It’s been over a year since Russia’s invasion of Ukraine began. Cities have been devastated, international sanctions applied, hundreds of thousands of fighters and civilians on both sides killed or injured, and millions of Ukrainians displaced. However, something has happened that few outsiders expected. Russia has repeatedly been forced to scale back as it faces ongoing strong resistance from Ukrainian forces.
The same war happening on the ground in Ukraine has been ongoing and escalating in cyberspace. And the result has been the same. Russia was expected to create havoc by launching cyberattacks on Ukraine’s digital infrastructure. But it has failed despite its numerous, continual attempts.
Why? Was Ukraine’s cyber defense better than expected? Was Russia’s army of hackers overrated? Is Russia holding back its cyber forces, and if so, why? What are other possible reasons or factors?
To answer these and other questions, we spoke to our very own Moonlock Lab Engineering Manager, who was previously involved in investigating attacks on Ukraine’s critical infrastructure (he asked to remain anonymous). We also reached out to CyberPeace Institute. Here’s what we discovered.
Why Russian cyberattacks have failed to destroy Ukraine
Experts argue that the Russia-Ukraine cyberwar predates the latest invasion. “Over the past 7-8 years, Russia has turned Ukraine’s cyberspace into a battleground for training and honing skills for cyberattacks. But Ukraine did not stand still because each attack allowed information security specialists to develop and improve protection systems,” the Moonlock Lab Engineering Manager said.
Ongoing attacks have allowed Ukraine’s cyber defense to prepare for escalations in cyberwarfare, taking on measures and adopting strategies and technologies. According to our source, these measures included the creation of Security Operation Centers (SOCs) and the use of Managed Security Service Providers (MSSPs). Additionally, cybersecurity experts began training, while organizations implemented measures to increase specialists’ awareness of information security specialties.
The Ukraine government and organizations have been improving the IT infrastructure and bringing it up to international standards and best practices during military operations.
“This was one of the decisive factors of resistance because every specialist in his place realized that it was not only a matter of quality performance of his functional duties. It is a matter of survival, of his loved ones, his family, and the entire nation. In contrast to the Rashists (Russians), whose motivation was only everyday work.”
The engineer also highlighted the importance of historical attacks and how these shaped a strong culture of cyber defense in Ukraine. He provided a chart detailing attacks dating back to May 2014, when the Central Election Commission attack occurred.
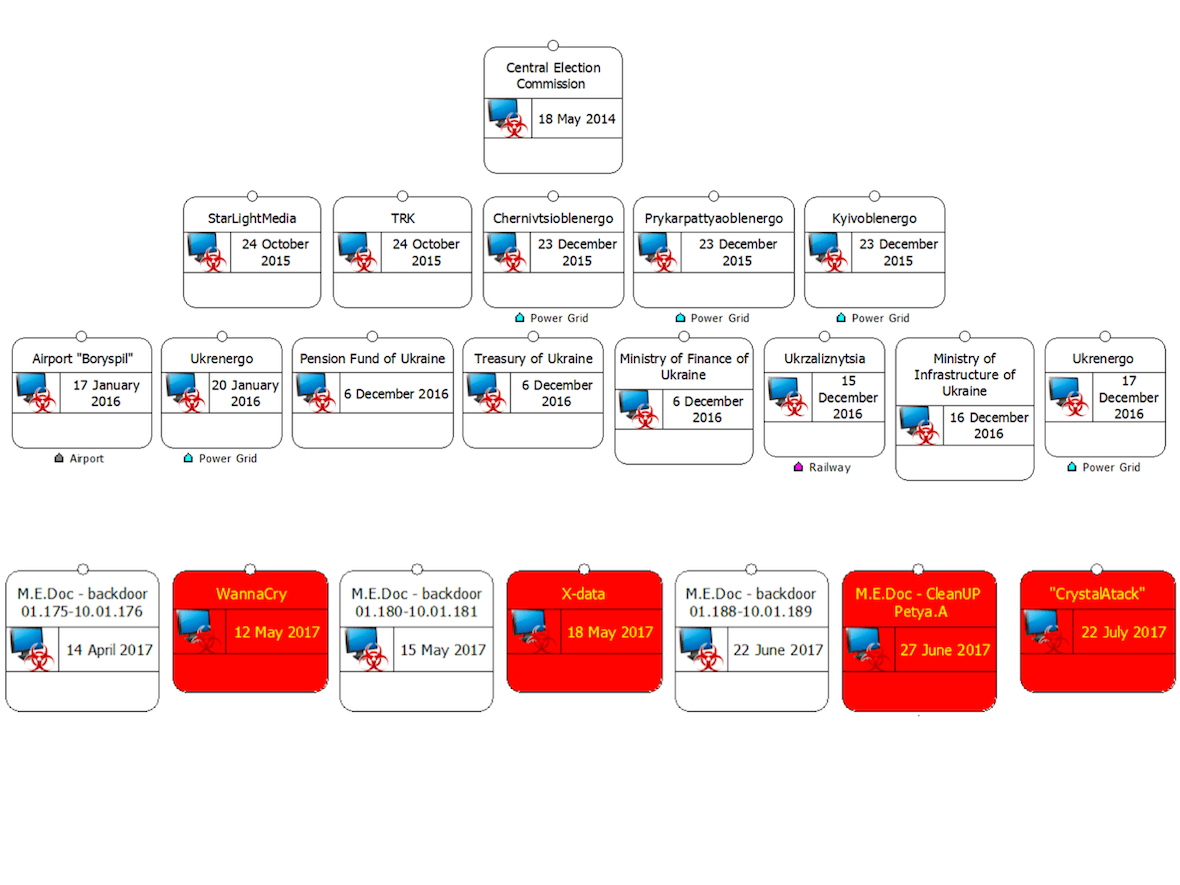
“Each of these cases deserves a separate article,” he said. “The attacks affected many companies, state structures, and ordinary citizens, but what does not kill us makes us stronger.”
Russia’s cyberwarfare techniques
