Apple ID security is extremely difficult to hack via malware. However, if criminals get hold of your Apple credentials, things can go wrong very fast. A recent report from Broadcom, the company that acquired Symantec in 2019, found that active smishing campaigns are currently targeting Apple users. These new cybercriminal campaigns heavily leverage the trust that users have in Apple.
Fake Apple iCloud SMS targets vast pool of victims
Bad actors are sending out smishing attacks via SMS communications impersonating Apple itself. The attackers’ main goal is to exfiltrate the victim’s Apple IDs. According to Boracom, these smishing campaigns are widespread and active, and they reach a “vast pool of potential victims.”
One example of an SMS message identified in this wave of attacks reads as follows:
“Apple important request iCloud: Visit sign in[.]authen-connexion[.]info/iCloud to continue using your services.”
Apple users who clicked on this link (now defunct) would be redirected to a CAPTCHA. After completing, they were automatically sent to a malicious web page using an outdated iCloud login template to appear legitimate.
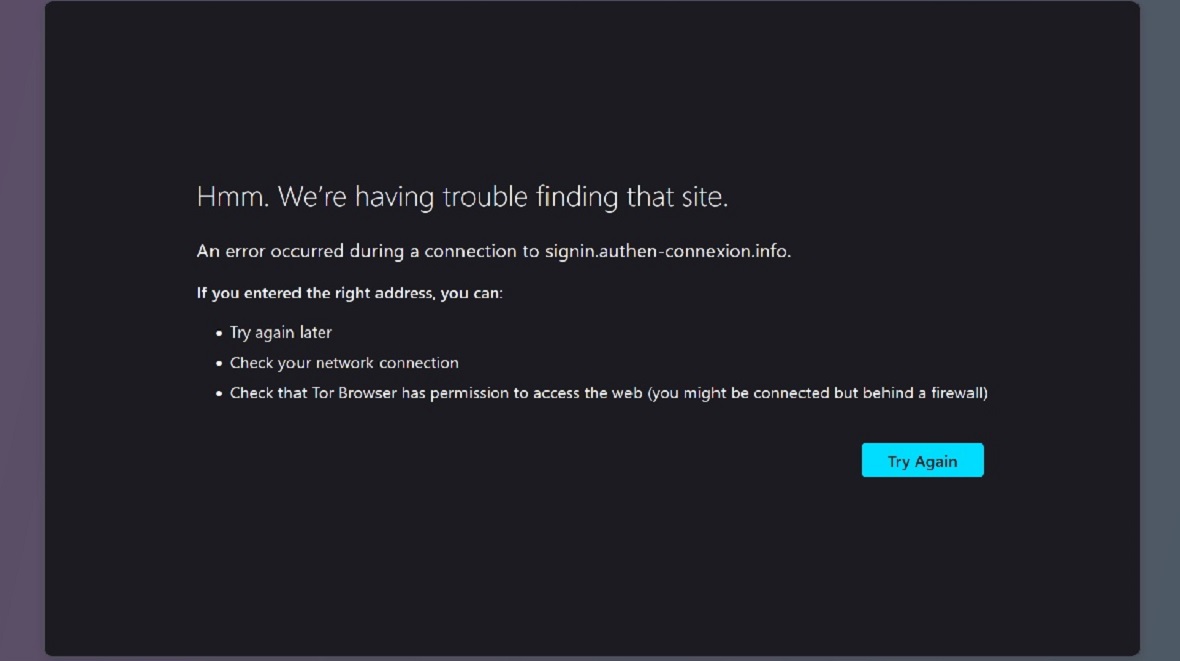
The malicious links, sent via SMS, work on iPhones and Macs alike.
As mentioned, the trust that the Apple brand carries among its users goes a long way. And while there is nothing extravagant about how the attack works, the simplicity of the tactic makes it efficient.
A little digging reveals how Apple ID attackers covered their tracks
Who is behind these campaigns? What is their infrastructure? Where are they based? And how many fake sites and malicious SMS messages have they sent out? The Broadcom report, while presenting necessary security information and warnings for the Apple community, leaves us with more questions than answers.
