For the second time in less than a month, Apple released a new emergency security update in a rush to patch vulnerabilities. Early in September, Apple rolled out a security update to patch the BLASTPASS zero-day exploits discovered by Citizen Lab. About 2 weeks later, Chrome, Firefox, Bing, Signal, and other top web browsers followed through with updates linked to BLASTPASS.
Now, on September 21, Apple once again released security updates and Rapid Security Responses for 3 new vulnerabilities, once again discovered by Citizen Lab. The updates are for iOS, iPadOS, macOS, watchOS, and Safari.
All the Apple devices affected by the new exploits
To date, Apple has not officially made public the technical details of the upgrade nor the vulnerabilities. The company’s policy is not to disclose or confirm security issues until after an investigation has concluded and the security upgrades are available for all users.
Apple reported that the following devices and operating systems have new security updates, all released on September 21:
- Safari 16.6.1 for macOS Big Sur and Monterey
- iOS 17.0.1 and iPadOS 17.0.1 for:
– Phone XS and later
– iPad Pro 12.9-inch 2nd generation and later
– iPad Pro 10.5-inch
– iPad Pro 11-inch 1st generation and later
– iPad Air 3rd generation and later
– iPad 6th generation and later
– iPad mini 5th generation and later - iOS 16.7 and iPadOS 16.7 for:
– iPhone 8 and later
– iPad Pro (all models)
– iPad Air 3rd generation and later
– iPad 5th generation and later
– iPad mini 5th generation and later - watchOS 10.0.1 for Apple Watch Series 4 and later
- watchOS 9.6.3 for Apple Watch Series 4 and later
- macOS Ventura 13.6 for macOS Ventura
- macOS Monterey 12.7 for macOS Monterey
Google and Citizen Lab discover spyware attacks in the wild in Egypt
All 3 zero-day vulnerabilities that Apple is remediating through these updates were discovered and reported to the company by Bill Marczak of Citizen Lab and Maddie Stone of Google’s Threat Analysis Group (TAG).
On September 22, Maddie Stone from Google’s TAG reported that, working alongside Citizen Lab, they discovered an attack between May and September 2023 on the former Egyptian MP Ahmed Eltantawy. Eltantawy was targeted with Cytrox’s Predator spyware after he announced his plans to run for president in the 2024 Egyptian elections. The attack used all 3 of the recently patched vulnerabilities.
The vulnerability CVE-2023-41993 affects Safari and allows bad actors to create malicious online web content that could lead to arbitrary code execution.
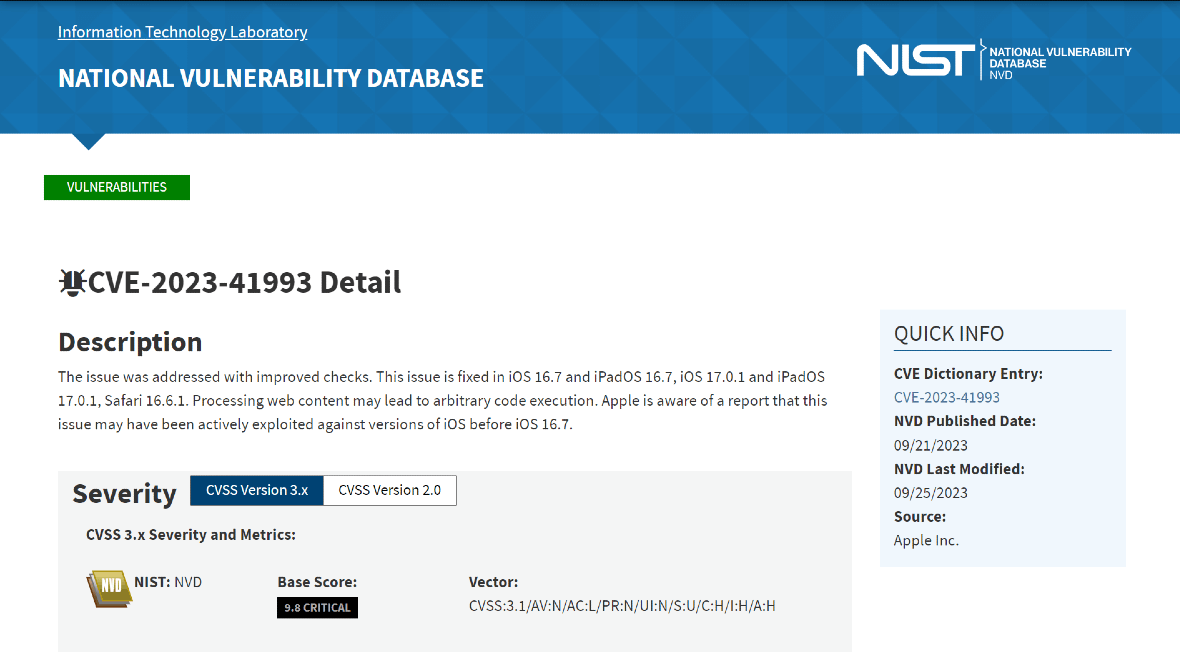
On the other hand, iPhones and iPads were affected by the vulnerability CVE-2023-41992, which allowed attackers to elevate their privileges. Finally, the fix for CVE-2023-41991 in the Security framework puts an end to possible exploits done by malicious apps that could bypass signature validation — a key security process.
