The year 2023 saw a significant shift in the cybersecurity landscape, with macOS becoming a prime target for malicious actors. While traditionally considered more secure than other platforms, Apple’s operating system faced diverse cyberattacks.
Moonlock has prepared a detailed report to highlight the most significant macOS malware threats of the year, providing a deeper understanding of their characteristics, impact, and implications.
This article has been updated with comments reflecting newly found information about the malware threats included in it.
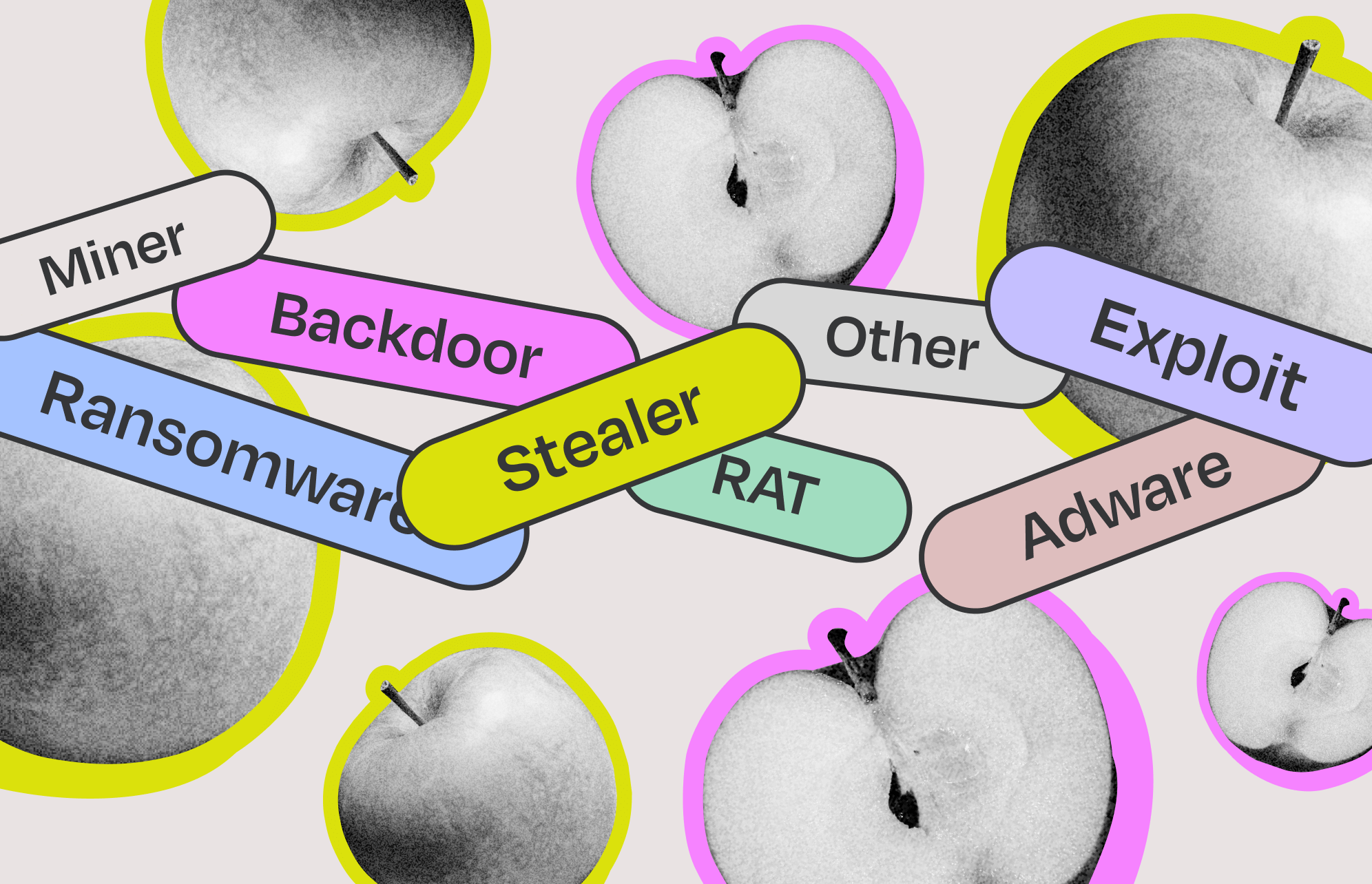
The 2023 macOS malware threats by month
Moonlock’s research shows that backdoor attacks (29.6%) were the most predominant macOS malware, followed by stealers (25.9%), a rising trend in the Apple universe.
