In social engineering and phishing, credibility is everything for the attackers. Impersonating known brands and familiar contacts is a common tactic. Attackers also offer up malicious and fake links that look like the real thing.
However, a new security incident that targeted the founder of the Hack Club — a global nonprofit organization focused on technology for teenagers — reveals that anyone, even the most tech-savvy developers, can fall for social engineering tricks. The tactic, if replicated by criminal gangs, can be used to go after any Google Workspace and Gmail users.
Let’s dive straight into this incident.
The founder of the Hack Club, a global tech NGO for teens, was almost pwned
Recently, Zach Latta, the founder of the Hack Club, posted on GitHub his own personal experience when at least 2 people attempted to break into his Google Workspace account.
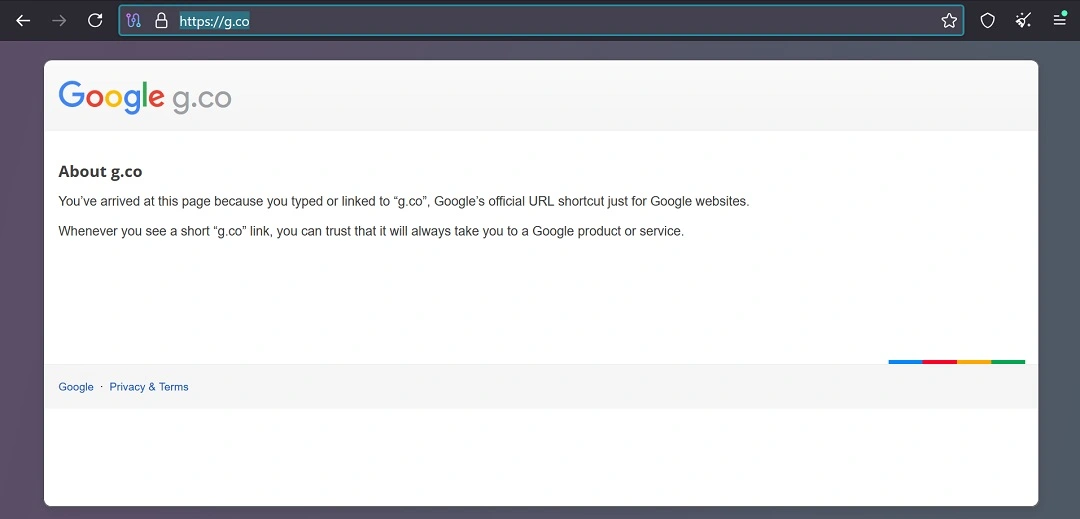
Latta was called from a Google web-listed phone (spoofed). The caller claimed, “Your account has been blocked due to suspicious activity.” Latta was also redirected to malicious g.co sites that abused the trust of Google. G.co is the legitimate top-level domain URL shortcut for Google.
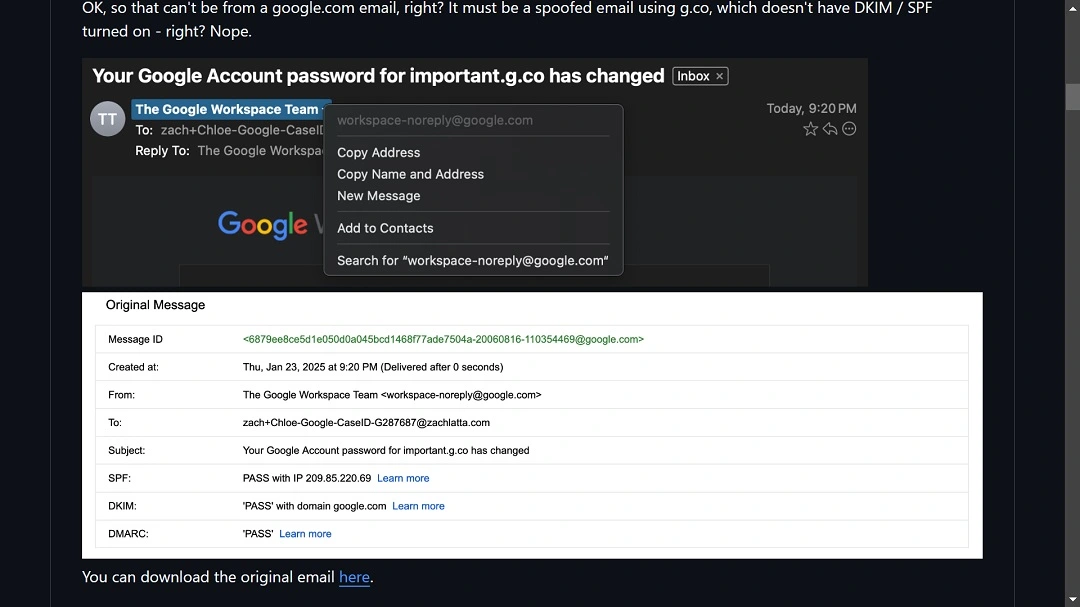
During the call, Latta also received fake emails that originated from legitimate Google Workspace addresses. Latta is a developer who has been dedicated to coding and computers since he was 15. Naturally, Latta was suspicious throughout the entire call.