Understanding the man-in-the-middle zero-click attack
Google’s TAG explained that this type of attack is a man-in-the-middle (MITM) attack.
Here’s how MITM attacks work:
- A cybercriminal intercepts when a victim tries to access a website, or they send them a link via message or email.
- The attacker alters the victim’s traffic and redirects them to a malicious site.
- Once on the site, they use the vulnerability CVE-2023-41993 to execute a remote code on Safari.
- Later, they use the vulnerability CVE-2023-41991 to bypass validation checks.
- Finally, they use CVE-2023-41992 to escalate local privileges. This is when the attackers gain a foothold in the device.
- Once criminals have access to the device, they can steal data, install malware, launch attacks, and install spyware.
It is important to note that while the attackers need to intercept traffic to be successful, this is still a zero-click attack, as victims can be affected even if they don’t download a file, click a link, or respond to emails or messages.
What should Apple users do?
All iPhone, iPad, Apple Watch, and Mac users should install the new updates immediately to increase their safety and privacy.
How to update your iPhone or iPad wirelessly
- Back up your device with iCloud or your computer.
- Plug in your iPhone or iPad to make sure you do not lose power during the update.
- Connect to Wi-Fi (do not do security updates over public Wi-Fi or networks).
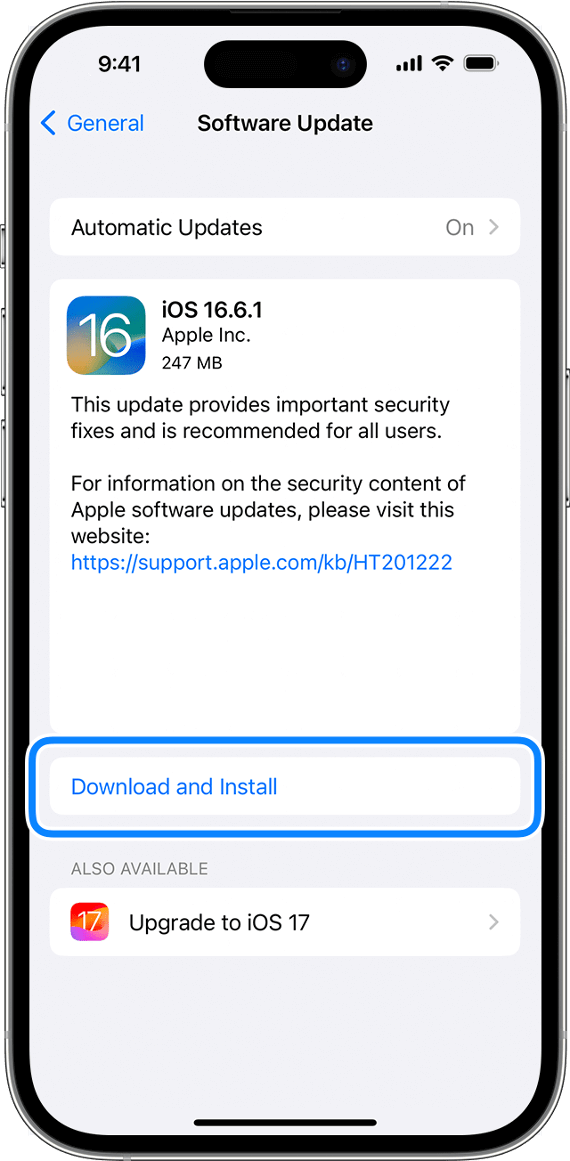
- Go to Settings, General, and Software Update.
