Social engineering is a manipulative technique that cybercriminals and hackers use to gain access to systems, information, or credentials. It has been a major threat since the earliest days of the internet, and it continues to be a significant danger to individuals online. Use this guide to learn all about social engineering, what it is, what the common types are, how to spot attacks, and what to do to protect yourself.
What is social engineering? The definition and meaning
The easiest way to define social engineering is that it’s a method of executing malicious attacks using psychological manipulation. The bad actor uses techniques to trick the victim into trusting them or believing they are someone else. Once they gain the victim’s trust, they ask for money, information, or credentials to break into other systems.
This process works because the perpetrator gathers information on the victim to make it seem like they already know them. Then, they reach out via email or text and start a conversation. Many social engineering attacks require multiple steps, and the bad actor takes time to gain trust so that when they ask for credentials, the victim doesn’t think twice.
Learning to stay safe online?
Notorious social engineering examples
The worst part of social engineering attacks is that they take advantage of a human being’s natural inclination to trust others.
Social engineering is not new, and it takes many forms. The following are a few notable examples.
2005–2006 HP executives scandal
One of the most notorious examples of a social engineering attack is when Hewlett-Packard (HP) management executives hired private investigators to collect board members’ names and partial SSNs to access their AT&T phone records illegally. They were convinced someone was leaking information. However, after the scandal broke in the news, HP execs denied involvement. The incident resulted in multiple resignations.
The Nigerian prince
By now, most people have, at one time or another, received an email claiming to be from a Nigerian prince begging for help to get his vast fortune out of the country. These attacks date back to 2007. Typically, the email asks for upfront cash to pay fees and government bribes, for which you will be handsomely rewarded. Victims, of course, never see a dime.
2015 Ubiquiti Networks (UN)
Another notorious incident was when Ubiquiti Networks, a network equipment manufacturer, fell prey to a “business email compromise” scam when a threat actor emailed finance employees claiming to be a top executive and ordered them to wire transfer money to “third parties.” Unfortunately, the duped employees complied. Ubiquiti Networks never confirmed how much money was stolen.
Common types of social engineering attacks