According to the CyberPeace Institute, while cyberattacks during the armed conflict in Ukraine have destroyed data and systems, disrupted critical infrastructure and services, controlled the information space, and exfiltrated significant volumes of data, the hidden impacts on people are the most significant.
A common tactic is the use of wiper malware targeting Ukrainian government entities and other sectors. This malware permanently deletes data or damages systems to the point that they are unrecoverable. “These attacks can have long-lasting effects on organizations if they are unable to retrieve backups or reset systems,” the Institute told Moonlock.
Flooding organizations and businesses with fake traffic in Distributed Denial-of-Service (DDoS) attacks is another highly used cyberattack technique. DDoS has been used, for example, to prevent official communications from being effective and reaching the population or other governments. Strategies include data theft, exfiltration of data, disinformation, and propaganda. In addition, attacks may cause ATM networks to malfunction or target TV stations and social media, in addition to phishing, ransomware, DDoS, and industrial and public service sabotage.
“Russia uses all the above-mentioned,” our source assured us. “In general, there are no specific goals for them — they just try to win in numbers. The NVD database holds 8,051 vulnerabilities published in Q1 of 2022 — about a 25% increase from the same period the year prior. This means that it is possible to cause damage in 8,051 ways by analyzing new vulnerabilities in just one quarter.”
Do Russian cyberattacks affect civilians?
The CyberPeace Institute explained that Russian-supported hackers are not just targeting government departments or operations. They can also affect civilians and extend beyond borders into other countries. Our source at Moonlock Lab explained the holistic vision that cybersecurity experts have in Ukraine. They view cyber protection as a broad concept and consider cyberspace to consist of many elements, including civilians.
“Almost all of these elements are interconnected in one way or another,” he said. “It can be both a large company with a complex IT infrastructure or a small company that is a contractor — and has access to a large company within the supplier chain.”
And civilians are not immune from attacks. “Each person is affected,” he added, “either because they were forced to work remotely from a bomb shelter using their personal laptop or because they were affected by the bombing of peaceful residential areas where Russian invaders repeatedly physically damaged the energy sector.”
Each person is affected — either because they were forced to work remotely from a bomb shelter using their personal laptop, or because they were affected by the bombing of peaceful residential areas where Russian invaders repeatedly physically damaged the energy sector.
The engineer described the need to view cybersecurity “as spread over a large number of computers.” In the end, the security of these computers, in most cases, depends on the human factor.
