On September 23, the UK’s National Crime Agency (NCA) detained a 40-year-old man on suspicion of Computer Misuse Act offences following a cyberattack that left dozens of flights cancelled or delayed across Europe.
Investigations into the incident are ongoing. What we do know is that a cyberattack targeted the IT automated check-in systems of Collins Aerospace. The security incident led to cancellations and delays across several major European airports, including Brussels, Berlin, and London’s Heathrow.
In this report, we talk to Eray Altili, Cyber Security Architect at World Bank, and other experts to get their insight on the issue, as well as how ransomware increasingly affects the average traveler every day, and what can be done.
A knocked-offline boarding system grounds flights across Europe
On September 21, Security Week reported that starting on late Friday, airports in Berlin, Brussels, and London were hit by disruptions. The IT electronic systems responsible for check-in were affected. This left “airline staffers trying options like handwriting boarding passes or using backup laptops,” the media reported.

Many industries, including energy, manufacturing, water, and aviation, operate IT-OT systems. You can think of IT-OT systems as the combination of IT — the digital brains that handle data, emails, and business systems — and OT — the actual real-world physical hardware and the muscles that keep planes flying, factories running, water flowing, or power grids humming.
Due to the interconnected nature of IT and OT systems, when a threat actor deploys a cyberattack against a non-flight-related system like e-boarding passes, flights may be grounded.
Why would actors threaten flights?
“The attackers likely aimed for financial gain through ransom demands,” Altili from the World Bank told us.
The attackers likely aimed for financial gain through ransom demands.
Eray Altili, Cybersecurity Architect at World Bank
“They may also have wanted to create disruption and erode confidence in critical infrastructure,” he added.
What we know about the cybersecurity incident that grounded airplanes in the EU
Because this is an ongoing investigation, authorities have not yet released conclusions or statements that clarify exactly what happened.
However, there are some facts in the case that are in the public domain. These are:
- CNN reports that the UK’s National Crime Agency (NCA) arrested a man on September 23 in West Sussex, England, on suspicion of offenses under the Computer Misuse Act.
- Paul Foster, head of the NCA’s National Cyber Crime Unit, said in a statement that “the investigation is at an early stage and remains ongoing.”
- Media outlets reported that authorities have not determined whether Russia or any other nation-state played any role in the incident.
- The European Union Agency for Cybersecurity (ENISA) confirmed that this incident was a ransomware attack, Reuters reported.
- In ransomware, hackers lock data and systems and demand payment for their release.
- Ransomware motives are usually financial but can also be used to disrupt critical infrastructure.
- The cyberattack targeted Collins Aerospace.
- Collins Aerospace is a US aviation and defense technology company.
- Collins Aerospace is one of the world’s largest suppliers of aerospace and defense products.
- Collins Aerospace provides check-in/boarding/baggage/passenger processing software (for example, the MUSE system) used by airlines at airports, including London Heathrow, Berlin, Brussels, and Dublin.
- The attack left automated check-in and baggage drop systems nonfunctional, forcing airports to revert to manual procedures. This led to significant flight delays and cancellations, affecting thousands of passengers and highlighting the risks in the aviation industry’s supply chain.
“The attack targeted Collins Aerospace’s MUSE (Multi-User System Environment) software, used by many airlines for check-in and boarding at airports,” Altili from the World Bank told us.
What the attack says about aviation infrastructure
Dependence on a single vendor for essential operations is a vulnerability, Altili said. “The attackers exploited weaknesses in the third-party supply chain, showing that the real issue lies in vendor ecosystem security rather than direct airport infrastructure,” he added.
The attackers exploited weaknesses in the third-party supply chain, showing that the real issue lies in vendor ecosystem security rather than direct airport infrastructure.
Eray Altili, Cybersecurity Architect at World Bank
Although no specific group has taken credit, it is likely that a state-sponsored hacking group is behind the attack, Altili said. Previous cyberattacks on critical infrastructure have often been linked to state actors or criminal organizations seeking to extort money, he added.