Social engineering is a broad term covering a wide range of attacks. Due to the diversity, you must become familiar with each type to avoid becoming a victim yourself. Some of the most common social engineering attack types include the following.
A friend’s email
Hackers often break into people’s email accounts and then use the compromised accounts to send sneaky emails to everyone on their contact lists. Because these emails appear to come from a friend, you are more likely to trust them and act accordingly.
An authority figure
As evidenced in the UN example above, cybercriminals often pretend to be a person of authority and demand that someone beneath them provide credentials, money, or other personal information. Many phishing emails use this technique, pretending to be banks, credit card companies, government authorities, and others in power to intimidate the user into providing something. They often use scare tactics to ensure compliance.
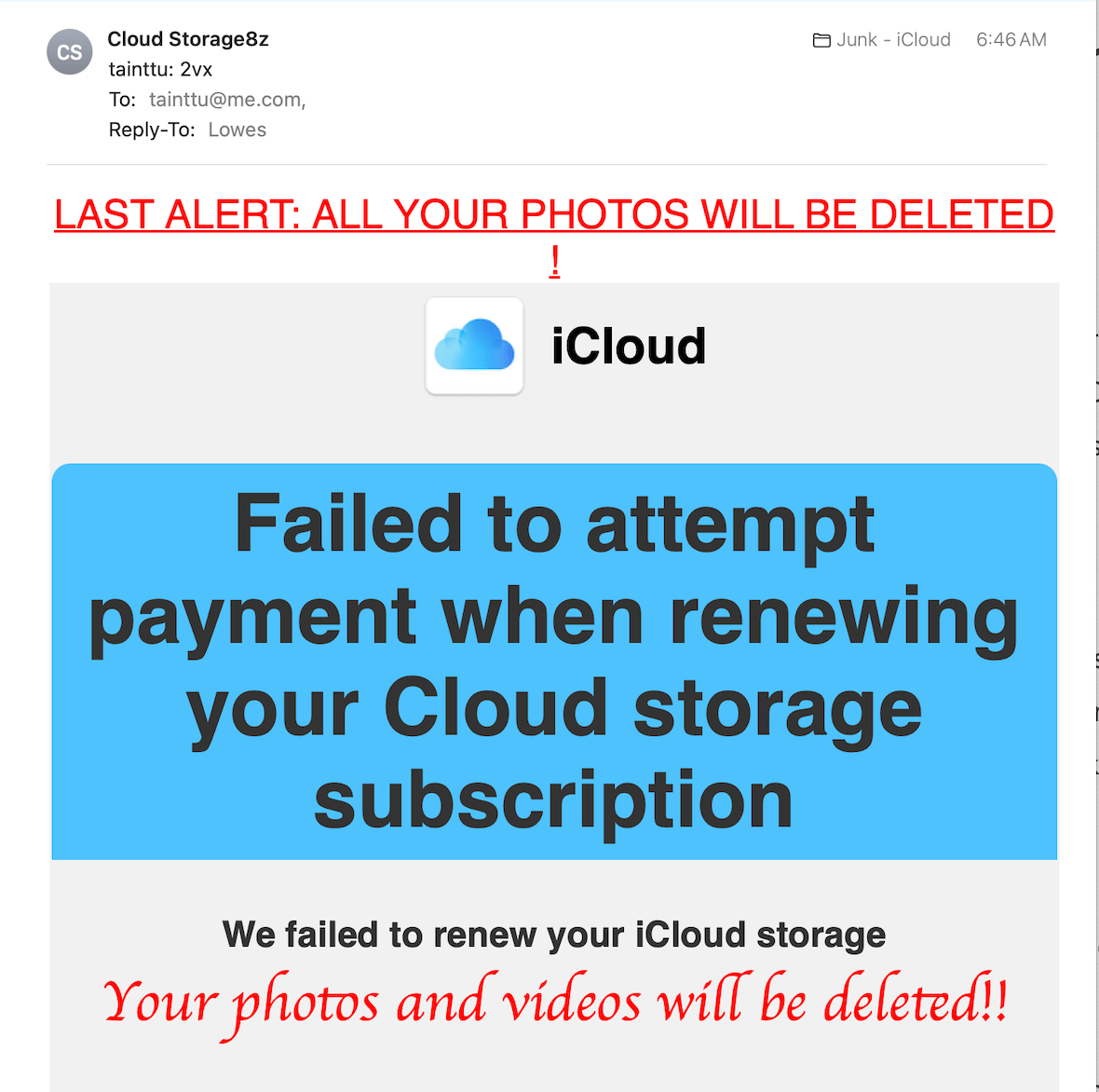
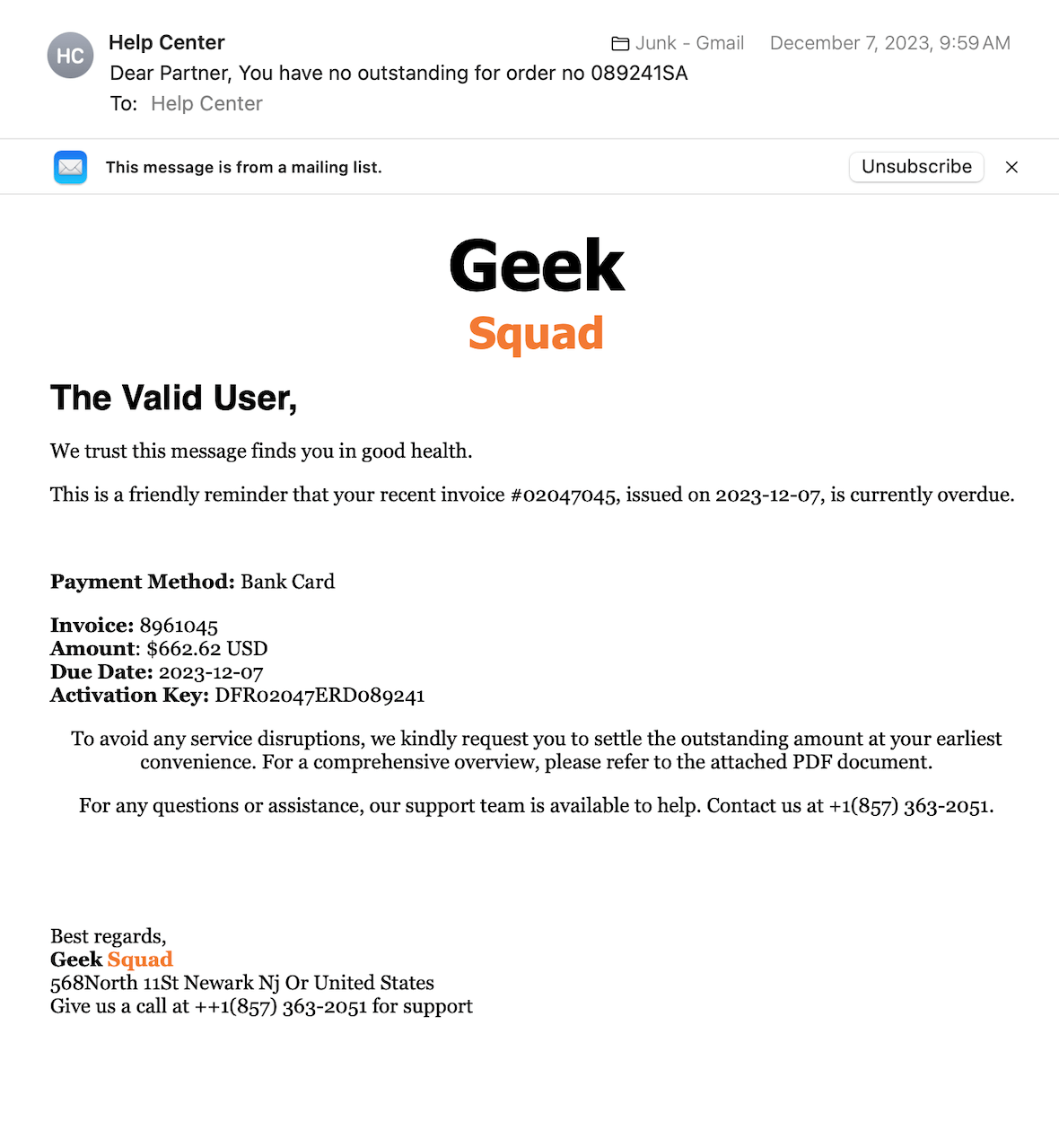
Answering a question you didn’t ask
Many of us receive suspicious emails claiming we asked a question, and the email is in response to that. Malicious perpetrators may pretend to be Microsoft, Apple, or the Geek Squad reaching out to provide you support for an inquiry, but you never made one. They are banking on the