The most popular macOS stealer among cybercriminals, AMOS, has been updated with a backdoor. This innovation signals a significant and dangerous escalation.
In the past, the AMOS distribution gang, which is of Russian origin, focused solely on rapid smash-and-grab data theft. With the addition of a backdoor, it has the potential to hold its own with some very heavy threat actors.
Backdoors are mainly used by nation-state units, corporate espionage groups, and governments that surveil human rights groups, opposition parties, and journalists. These are the clientele the AMOS group will attract as they roll out the updated stealer with its ready-to-use backdoor. Let’s dive in.
Moonlock Lab discovers the second case of a macOS backdoor ever identified, and it’s inside AMOS
On July 4, Moonlock Lab reported that, for the first time, AMOS is being distributed with an embedded backdoor. With this backdoor, bad actors and operators who lease out AMOS from the developers will be able to literally take over a Mac like never before.
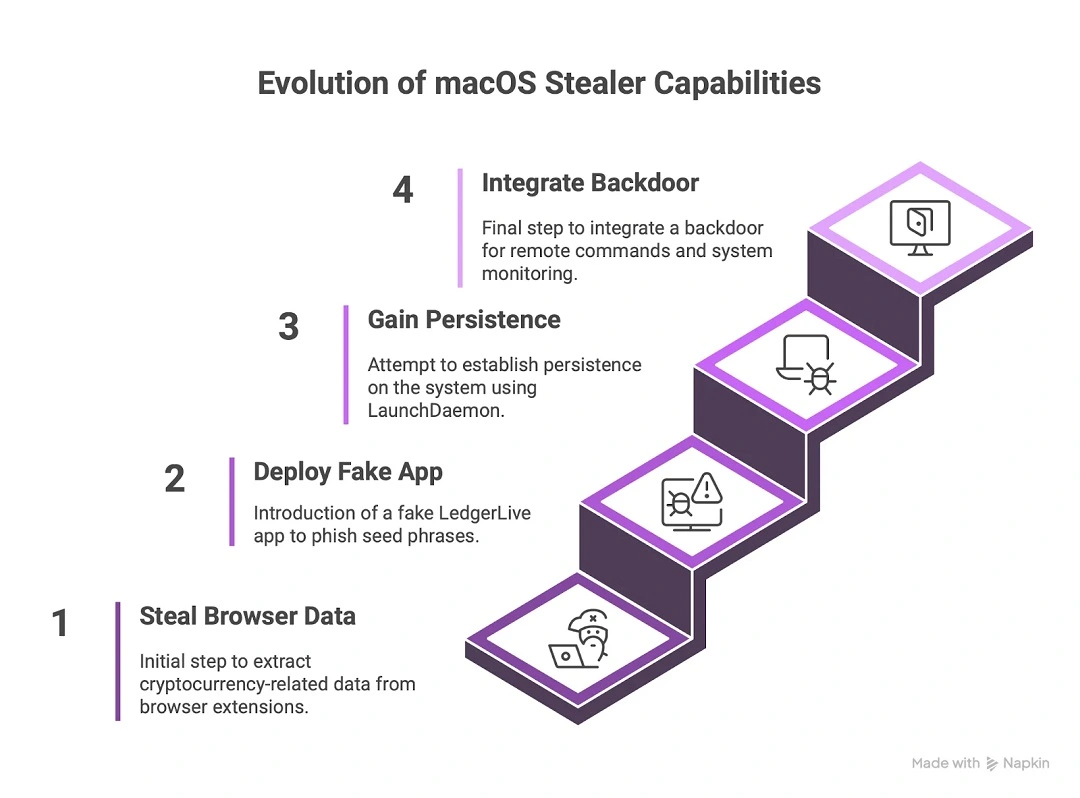
AMOS was already a powerful piece of malware, capable of stealing browser data, credentials, files, wallet keys, and more. The addition of an embedded backdoor allows attacks to persist in victim-infected Macs, run arbitrary tasks from remote servers, and gain extended control over compromised machines.
We asked the Moonlock Lab Team why developers would integrate a backdoor on AMOS.
“We suppose that the AMOS team may be responding to growing awareness and defenses around stealer malware,” the team said.
We suppose that the AMOS team may be responding to growing awareness and defenses around stealer malware.
Moonlock Lab
By maintaining persistent access, attackers can reinfect victims if the stealer is removed or update their payloads dynamically, Moonlock Lab added.