“This attack serves as a serious warning about both financial and strategic threats to critical aviation infrastructure,” said Altili. “It stresses the need to improve cybersecurity across supply chains and operational vendors.”
How airlines can mitigate IT-OT flight delays and cancellations
Delayed or cancelled flights not only mean millions of dollars in losses for the airliners, but they also affect passengers on a wider scale.
Naturally, travelers affected by this incident and other similar incidents impacting aviation would like to see some action on the part of airline companies. We asked Altili what companies and third-party providers should do to mitigate these types of cyberattacks.
“Airports can lower the risk of ransomware attacks by combining technical, operational, and collaborative security measures,” Altili said.
What is network segmentation, and how can it benefit the aviation industry and travelers?
Altili explained that the best technical and operational defenses include network segmentation, a technology concept that implies the subdivision and isolation of systems.
“By isolating critical operational systems, like check-in, baggage, air traffic control, from less critical networks using micro-segmentation and VLANs, airliners can slow or block attackers if a breach happens,” said Altili.
Network segmentation must be combined with zero-trust architectures. “Treat every user, device, and service as potentially compromised,” Altili said.
Redundancy combined with network segmentation can help airline companies, airports, and third-party software providers mitigate the threat of ransomware and other disruptions.
It is worth noting that most of the cyberattacks that grounded airplanes in the past year targeted e-boarding systems or check-in electronic platforms and did not affect aviation OT integrity or security.
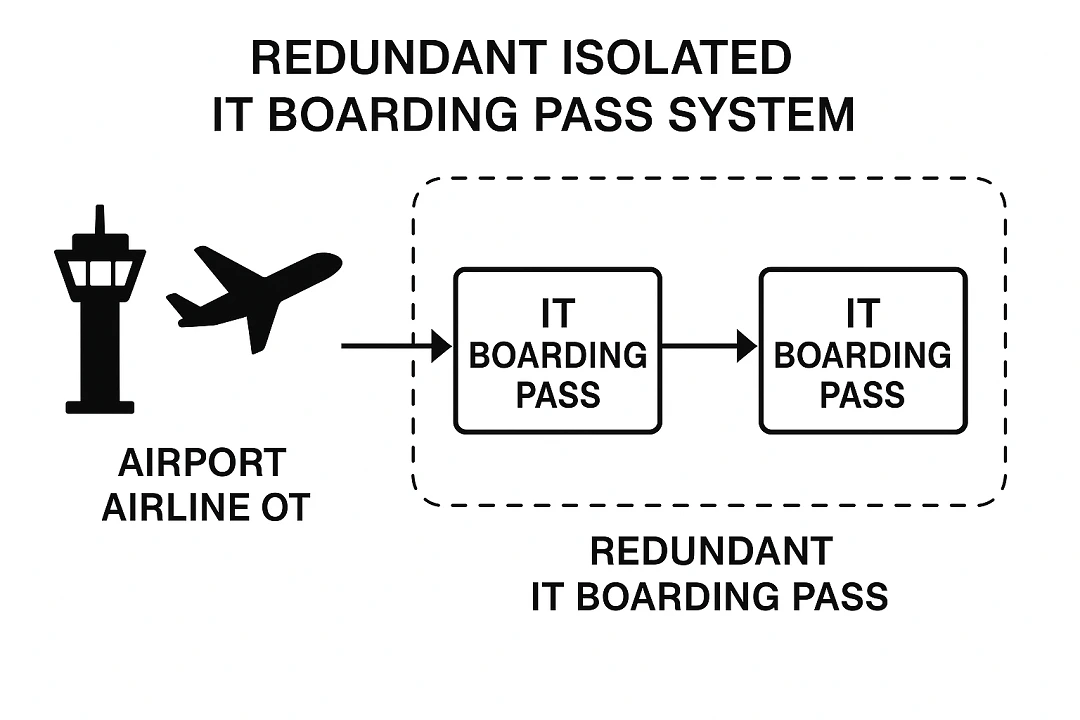
The image above, generated by ChatGPT upon request, shows how redundancy and network segmentation would add a layer of security, much needed by travelers in this day and age.
