For the past 2 years, the most prolific and most dangerous type of malware targeting Apple users has been stealer malware. Stealers continue to attack Apple users relentlessly. But who develops this malware and why?
All signs point to North Korean hacker units being partially responsible for the rise of stealer macOS malware. And now, they could be collaborating with or inspiring Russian cybercriminals who target Mac users well. But things get even more interesting than that.
How are FBI “laptop farm” raids connected to the surge in stealer malware?
Unless you live under a rock, you’ve probably heard about the FBI and US Department of Justice (DoJ) raids on North Korean laptop farms. These raids, along with new cases brought to US courts, focus on arresting individuals who allegedly acted as North Korean hacker accomplices setting up laptop farms.
North Korean laptop farms, which, as we mentioned, have been in the news lately, are how North Korean operatives — usually operating from Asia — manage to trick US companies that hire them into believing that they are, in fact, in the US.
The “fake IT worker” campaign is just one of the favorite scams used by North Korea’s threat groups. Others include crypto heists and targeting blockchain developers.
However, through the fake IT worker campaign, they have managed to infiltrate hundreds of US companies and taken things too far. Their goal is to collect monthly paychecks and send them back to North Korea, where their funds are, according to the United Nations, used to fund sanctioned international programs.
Their secondary goal is espionage, if they happen to stumble across information that could be of value to the North Korean government.
Our malware research team, Moonlock Lab, told us that this campaign, which is being disrupted by US authorities, is linked to the surge in stealer malware that has been happening since 2023.
The dangerous rise of macOS-targeting stealer malware
North Korean operatives use stolen personal information when applying to IT jobs in the US. They get this information through the use of stealer malware.
“Law enforcement is all about busting laptop farms — networks of shady devices North Korean operatives use to infiltrate tech giants,” Moonlock Lab told us. “But the real enabler? Stealers.”
Law enforcement is all about busting laptop farms — networks of shady devices North Korean operatives use to infiltrate tech giants. But the real enabler? Stealers.
Moonlock Lab
As mentioned, stealer malware has been on the rise for the past 2 years. This malware snatches IDs and credentials, letting hackers pose as legit job applicants to ace background checks.
“It’s the first step, not a sideshow,” Moonlock Lab said. “They grab data, use it to sneak into companies, get caught, then rinse and repeat with fresh stolen identities. It’s a cycle, and stealers are the engine, even if they’re not grabbing headlines.”
macOS-focused companies are among the targets, and the malware involved includes stealers that target macOS, Moonlock Lab added.
The bottom line is that stealers are no longer just about low-level cybercrime. Rather, they are connected to global espionage and money laundering operations — especially by sanctioned regimes like North Korea.
North Korean hackers’ crypto money laundering schemes may be more impressive than their malware
Besides the dangerous skill of developing malware that can breach macOS security (known for being among the strongest in the tech industry), North Korean hacker groups like Lazarus also display extremely sophisticated crypto-laundering tactics.
The threat group uses mixers and tumblers (e.g., Tornado Cash) to obfuscate stolen funds. This includes chain-hopping and converting between cryptocurrencies (BTC → ETH → Monero) to break tracing trails, as well as using DeFi protocols, cross-chain bridges, and NFTs to further anonymize assets.
Stolen funds also seem to be reaching the North Korean government through human proxy networks and crypto mule accounts created with fake or stolen documents.
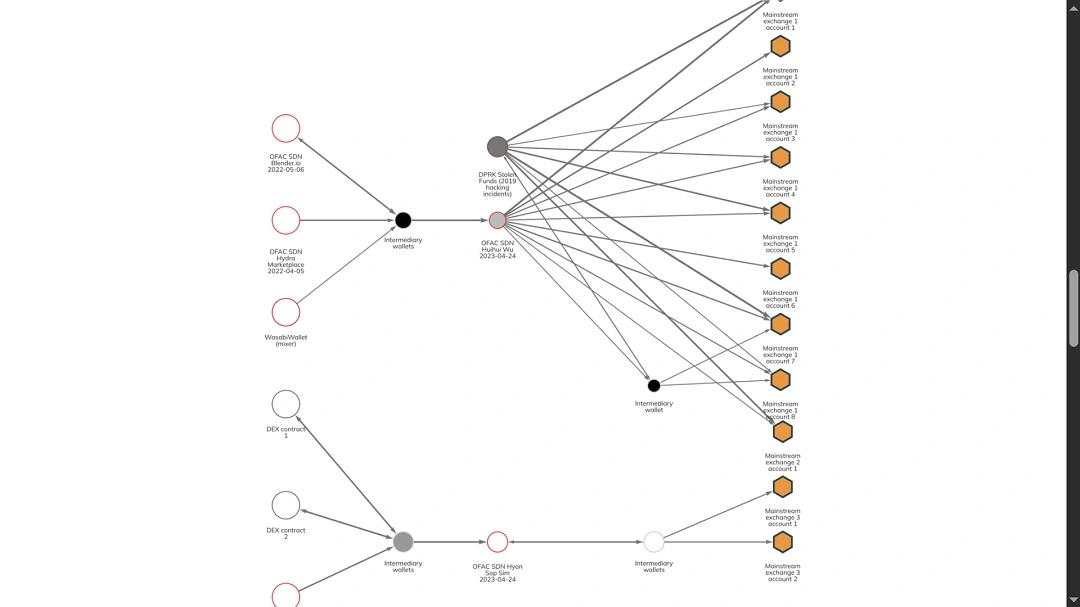
As the UN report linked above states, North Korea has laundered billions of dollars every year using these methods, bypassing sanctions and using the funds to finance its internationally sanctioned weapons and military programs.
