Things move fast on the dark web. It was only about 2 months ago that Moonlock reported a new “cheaper” macOS stealer on the rise. Fast-forward about 60 days, and that same stealer has been purchased by unknown threat actors and updated with a backdoor.
In this report, we focus on the new features of this malware and what Apple users need to focus on to avoid this threat.
Meet MacSync, the new macOS malware that wants to be more
MacSync is an evolution of the Mac.c stealer. A little backstory: Mac.c was developed by the user “mentalpositive” in April this year. The stealer was coded for quick in-and-out macOS data stealing. Its main selling point was its low price, set at $1,000.
Now, according to an interview by security researcher g0njxa and Moonlock Lab’s macOS researcher xiu (@osint_barbie), the malware has been bought by unknown threat actors and rebranded with the new name “MacSync.”
Why MacSync? “Because it’s catchy,” said the threat actors distributing it.
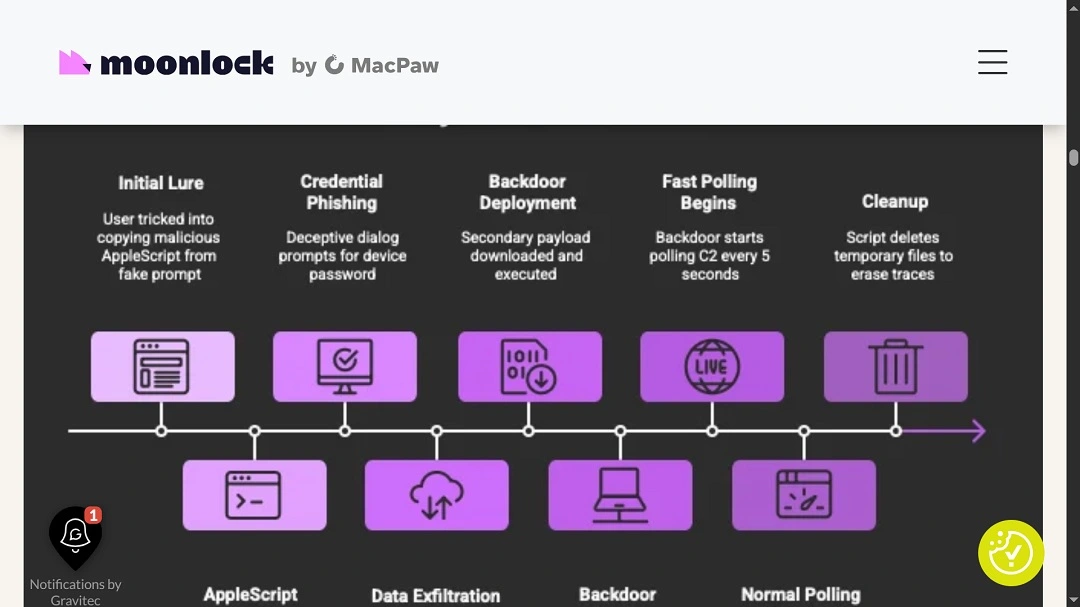
Apparently, the first thing the new owners of this upcoming, cheap, macOS dark web malware-as-a-service business did, besides rebranding the malware, was to update it with a backdoor. The backdoor uses Go Mach-O binary to fly under the radar, making it stealthier and harder to detect than AMOS.
“This obfuscation (Go garbling) complicates static reversing,” Moonlock Lab said in a recent analysis of the malware.
How big a problem is MacSync?
According to MacPaw’s CleanMyMac data, MacSync has already been identified in the wild in multiple countries.
The detection heatmaps show that those who are purchasing this malware from the new developers/distributors are targeting victims in Europe and North America the most. However, the malware has also already been used by criminals in Morocco, Ukraine, Brazil, Argentina, Japan, India, Australia, and other countries.
