From impersonating Slack to promoting fake websites on Google Search and Google Ads, stealing information on Telegram, posing as fake browser updates, and more, Atomic Stealer (AMOS) has been shape-shifting in the past years.
Now, AMOS is once again back. This time, it has changed its tactics and is going after the Web3 gaming community and their crypto wallets.
Exposing a large-scale Russian-language criminal enterprise
On April 11, the Insikt Group — a Recorded Future’s threat research division — reported that a large-scale, evolving, and dynamic Russian-language cybercriminal operation is using fake Web3 blockchain gaming projects to distribute stealers among Windows and macOS users.
In the Web3 gaming community, it is common for new gamers or testers to receive financial incentives through cryptocurrency earnings, including NFTs. Criminals leverage this arrangement to trick users into engaging with fake games and other blockchain projects.
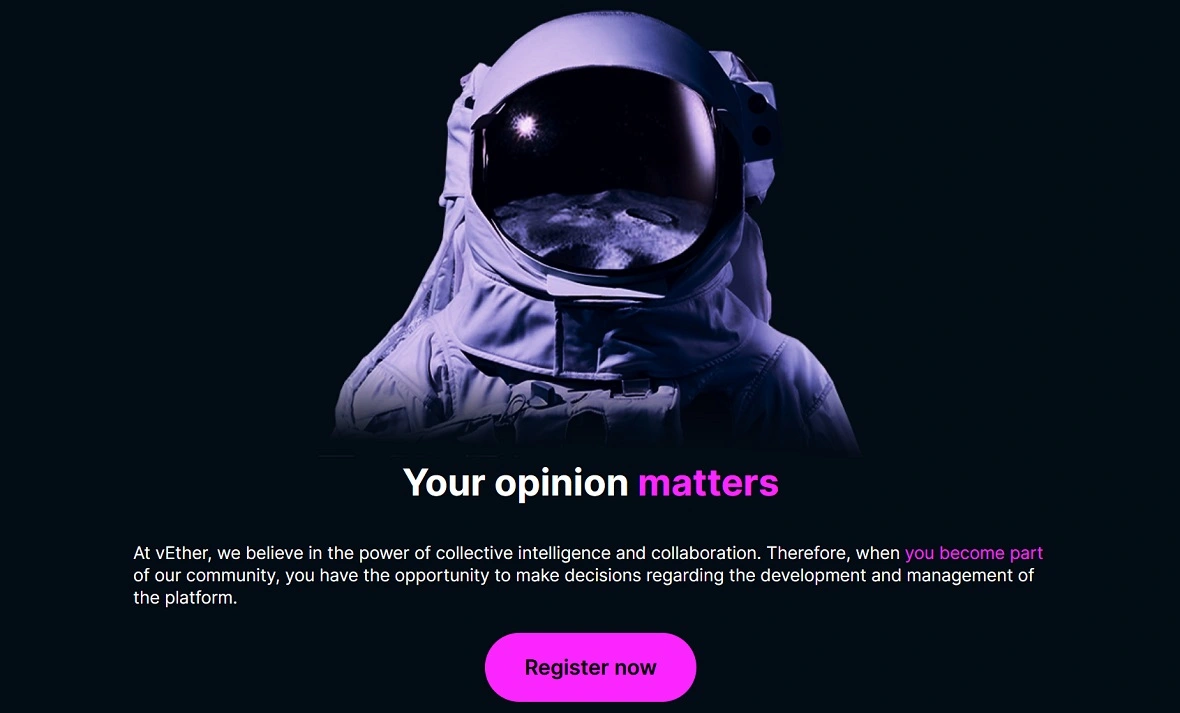
How does the new AMOS distribution operation work?
