North Korean hackers have been behind a “fake interview” malware campaign over the past year. Now, the threat actors have made an interesting update. While the update does not change how the well-known job interview scam works, it takes cybersecurity researchers on a wild ride by using new programming languages. Let’s explore this development.
Sentinel One pulls back the curtain on North Korean use of new programming languages
On July 2, Sentinel One released a deep technical analysis of new updates used by North Korean hackers. As mentioned, the threat group has not changed its attack vector for its “fake interview” campaign.
As we have covered numerous times, the fake interview campaign used by North Korean hackers involves spear phishing individuals or businesses in the Web3, crypto, and blockchain industry. Luring them with the promise of a job, the black hatters set up fake interviews via Zoom.
Once a victim agrees to an interview, the hackers send them a malicious, fake Zoom update via email. Opening the “update” allows scripts to run on macOS and payloads to be downloaded.
What follows is a breach of their device. From there, the hackers empty out e-wallets, stealing crypto assets and personal data.
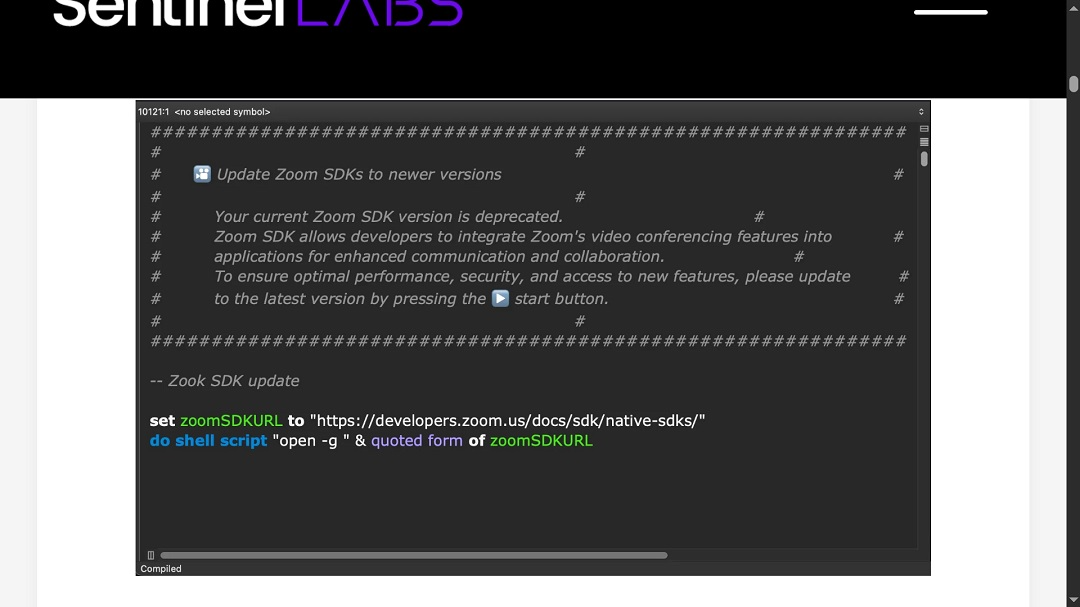
This vector of attack has remained the same for at least a year. The reason why North Korean hackers have not changed is because, evidently, it still works like a charm. However, they have introduced some new developments.
Now, in order to confuse cybersecurity researchers and avoid raising automated flags online, North Korean black hat hackers have switched to using new programming languages.
Languages like Nim, which are now being leveraged in the “fake interview” campaign, are niche and relatively new. And since some cybersecurity researchers may be unfamiliar with newer programming languages like Nim, using them gives hackers an edge.
Additionally, most automated online and on-device anti-malware checks and security guardrails may also be unfamiliar with newer programming languages. As such, they might fail to detect suspicious activity.
“DPRK threat actors are utilizing Nim-compiled binaries and multiple attack chains in a campaign targeting Web3 and Crypto-related businesses,” Sentinel One reported.
A closer look at North Korean malware coding developments
In addition to Nim, North Korean hackers are avid coders, sometimes using multiple coding languages. They also manage AppleScript — native to the Apple environment, Java, and C++.
The trend of using multiple, newer programming languages during cyberattacks coding languages isn’t exclusive to North Korean hackers. Other groups, like the threat actors behind AMOS, are picking it up as well.
In the past, malware like ransomware would be written mostly in a single programming language. New languages like Go might be introduced, but for the most part, only a single language would be used. However, cybercriminal groups are now mixing different scripts, binaries, and languages in individual attacks.
