If you’ve ever wondered how cyberattacks begin, the answer is usually through stolen credentials, data, and passwords dumped on the dark web and forums. From phishing to spear phishing, credential stuffing, account takeovers, and more, cybercriminals love to get their hands on ready-to-use data because it makes their job so much easier. After all, if you have the email and password, you’re in.
It’s not uncommon for security specialists to identify new password dumps. But the recent Naz.API list has everyone concerned. About 71 million accounts are included in the dump. So, let’s dive into this news and learn how you can stay safe.
What’s the Naz.API password list dump?
On January 18, Troy Hunt, CEO and founder of Have I Been Pwned? and Microsoft Regional Director & MVP, wrote a post breaking the news and details of the Naz.API credential stuffing dump. While the Naz.API list was released about 4 months ago, in September 2023, it flew under the radar until recently, when it caught Hunt’s attention.
The dump was posted on BreachForums by the user Ox64, who assured that the database was created by extracting data from stealer logs. Stealer logs are created using malware that can breach systems. Stealer logs usually contain data such as email addresses, passwords, and account websites.
Ox64 also claimed in his post that the list was the original Naz.API data that was obtained from the now shut-down open-source intelligence OSINT tool site Illicit Services (more on this below).
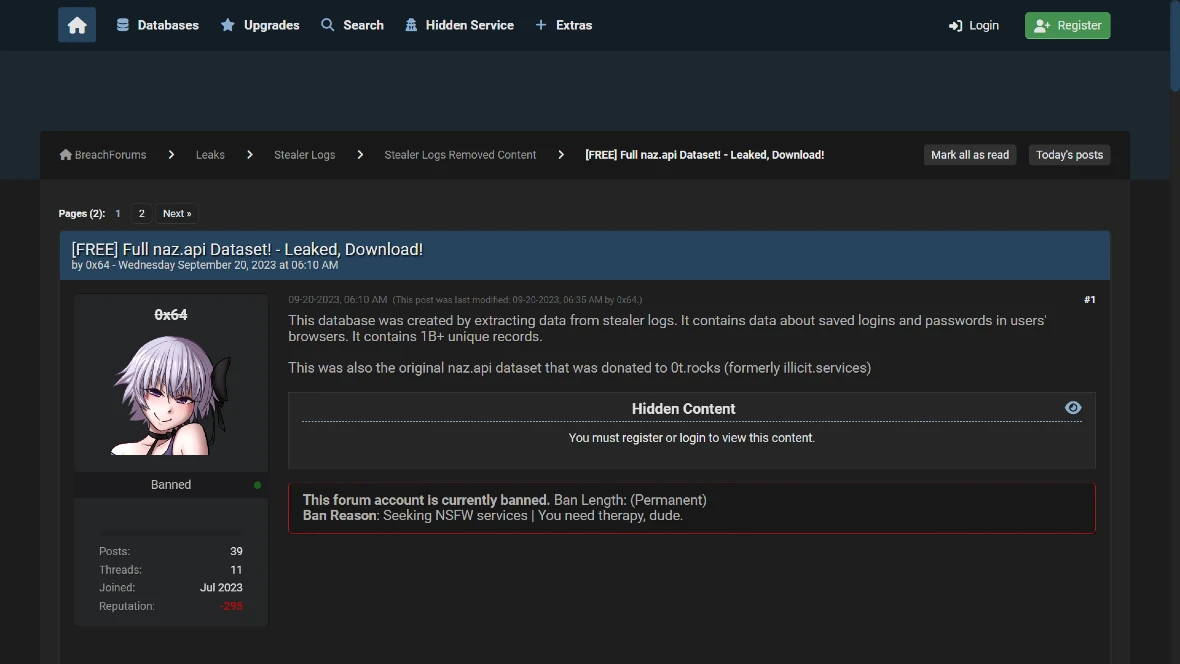
The Ox64 account on BreachForums has been permanently banned. However, the posts, comments, and replies can still be seen and accessed by anyone. This includes information on Ox64 and his Telegram contact account.
What the Naz.API dump includes
Hunt investigated the list and verified the legitimacy of the data. He found that the list has:
- 319 files, totaling 104 GB of data
- 70,840,771 unique email addresses (about 71 million)
Approximately 65% of email addresses were already in HIBP, meaning 35% of the data exposed belonged to newly breached accounts.
“That last number was the real kicker,” Hunt said. “When a third of the email addresses have never been seen before, that’s statistically significant. This isn’t just the usual collection of repurposed lists wrapped up with a brand-new bow on it and passed off as the next big thing; it’s a significant volume of new data.”
This isn’t just the usual collection of repurposed lists wrapped up with a brand-new bow on it and passed off as the next big thing; it’s a significant volume of new data.
Troy Hunt, Have I Been Pwned?
Hunt compared the data of the dump against the data of Have I Been Pwned? (HIBP). HIBP is a free website and service that helps users verify if their email address has been compromised in a data breach.
Hunt concluded that based on a 1K Naz.API random sample, 65.03% of addresses were already in HIBP. Additionally, the dump included 427,308 HIBP subscribers.
The origin of the massive data dump
As Hunt reports, the Naz.API list seems to be sourced from the site Illicit Services. Illicit Services was shut down in mid-2023 by its anonymous creator, who went by the name Miyako Yakota. Yakota realized that the service he had created as an open-source intelligence tool was being abused by criminals and was not serving its original purpose.
Illicit Services had become a popular OSINT tool used by security specialists, too. The site was a data breach search engine that had information on over 14 billion records in its database. The site included data such as names, email addresses, usernames, phone numbers, addresses, driver’s licenses, VINs, and geographical information such as city, state, and zip code data.
According to Hunt — as well as the user who posted the Naz.API list on BreachForums — Illicit Services is where the data came from. Stealer logs seem to have been used to extract the data.
The largest file in the Naz.API dump is composed of 312 million rows of email addresses and passwords.
How can you stay safe from Naz.API and other data dumps?
Naturally, you can check sites like HIBP to see if your email is in the latest dump. Or you can run free dark web reports with Google.
Ideally, we recommend using strong (and different) passwords for your accounts and enabling MFA with biometrics when possible. Using password managers is also a good idea. However, before you use a password manager, make sure you know how the tech works. Review different services to find one that is reliable, safe, and aligns with what you need.
You can also strengthen your security by using a privacy-focused web browser, making sure you don’t click or download files from suspicious sources, and keeping your software up to date. If you believe your information may have been compromised in a data dump, change your passwords immediately.