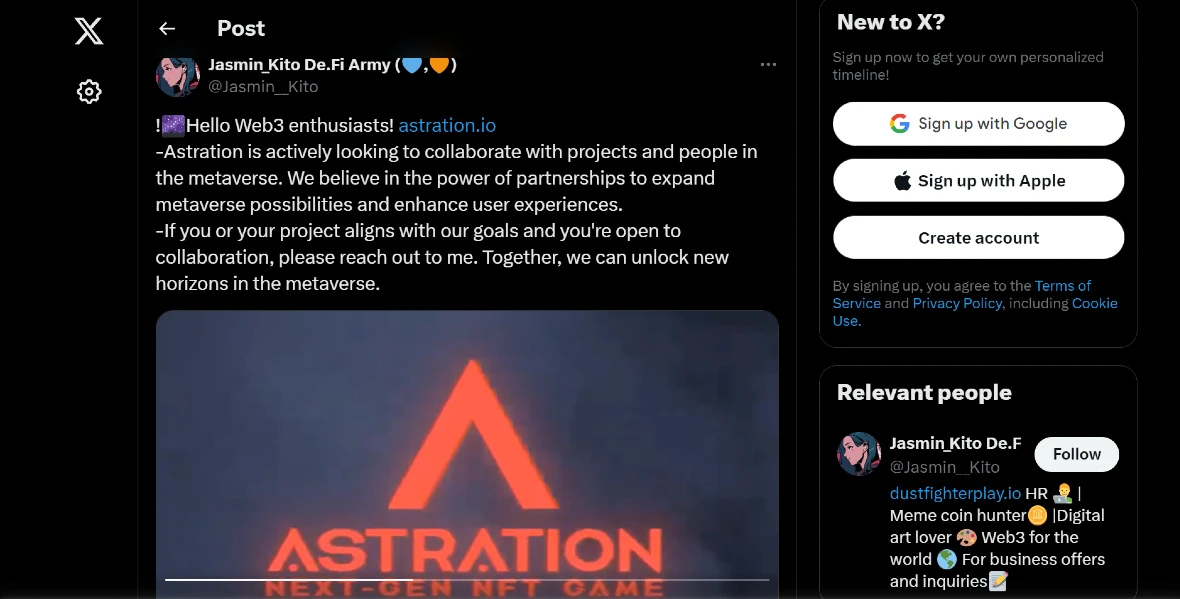
Bad actors operating under this new large-scale operation have created Web3 gaming projects that imitate known brands. They slightly change the name and style of popular projects and develop fake websites. They then create fake social media accounts and channels in messaging apps. From there, they post content on popular community sites, such as the NFT platform Open Sea.
Through social media, Telegram, and other messaging apps, criminals contact potential victims and trick them into engaging with fraudulent projects. The victims are then fooled into downloading malware from the fake sites.
The most-used malware in this campaign include Atomic macOS Stealer (AMOS), Stealc, Rhadamanthys, or RisePro, depending on the operating system.
Insikt Group found that criminals are using an AMOS version that can infect both Intel and Apple Macs. “The primary goal appears to be the theft of cryptocurrency wallets, posing a significant risk to financial security,” Insikt’s researchers said.
The full study analyzed components within the HTML code and identified a Russian link (Russian-language code comments and elements).
A dynamic, evolving, and active criminal gaming world
While the bad actors behind this new AMOS distribution campaign appear to be solely financially motivated, they are employing sophisticated tactics. To avoid detection and downtimes, their infrastructure is based on redundancy and continuity.
The group is capable of rapidly deleting all traces of a compromised fake site and rebranding to create new fake gaming projects.
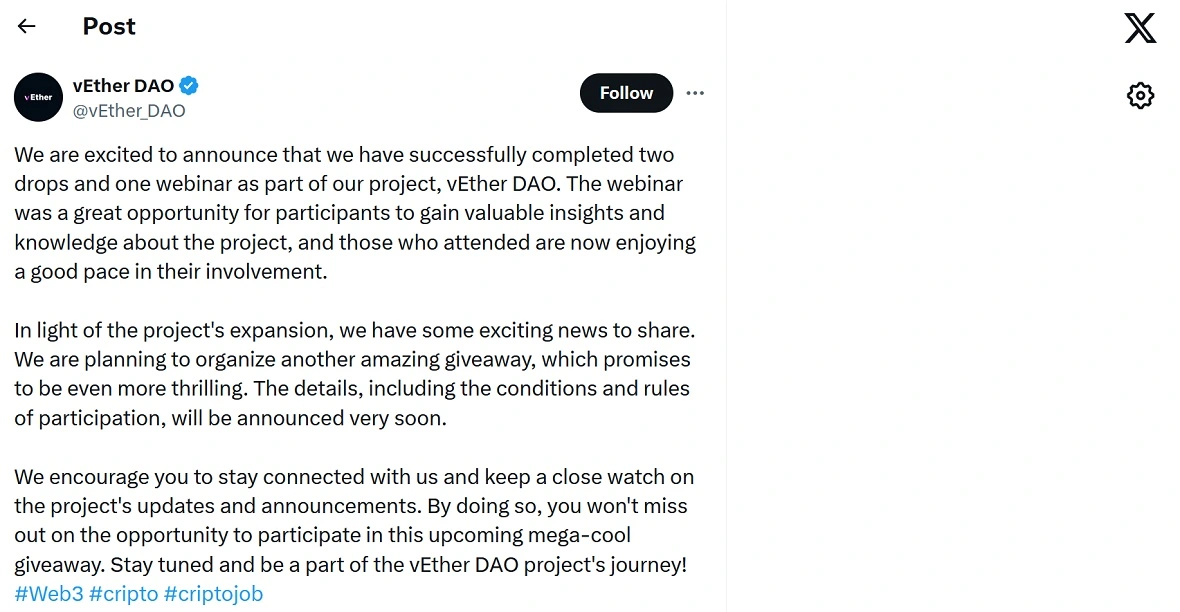
Moonlock checked the fake sites, social media channels, and the long list of domains and IP addresses identified by Insikt Group as vectors of attack. It was found that only 3 were still up and running. The rest had been erased by the criminal group.