Latta inquired for more information. Latta asked questions to attempt to verify that it was, in fact, Google Workspace security support he was speaking to.
By the end of the call, Latta was convinced that the call was the “most sophisticated phishing technique” he had ever seen. He recorded the last seven minutes of the call, available here.
Zach Latta may have been exclusively targeted due to his profession and links to the Hack Club. The Hack Club has been growing internationally, little by little, over the years. Today, it has hundreds of thousands of teens from different countries working to make “a difference with coding” in real-world projects. NGOs and hacker organizations are common cybercriminal targets.
But could this attack and technique be part of a wider trend?
Google responds to the phishing attempt against Zach Latta
Because Latta’s GitHub post reached international media, Google came out to address the issue.
“We’ve suspended the account behind this scam, which abused an unverified Workspace account to send these misleading emails,” a Google spokesperson told The Register.
Google claims that they have not seen evidence that this is a wide-scale tactic. They added that they are “hardening our defenses against abusers leveraging g.co references at sign-up to further protect users.”
However, Latta’s Hack Club teens and Latta himself have other thoughts. On GitHub, Hack Clubbers (those who belong to the Hack Club) said:
“We have determined that this is almost definitely a bug in Google Workspace where you can create a new Workspace with any g.co subdomain and get it to send some emails without verifying that you own the domain.”
How the Google Workspace phishing scam call works
On GitHub, developers joked with Latta that the first telltale sign was receiving a call from Google at all, because the company is known for its “legendary lack of customer support.” But, jokes aside, it’s easy to analyze scams after they happen. Living through them is a completely different experience.
Let’s look at how this scam works, why it is different from others, and why it could increase the attack success rate if this technique were applied in a large-scale cyber attack.
A breakdown of the Google Workspace phishing scam
Latta’s detailed account allows us to summarize the attack technique in 5 steps:
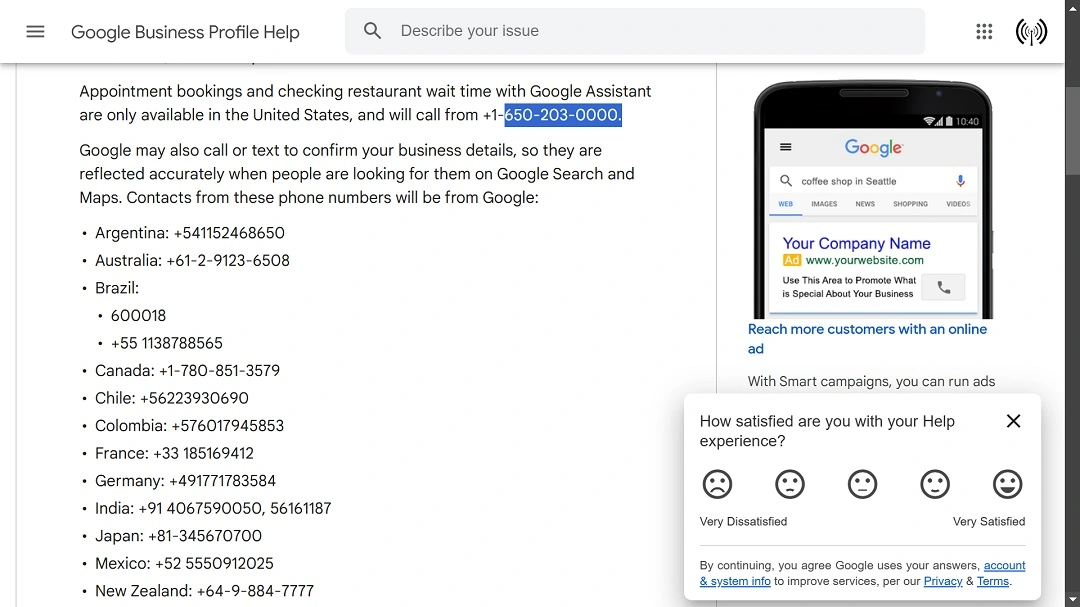
- Your phone rings: Initial contact by a convincing caller is made with the victim. The call registers as a legitimate Google number that has been spoofed. In this case, the number is 650-203-0000. The number is listed on Google Assistant Help. The caller is fluent in English and impersonates a Google Workspace engineer with skills.