Ransomware and remote access trojans (RATs) ranked third with 14.8%. Adware malware was also reimagined in 2023. Along with exploit attacks and others, they complemented the threat landscape.
Let’s dive into a month-by-month 2023 malware examination. In this report, we’ll reveal the main attack vectors, malware types, and techniques. Plus, we’ll examine how and when attacks began escalating and diversifying.
January: The Dridex RAT
Kicking off 2023 was a noteworthy RAT low-threat-level attack. The Dridex RAT — a new variant of the Dridex banking malware — used to be unique to the Windows environment. In a trend that we would continue to see throughout the entire year, cybercriminals enhanced the RAT malware to target Apple’s macOS.
Described as an evasive information-stealer, the malware is coded to steal as many credentials as possible. The new Dridex uses a novel technique that combines malicious macros and Mach-O, auto-executable Mac files. It allows criminals to breach macOS devices without having to trick users or hide code in malicious Word files, disguising them as invoices. Dridex is attributed to the Russian-based cybercriminal group known as Evil Corp (aka Indrik Spider).
Update: While the delivery of Dridex has been adapted to target macOS devices, the ability of the .EXE files to impact macOS systems is limited. There are currently no active Dridex campaigns targeting macOS users.
February: XMRig Miner
February followed with a high-threat-level miner malware dubbed XMRig. To breach Apple devices, the malware poses as legitimate pieces of software, including Apple Logic Pro X and Final Cut Pro. Victims who are tricked into downloading the software have the malicious app automatically installed.
By utilizing open-source XMRig crypto mining software and the I2P network tool, the attackers conduct crypto mining operations on compromised Mac devices. Abused by cybercriminals for years, XMRig mines cryptocurrencies like Monero or Bitcoin by using Mac computers infected with cryptojackers. These types of malware are known to infect hundreds of thousands of devices.
Update: XMRig is a legitimate open-source miner that is being used for malicious purposes. The miner itself is not malware.
March: SmoothOperator 3CX and MacStealer
In March, attackers picked up the pace, with 2 threats being the most noteworthy: SmoothOperator 3CX and the infamous MacStealer.
Both malware were identified as stealers, undoubtedly one of the fastest-growing types of malware in the Apple landscape. SmoothOperator 3CX is a high-level threat stealer that targets supply chains. The malware is linked to North Korean hackers.
Smooth Operator malware compromised the popular VoIP desktop software 3CX of Crowdstrike. 3CX is used by hundreds of thousands of customers around the world, including well-known major corporations. Like any supply chain attack, the malware targeted and breached 3CX, a trusted third-party provider, and used it to deliver malicious updates to millions of devices. Experts described the Smooth Operator attack as having the potential to be the worst supply chain attack since the Solar Winds attack in 2020.
That same month, cybercriminals behind the MacStealer used a similar approach, leveraging Telegram’s ecosystem. The new macOS stealer malware can extract sensitive data from browsers and Keychain databases, affecting macOS Catalina and newer versions on Intel M1 and M2 CPUs. The malware steals data through a fake password prompt in a .dmg file. It sends collected data to a Command and Control server via Python requests.
April: RustBucket, AMOS (Atomic Stealer), POOLRAT, and Lockbit
April was one of the busiest months of 2023 for cybersecurity, with RustBucket, AMOS (Atomic Stealer), POOLRAT, and Lockbit attacks affecting Apple users around the world.
RustBucket impressed cybersecurity experts with its ability to establish persistence, avoid detection, and target macOS users. The backdoor malware is linked to the North Korean threat actor BlueNoroff, working under the umbrella of the Lazarus Group, an elite hacking unit supervised by the Reconnaissance General Bureau (RGB) of North Korea.
RustBucket is an AppleScript-based backdoor that communicates with C2 servers to download and execute various payloads. The malware is actively evolving, incorporating built-in persistence and employing signature reduction techniques to avoid detection. Its new variant, REF9135, specifically targets a venture-backed cryptocurrency company in the United States.