The US Treasury and blockchain forensics firms like Chainalysis have repeatedly flagged North Korea as one of the most technically advanced crypto criminals operating today.
Why are North Korea operatives obsessed with Apple users?
We asked Moonlock Lab what was up with North Korea’s black hats and their obsession with Apple operating systems. We also asked why they seem uninterested in targeting Windows or other operating systems.
“North Korean hackers, like the notorious Lazarus group, are diving into macOS malware because Apple’s ecosystem is booming,” Moonlock Lab said.
North Korean hackers, like the notorious Lazarus group, are diving into macOS malware because Apple’s ecosystem is booming.
Moonlock Lab
C-level executives, developers, and crypto enthusiasts use Macs, and think they’re untouchable, Moonlock Lab added.
However, when it comes to malware skills, Moonlock Lab isn’t all that impressed.
“DPRK hackers don’t need fancy code,” they said. “They lean hard on social engineering, tricking users into running sketchy scripts or apps.”
Moonlock Lab is also witnessing an evolution in their malware; it is now modular, mixing stealers (grabbing passwords or crypto keys) with backdoors (sneaky access for later).
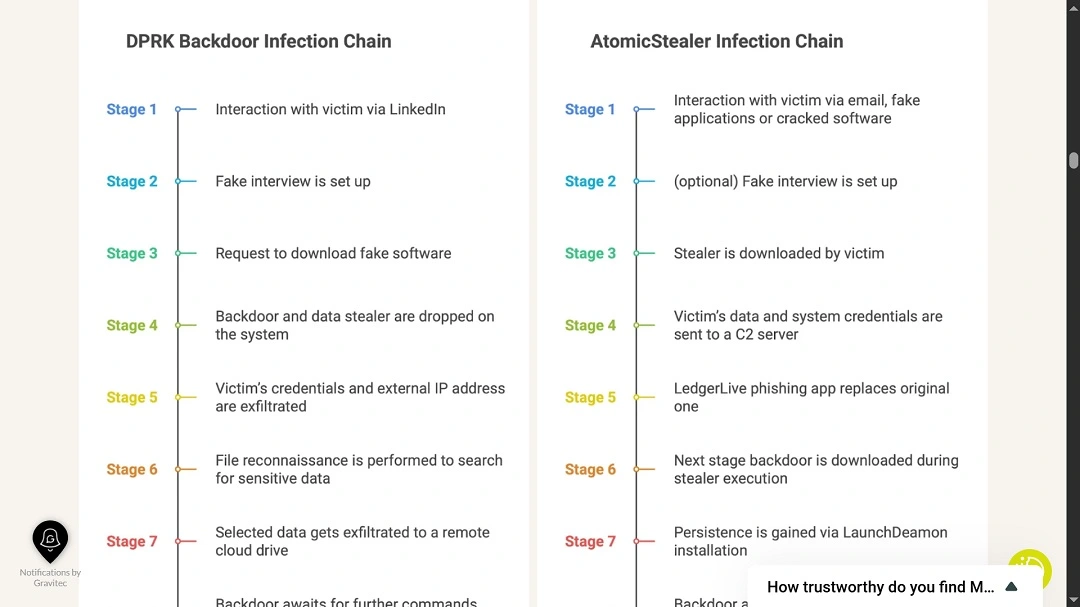
Moonlock recently reported that the addition of a feature that acts as a backdoor on the Atomic AMOS macOS stealer shares many similarities with North Korean backdoor malware. This means that the Russian-linked developers of the AMOS stealer are either inspired by North Korean black hat hackers or collaborating with them in some way.
How can the average Apple user mitigate this threat?
What can end users do to prevent their data from being stolen and used in these types of schemes? What should users know about the future of macOS stealers and how they will work — or are already working?
“Want to keep your data out of North Korean hands? Watch for social engineering signs,” said Moonlock Lab. “Those LinkedIn fake recruiters who chat you up for months might be fishing for a big catch.”
Other tips from the Lab include:
- Don’t download cracked software or run random commands (like in the ClickFix scam).
- Use a solid antivirus for macOS.
- In the future, macOS stealers are likely to get sneakier, blending data theft with persistent access, targeting users’ data and crypto wallets.
“Hackers know Macs are a goldmine, and they’re playing the long game,” Moonlock Lab said.
Final thoughts
As Moonlock Lab told us, North Korean spy schemes are definitely fueling the rise in macOS stealers, but they’re not the whole story. While Russian hackers are dropping slicker malware, North Korea’s stuff is scrappier, focused on stealing IDs and crypto.
According to Moonlock Lab’s internal detection statistics, from June to July 2025, North Korean stealers hit Singapore, Japan, Argentina, Spain, and the US, showing they’re playing globally.
Taking this into consideration — and taking a step back from the big, flashy news on laptop raids in the US — Moonlock Lab said that North Korea is definitely in the malware stealer game. “But they’re not the only players.”
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