assumption that most people have some technical problem and will jump at the chance of free help. However, they will ask for login passwords before offering their assistance, which, of course, is fake. Sometimes, they insinuate that your antivirus or tech help account is about to expire and you must act fast.
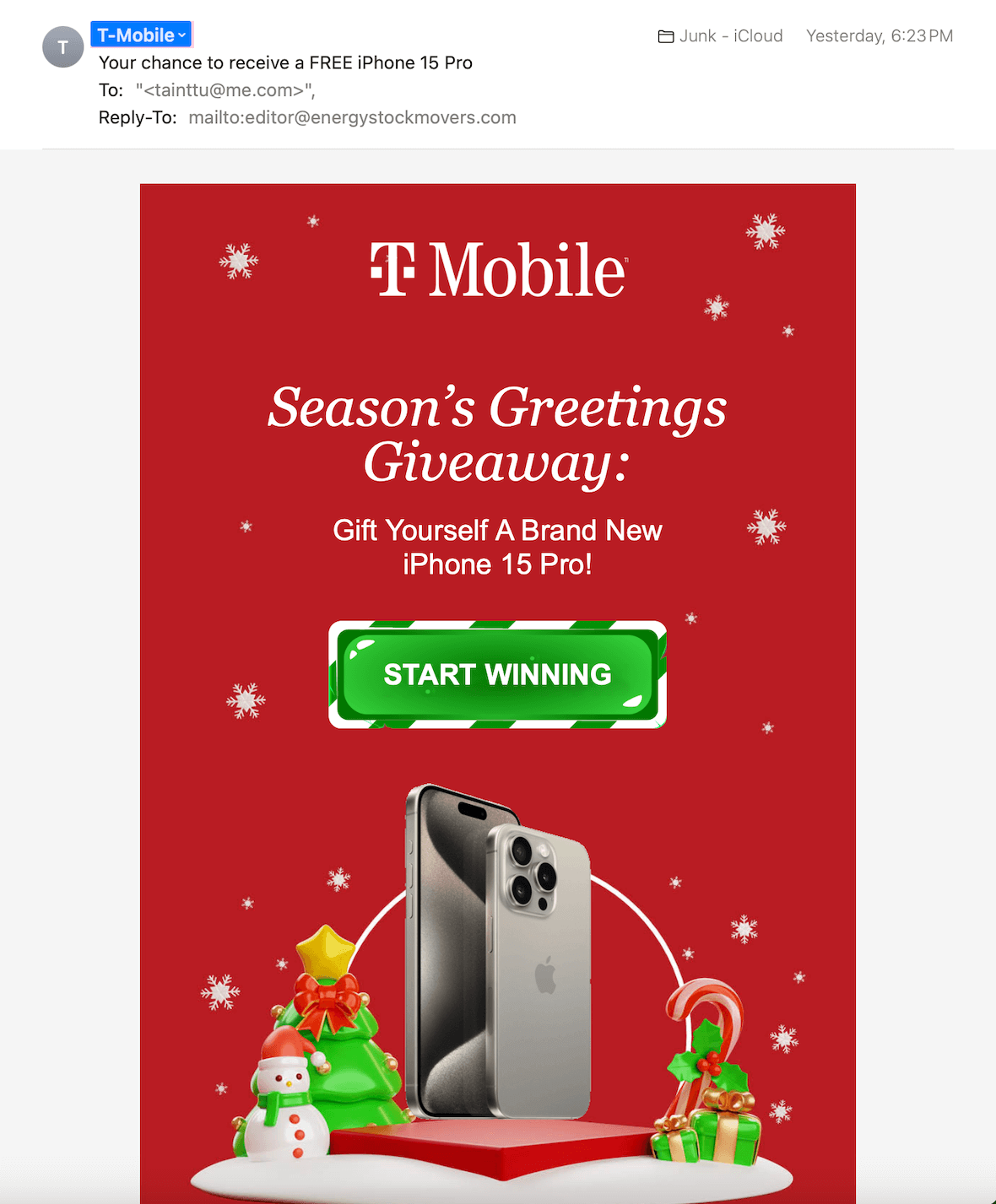
Baiting
Other types of attacks bait the victim with the promise of winning something or getting free downloads. They dangle the prize, waiting for victims to take the bait, and then they pounce. Typically, these attacks result in malware or ransomware installed on the user’s device.
These are just a few examples of social engineering in cybersecurity.
How to spot a social engineering attack
The first rule of cybersecurity is to never take anything at face value. There are many ways to trick people online, and you never really know who you are engaging with. Here are some signs to help you identify social engineering attacks.
Contains a link or download
If the email or text in question contains a link and the message urges you to click it and log on, don’t do it. These links are often designed to infect your device. Hold your mouse over the link to see where the URL leads. Instead of going to a legitimate site, you will see that it redirects you to a completely different location. That is a big red flag.