“Flights are being grounded because e-boarding relies on a single synchronous decision node, creating a systemic choke point, concentrated failure paths, and amplified attacker ROI,” Nic Adams, Co-Founder and CEO of 0rcus, told us. “Distribute verification across independent redundant channels and enforce strict telemetry contracts to neutralize attacker leverage.”
“Segment boarding and add redundant verification lanes, and you remove the single choke point attackers exploit,” he added.
Zero-trust and zero-day vulnerabilities are important when flying, too
Threat actors will often leverage the release of new software, which industries like aviation release to modernize operations. New software is great, but it’s not without risks. This is where zero-day vulnerabilities come in.
A zero-day vulnerability is simply a weakness found in new software, unknown to the vendor. These vulnerabilities are like holes in a dam that are constantly patched up by security developers through security updates.
This is why updating all systems, including third-party software, with the latest security patches to fix vulnerabilities that ransomware may exploit is important, Altili explained.
Zero trust is not a once-and-done process. It requires continuous authentication, strong identity controls, and micro-segmentation across airport systems, Altili explained.
Finally, Altili said airlines and partners can use advanced threat detection technologies, which today are powered by AI and can autonomously monitor networks and identify and respond to suspicious activities in real time, covering IT and OT systems alike.
Things travelers can look into when booking a flight
As consumers, travelers can take certain steps when booking flights to avoid being stuck at the airport as much as possible. This includes checking out what airports and airlines offer and how they manage important things like cancellations and your personal data.
Some important elements travelers can look into when booking a ticket include:
- Incident response and disaster recovery plans: Make sure the airline has detailed crisis communication strategies, has manual fallback procedures, and conducts regular disaster recovery drills to keep operations running during a cyber incident.
- Data policies: Take note of how your airline manages its own data and what steps it takes to protect your personal information.
- Employee training: Check if the airline provides regular cybersecurity awareness programs and phishing simulations to help staff spot and report threats.
- Transparency and communication: See how clearly the airline communicates with passengers during delays, cancellations, or cyber incidents.
- Third-party security: Find out if your airline and airport carefully vet and monitor the security of their technology vendors, such as check-in software providers.
- Privacy and data sharing: Review how your data is shared with booking platforms, security agencies, or marketing partners, and whether you can control these options.
- Regulatory compliance: Confirm whether the airline follows aviation cybersecurity standards and complies with local and international data protection rules.
- Cancellation and refund policies: Look into how the airline handles cancelled flights — do they offer clear refund options, rebooking support, and timely updates, especially during IT or cyber disruptions?
- Cybersecurity commitment: Check if the airline or airport publicly shares its cybersecurity policies, invests in strong protections, and demonstrates a commitment to keeping passenger data and operations safe.
The next time you book a flight, make sure your airline and airport provide these services.
What else can airports do for travelers in the era of ransomware-disrupted flights?
We asked experts what airports can do, as flight cancellations driven by ransomware attacks seem to have become the new normal.

“Airports can be transparent about any situation and inform what steps have been taken,” Fergal Glynn, AI Security Advocate and Chief Marketing Officer at Mindgard, told us.
“They can also make the IT system defenses stronger and run regular cybersecurity drills while having manual backup processes ready. Prompt communication and transparent action can help restore traveler confidence.”
Glynn added that this incident shows just how much airports rely on technology.
“It reminds us that even non-physical attacks can cause chaos, and both airports and travelers should be ready for these possibilities,” he said.
Final thoughts
While cybersecurity incidents that disrupt airport activity are high-level security concerns for governments, they are also a headache for travelers. When this happens, travelers by the thousands are faced with uncertainty and forced to reschedule.
Let’s face it. Being stuck watching the airport ticker go red with “Cancelled” or “Delayed” is no fun for anyone. Given that ransomware gangs and threat actors seem to have no plans to stop targeting airline systems, it’s critical that the aviation sector step up and update systems with simple but effective cybersecurity measures that will benefit the industry and customers.






