A large-scale phishing-as-a-service (PaaS) group allegedly based in China is sending out millions of SMS to iPhone and Android users. The group has more than 60,000 fake websites.
The typical SMS claiming that there have been movements in your bank account, you owe highway tolls, or you have a UPS package awaiting confirmation has evolved and is now a real risk.
Resecurity’s Hunter Unit, a threat intelligence and research group, recently blew the lid off the operation that is blasting SMS and instant messages (IM) in the US, the UK, Spain, Australia, and other countries.
Resecurity warns millions targeted in new smashing campaign
On April 8, Resecurity reported that Americans and people living in the UK were being targeted via fraudulent text messages. These messages claimed unpaid toll bills for services like FasTrak, E-ZPass, and I-PASS.
Resecurity said that they expect this new campaign to expand worldwide. In this threat, victims who click on the link of the message or call back the number are asked to provide sensitive information. The end goal of the campaign is to steal data such as account credentials, credit card details, or other personal identification information (PII).
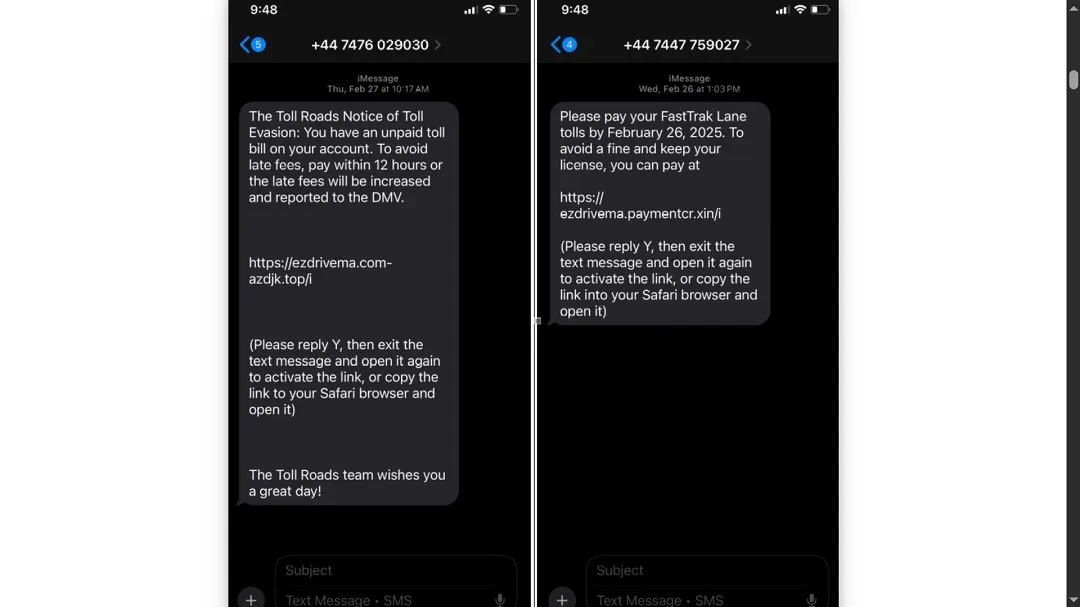
Resecurity warns that the threat actors behind this group are using the stolen data immediately. They also store it for future financial fraud or identity theft crimes.
The success of this new threat is driven by new technical advancements, the use of compromised accounts, and stolen data. Additionally, the infrastructure of the attackers is evidently advanced, global, and capable.
Moonlock speaks with Resecurity’s Hunter Unit
Moonlock spoke to the Hunter Unit at Resecurity about this new criminal operation and its infrastructure.
“Our threat intelligence report is primarily centered around underground bulk SMS services, some of which position themselves as legitimate marketing companies operating out of Asia,” Resecurity’s Hunter Unit spokesperson told us.
These “marketing companies” based in Asia are driving smishing activity, the spokesperson explained.
Hunter Unit added that threat actors abuse the policies of these companies and misuse them to create their own cybercriminal infrastructure (based on their own SMS gateways) and routes to send smishing at scale.
“The timely identification of such services will lead to disruption of their activity globally and will significantly decrease the volume of smishing worldwide,” Resecurity’s Hunter Unit said.
Hunter Unit goes undercover in Telegram and infiltrates Smishing Triad as an operator
The Hunter Unit of Resecurity went undercover on Telegram (please don’t try this at home) and found an entire ecosystem linked to the Smishing Triad. The services offered in the dark marketplace include the tools, technologies, guidance, support, and infrastructure to send out millions of fraudulent messages at scale in different countries.
“These messages often include links to fraudulent websites mimicking legitimate entities such as banks, payment systems, and other online services,” Resecurity said.