AMOS, or Atomic Stealer, was one of the most reported malware throughout the year. This stealer, identified as a high-level threat, was being advertised on a Telegram channel. AMOS can specifically target macOS systems to steal sensitive information, including Keychain passwords, crypto wallets, browser data, and files from victims’ machines. The malware is distributed via .dmg files, displaying a fake password prompt to obtain system passwords.
Lockbit attackers also followed the 2023 trend of modifying and enhancing malware variants to make them capable of breaching and affecting Apple and macOS devices. The very well-documented ransomware, developed by the LockBit ransomware gang, moved from exclusive Windows, Linux, and VMware ESXi servers victims to using new encryptors specifically designed for macOS, including Apple M1-powered devices.
May: Snake and Geacon
The backdoor Snake and Geacon attack took over May to target macOS systems. Snake is an advanced persistent threat (APT). It is a creation of the Russian-based Turla group. This group is widely experienced and is believed to have been in operation since at least 2004. It coded the malicious backdoor Snake specifically to breach macOS devices. The malicious code was found within a file associated with Adobe Flash Player installation.
Geacon, a lower-threat-level attack, is a Go implementation of the infamous Cobalt Strike red-teaming tool. In May, it drew attention as it began targeting macOS devices. Geacon variants have been detected on VirusTotal, some showing signs of genuine malicious intent.
Update: The file mentioned in the tweet appears to be a legitimate one. Therefore, the activity of Snake in May 2023 may be questioned.
June: JokerSpy
Another backdoor that rose in June and gained traction as a high-level threat was REF9134, a complex cyber intrusion dubbed JokerSpy. The malware targeted a prominent Japanese cryptocurrency exchange. Attackers employed the sh.py backdoor to deploy the macOS Swiftbelt enumeration tool, showcasing advanced evasion techniques and manipulation of system permissions.
July: DangerousPassword, NokNok (GorjolEcho), ShadowVault, Realst, and FULLHOUSE.DOORED
July was an extremely active month. The cyberattack group DangerousPassword targeted cryptocurrency exchange developers with a high-level threat backdoor that exploited vulnerabilities in Windows, macOS, and Linux systems. In macOS and Linux, the attackers injected malicious code into Python files, compromising user data and system information.
Another backdoor, GorjolEcho, from the Iranian-based threat group APT42, also known as Charming Kitten, hit experts in Middle East affairs and nuclear security using phishing emails. GorjolEcho attackers deployed a variant specific to macOS dubbed NokNok. NokNok collects system information, encrypts it, and exfiltrates it. The campaign was identified as having a cyber espionage goal.
Following the rising trend of stealers, ShadowVault became a sophisticated malware. Designed to steal sensitive data from macOS devices, ShadowVault operates silently in the background, collecting valuable information like login IDs and financial data. Researchers discovered ShadowVault being sold online as malware-as-a-service, another global landscape threat area that is on the rise.
Similarly, the stealer Realst was distributed through fake blockchain games on malicious websites. Realst steals sensitive information, including crypto wallets and passwords, using various methods such as AppleScript spoofing and Terminal prompts. The malware comes in different variants with distinct characteristics.
But that wasn’t all. Another malware used by the North Korean Lazarus Group was the backdoor FULLHOUSE.DOORED. This malware was written in C/C++ and includes the capabilities of a tunneler and backdoor command support, such as shell command execution, file transfer, file management, and process injection.
August: HVNC, XLoader, AdLoad, and Akira
Throughout August, malware continued to diversify with the RAT HVNC, allowing attackers to gain unauthorized access to macOS devices. HVNC, sold for a lifetime price of $60,000, offers powerful technologies and new features, including persistence, reverse shell, remote file manager, and macOS compatibility.
In contrast, the XLoader stealer, breaching devices in persistent attacks, reemerged in August 2023 under the disguise of a new office productivity app named OfficeNote. This infostealer, previously limited by Java dependencies, is now written in C and Objective-C languages. Distributed through a revoked Apple Developer signature, XLoader works by targeting user data from Chrome and Firefox browsers.