- The caller presents verifiable information: The caller informs the victim that a security breach has happened in their Google Workspace or Gmail account and offers guidance on how to recover the account immediately. To make the claim more credible, the caller sends an email that includes a link to what appears to be an official Google website address (in this case, important[.g].co) and adds a fake but legitimate-sounding case number to the security incident.
- You are asked if you want to recover your account: The caller asks the victim to validate their identity to swiftly recover the account using Authentic Google Links.
- A fake check is made: The caller then engages in a fake, guided “Security Check” to regain control of the supposedly breached account. What they are really doing is forcing the victim to give away data like MFA notifications that the victim receives on their phone. Following this guidance will lead to your account being breached and taken over.
- Your phone rings again, and this time it’s the “manager”: If, for any reason, the victim is not convinced, a fake “Google Manager” may call back to attempt, once again, to trick the victim into giving away security popup notification data or 2FA and MFA codes.
How to respond to a phishing attempt
In retrospect, it may seem clear that there are several red flags in each of the steps above. But as Latta explained in his detailed account of the phishing attempt, living through these sophisticated phishing attempts is tricky.
Latta asked the right questions, checked URLs, checked email addresses, and even looked up suspicious IP logins on his Google Workspace account. However, despite his instincts telling him that something was off, everything he looked up to verify the caller linked back to official and legitimate Google resources.
Latta also faced another challenge. He had to conduct all these verifications while on the phone with a talented con — a convincing but fake Google Workspace engineer creating a sense of urgency.
Headspace, stress, and environment play very important roles in phishing.
How to keep your Gmail and Google Workspace safe from this threat
Some of the advice we usually give out to users to protect themselves against phishing is actually a bit outdated for this new technique. Usually, you can verify the authenticity of a caller through the phone number ID, email address, and URLs. In this case, however, all of that goes out the window.
As mentioned, the phone is Google’s, but it’s spoofed. And the email and links stand solid on initial checks. However, even with little time to do verifications when pressured by a caller who says your account has been hacked, there is still plenty you can do.
Number one, if a caller is claiming that your account has been compromised and is pressuring you to take action, hang up the phone, put the phone in silent mode, and calmly verify things on your end. The more you speak with a professional phishing actor, the better.
After hanging up, try to log in to your Google Workspace or Gmail account. If you can’t log in, follow these official steps. If you can log in, immediately change your password, enable MFA, and add passkeys or biometrics to your account.
Additionally, remember that Google, like most big tech companies, never calls users on their phones to offer instant recovery of email accounts — or any other resources, for that matter. This is as suspicious as someone calling from your bank asking for your ATM PIN.
It’s also important to trust your instincts. If something that has never happened before interrupts your day, like a call out of the blue from a Google Workspace engineer that involves codes, emails, URLs, and links you have never interacted with, you are likely being scammed.
Even when everything you verify appears to be legit, it may not be.
Final thoughts
Whether this technique is a new trend that will gain popularity in the coming months or just an isolated spear phishing attack is still unclear.
One thing is clear. Phishing callers will keep making phones ring all over the world because having a voice on the other end is an effective means of placing a victim under pressure.
These callers are trained and skilled in the art of deception. Social engineering has higher success rates than other, more impersonal phishing methods. You are more likely to be fooled by a “Google engineer” talking jargon than you would be by a simple SMS text or a stranger saying “Hi” on social media.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Google LLC. Gmail and Google Workspace are trademarks of Google LLC.






