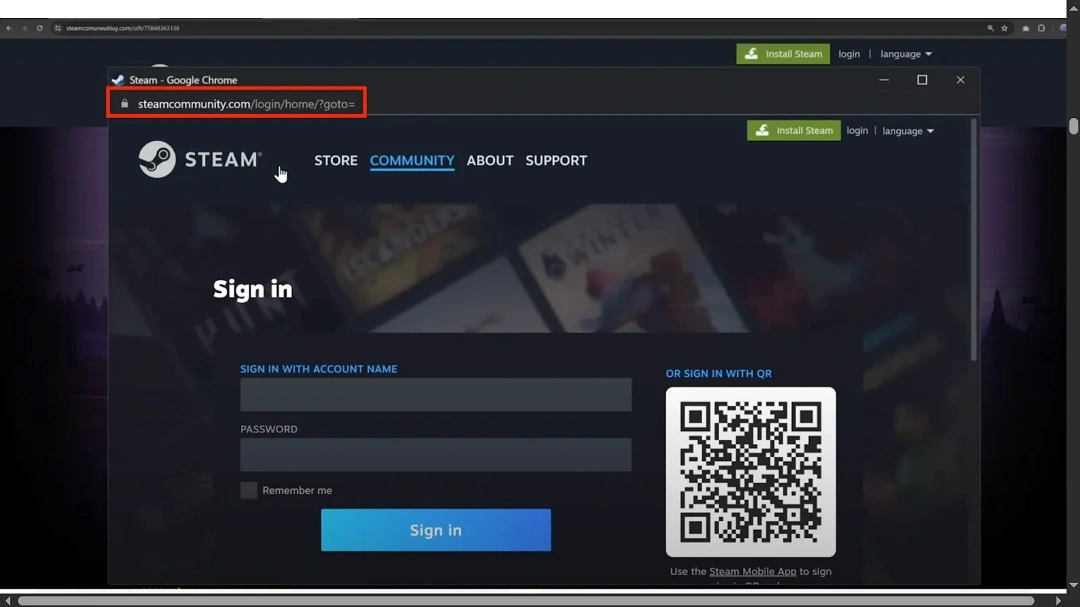
For example, a threat actor might design a malicious site that impersonates the domain www.steamcommunity.com (a legitimate and popular site), but the URL might read differently, with minor errors such as https://steamcomuneuitiuy[.]com/oift/75848363136. The misspellings are usually minimal, but most users will spot a difference.
However, SquareX Labs’ investigation found that by leveraging the full-screen function of the Safari browser, the malicious URL remains hidden. SquareX Labs claims that this abuse of the full-screen Safari function, in combination with remote browser attack techniques, leaves Apple users at great risk of having their credentials stolen.
Distributed via malvertising and phishing channels
If you’re wondering how to spot this attack technique, consider the following. According to SquareX Labs, browser-in-the-middle (BitM) and browser-in-the-browser (BitB) attacks are distributed via malvertising. This means bad actors create, pay for, and run fake ads that direct users to the malicious sites that trigger these attacks by using platforms like Google Ads.
To avoid falling for this, double-check any sponsored content or ads that you might find online while searching the web on your favorite search engine.
Another thing you should be on the lookout for are comments that incentivize users. These may be free gifts, giveaways, or rewards spread via social media platforms like Telegram, Discord, and others. The gaming and crypto communities are heavily targeted, so keep that in mind as well.