Overall, adware made a comeback in 2023. Malware like AdLoad, initially discovered in 2017, continued to infect Mac systems. This adware can be used to download additional malware and impact macOS users with malicious ads, bundleware, PiTM attacks, backdoors, and proxy applications to macOS systems.
While ransomware played an undeniable role throughout the entire year, in August, the Akira ransomware broke headlines when it targeted corporate networks through Cisco VPN products. Akira’s main goal is to breach systems and networks, steal data, and encrypt files in demand of payment.
Update: While Akira was a serious threat in 2023 and indirectly affected macOS users, it does not target macOS systems specifically.
September: MetaStealer and Knight
Two significant threats emerged in September, targeting business users and sensitive data. MetaStealer, a new stealer, spread through deceptive disk image bundles posing as fake clients. Once executed, it attempted to extract sensitive information and connect to specific domains, potentially compromising confidential business documents and financial data.
The second threat, Knight ransomware, arrived as an evolution of Cyclops ransomware. Operating as a ransomware-as-a-service (RaaS), it targeted both enterprise and SMB environments, demanding ransom payments in exchange for data decryption. Knight employed two versions, a normal and “lite” version, and was primarily delivered through phishing campaigns, highlighting the continued threat of social engineering tactics in ransomware attacks.
Update: While Knight was a serious threat in 2023 and indirectly affected macOS users, it does not target macOS systems specifically.
October: Monti, DirtyNIB, and TriangleDB
October introduced new concerns with the emergence of Monti, a novel ransomware affiliate scheme discovered on dark web forums. Claiming to use a modified version of Conti’s EXSi ransomware, Monti brought a potentially more sophisticated threat to the table. Its connection to experienced operators from REvil’s early days further raised security concerns.
Researchers also discovered DirtyNIB, an exploit targeting macOS Monterey and Sonoma through modified NIB files. This exploit allowed for code execution, highlighting the need for vigilance and timely updates to mitigate vulnerabilities.
Additionally, the discovery of TriangleDB, a complex iOS spyware implant used in targeted attacks, underscored the potential dangers lurking within seemingly legitimate applications.
Researchers investigating Operation Triangulation uncovered a complex iOS spyware implant called TriangleDB. This was deployed through targeted attacks involving exploits to gain root privileges. The implant, written in Objective-C, operates in memory, making detection challenging. It communicates with C2 servers using encrypted Protobuf messages, allowing attackers to control infected devices remotely.
Update: TriangleDB has also been known to impact macOS devices.
November: Kandycorn
In early November, security researchers realized that North Korean state-sponsored hackers were back with a new campaign. The goal? To infect blockchain engineers with a new form of macOS malware.
Elastic Security Labs were the first to disclose the threat. This new form of macOS malware, Kandycorn, is also known as REF700. The REF7001 campaign unfolded in November, demonstrating a multi-stage approach to malware delivery. The campaign involved Python scripts for initial compromise, followed by deployment of SugarLoader and HLoader variants, culminating in the arrival of the Kandycorn RAT.
This malware displayed concerning capabilities, including data collection, arbitrary command execution, and retrieval of additional payloads from attackers’ servers, emphasizing the potential for significant damage from such multi-stage attacks.
December: WSProxy
December closed the year with the discovery of WSProxy, a backdoor distributed through cracked software packages. Disguised as a GoogleHelperUpdater agent, WSProxy installed itself on infected systems. While no malicious payloads were observed at the time of discovery, the functionality posed potential risks for future attacks. It also served as a reminder of the dangers associated with using cracked software.
Conclusion
There were several concerning malware and cybercriminal trends observable in 2023.
MacOS-specific malware is perhaps one of the biggest trends we have identified. Additionally, the role of the dark web as a haven for criminals is fueling ransomware-as-a-service, malware-as-a-service, zero-day exploits, and file-less attacks across every industry. This lowers the barrier to entry for would-be attackers, making malware more accessible to anyone.
Mac stealers and backdoors were undoubtedly the big players of the year. Still, the threat landscape remained diverse and dynamic.
The most significant takeaway from this report is the need for continued vigilance, proactive security measures, and awareness of current threats to ensure the safety and security of macOS systems. As the threat landscape continues to change, staying informed and adopting best practices will be critical in mitigating the risks and protecting valuable data.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.