“There were cases,” he explained, “in the occupied territory — where the aggressor had free access to infrastructure elements to penetrate the network of one or another company — when captured office computers were used, and they tried to gain access to critical systems.”
While many of these attempts were detected and prevented by specialists and government operations, the greatest strength of Ukraine in the cyberwar is attributed to the general population. “In general, Ukrainians are very well-versed in cybersecurity thanks to periodic training and the cybersecurity culture that has been introduced in almost every company over the past 7 to 8 years,” our source said.
While those past 7 to 8 years have been intense, each Russian attack presented an opportunity for Ukrainians to learn, improve their skills, and strengthen their security postures, strategies, policies, talent teams, and technologies.
What Russia’s hackers have been able to accomplish
The CyberPeace Institute Timeline cites 1,408 cyberattacks and operations that have evolved over time since the military invasion of Ukraine. These have impacted 17 different sectors. And momentum is still growing. The Institute adds that there has been a 248% increase in incidents in just one quarter.
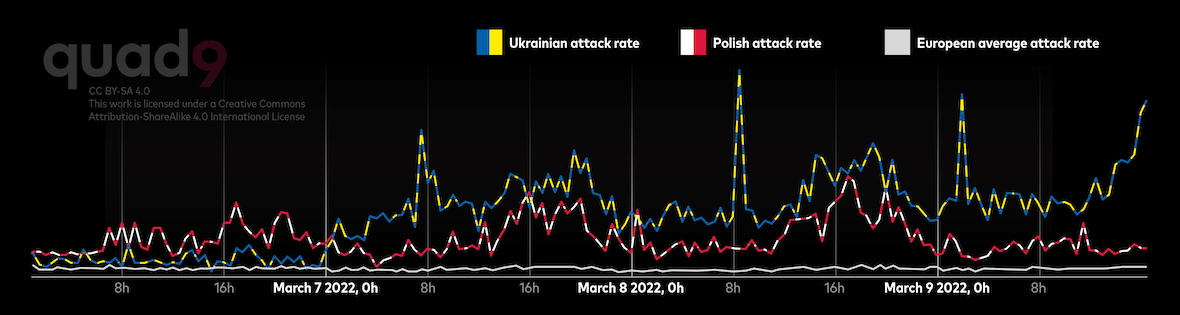
Public administration is the most targeted sector in Ukraine, followed by notable increases in industries like energy and transportation, media, and information and communication technology (ITC).
The European Parliament added that Russian cyberattacks against Ukraine have persisted since Russia’s illegal annexation of Crimea in 2014. These attacks intensified just before the 2022 invasion.
According to the EU Parliament, the most affected sectors include Ukraine’s public, energy, media, financial, business, and nonprofit sectors. Supply chains are also being targeted. “Russian cyber-attacks have undermined the distribution of medicines, food, and relief supplies,” the EU Parliament adds.
Russian cyber-attacks have undermined the distribution of medicines, food, and relief supplies.
Throughout 2022 and 2023, Russia attempted to disable energy systems with cyberattacks. They failed.
“The fact that they resorted to the strategy of bombing energy carriers can be cited as confirmation of this conclusion,” the Moonlock Lab Engineering Manager added. “Russia also tried to disable mobile and landline operators through cyber operations and failed. They have attacked logistics (post services) and caused damage but did not achieve the goal. Everything is working.”
Banks were also attacked. Attempts to steal citizens’ personal data were made, and fake news and fake channels on social networks aimed to scare, demotivate, and weaken the nation’s spirit were created. All of which, with a few minor exceptions, failed.
“They attacked everything they could get their hands on because they had no specific goal — except to cause chaos and panic and break the will of the people of Ukraine. As you can see, they did not succeed,” he concluded.
How Ukraine’s hackers have responded
The CyberPeace Institute said that Ukraine has conducted over 236 cyberattacks and operations against Russia since early 2022. These range from DDoS attacks to data exfiltration, primarily aimed at debilitating Russian attack abilities.
In March 2023, Ukraine’s IT Army ran several operations, including a DDoS attack against the website of a Russian bank. Other Russian sectors targeted besides finance and media include shipping, manufacturing, and Russian alcohol producers and distributors. Similarly, several anonymous and international red hat hackers have supported Ukraine in launching cyberattacks against Russian digital assets.
