An alleged “accidental” leak of US “war plans” on Signal has snowballed into a full political and international bombshell in just 24 hours. While Republicans and the Trump administration minimize the incident, Democrats express serious national security concerns and call for accountability. However, others in the technology sector, like us, are left with questions.
Was classified military information really shared on Signal accidentally by the Secretary of Defense with the editor-in-chief of the Atlantic? Or was it unclassified info? Are US top officials using free public messaging apps to communicate? And what type of communication platforms are suitable for operations at this level?
In this highly active, still developing, breaking news environment, we talk to expert sources with experience in secure communication technologies to answer these questions. The following is their view on the matter.
What happened in the Signal chat leak incident?
Before we jump to our panel of experts, here’s a brief breakdown of what we know at the time of this writing.
On March 24, Jeffrey Goldberg, editor-in-chief of The Atlantic, reported that he had received information about a live US military operation. The information, he claims, was shared with him two and half hours prior to the operation via the consumer-grade messaging app Signal.
A day later, US President Donald Trump addressed the issue. On March 25, Trump told Fox News that a staffer with national security advisor Mike Waltz’s office included the editor-in-chief of The Atlantic in the group chat. Trump said that the leak had “no impact at all” on the military strike in Yemen.
The President also hinted that the administration was looking into the technology used for operational security and highly sensitive communications. This includes whether these apps could be hacked — which, of course, they can be.
The role of Europe and the Red and Black Sea conflicts’ disruption on global trade routes
The editor-in-chief of the Atlantic told the press that he was invited to a group chat on the messaging app. In the chat, the US Secretary of Defense and other top security administration officials shared information on a strike against Houthi rebels currently waging guerilla warfare in the Red Sea near the Yemeni coast. Houthi rebel attacks have disrupted vital global logistic routes for oil, gas, and other commodities.
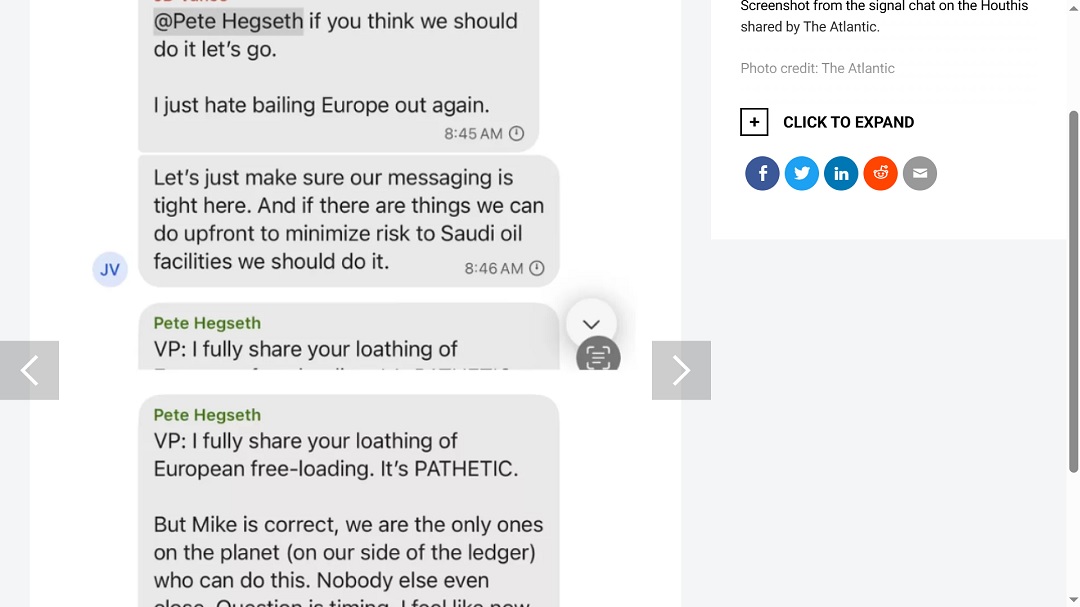
The alleged chat on Singal also contained hard words from US administration officials for Europe’s role in securing the Red Sea global routes.