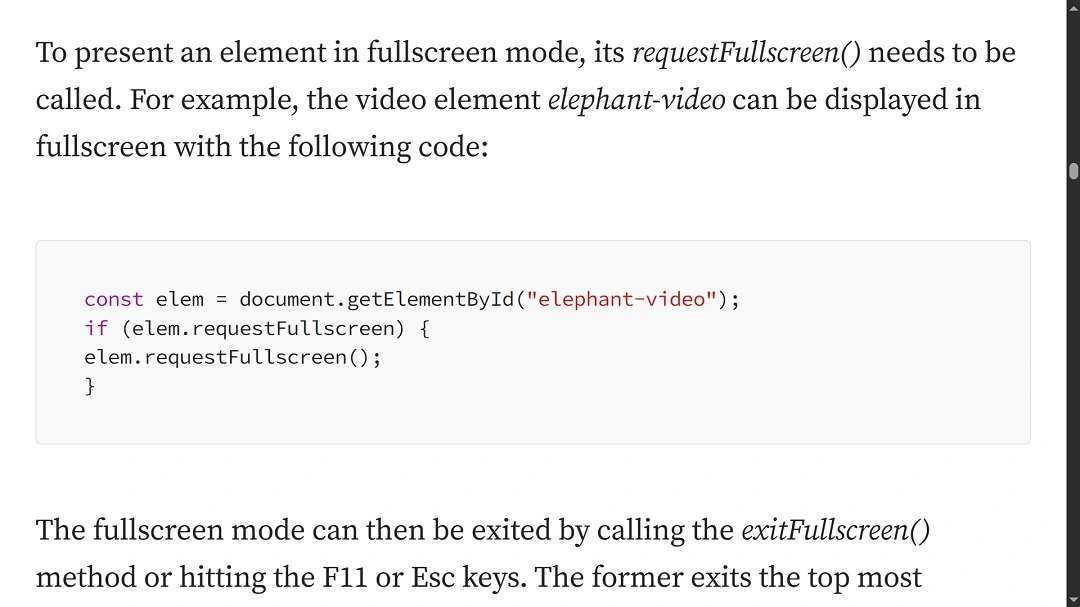
How does the full-screen BitM attack work on Safari?
SquareX Labs mounted a demonstration and a short video on how the attack works.
Step 1: The bad actors create ads and promotional videos on YouTube, Instagram, or TikTok. They also may create QR codes or social media messages to promote a fake campaign, usually a giveaway.
Step 2: Victims click on the link in these fake ads or messages and land on a malicious page. The malicious page is a phishing page hosted inside a virtual cloud environment, for example, on Amazon Web Services (AWS).
Step 3: The victim lands on the malicious site. The victim has no idea they are, in fact, inside a virtual machine and virtual environment created by cybercriminals.
Step 4: The malicious website might have a button to “Claim” or “Sign in” or a QR code to scan. Using iframes, attackers conceal code behind these buttons that eventually lead users to a full-screen remote browser (developed and controlled by the cyber attackers).
Step 5: Safari does not restrict full-screen functions or remote browsers. Therefore, the attacker’s code runs without a problem. The phishing link takes users into a streamed session of a pre-hosted remote browser on the virtual environment controlled by the attacker.
Step 6: Once on the remote browser, the victim is prompted to enter their credentials for a specific account (Google, Steam, or any other). The sign-in pages are identical because they are the actual, legitimate service in these attacks. The victim has no way of knowing he is being hacked.
Step 7: The attackers register all the data, including passwords, that the victim exchanges with the login sites through the remote browser. The victim may even continue opening new tabs, thinking they are using their own browser and logging in to other accounts. The attackers will steal that information as well.
A quick note on BitM vs. BitB
SquareX Labs researchers explained that browser-in-the-middle attacks are much more powerful than browser-in-the-browser attacks. This is because they allow the victim to access their account after entering their credentials, leaving them unaware that they have been phished.
In a BitM attack, the login pop-up is actually a fully interactive, attacker-controlled remote browser, such as one streamed through a noVNC client. It renders the legitimate site (like Steam or Microsoft 365) inside a cloud-hosted session, not locally. The victim sees the real UI and backend in action, but it’s all happening in a browser they don’t control.
By contrast, BitB attacks use HTML/CSS/JS tricks to fake a browser window within the current tab, no remote browser involved. BitB is easier to detect because everything is client-side and static.
BitM is more dangerous. Once the victim logs in, they’re still inside the attacker’s browser session and might keep using it to check email, access internal apps, or open other tabs — all visible and controllable by the attacker.
Why is Safari particularly vulnerable to full-screen BitM attacks?
