Cybercriminals are masters at developing clever ways to deceive, harass, and steal from the public. One of these techniques is called spoofing. It’s been around for a long time but continues to be a standard attack procedure.
Keep reading this guide to learn what spoofing is, how it works, and how threat actors use it to gain unlawful access to your most personal information or steal your money.
What is spoofing? The definition, meaning, and examples
A spoofing attack is when someone pretends to be someone else in order to gain access to secure servers, bank information, other digital assets, or accounts. The intent is usually to steal money or information for identity theft or to install malware or ransomware.
Clicked on a sketchy link? It happens.
One example would be a hacker emailing someone within a company, pretending to be an executive, asking for passwords or a digital transfer of funds. If the recipient doesn’t realize it is an attack, they may unwittingly give out private information or money to a stranger.
Some professional criminals use job offers to try to trick you into transferring money into their accounts or paying for something you don’t want.
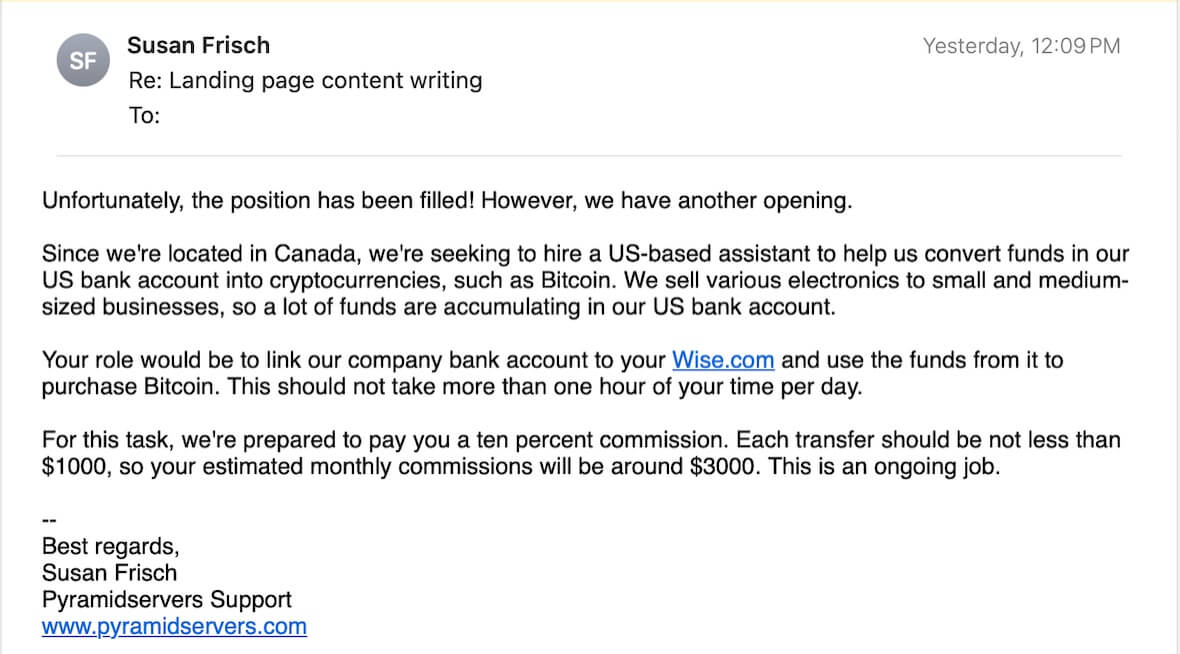
What does the spoofer want?
Criminals use spoofing for many reasons. The most common is to steal money by gaining access to bank accounts or manipulating purse string holders within a company.
Sometimes, the spoofer wants personal information they can sell on the dark web or use to impersonate the victim, harvesting credentials to access other digital assets. Other hackers use spoofing to breach networks and install malware, ransomware, or viruses.
Types of spoofing
Fraudsters use many different types of spoofing to trick users and obtain what they want. These techniques utilize various forms of communication, such as phone, email, SMS/messaging, and website access.
Caller ID or phone spoofing
Caller ID revolutionized the phone industry, allowing recipients to see who was calling before they picked up. Spoof calling is when a threat actor fools your caller ID by pretending to be someone in your local area. When you see a town or state name on the caller ID, a spoofer may be trying to get you to pick up the phone.
These criminals have found that victims are more likely to pick up an unrecognized number if they see that the call originates from their local area code. Occasionally, the scammer will even use your own number so that it appears that the call is coming from you. They will try anything to get you to pick up the phone so they can continue the ruse.
Email spoofing
Email spoofing is very common. You probably get dozens of spam emails every day. They are used for phishing attacks to get people to take action without thinking.
An email spoofing attack is when a hacker sends you an email that appears to be from a reputable source. They manipulate the “from” name so that it appears legitimate. They may even insert logos, colors, and fonts from the actual company to make you trust it.