“Additionally, a backdoor allows attackers to harvest more over time — not just browser data or wallets, but screenshots, mic/cam access, or even install additional modules like keyloggers,” they said.
For high-value targets (e.g., crypto holders or enterprise users), attackers may want to stick around longer.
Why should I worry or care about AMOS’s new backdoor?
How significant is this new AMOS backdoor? Considering that AMOS is the malware most commonly used by cybercriminals who target Apple users and that it is widely available on the dark web for prices that have ranged from $1,000 to $3,000, this new development is something to take seriously.
More concerningly, AMOS distributors are following the steps of North Korean threat actors, who are known for having no problem crossing the lines into cyberwarfare, nation-state cyberattacks, and espionage.
Moonlock Lab explained that before this new AMOS backdoor, only 1 case of a macOS backdoor had been recorded.
“It is believed to be only the second known case — after North Korean threat actors — of backdoor deployment at a global scale targeting macOS users,” the Moonlock Lab Team said.
It is believed to be only the second known case — after North Korean threat actors — of backdoor deployment at a global scale targeting macOS users.
Moonlock Lab
As mentioned, AMOS is widespread. It has breached devices in more than 120 countries, including the United States, France, Italy, the United Kingdom, and Canada, among many others.
What can the AMOS backdoor do?
The new AMOS version will likely install hidden backdoors in thousands of devices if left unchecked by law enforcement. This means that operators who lease out AMOS and the developers of AMOS itself will have the ability to access, spy on, remotely control, and operate thousands of infected Macs.
With the addition of the backdoor, AMOS can now:
- Remotely execute arbitrary commands
- Gain full user-level access
- Persist on macOS even after a reboot
“For Mac users, this update means the threat is no longer limited to stolen credentials or documents,” Moonlock Lab reported. “It now opens the door to full system compromise.?
Additionally, thanks to this backdoor access, AMOS allows hackers to remotely install other malware, such as keyloggers.
The Moonlock Lab Team answers our questions
When asked about this potential third channel of distribution, the Moonlock Lab Team told us that their team already tracks extra activity related to a potentially new vector of distribution targeting high-value individuals/groups.
“However, currently, the AMOS group is focused on expanding their fake meetings campaign,” explained Moonlock Lab. The AMOS group is “adding more infection vectors to it so that it eventually becomes harder to track all of them.”
They disagreed that the AMOS effort would switch to espionage and new clientele.
“It looks like their main effort is still aimed at existing schemes while regularly dedicating some time researching other distribution vectors,” the Moonlock Lab Team said.
However, they added that AMOS is clearly moving closer to spyware-like functionality, especially with the inclusion of a persistent backdoor and the infrastructure to manage compromised machines long-term.
A revealing peek into internal messages from the AMOS gang
Internal chat messages of the AMOS distribution threat group, discovered by @g0njxa and shared with Moonlock Lab, specifically mention the addition of keyloggers in AMOS. Keyloggers are also typically found in spyware and precede the addition of audio, video, and screen recording.
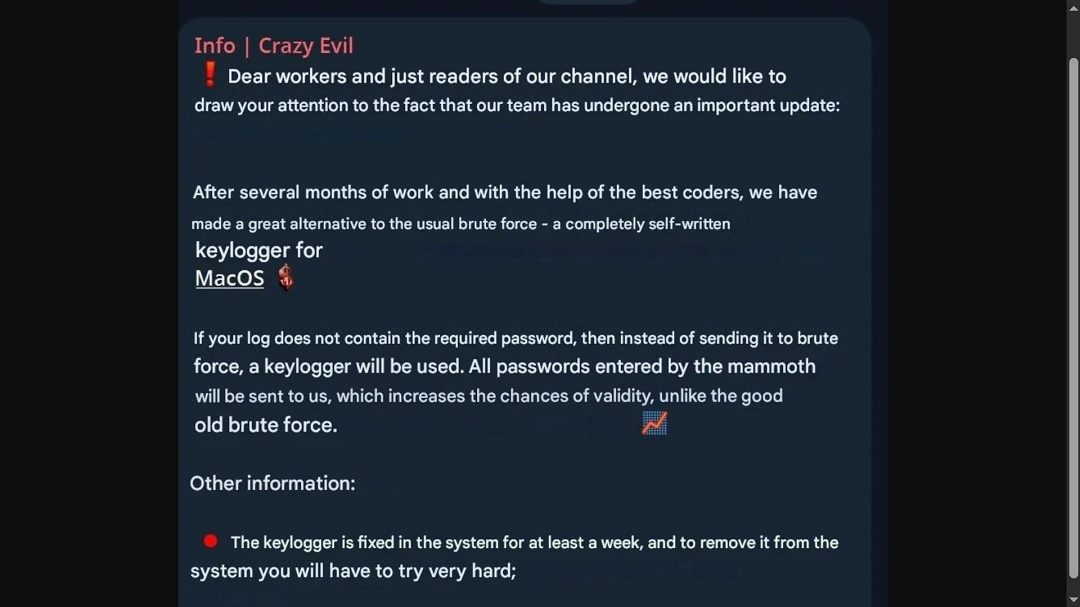
It is noteworthy to point out that the message shared by @g0njxa refers to the use of keyloggers for common data theft cyberattacks. These would be deployed if the usual brute forcing techniques (guessing passwords after passwords with automated software) seem to be failing.