Moonlock checked the registrant information of the only malicious site identified by Broadcom for this campaign: sign in[.]authen-connexion[.]info/iCloud.
What we found comes as no surprise. Naturally, the fake website that impersonated the iCloud sign-in page has been shut down. This was most likely done by the attackers, as they were content to count their losses when the criminal campaign was exposed to the public.
A WHOIS search revealed that the domain is registered to NameSilo — an online site offering cheap domains. One thing we can say is that this particular campaign is relatively new. The site was registered on June 4, 2024. This means that bad actors were actively targeting Apple users for at least an entire month before they were discovered.
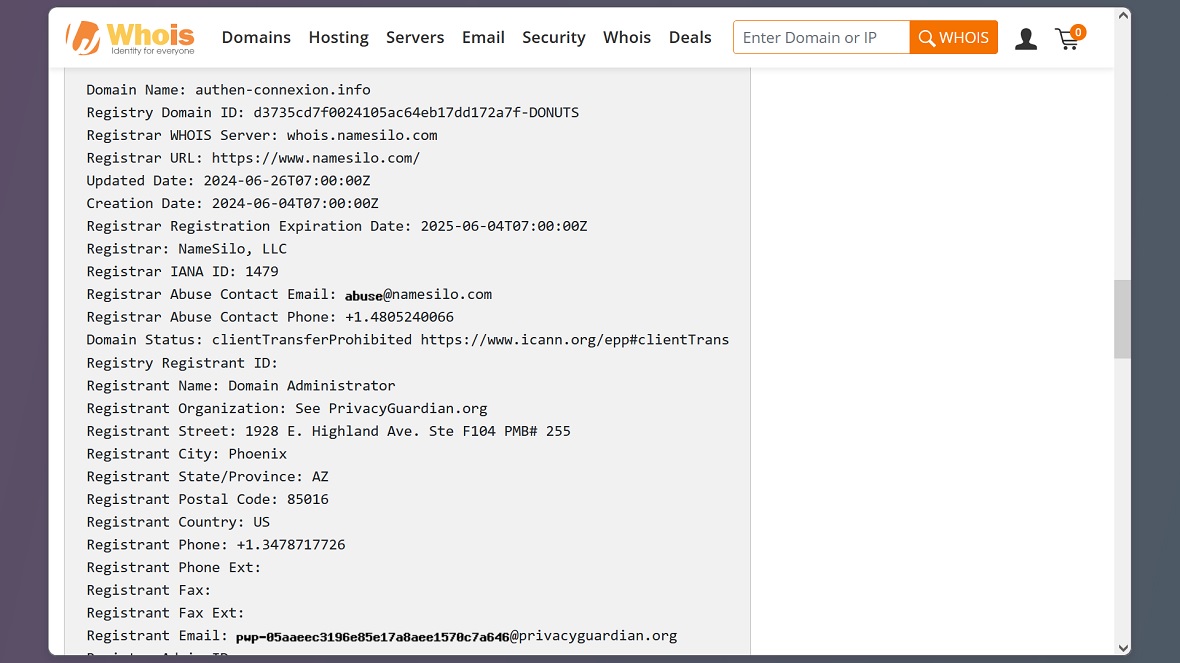
Privacy service leveraged for malicious purposes in Apple ID smishing attacks
The malicious domain “Status” is listed as “clientTransferProhibited”2.” This means that whoever registered the domain didn’t want it to be transferred or hijacked.