These spoofing emails are often designed to get you to click a link to steal credentials or install malware on your device.
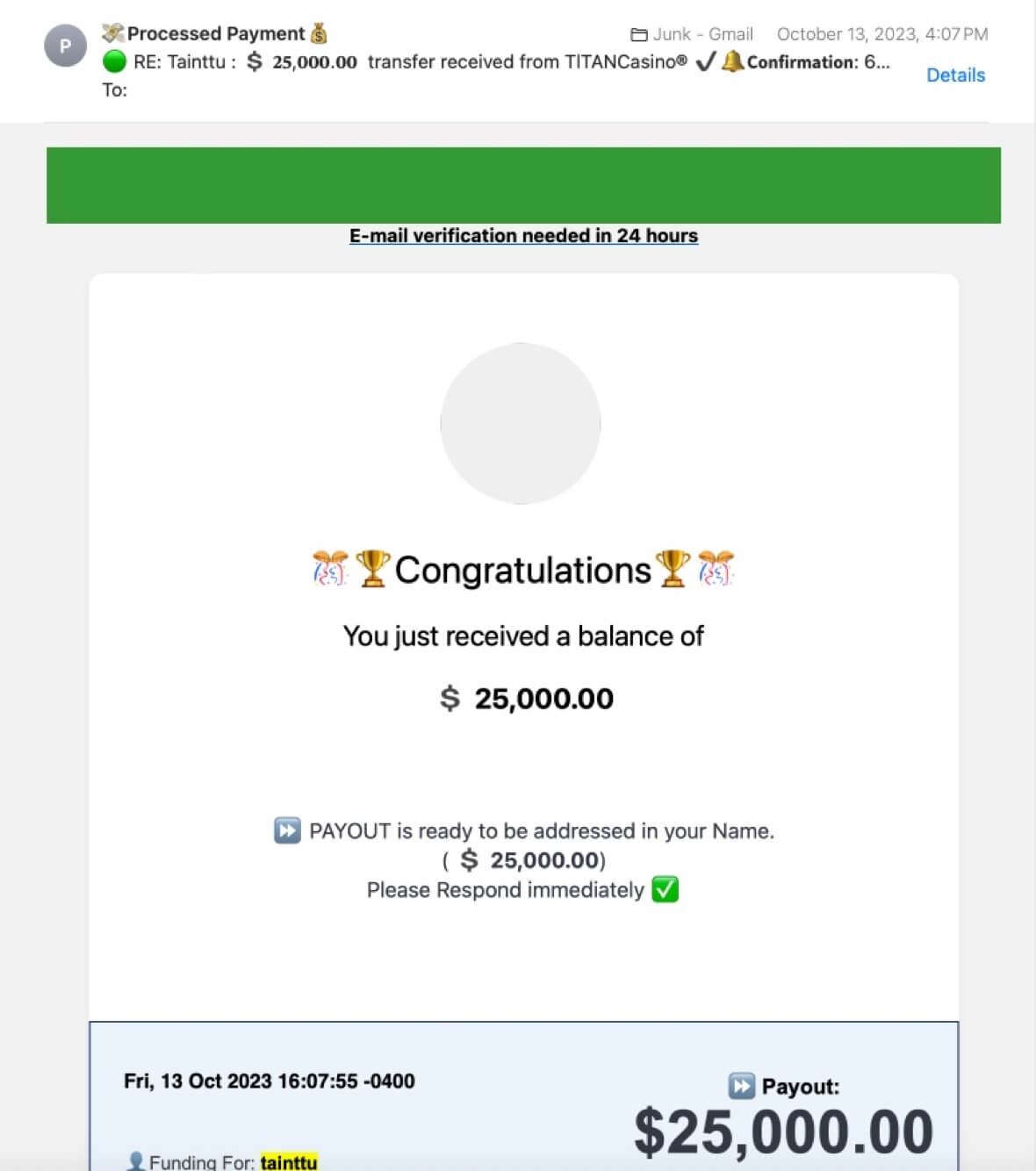
SMS spoofing
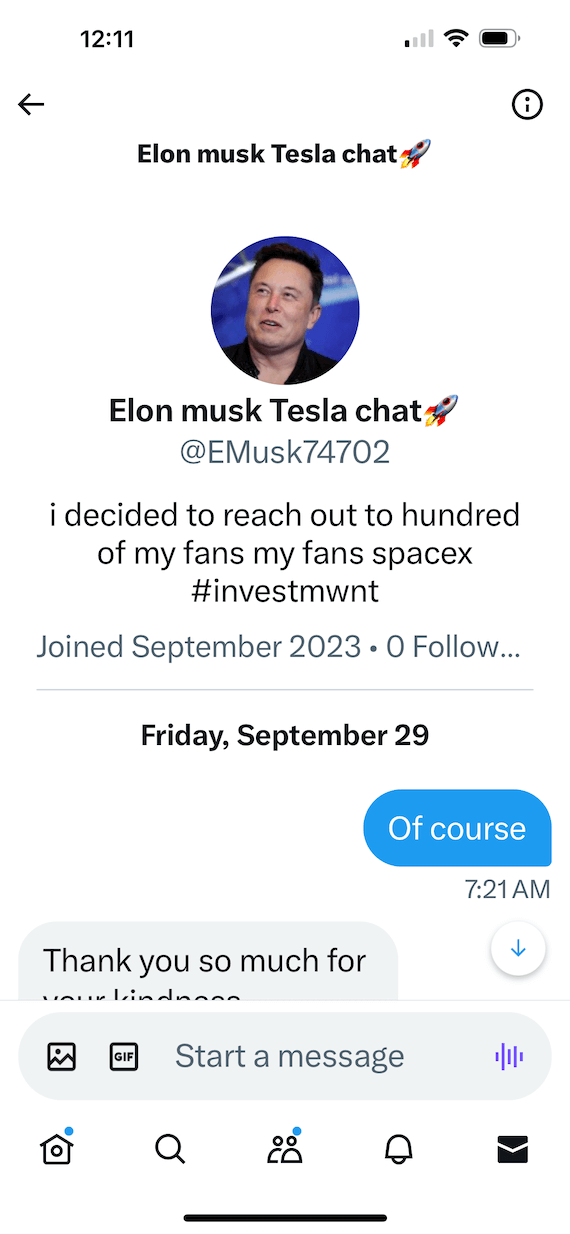
We live in an age of text messages, and cybercriminals have taken advantage of this opportunity for spoofing. They may send you fake messages urging you to click a link to check a breached account or review a non-existent invoice for something you didn’t buy. They are designed to incite fear so you act quickly without thinking.
In other cases, someone may contact you through a text message pretending to be a famous or notable person to get you to install an app or take an unsafe action that could result in theft.

IP spoofing
In the case of IP spoofing, attackers will falsify their IP address to conceal their location during distributed denial of service (DDoS) attacks and other nefarious activities.
DNS spoofing
DNS spoofing is particularly damaging. This occurs when hackers alter DNS records on servers to redirect web traffic to malicious websites that mimic the original. The fake website may look very realistic, so victims are unaware as they enter personal information and passwords.
How to recognize a spoofing attack
Spoofing uses social engineering to trick unsuspecting victims. The bad actor typically uses some legitimate information to make the user think it’s real. They use urgency to try to get people to act quickly without thinking to ensure that their attacks are successful.
Below are some ways to recognize a spoofing attack and prevent potential damage.
Spoof emails
There are many signs that an email is not legitimate. Here are just a few:
- For starters, the recipient’s address. If you hold your mouse over it, you may find that it comes from a very different source than what is shown in the “name” field.
- Another sign that an email may be spoofed is that the language may contain errors. Many cybercriminals operate out of non-English speaking countries, so the grammar and punctuation may be messy.