AMOS and North Korean hackers now share a lot in common
A recent report from Sentinel One on North Korean threat actors — running an updated version of their “fake interview” campaign with fake malicious Zoom updates — highlights strikingly similar techniques between AMOS and the North Korean campaign.
Both backdoors:
- Target macOS systems
- Use scripting and compiled binaries in multi-stage attacks
- Implant AppleScript (or shell script wrappers) as initial implants to evade detection and deploy native Mach‑O binaries
- Allow remote command execution via a C2 channel
- Have evolved from data stealers to full-fledged persistent backdoors
Moonlock Lab said that AMOS and North Korean threat actors have been combining backdoor tech with stealer malware to target macOS attacks for some time now. Moonlock Lab highlighted not only similarities in the specific techniques but also in the groups being targeted, the vector of attack (phishing and downloads), and more.
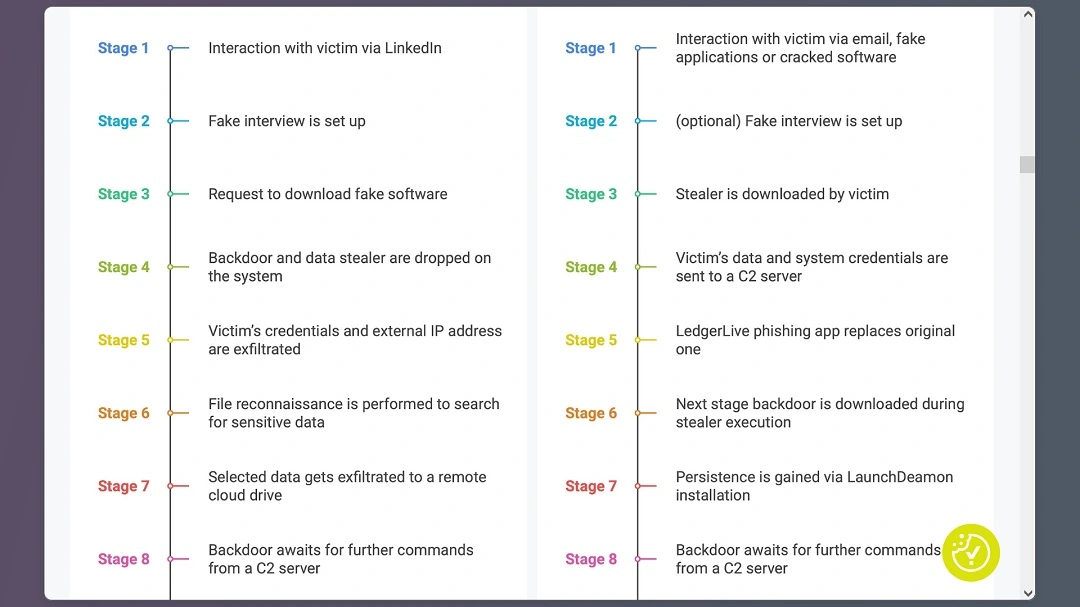
From stealers to backdoors, from theft to espionage and spyware
A comparison chart of the malware stages of North Korean hackers’ backdoor and the AMOS macOS stealer was made by Moonlock Lab. The comparison reveals so many similarities that it should send chills down the spine of any cybersecurity expert.