Using this technology, Smishing Triad operators can spoof sender IDs from, for example, legitimate American or UK banks. They can also use a combination of ranges of phone numbers and targeted databases built from stolen consumer data obtained through data breaches. This makes their SMS more victim-personalized and increases the success rates of the attacks.
Hunter Unit posed as an interested buyer on Telegram. They then made crypto payments to a dark web vendor and accessed an underground bulk IM service called Oak Tel.
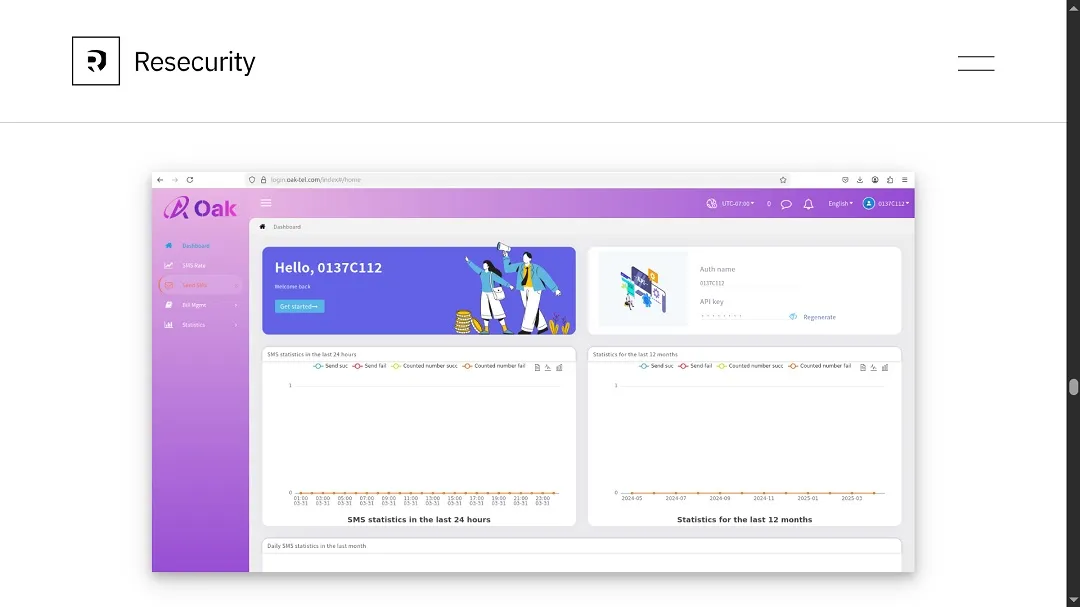
“The price for such underground services varies and depends on the region,” Hunter Unit said. “For example, sending 1,000 smishing messages to UK consumers will cost around $8.00.”
Who is Carrie? Smishing Triad’s first-hand SMS route provider
A Telegram user known as “Carrie” guided Hunter Unit through crypto payment. Carrie later provided them with access to the online smashing platform they use dubbed “Oak.” The platform supports SIDs of many US-based financial institutions, including Chase, Bank of America, Wells Fargo, and Citi.
Hunter Unit said they even got a “manual with instructions” along with access to the online platform.
In their channel, the Telegram user Carrie claims to be a “First-hand SMS route provider.” This is noteworthy.
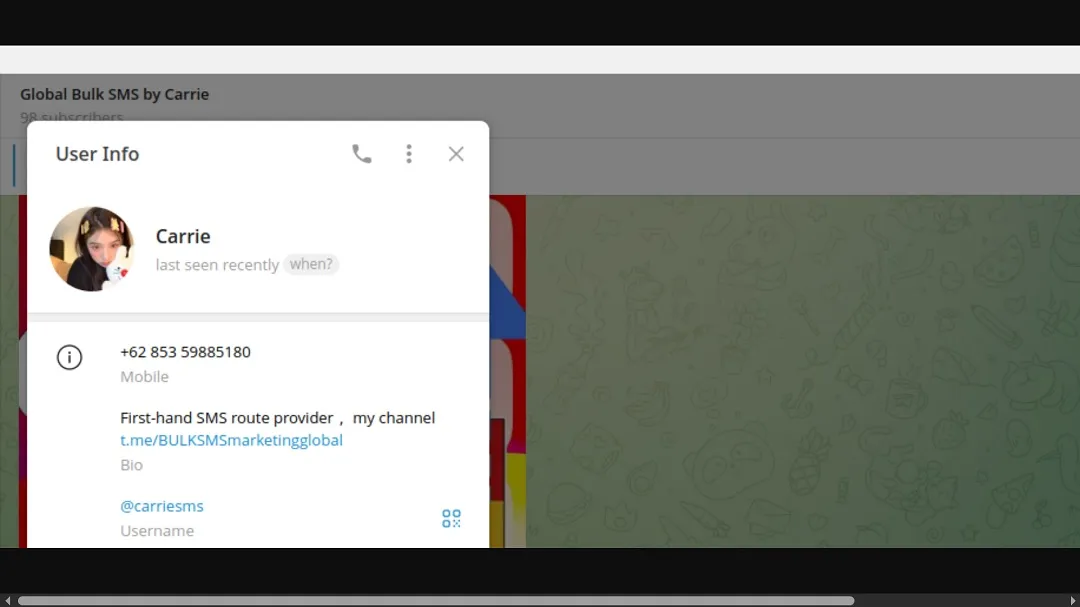
It is clear, thanks to the screenshots that Resecurity disclosed, that “Carrie” is posting about services that facilitate banking, e-commerce, and crypto-enabled fraud on Telegram. But let’s briefly explain why the phrase “First-hand SMS route provider” on the profile is important.