- Look for a sense of urgency or a dire alert. If the email says that your account has been hacked and you must call or click a link immediately, be wary. These are tactics used by spoofers.
- It is also probably fake if the email asks you to pay money or provide personal information such as account login information, your social security number, or your ID.
Never click a link in an email from any source that you do not trust completely. You could infect your device with malware or a virus.
Also, never give out personal information to anyone online or over the phone unless you initiate the conversation. Do not share logins or passwords with anyone.
Spoof websites
- Check the address bar. Chances are the URL will be slightly “off” from the original. Stay away if the site doesn’t start with “https” (meaning it is secure).
- Look for blurry images, logos, or graphics, along with broken English and poor grammar. Be careful of logging into any website that doesn’t seem legitimate.
- Don’t click a link to visit the site. Go to your browser and type it in manually so you are sure you’re going to the right place.
Spoof calling
Spoof calling is one of the oldest types of trickery. Callers pretend to be from a charitable organization and elicit donations from people. Sometimes, spoofers pretend to call from the IRS demanding payment. Rest assured, the IRS doesn’t make threatening phone calls and can’t put you in jail without a lengthy court process.
If anyone calls you with a threat or something that feels “off,” don’t provide any payment information over the phone, and don’t provide access to any of your accounts. Some hackers ask for access to your computer, then take it over and install malware. Just hang up.
In general, a good practice is to just not answer a call when you don’t recognize the caller ID. Let your voicemail pick up. Spoofers rarely leave messages.
Hackers can trap you in many ways. However, if you are vigilant and remain alert, you can stay safe from all these different types of spoofing attacks. Protect your personal information and account credentials diligently, and follow all cybersecurity best practices.