North Korean threat groups have also been combining crypto and data theft with nation-state and corporate espionage for some time now.
AMOS developers are either inspired by North Korean hackers’ campaigns, are connected and collaborating in some way, or simply want a piece of the illegal gains that the global spyware and espionage market has to offer.
“It’s clear that the Russia-affiliated authors of Atomic macOS Stealer are following in the footsteps of North Korean attack groups,” the Moonlock Lab Team said.
You can access the full Moonlock Lab technical report and a detailed analysis of the new AMOS and its backdoor here.
AMOS’s new infrastructure is live and hot; a new, more dangerous campaign seems inevitable
We know that AMOS has been distributed through 2 main channels or campaigns. In 1 of these, it is offered to those searching for cracked or fake software. In the other campaign, AMOS operators use spear phishing to go after high-value victims, such as large crypto holders.
Both of these campaigns lure victims through different fake offerings. One does so through malicious websites, while the other gets up close and personal with victims by offering them fake job interviews. However, now that AMOS has a backdoor, a third distribution channel and campaign could emerge.
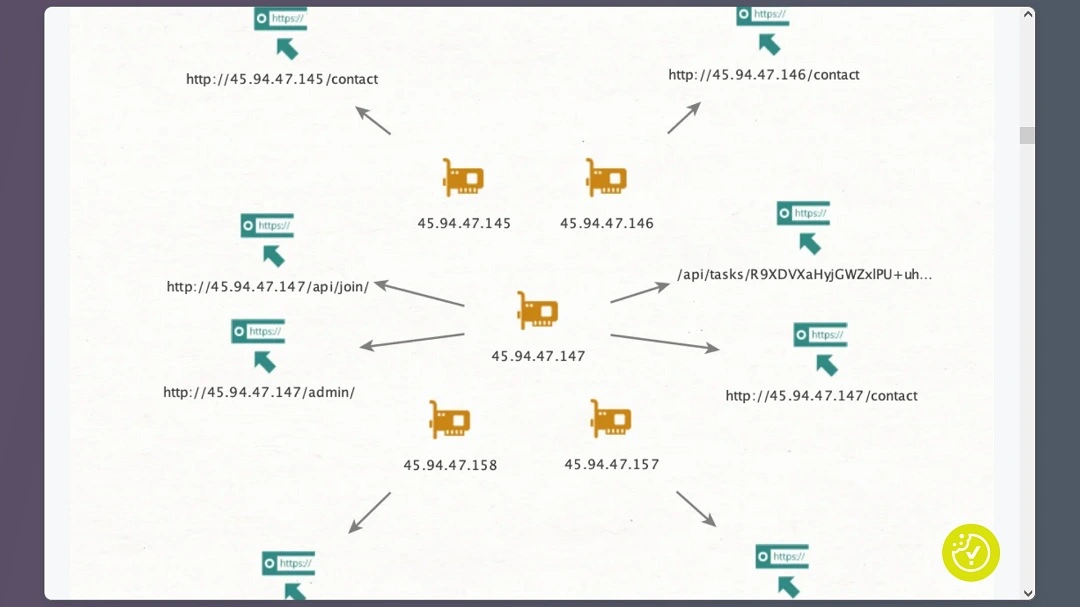
“We constantly see their C2 servers adding up more functionality, which looks like some bot-managing software,” the Moonlock Lab Team said.
Going into more specifics on what might come, they explained that the Russia-affiliated group may also be learning from APT playbooks to improve campaign effectiveness or even attempting to blur attribution by mimicking DPRK TTPs (tactics, techniques, and procedures). “But we haven’t seen the direct evidence of their collaboration just yet,” they said.
Who will be targeted with the new AMOS?
Besides the capability to continue to breach the devices of known victim groups, we expect AMOS to be used against even higher-level individuals. What kind? The kind of individuals that a hacker would need to have direct access to the infected Mac to run specific scripts in real time.
Yes, this is scary. And it’s as sophisticated as it gets.
Another possibility, as the internal message from the threat group that @g0njxa shared implies, is that the AMOS group developed this backdoor to provide operators with the ability to take over when the malware is not achieving the specific result it needs. If this is the case, the backdoor was developed to enhance data theft. However, this does not exclude espionage threat actors from targeting macOS victims with AMOS.
