Since 2024, macOS stealers have been constantly on the rise, and they’re gaining incredible speed throughout this year. Now, a new piece of malware, dubbed ModStealer, has emerged. Once again, this malware is reported to bypass Apple’s built-in security, steal user data, and go after crypto wallets. Let’s dive straight in.
Mosyle shares findings with 9to5Mac but releases few technical details
On September 11, 9to5Mac ran a report on a new infostealer that can breach macOS, Linux, and Windows devices. The report is based on discoveries made by the Apple-focused cybersecurity company Mosyle.
Other than warning users and the community via 9to5Mac, Mosyle has released no official communication or press release. Nor have they shared their digital forensic findings and investigations. This is rather unusual, as cybersecurity companies tend to share their discoveries in full through a dedicated blog.
Last month, Mosyle did the same. The company shared a report with 9to5Mac on a browser hijacker that breached Mac users via a fake PDF software download. We followed up on that report and discovered that the threat actor behind the threat was running a massive malvertising campaign.
What Mosyle says about ModStealer
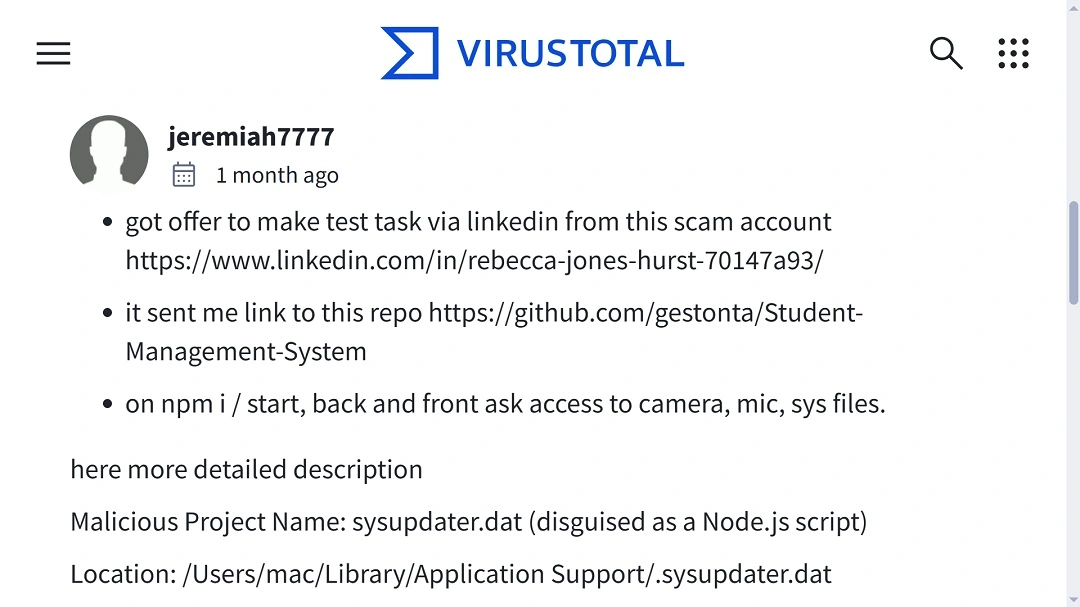
According to Mosyle, ModStealer first appeared on VirusTotal a month ago. The malware targets developers, luring them with fake job ads and recruitment opportunities.
The malware is also reported to be cross-platform. This means that it can breach macOS, Windows, and Linux devices. It is unclear how the malware achieves this. Cross-platform malware campaigns usually serve victims with different malware depending on the operating system used by the victim.
Mosyle also claims that this malware can breach more than 50 extensions across Chrome and Safari. Infostealers that can hack Safari are also rare.
What else can ModStealer do?
Besides targeting crypto wallet browser extensions, ModStealer is reported to be able to maintain persistence by installing itself in the launch/startup processes of macOS.
The stealer is reported to:
- Grab data from browser wallet extensions (Chrome/Chromium and Safari)
- Copy clipboard contents (seed phrases and private keys pasted by users)
- Take screenshots and capture visible user data
- Harvest saved browser data (local storage/LevelDB/IndexedDB), cookies, and credentials
- Install persistence on macOS via LaunchAgent and hide payload files (e.g., sysupdater.dat)
- Run remote commands to collect more data or move laterally
- Extract and transmit stolen user data to a C2 attacker-controlled server
None of these capabilities is uncommon in macOS stealers. The Atomic Stealer can do all these things and much more. However, ModStealer’s persistence mechanisms seem to be unique.
“On macOS, the malware achieves persistence or a long-term undetectable presence on a victim’s Mac by abusing Apple’s own launchctl tool, embedding itself as a LaunchAgent,” the 9to5Mac report reads.
Tips for developers and crypto holders as they become the prime target groups
Cybercriminals are targeting developers and crypto holders more and more every day. The reason for this is simple. These groups are seen by bad actors as a treasure trove to tap into.
Additionally, developers are known to download resources online and work with programming tools. This gives cybercriminals a way into their systems by producing Trojan malware for them to download.
On the other hand, as crypto goes mainstream, many users are turning to common e-wallets that operate on browsers. These browser extension e-wallets store high-value information in the high-risk digital environments of browsers.
So, what should users do? Stephen Ajayi, DApp and AI audit technical lead at Hacken, told Cointelegraph that developers should take extra precautions when asked to download files or complete assessments.
“Developers should validate the legitimacy of recruiters and associated domains,” Ajayi told Cointelegraph.
Developers should validate the legitimacy of recruiters and associated domains.
Stephen Ajayi, DApp and AI audit technical lead at Hacken
Ajayi added that developers should ask for assignments to be shared via public repositories. They should also only open tasks on disposable virtual machines that store no wallets, SSH keys, or password managers.
“Use hardware wallets and always confirm transaction addresses on the device display, verifying at least the first and last 6 characters before approving,” Ajayi told Cointelegraph.
What else can Apple crypto users do?
Crypto holders should consider using cold wallets that don’t store information online. If these aren’t the right fit for you, look into respected and trusted wallets that don’t store your data on your browser.
By reducing your digital attack surface, meaning having the least amount of data spread out online, you can mitigate the damaging effects that infostealers have.
Remember, infostrealers will roam through your macOS in search of data to open up your accounts. Therefore, we recommend keeping locked-down browser profiles or using separate devices that have multi-factor biometric authentication enabled for crypto operations.
Final thoughts
As Mac infostealer threats become more prevalent, dangerous, effective, and persistent, users should take steps to safeguard their data. Follow the tips in this report to stay one step ahead of attackers, and stay updated with cybersecurity news to learn the new tricks criminals use to try to lure you into a world of trouble.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