From a cybersecurity standpoint, it’s like a hacker throwing 5 dictionaries at you, all encrypted, each with a different language. Figuring out exactly what is going on and what the malware is doing becomes a nightmare.
The Sentinel One report, which guides us step by step through how North Korean hackers mix various languages in a single cyberattack, revealed just how complex these new techniques can be, even for the most tech-savvy experts.
“Analysis revealed an attack chain consisting of an eclectic mix of scripts and binaries written in AppleScript, C++, and Nim,” Sentinel One reported.
Analysis revealed an attack chain consisting of an eclectic mix of scripts and binaries written in AppleScript, C++, and Nim.
Sentinel One
“Although the early stages of the attack follow a familiar DPRK pattern using social engineering, lure scripts, and fake updates, the use of Nim-compiled binaries on macOS is a more unusual choice.”
Previous reports on North Korean hackers’ cyberattacks by Huntress and Huntabil.IT reveal that the use of mixed programming languages and Nim has evolved in the past couple of months — with significant speed and efficiency. The use of AI coding tools is probably why cyber gangs are capable of making this switch so fast.
Why are cybercriminals using new languages and mixing them up?
When asked why cyberattackers would initiate a shift in languages, Sentinel One said it’s part of the eternal “cat and mouse game” between threat and threat detection. “When one side innovates, the other must respond,” Sentinel One researchers said.
Sentinel One called for analysts, researchers, and detection engineers to “invest effort in understanding these lesser-known languages and how they will eventually be leveraged.”
How new, niche code affects Apple end users
Apple end users are also affected by the use of these new programming languages. Because security guardrails and anti-malware technology may fail to recognize suspicious activity in these lines of code, the attack becomes more evasive, persistent, and stealthy.
Apple users who could previously detect malware based on the behavior of macOS may now struggle to identify a breach.
Despite these new coding language techniques, the North Korean attack still relies on social engineering to succeed. Therefore, we suggest that all Apple users remain vigilant, especially if they work in the blockchain, crypto, or Web3 industry and are looking for a new job. The same goes for users who receive cold messages from unknown contacts offering a position or an interview.
“The target (victim) is subsequently sent an email containing a Zoom meeting link and instructions to run a so-called ‘Zoom SDK update script,’” Sentinel One reported.
The data that North Korean hackers are after
Using this new technique, North Korean hackers are targeting the following:
- Browser-stored credentials and sessions: This includes data pulled from Chrome, Brave, Edge, Firefox, and Arc — such as saved passwords, session cookies, and browsing history tied to crypto exchanges or wallets
- macOS Keychain passwords: Hackers seek full access to credentials stored in Keychain, which may include logins for wallets, exchanges, and other financial services.
- Telegram user data: Local encrypted databases, key blobs, message history, possibly 2FA codes, and wallet addresses communicated via Telegram are of particular interest to hackers.
- System and environment data via backdoor commands: The malware communicates over secure WebSocket (wss) and may execute shell commands, dump system info, inspect running processes, and exfiltrate selected files.
What can I do to stay safe? Do not update your Zoom with strange links
Our advice to keep safe from this threat is not to run Zoom updates unless they are sourced from official Zoom channels or the Apple App Store.
Sentinel One identified the following domains impersonating the legitimate domain of Zoom (us05web.zoom[.]us) for the malicious Zoom update:
- support.us05web-zoom[.]forum
- support.us05web-zoom[.]pro
- support.us05web-zoom[.]cloud
- support.us06web-zoom[.]online
For the full technical analysis of this new North Korean hackers’ cyberattack, check out Sentinel One’s report.
Final thoughts
North Korean hackers aren’t the only cybercriminals turning to new programming languages and mixing scripts to run their attacks. This is a trend we have seen on the rise in the past months. As such, the use of multiple languages in cybercrime is a movement worth tracking.
Each language or script, whether Bash, AppleScript, Java, C++, Go, or Nim, has its unique strengths. When combined in a single cyberattack, they can create a formidable threat.
As mentioned, the rise of AI coding tools is likely accelerating this trend, allowing threat actors to learn, adapt, write, edit, test, and deploy code in different languages with greater speed and accuracy.
To respond, cybersecurity researchers can also turn to AI coding tools to augment their capabilities, increase their understanding of new languages, and level up their game.
In the end, the concept behind these North Korean cyberattacks remains the same. This is good news for users. It means that with a proper focus on cybersecurity awareness (not installing unknown software or responding to unsolicited requests from strangers), these incidents can be prevented.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc. Zoom is a trademark of Zoom Video Communications, Inc.