One thing the Moonlock Lab Team is certain of is that a new wave of AMOS cyberattacks is inevitable and coming soon.
“A new AMOS command-and-control (C2) infrastructure is currently live and responsive,” Moonlock Lab said. “This is clear evidence that the campaign has already been launched and is in full swing.”
Understanding how backdoors can be used by attackers
Much of the AMOS stealer involves automated scripts, lines of code that someone wrote to perform specific actions. These actions can be wide-ranging, such as “search for this and that file” or “go to this URL and download a payload.”
These lines of code, which are automated and self-executable in malware, can be expanded with new functions or even written in real time by advanced black hat hackers.
A backdoor gives AMOS threat actors this specific capability. They can, at any time, jump into the breached machine and write specific malicious code or use a library of ready-to-deploy tasks (prewritten code designed for specific purposes).
Moonlock Lab said that “it is fair to assume that there is a pool of so-called ‘tasks’ fetched by infected machines and executed on a compromised system, thanks to this backdoor.”
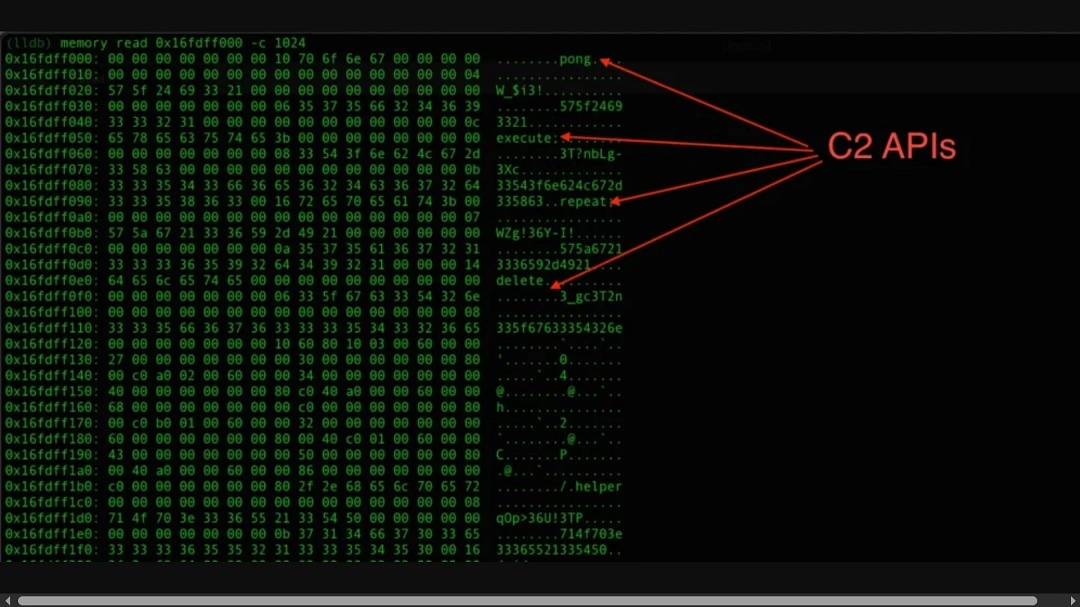
The team of researchers at Moonlock Lab also believes that further modifications to the backdoor will appear soon.
Backdoors developed by North Korean threat actors used at least 13 separate C2 commands, with additional ones included for logging, Moonlock Lab said, as a signal of what may soon come to AMOS.
“Currently, it looks like the infamous developers of macOS stealers have only taken their first steps into a new niche on the market,” they said. “There can be no doubt that this represents a high level of danger for macOS users.”
Final thoughts
The specific details of what Mac users should be on the lookout for are still unknown. What is clear is that by developing and embedding a backdoor into their malware, the AMOS gang has shifted away from cybercrime to more dangerous territory.
The new ability of this malware will not only attract more sophisticated threat groups but will also cause more damage, damage such as that which we see during persistent cyberattacks.
In a way, because AMOS is like a Swiss army knife, has so many features, and has been updated so many times, the addition of a backdoor is not entirely a surprise. However, of all the things that black hat hackers could have integrated into AMOS malware, a backdoor, more than anything else, escalates the threat of this malware to unprecedented levels.
Our advice is to stay on top of AMOS news to understand the lures and prevent this backdoor from breaching your Mac.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