As far as we know, the Houthis have not publicly commented on the Signal chat leak involving US officials. However, the leak has raised concerns about the implications for US military actions and regional security.
Operational security risks: From message interception by foreign actors to the new AI era of offensive tools
Moonlock spoke to Jeff Lee, Managing Principal for 100 Mile Strategies, a public sector navigation and tech consultancy. Lee is the former Deputy Cabinet Secretary for the Democratic California Governor Jerry Brown and is experienced in sensitive government communication.
Lee said that non-secure phone communications in the US are a high-priority concern. This is especially true when one considers the risk environment created by the Chinese-supported Salt Typhoon hacks against national telecommunications system. Other recent cyberespionage campaigns of note include the targeting of US Vice President JD Vance’s phone.
The incident underscores the risks of leaking military or classified information to countries like China, Russia, Iran, North Korea, or other adversaries who have geofencing surveillance technologies and monitor public messaging apps like Signal, said Lee.
“Sharing information on these insecure platforms is wholly a violation of security,” Lee explained. “Any of these players (foreign adversaries) could have alerted the various targets and risked American interests and lives,” said Lee.
“While Signal has some modicum of rigor, the powers of our adversaries of massive countries surely outmatch any one app,” Lee added. Lee spoke to us about the advancements made in the age of AI-powered offensive technologies and how these put operational security under greater threat.
While Signal has some modicum of rigor, the powers of our adversaries of massive countries surely outmatch any one app.
Jeff Lee, Managing Principal for 100 Mile Strategies
Humans, explained Lee, are the final barrier of defense. Lee also spoke about how decorum should be maintained by government officials while communicating.
“Fundamentally, all the tools in the world, regardless of their strengths, are still predicated on the judgment of humans,” Lee said. “Cyber is a human enterprise, not a tech one, and in national security, humans are still the weakest link as seen in honest mistakes or ones of malice or hubris.”
Similar incidents and their repercussions at corporate levels
Businesses, organizations, and enterprises can learn valuable lessons on communication risk management from the Signal incident. Similar events at the corporate level could lead to consequences ranging from potential blackmail to other ops where state-sponsored actors have leverage.
“From a corporate perspective, there are similar threats, but especially as it relates to gaining privileged credential access and intellectual property theft, a regular occurrence in this current environment,” said Lee.
A growing concern from these attack vectors is in the third-party risk space. Vendors, contractors, partners, and subcontractors are the entryway into broader enterprises. This can be seen with Change Healthcare, Halliburton, Colonial, and Uber, Lee added.
Do governments use messaging apps like Signal?
Government workers use messaging apps, including Signal, Microsoft Teams, Wickr RAM, and Troop Messenger. These provide end-to-end encryption and are used by state and federal governments.
According to a recent Associated Press review, 1,100 government workers and elected officials in all 50 US states use publicly available encrypted messaging platforms.
AP found that these types of apps are used by state, local, and federal officials in nearly every state. This includes state attorneys, legislators and staff, governments, education departments, and others. Incidents of government-leaked messages driven by the use of these apps have been registered in Missouri, Oregon, Oklahoma, and Maryland, AP reported.
What apps are government officials using in the US? AP says that Singal, WhatsApp, Confide, Telegram, and others are used.
The Cybersecurity and Infrastructure Security Agency (CISA) recommends the use of encrypted apps for “highly valued targets.” These include senior officials who handle sensitive information. Beyond that, agencies and departments have their own security memos and documents on which encrypted apps should be used.
The cost of “moving fast” and “breaking things”
Jake Williams, VP of R&D at Hunter Strategy, told Moonlock that when he first heard of the incident, he was shocked to learn that such data was being shared over Signal.
“When you’ve adopted the mantra of ‘move fast and break things,’ you’re going to break things,” said Williams. “This is a great example.”
Williams explained that one of the biggest risks with Signal specifically is that users can link Signal messaging to a desktop application. This means that Signal data is potentially being delivered to multiple desktop and laptop computers. In other words, it isn’t being stored in a phone’s secure enclave.