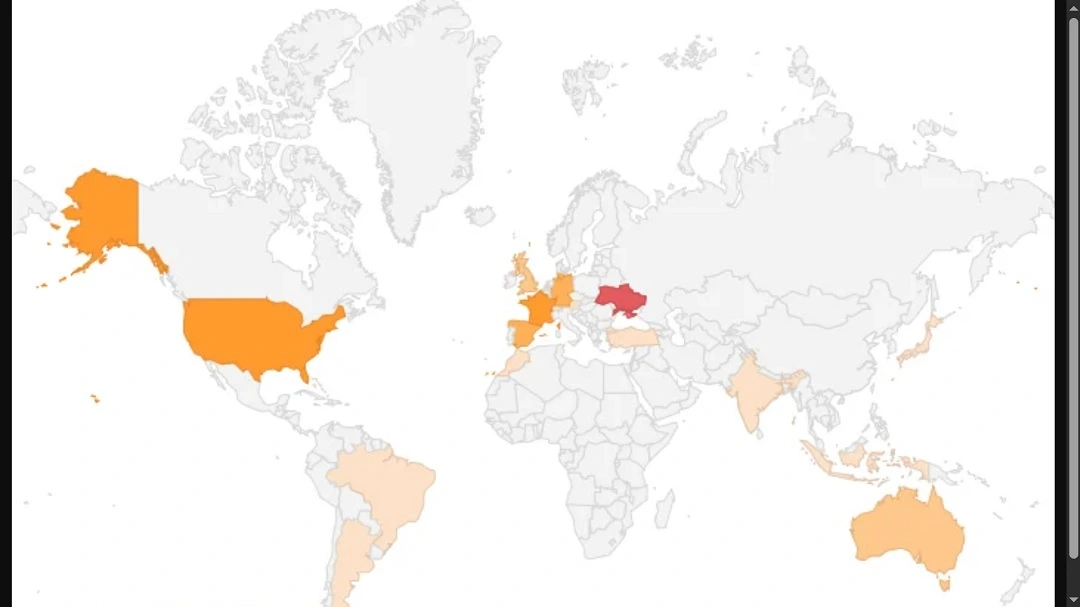
“While the infection volume remains relatively low overall (hundreds of detections compared to AMOS’s tens of thousands), the spread across diverse regions signals growing adoption among transfer teams targeting macOS users globally,” Moonlock Lab said.
Notable highlights of MacSync
MacSync is a modular malware. The stealer component of the malware, originally developed by the user “mentalpostive,” remains the same. It is written in AppleScript and searches for sensitive and valuable data to extract or steal.
However, the malware, as mentioned, now includes a backdoor written in Go for obfuscation. The stealer and the backdoor are separate modules. Modular malware allows black hat developers to easily add new features or capabilities to their software, although this can be done via integration as well.
Most importantly, MacSync is not an experiment or malware in development. It is fully functional. And updates to this malware are expected.
“The stealer phishes credentials while the backdoor reuses them (via sudo_password) for privileged RCE,” Moonlock Lab said.
Once it breaches a Mac, the stealer can collect sensitive data (yes, this includes credentials and e-wallet data), zip it, and send it over to the C2 attacker-controlled server using the backdoor malware.
Cybercriminals and black hat hackers are on a PR impunity tour
The new owners of this rebranded malware aren’t just advertising their product on dark web forums as usual. Apparently, they are going as far as taking interviews from members of the press.
In their recent interview with g0njx, the distributors of MacSync assure that there are no fights among dark web macOS stealer teams and that the malware-as-a-service “business” welcomes competition.
When asked if those who develop and distribute AMOS, the most-used macOS stealer in the world, had reached out to them — and if they had any interactions, conflict, or mutual respect — their answer was as follows.
“We haven’t encountered them yet; clients choose what they prefer. Competition is healthy — it pushes everyone to improve and differentiate their products.”
Nothing could be further from the truth.
On the dark web, threat actors either collaborate or fight for dominion. Giving interviews and or putting on a show about their technical capabilities on dark web forums are just a few of the ways threat actors advertise their malware. The other method? Cyberattacking victims.
Should Apple users be concerned about the malware stealer news?
While international law enforcement agencies investigate this new malware group (we hope) and cybersecurity researchers continue to analyze this new malware, Apple and Mac users may be left with a bad taste in their mouths.
How are threat actors able to develop malware that empties victims’ wallets and steals their data while openly giving interviews to the media online?
The impunity with which they operate is a tough pill to swallow. And it’s taking its toll on Apple users.