In the telco industry, a first-hand SMS route provider is a company or individual that has a direct, often contractual relationship with mobile carriers (like Verizon, T-Mobile, or AT&T) to deliver SMS traffic into their networks. They’re at the top of the food chain in SMS delivery — no middlemen, no resellers.
Because first-hand SMS route providers have application-to-person (DirectA2P) connections, operate in compliance with laws, and have established reputations, they are often targeted by threat actors.
This goes back to our initial question about the existence of Smishing Triad infrastructure in the US, UK, and Europe. “Carrie” claims to be a first-hand SMS route provider. Does this mean that Carrie has, for example, direct access to Verizon, T-Mobile, or AT&T infrastructure? If not, how are they doing what they are doing?
One thing is certain. At some point, the threat actors behind these scams have to use local infrastructure and networks to reach their victims. That is one of the most concerning elements of this threat.
Hunter Unit talks about attacker infrastructure
Moonlock asked the Hunter Unit what specific details they could tell us about the infrastructure used in this threat campaign targeting Americans, Europeans, and the world.
We wanted to know if the infrastructure is hosted in the cloud. We also wanted to know if there were indications that in-country SMS blasting technology or compromised edge local telco devices could be in use.
Some cybercriminals in Asia have been using SMS-blasting mobile technology setups inside vans. These vans circulate around a city, positioning themselves as a man-in-the-middle between cellphone users and local network antennas while blasting off millions of SMS.
Operations like this are a way to circumvent the security protocols that exist in every country — such as message protocols and local origin restrictions. There are, however, other methods to send out SMS without the use of in-country devices, remotely operated from abroad.
“We do have early warning indicators of it and will be covering it in our further reporting in the future,” a Hunter Unit spokesperson told us.
Be warned: This is not your usual SMS scam
It is not the first time Resecurity threat intelligence researchers have crossed paths with the Smishing Triad. On August 30, 2023, another Resecurity investigation found that the Smishing Triad was targeting US citizens for data theft using the old-fashioned USPS scam.
At this point, you may be wondering: Why all the fuss over USPS, FedEx, banks, and tollbooth debts? These are common SMS scams. Can’t most users see them coming from a mile away?
Unfortunately, this is not the usual SMS scam. In this scam, you won’t know what hit you until it’s too late. That’s how good the tech this group is selling and using is. Let’s dive into the details.
New technologies driving modern global smishing-as-a-service success rates
Resecurity’s report explains that because this group operates technology that can spoof a Sender ID (SID), people who get these messages will not know the difference. For example, your phone might show the actual CHASE bank number, but in reality, it’s just a hack.
“They also leverage SMS, iMessage, and similar instant messaging apps that have reduced spam protection compared to email service providers,” Resecurity said.
They also leverage SMS, iMessage, and similar instant messaging apps that have reduced spam protection compared to email service providers.
Resecurity
Naturally, an SMS or an instant message usually has a more urgent effect than an email. This is also driving the success of these cybercriminals.
The motivation for this operation seems to be solely financial. However, threat actors based in China appear to be targeting regions far from home. This gives the campaign a nation-state bias, to say the least.
Companies like Apple are having a hard time shutting down this operation because of its sheer volume. It’s like a game of whack-a-mole. As mentioned, the group has about 60,000 domains.
Notably, smishing operators are including in their scam message links that end with the .xin top-level domain (gTLD) instead of the usual .com. If you get a message with a link that includes or ends in .xin, do not click it out of caution.
Strangely enough, .xin is managed by a company or entity known as Elegant Leader Limited. It is supposed to be a new element for startups and innovators in China.