That data is then at risk from commodity malware on the system. “You can’t tell which of your contacts have their accounts linked to desktop machines, so you can’t evaluate the risk,” Williams said.
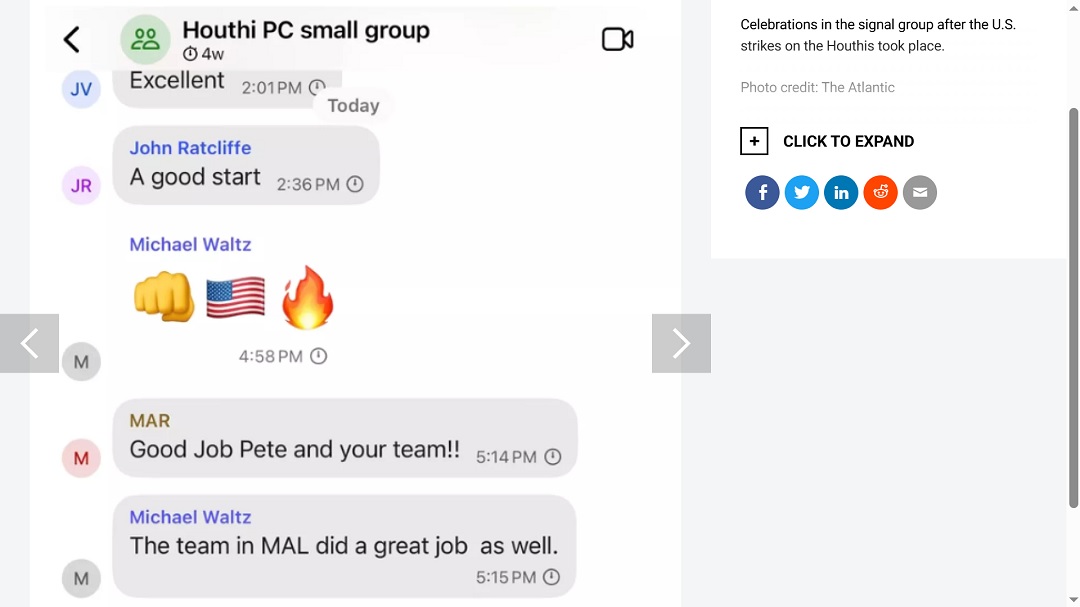
Public messaging apps vs. enterprise-grade secure communication
Moonlock also spoke with Anurag Lal, former White House Director of the US Broadband Taskforce. The US Broadband Taskforce was an initiative launched by President Barack Obama to expand broadband access for Americans. Today, Lal is the current CEO of NetSfere, a secure enterprise messaging platform company.
“In no world should federal employees be discussing matters such as war plans on a consumer-grade messaging app, likely on personal devices, too,” Lal said.
In no world should federal employees be discussing matters such as war plans on a consumer-grade messaging app, likely on personal devices, too.
Anurag Lal, former White House Director of the US Broadband Taskforce
Publicly available platforms like Signal are designed for consumers and should not be used by governments, said Lal.
Lal explained that secure, enterprise-grade communication solutions are centrally managed by IT. Chats in publicly available messaging apps have no enforced IT permissions. These allow, for example, for a journalist to be mistakenly added to a conversation on classified military plans, Lal said.
“To safeguard both the government officials and sensitive data, leaders have to go beyond consumer-grade applications and utilize purpose-built, secure, and IT-managed communication solutions that can ensure ironclad security, controlled access, and complete and absolute protection against breaches that threaten national security,” Lal said.
Final thoughts
The recent incident involving the Trump Administration’s alleged accidental sharing of sensitive information underscores the urgent need for secure communication channels in government and corporate settings. alike
While messaging apps like SMS and WhatsApp are convenient, they often lack necessary security measures such as end-to-end encryption. This makes messages vulnerable to interception.
To address these risks, organizations should adopt secure communication platforms and implement strict access controls. They should also provide regular training on communication security and establish clear policies regarding the use of communication tools for sensitive information.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Signal Technology Foundation. The Signal app is a trademark of Signal Technology Foundation.