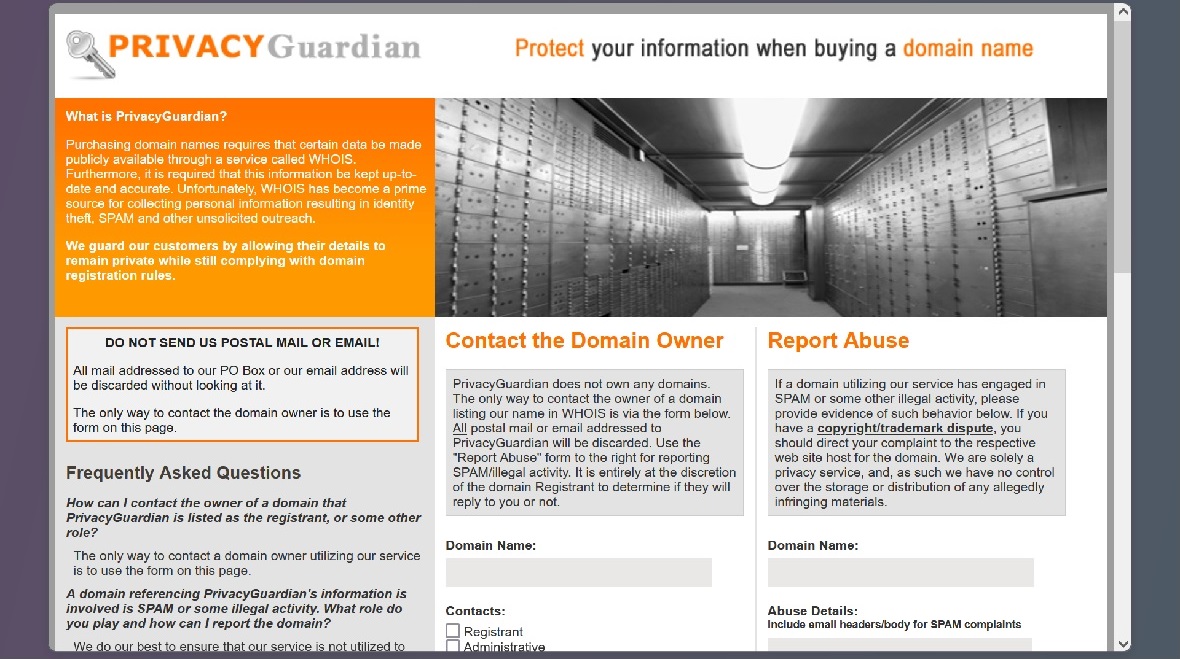
Additionally, the registration of a domain requires users to submit data such as the name of the organization, domain administrator, address, email, and phone. Cybercriminals in this operation chose to use PrivacyGuardian.org.
PrivacyGuardian provides its own data to WHOIS, guarding users by allowing their details to remain private while still complying with domain registration rules. By using this service, the attackers managed to check all the required boxes while leaving no contact information that could leave a trail back to them.
These domain registration tactics are very common among cybercriminals. The malicious domain is set to expire one year from now, in June 2025.
Phishing and smishing are not new for Apple: Here’s how to stay safe
Phishing and its many variants have plagued Apple in the past. The company’s official support page for phishing, smishing, and vishing —- email, SMS, or phone call scams and attacks — guides users on how to recognize and avoid common social engineering schemes.
Apple explains that scammers often pretend to be representatives of a trusted company. In this case, the company is Apple itself.
Apple says that if you receive a fake message that is made to look as if it is from Apple, you should take a screenshot of it and email it to [email protected].
It’s important for users to remember that fraudulent messages may come in the form of email messages, pop-ups, and phony calls from fake Apple Support representatives or Apple partners. Attackers might even send victims unwanted Calendar invitations and subscriptions.
Apple breaks down how users should proceed with suspicious messages:
“If you’re suspicious about an unexpected message, call, or request for personal information, such as your email address, phone number, password, security code, or money, it’s safer to presume that it’s a scam — contact that company directly if you need to.”
Victims who believe that their Apple ID has been compromised, or have typed in their password or other personal information on a malicious website, must immediately change their Apple ID password and enable 2-factor authentication.
When receiving SMS or email messages with links, double-check the URL and never share information with unknown sources.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Apple ID and iCloud are trademarks of Apple Inc.