How to stay in the clear from the Smishing Triad campaign
Those operating under the Smishing Triad umbrella are also impersonating popular cryptocurrency exchanges such as Coinbase, Binance, and KuCoin, as well as banking institutions like BBVA. If you are a crypto user, be warned. PayPal is also on the table.
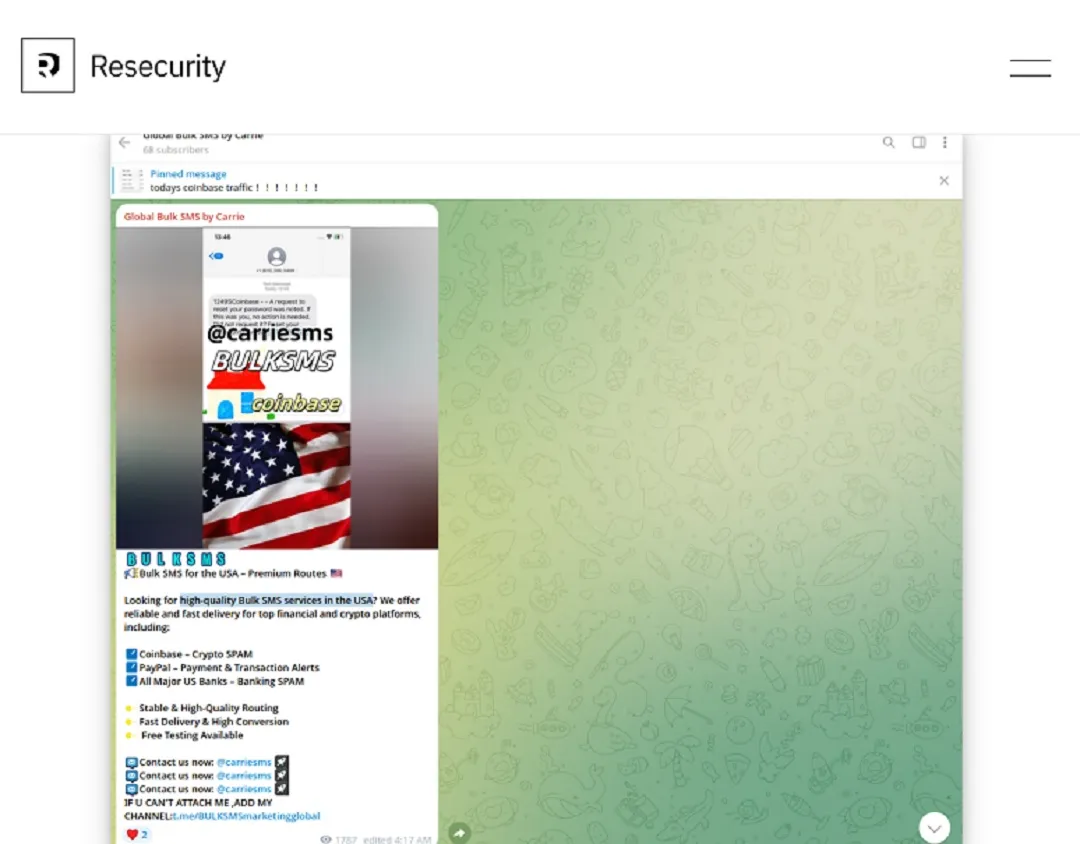
Besides being quick on your feet, what else can you do to keep away from this scam? You could ignore all SMS messages, but that’s not a realistic solution, is it? Instead, let’s check with Resecurity researchers, who say mitigation is “challenging.”
- Tip 1: “If you receive a message that appears to be from a bank or service provider, contact them via their official number and make sure their notification is legitimate,” Resecurity said.
- Tip 2: “Be wary of messages that create a sense of urgency or ask for personal information,” said Resecurity. “Scammers often use tactics that pressure you to act quickly.”
- Tip 3: Resecurity explains that enabling security features on your smartphone, such as spam filters and message blocking, can help reduce the number of smishing attempts you receive.
If it makes you feel any better, message providers have an even more difficult mitigation road ahead of them.
Final thoughts
Wrapping up these types of reports is becoming more challenging every day. Not that summarizing this operation in a couple of sentences is the main pain point; the problem is that threat actors and their ecosystems are becoming larger, more obfuscated, more diverse, and harder to track and verify.
The challenge is not due to a lack of evidence. Rather, it’s the opposite. These groups generate such large digital transnational footprints that investigation can become a real mess.
We can say, however, some things for certain. First, keep an eye on your SMS or instant messages. Second, Apple and iPhone users are being actively targeted in the US, UK, Europe, and other countries. Third, this threat is very difficult to spot. Finally, we recommend exercising caution with any SMS or message you receive, even if it appears to come from a real number.