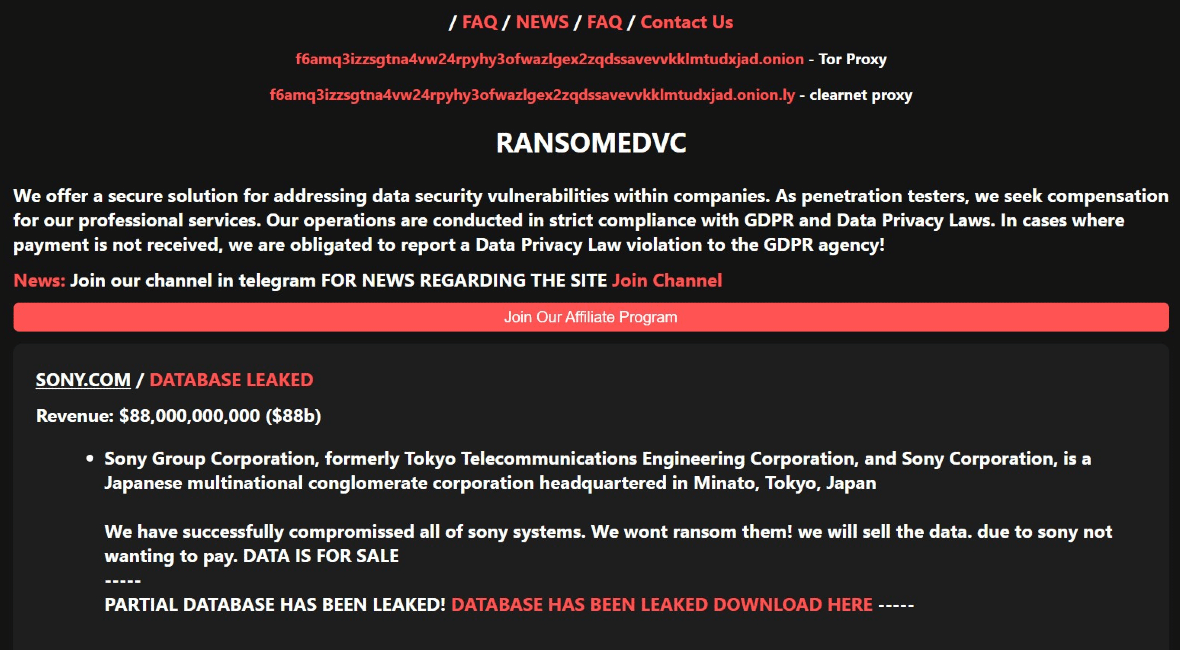
Sony is investigating an alleged full system breach claimed by a ransomware group new to the cybercriminal scene. On September 25, Cybersecurity Connect reported that the ransomware newcomer group RansomedVC claimed online to “have successfully compromised” all Sony systems. The group added that they would not be asking for ransom because Sony was not willing to pay. “DATA IS FOR SALE,” the group added on its post available online.
While it is still too early in the game to understand exactly what is happening or how this will affect users or other parties, several key facts have been made public. Additionally, Sony users, employees, and other parties can take certain actions if they feel the need to protect themselves.
What happened with the 2023 Sony hack?
If RansomedVC’s claims are true, the damage of the Sony breach and its consequences due to data leaks could be significant. Sony offers a wide range of services and products, including financial services. Its biggest money maker is PlayStation, which currently has more than 108 million active monthly users. Additionally, the company employs about 113,000 people around the world.
As of September 27, Sony was still being cautious about its response. The company issued a brief statement to the press signaling that it was taking action but did not reveal much.
“We are currently investigating the situation, and we have no further comment at this time,” said Sony’s press statement, which was echoed by the press around the world.
The plot thickens and gets stranger by the minute
RansomedVC’s post assures they are selling “all” of Sony’s systems. However, their proof-of-hack files appear small. The group added links online that include fewer than 6,000 files. Cybersecurity experts agree that if they had breached all of Sony’s systems, the files would be much more abundant.
Among the files RansomedVC leaked is a PowerPoint presentation that allegedly shows how they hacked Sony. BleepingComputer examined the proof-of-hack data and described it as “minuscule, about 2 MB — comprising a PowerPoint presentation, some Java source code files, Eclipse IDE screenshots, and other assets”.
BleepingComputer states that RansomedVC claimed to have stolen 260 GB of data during the attack and was asking $2.5 million for it.