Naturally, if threat actors are giving interviews and publishing what their malware can do without any type of consequence, month after month, year after year, it’s going to affect macOS users’ behaviors and concerns. In fact, the recently released Moonlock Security Survey 2025 shows that Mac users are actually more worried than necessary about threats and malware.
The continual coverage of malware news focusing on dangerous stealers that can breach the once thought to be impenetrable Mac appears to be why Mac users are overly worried about threats and want more expert support today than before.
So, what can Apple users do? Believe it or not, there are a few simple steps anyone can take today to stop this type of cyberattack in its tracks.
Let’s cut through the PR impunity noise and look into how to not install MacSync on your Mac.
Again, for a more technical analysis of the backdoor and the updates of this malware, check out the full technical release.
How to NOT install MacSync — or any other stealer — on your Mac
The following is a list of 5 simple but highly effective actions Apple users can take to help them avoid installing MacSync or any other similar type of stealer malware.
1. Zero trust: Assume everything and everyone is malicious
First things first. MacSync can only breach your Mac if you install it. This means some kind of initial contact is needed. This initial contact with potential victims usually comes in the shape of emails, search engine results, or sponsored search engine ads that lure victims to malicious sites or other types of channels, like social media and social media messages.
By applying a “zero trust” approach to your digital lifestyle (trusting no one and verifying everything and everyone constantly), you close all the gates that MacSync or any other macOS stealer uses to breach your Mac.
Consider any and all suspicious or non-requested emails, messages, or SMS to be malicious. Assume that all websites, search engine results, and ads are malicious, and verify that they’re the real thing.
2. Verify, verify, and verify
Because digital behavior involves, to some degree, interacting with other users, websites, or platforms, constant verification is needed to maintain a zero-trust policy.
Double-check URLs, only download apps and code from respected and trusted sites, and only open attachments from sources you trust and have verified.
3. Keep your software up to date
Every day, Apple researchers, in collaboration with the broader cybersecurity community, work on security patches to fix known vulnerabilities that criminals use to breach your devices. These security patches are distributed for free to all Apple users via over-the-air updates.
Keep your devices up to date. Do the same with third-party apps.
4. Have a backup and mitigation plan
Backup and mitigation plans aren’t just for big corporations or large businesses. Any user should have one. Back up your important data. Keep any data of value to you offline.
A good idea is to use cold storage devices like memory cards, hard drives, or USB sticks. Anything that can be taken offline will do.
For crypto users, it’s time to get multiple wallets. Have one with only the minimal necessary funds on your Mac or browser extension. The other one, where you keep your hard-earned cash, should be kept on another device. This way, if someone gains access to the wallet you use on your Mac, they will get less than a bite.
5. Get a strong anti-malware tool and combine it with good practices
MacSync uses AppleScript intentionally so your Mac will not flag it when it runs commands, mistakenly believing these are “system-legit.” The Go backdoor, as analysis shows, also flies under the XProtect radar, Apple’s built-in anti-malware.
However, professional macOS anti-malware can detect MacSync and other stealers like AMOS before they breach your Mac. Anti-malware software is updated regularly to deal with malware variations and updates, like the one in this report.
The bottom line is, a good anti-malware tool will flag the threat, notify you, and shut down the stealer attack in real-time.
Combine a trusted anti-malware solution with strong security practices. This means not clicking on that particular link, downloading that suspicious file, or responding to that message from an unknown sender. Not only is this the best defense you have, but it proves to be highly effective.
If things go south, you can always hit Apple’s Lockdown Mode. Think of Lockdown Mode as a powerful kill switch to click when you’re being breached. Lockdown Mode was developed for the most sophisticated cyberattacks that exist in the wild (nation-state espionage-style). However, you can also use it to significantly reduce your digital attack surface.
Final thoughts
Apple users will continue to read about stealers breaking news. We might get more interviews and see more dark web posts as well. This, for now, has become the norm, despite it being far from normal — or even close to legal.
However, users are not defenseless. By following the tips in this article, understanding how cybercriminals work, and taking ownership and control of your digital environment, you can live a digital life without worries and steer clear of criminals and scammers.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