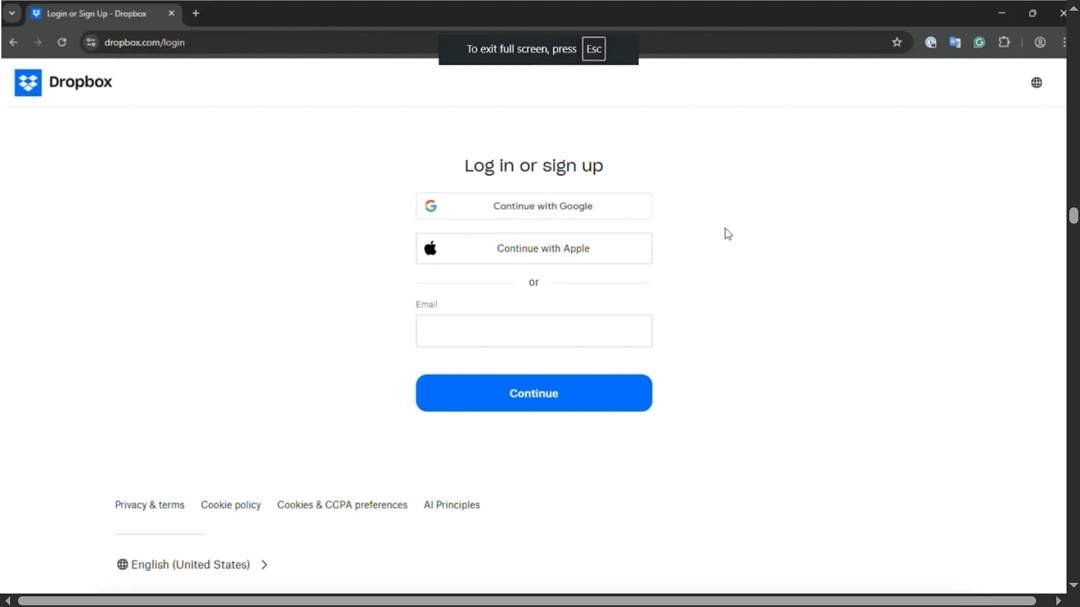
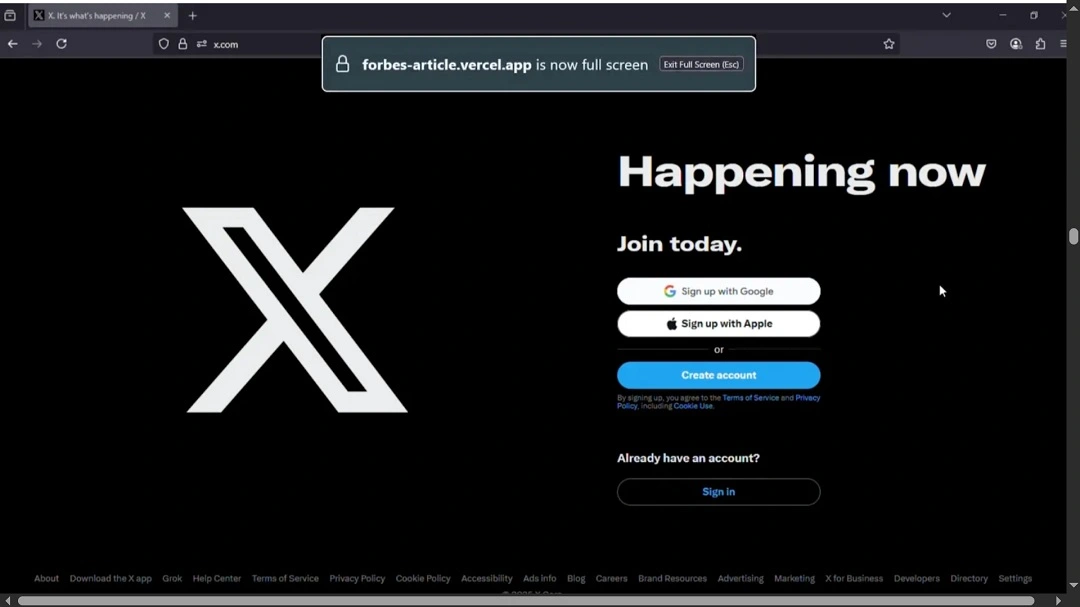
As mentioned at the beginning of this report, Chrome and Firefox browsers display visual cues for users to be aware that they have entered full-screen mode. Safari, however, does no such thing.