For example, on April 30, 2022, the Anonymous-affiliated hacker group Network Battalion 65 (NB65) breached a major payment and financial services provider in Russia. NB65 accessed data on over 12.5 million credit cards and 30 million payment records. The company targeted by NB65 was one of the most widely used payment applications in the Russian Federation. That same month, NB65 claimed to have hacked the largest media in Russia, the All-Russia State Television and Radio Broadcasting Company.
However, most of Ukraine’s cyber defense tactics and achievements are safely guarded in secrecy to prevent diminishing its defense capabilities. While Russian state-sponsored hackers are out in the open, Ukraine cybersecurity specialists defend the country and its people and business in the shadows, often leaving no digital footprints, claiming no responsibility, nor revealing the mastery of their skills, strategies, or plans.
Russia’s cyberattacks against the EU, the US, and others
The European Parliament explained that while Ukraine defends and responds, international governments and organizations have stepped up. EU, US, and NATO-led initiatives have been carried out to neutralize cyber threats and protect essential infrastructure. Under these initiatives, the EU activated its Cyber Rapid Response Teams, a project under Permanent Structured Cooperation (PESCO) in the area of security and defense policy.
Additionally, non-government and private organizations support Ukraine in its cyber-resilience efforts. “Since the beginning of the invasion, a significant number of counter-attacks have been launched by independent hackers, affecting the Russian state, security, banking, and media systems,” the EU Parliament explained.
Accenture refers to the internationalization of the Ukraine-Russia cyberwar as a new global “Cold War” in its Global Incident Report. The report reveals that Russia has been actively launching cyberattacks against other countries.
Examples of cyberattacks listed in the Accenture report include DDoS attacks affecting Estonia government sites during a NATO cybersecurity exercise in April 2022, websites in the Czech Republic and Moldova, and BlackBasta ransomware actors posting ads on underground forums to buy access to corporate networks in the US, Canada, the UK, Australia, and New Zealand.
Additionally, ALPHV (a.k.a. BlackCat) ransomware operators targeted other countries. In Latin America, BlackCat targeted countries that explored new fuel and gas suppliers, which would allow them to lessen their dependence on Russian energy. Wind power companies Nordex and Deutsche Windtechnik in Germany also experienced ransomware attacks by Conti28, and Black Basta, respectively.
Cybersecurity officials in the US and other countries warned that “Russia-aligned” threat groups could threaten critical infrastructure in countries around the world. Groups like the pro-Russian hacktivist group Killnet claimed responsibility for DDoS attacks against European countries and threatened further actions against the US, the UK, Germany, Italy, Poland, Romania, Latvia, Estonia, Lithuania, and Ukraine.
Was Russia’s army of hackers overrated?
The reputation of Russia’s army of hackers has been carefully crafted and developed objectively to inspire fear and respect. According to our source at Moonlock Lab, this is a deliberate psychological campaign.
“One should never underestimate the enemy,” he said, “but hackers are not the threat. The damage they can cause is.”
One should never underestimate the enemy, but hackers are not the threat. The damage they can cause is.
While the security expert we spoke to does not underestimate Russian hackers, he emphasized that the main goal of the Kremlin is “to create complete chaos in order to be recognized as worthy of respect.”
“They created a food crisis, an energy crisis, chaos in the information field (bots in every social network that create chaos by misplacing concepts), and then chaos in cyberspace.”
And as the BBC reports, chaos and reputation-building is not the only goal. Money is a primary goal, with 74% of ransomware revenue going to Russia-linked hackers. “There is no big secret about who the Russian cyber army is, either,” our source at Moonlock Lab said. “Almost everything is known. Moreover, the commanders of such units have already fallen under arrest, but for some reason, they managed to avoid responsibility.”
While Russia’s hacking capabilities weren’t underestimated, Ukraine’s defense capabilities may have been. Not only have Ukrainian cybersecurity experts mastered new technologies and developed Security Operation Centers (SOCs), but they have formed a significant pool of skilled, talented people behind the monitors and keyboards.
“Exactly how many there are, I won’t say,” said our source. “But I know for sure that every specialist in his place is a real weapon against Russian cyber aggression.”