As Insikt Group explains, this does not mean that the operation has been dismantled. Rather, it speaks of the capability that the criminal group has to rapidly delete fake content as it is identified by researchers, then release new projects with the purpose of spreading AMOS.
Insikt Group’s research shows that the criminals prepare their next series of targets and rapidly shift resources once disrupted or identified, making sure the operation continues even if it is exposed.
This constant and agile shape-shifting concept makes it impossible for researchers or organizations to monitor the group. The solution instead is to create awareness of how the attack works so potential victims do not fall into the vector.
Trap phishing: Web3 fake sites represent an exclusive blockchain criminal trend
The vector of attack and distribution techniques that this criminal organization is using are those of a “trap phishing” scheme. Trap phishing is a term that emerged in January 2024, when the Web3 smart contract auditor CertiK used it to describe a new criminal trend happening on Web3 blockchain platforms.
In trap phishing, bad actors duplicate known Web3 projects to attract victims and convince them to download a game or test it in exchange for blockchain crypto assets of financial value. Downloading the fake and malicious game or project automatically installs infostealer malware.
Once up and running on a victim’s device, the infostealer will steal credentials and passwords, as well as data that can be used to access the victim’s cryptocurrency wallet.
To bring in a constant flow of new potential victims, these groups have a team of workers who pretend to be gaming recruiters online. These fake recruiters use YouTube, X, Telegram, and other common Web3 social channels to engage with potential victims.
Additionally, the team of recruiters may also shift to bigger targets by posting fake work positions for game developers, Web3 experts, and other higher-paying roles within the industry.
Astration, ArgonGame, CosmicWay Reboot, and others
Only 3 of the 28 sites linked by Insikt Group to this criminal group are active. The rest were recently deleted. However, digital forensic analysis allows us to gain insights into the techniques used by the hackers.
For example, their Astration project, designed solely to distribute malware, duplicated a legitimate project named Alteration.

Similarly, gamestration[.]com attempted to pass as GameStation, and several links were created for DustFighter, Cosmic Game, ArgonGame (an active campaign), Cosmic Way Reboot, and others. Additionally, each project has several social media channels and uses online messaging apps for fake recruitment.
Fake websites and indicators of compromise linked to this operation include the following (only 3 of which are currently active):
- astration[.]io
- astrationplay[.]io
- astrationplay[.]com
- astrationgame[.]com
- astrationgame[.]io
- playastration[.]com
- gameastration[.]com
- dustfighter[.]io
- dustfighter[.]space
- dustfightergame[.]com
- dustoperation[.]xyz
- ai-zerolend[.]xyz
- cosmicwayrb[.]org
- argongame[.]com
- argongame[.]network (active)
- argongame[.]fun
- argongame[.]xyz (active)
- crypteriumplay[.]com
- playcrypterium[.]com
- playcrypterium[.]io
- worldcrypterium[.]io
- crypterium[.]world
- crypteriumworld[.]io
- crypteriumplay[.]io
- vether[.]org (active)
- vether-testers[.]org
How to protect yourself against this threat
While this new AMOS distribution campaign is rich in resources and utilizes in-depth knowledge of the Web3 gaming community, there are some crucial steps that users can take to protect themselves:
- Scrutinize Web3 projects: Be wary of unfamiliar Web3 games, especially those promising high financial rewards. Research the project thoroughly, checking for legitimacy through established platforms and communities.
- Verify sources: Do not download game files or applications from untrusted sources. Always rely on official developer websites or reputable app stores.
- Beware of social media recruitment: Ignore unsolicited job offers or project invitations, particularly on platforms known for crypto scams. Verify the legitimacy of any potential employer through independent channels.
- Maintain strong cybersecurity practices: Keep your operating system and software updated with the latest security patches. Utilize a reputable antivirus program and practice strong password hygiene with 2-factor authentication wherever possible.
- Educate yourself: Stay informed about current cyber threats, especially those targeting the Web3 space. Familiarize yourself with trap phishing tactics and learn how to identify red flags. By following these precautions, you can significantly reduce your risk of falling victim to AMOS stealer and other malware threats.
By following this advice, your security posture and your Mac security will be strengthened. And remember, never download files from suspicious contacts.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