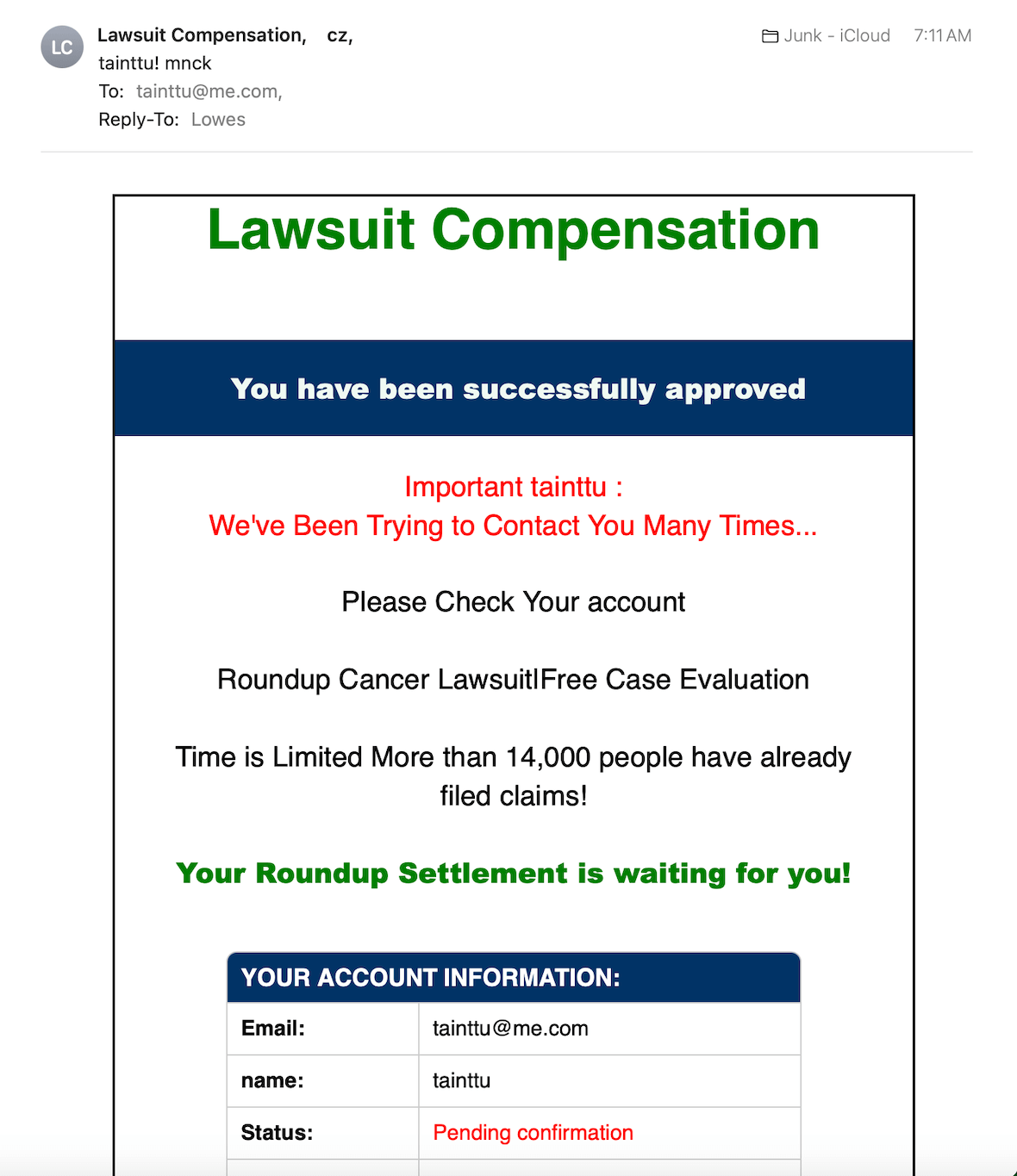
Has a sense of urgency
Most social engineering attacks have a sense of urgency. They try to scare you by implying that your account was hacked or something is wrong, hoping that you will act quickly without thinking. If you receive a frantic email about some urgent issue, stop, take time to investigate, and don’t do anything quickly.
Asks for money
Many social engineering attacks will ask you to wire money, purchase gift cards, send cryptocurrency to help someone in need, or pay off a debt. Legitimate companies and government agencies do not ask you to pay for something online with gift cards, cryptocurrency, or other forms of electronic money. Never donate or pay online unless you are absolutely sure of who you are dealing with.
Mimics verification emails
Information is precious these days. Hackers will do anything to get their hands on your login information. Often, they send text messages or emails requesting that you “verify” your login through a link. The problem is that instead of logging on to the actual website, you are on the hacker’s site, giving them your credentials. Always check where a link leads before clicking on it. Call the actual company to verify that something is real before you take any action.
Foreign individuals and organizations perpetrate many of these attacks. Often, you can tell just by the poor grammar, incorrect punctuation, broken English, or odd writing style that an email or message didn’t come from a legitimate source.
Armed with this information, you should be able to easily spot a social engineering attack and avoid any nasty consequences. Always be on the lookout for cybersecurity attacks and those who want to take advantage of you.