The images shared by SquareX Labs below clearly show what happens when you enter full-screen mode in Chrome and Firefox.
The visual cues pop up every time you enter full-screen mode in these browsers. They also offer users clear indications on how to exit full-screen mode.
Why does Safari have no warning? This question is probably for Apple developers and designers to answer.
We can think of no reason other than a “cooler user interface design” choice to be the reason why full-screen messages are not displayed in Safari.
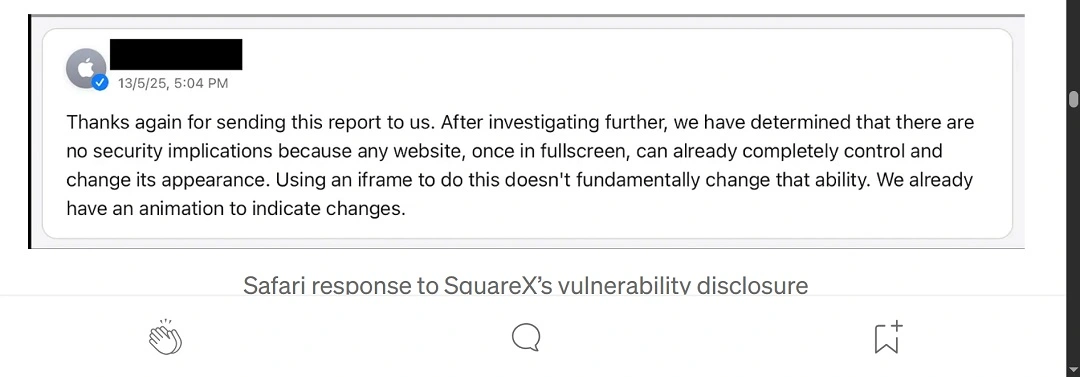
SquareX Labs believes that the lack of visual cues to indicate to users that they are in full-screen mode in Safari is a “vulnerability” that presents risks and should be patched. After disclosing the problem to Apple, they got a response. But it was not what they expected.
Apple claims that the “vulnerability” that SquareX Labs identified is not a vulnerability at all. They assert that the function (full screen) in Safari is working as intended.
Only time will tell if this “design flaw” becomes a popular technique among cybercriminal groups and underground criminal gangs. It could force Apple to change its mind on full-screen messages and patch Safari in a future update.
Avoid the hack, keep your passwords where they belong
As of today, your Safari cannot detect, flag, warn you, or shut down any attempt that a cybercriminal makes to lead you to a remote browser. Actually, there is nothing to detect, as these are functions created and used for legitimate purposes.
Safari will also not warn you if what you are looking at has been a full-screen reload or a normal redirect. So, what can you do to avoid these hacks?
To stay safe from this threat, we recommend the following:
- Avoid clicking on suspicious ads or giveaway links, especially from unfamiliar sources or platforms like Telegram, Discord, or YouTube comments.
- Don’t trust login pages that open in full-screen mode. If something feels off, exit full screen and check the URL carefully.
- Use a password manager. These tools won’t auto-fill credentials on fake sites or remote browsers.
- Keep your browser and operating system updated. Consider using Chrome or Firefox for critical logins since they show full-screen warnings that Safari does not.
Final thoughts
Don’t hold your breath waiting for Apple to fix this issue with Safari. In theory, the function is legitimate. However, cybercriminals are getting better at doing exactly this: turning “allowed” elements, features, and content against users.
The weaponization of digital elements and Apple’s own user interface is also not expected to slow down anytime soon. For us, mere mortals, all that’s left to do is keep an eye on the news, learn new cybercriminal techniques, and follow wise privacy and cybersecurity practices every day — one webpage at a time.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Safari is a trademark of Apple Inc.