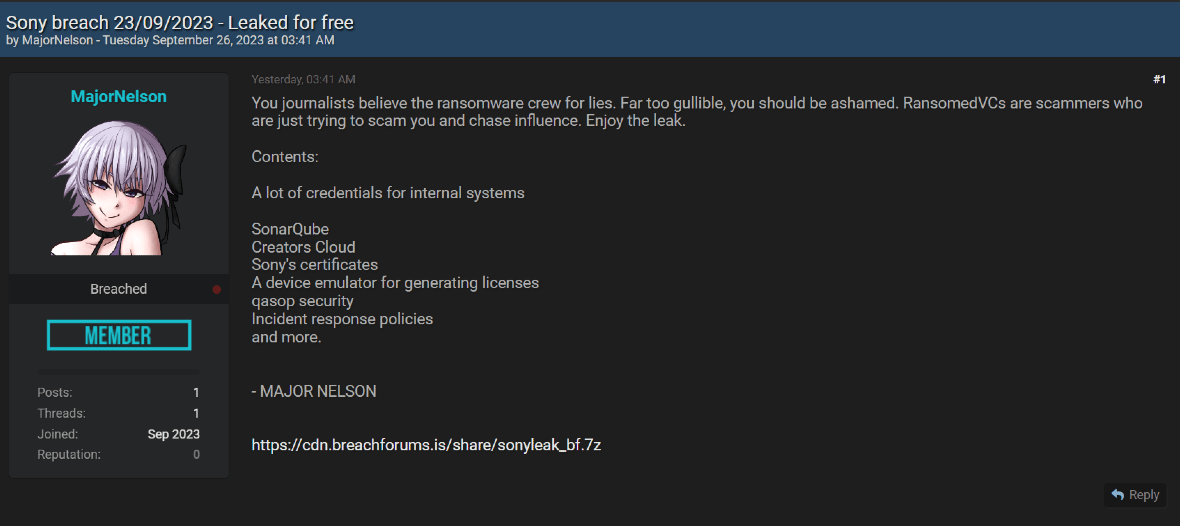
To make matters even more confusing, a hacker called MajorNelson jumped into the controversy, adding fuel to the fire. MajorNelson leaked a 2.4 GB compressed archive, which contains 3.14 GB of uncompressed data. This user claims that the data belongs to Sony. They made the file available to anyone for free through BreachForums.
MajorNelson said in its post that RansomedVC “are scammers who are just trying to scam you and chase influence.”
“You journalists believe the ransomware crew for lies. Far too gullible, you should be ashamed,” MajorNelson’s post reads. According to BleepingComputer, the MajorNelson leak file contains all the files that the RansomedVC smaller sample has.
RansomedVC is also staying busy. One day after claiming it hacked Sony, the group released a new post claiming it had breached Nippon Telegraph and Telephone Corporation (NTT), another major company based in Japan. NTT is a leader in telecommunications and provides mobile, internet, and other services around the world.
What Sony data may have been stolen?
At this point, no one has been able to confirm the veracity of the allegations. And because Sony’s official statement has yet to be released, determining the nature of the compromised data is tricky.
If we are to believe that RansomedVC has stolen all of Sony’s system data, the impact would be severe. Sony’s systems and data include personal user data, employee data, sensitive business data, and business partners’ data.
However, as we have already mentioned, RansomedVC´s proof-of-hack files and the data leaked by MajorNelson do not seem to reveal a significant amount of sensitive business data or user data compromised. Additionally, the leaked samples contain credentials for internal systems used by Sony, including:
- SonarQube: An open-source platform used for code quality reviews.
- Creators’ Cloud: A platform that gives any Sony camera owner access to a free plan used to support creative images and videos.
Other files in the sample include Sony’s certificates, the company’s incident response policies, and more.
It is worth noting that this event has brought back memories of the 2011 Sony PlayStation breach. At that time, 77 million users were affected.
What can users do when they are affected by data breaches and leaks?
Until the Sony investigation is better understood, the real extent of the damage is unknown. However, Sony users, or anyone who believes they might be affected by this incident, can take several steps to increase their security and privacy.
When affected by a data breach and leak:
Stay on top of the event: Keep up to date with news of the breach. Pay special attention to official statements from companies affected and cybersecurity experts. You can follow the news sources you trust on social media.
Change your password: Log into the accounts that have been affected by the breach and change your password immediately. Data leaks may include your authentication data, but if the password is no longer valid, your account should be safe.
Change your security settings: Once you have changed your password, make sure the security settings have not been modified. Ensure that your recovery phone or email is up to date. Also, enable security notifications so that you’ll be warned if someone tries to access your account.
Enable MFA: If you haven’t enabled multi-factor authentication (MFA) yet, now is the time to do so. Most services give users the option to use biometrics such as fingerprint ID, FaceID, one-time passcodes, or authentication apps.
Back up your data: A lot of information on your accounts is stored on the cloud. It’s a good idea to back it all up.
Pause and monitor your financials: Whether you linked your bank account, debit or credit card, or even an e-wallet to a possibly affected account, make sure you hit pause and keep an eye on any suspicious spending.
Watch your email, phone, SMS, and social media: If criminals get a hold of your personal data, they might use it to launch phishing campaigns. Monitor your communication channels and be on the lookout for any suspicious messages.
What happens next?
The Sony 2023 alleged full data breach is clearly in its early stages. The next days, weeks, or even months could bring us more important and relevant news. And hopefully, we’ll gain some clarification to reduce the confusion that is being generated.
We sincerely hope that Sony’s breach does not result in massive data leaks or cause damage. At this time, if you believe you may be affected, taking the steps above is the best advice we can offer.