- Select the update you want to install from the list and tap Install Now. You might be asked to enter your passcode.
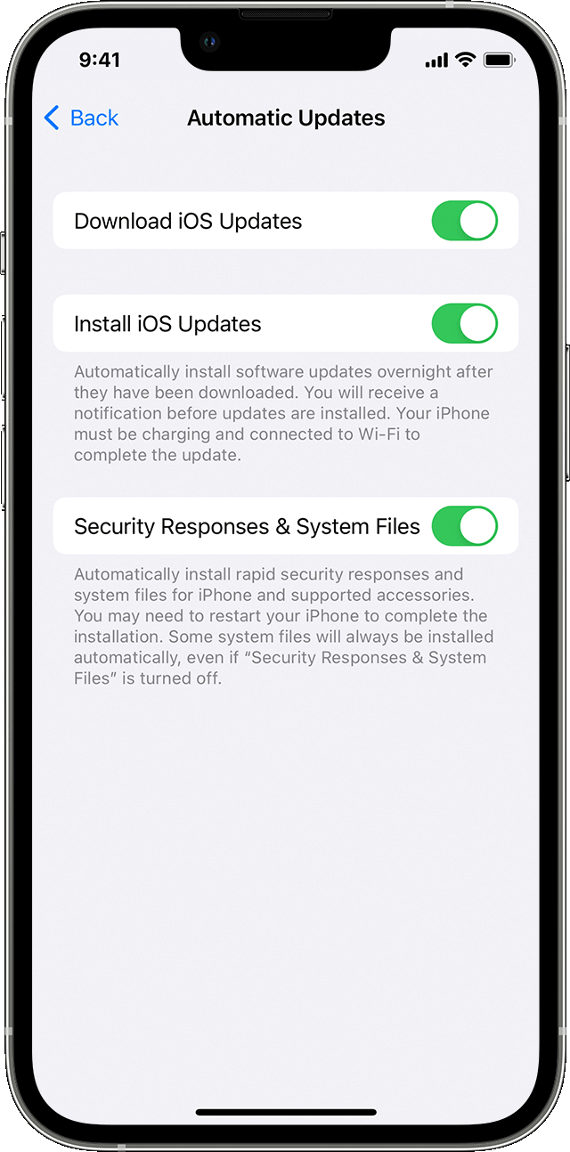
Users should also make sure that automatic updates are enabled. To do this:
- Go to Settings, General, and Software Update.
- Tap Automatic Updates and turn on Download iOS Updates.
- Finally, turn on Install iOS Updates.
Remember that some updates may still require manual download.
How to update your Mac
- Go to the Apple menu.
- Select System Settings and click General on the left side of the window.
- Click Software Update on the right.
You can also update your Mac by going to the Apple Menu, selecting System Preferences, and clicking Software Update.
How to update your Apple Watch
- On your iPhone, go to the Apple Watch app.
- Tap the My Watch tab, then General, and Software Update.
- Enter your passcode if asked.
- Allow the progress wheel that appears on your Apple Watch to finish.
You can also update directly from your Apple Watch as long as it is connected to Wi-Fi. To do this, just go to the Settings app on your watch, select General, and choose Software Update.
Whether it’s your iPhone, iPad, or Apple Watch, remember that it must be connected to Wi-Fi and plugged into the charger beforehand to avoid interruptions. Don’t restart the device. If a restart is needed, it will do so automatically.
Protect yourself from high-profile attacks with Lockdown Mode
If you believe that you are being targeted in a sophisticated cyberattack, turn on Lockdown Mode immediately. Lockdown Mode was built specifically to protect Apple users from spyware and nation-state high-profile cyberattacks.
How to turn on Lockdown Mode on your iPhone or iPad
- Go to the Settings app.
- Tap Privacy & Security.
- Scroll down and tap Lockdown Mode.
- Tap Turn On Lockdown Mode.
- Select Turn On & Restart and enter your device passcode.
How to turn on Lockdown Mode on your Mac
- Go to the Apple menu and select System Settings.
- Click Privacy & Security on the sidebar.
- Scroll down, click Lockdown Mode, and click Turn On.
- Select Turn on Lockdown Mode and enter your user password if asked.
- Confirm the operation by clicking on Turn On & Restart.
Remember that before you turn on Lockdown Mode, your device must be updated. And Lockdown Mode needs to be turned on individually on each Apple device.
We also recommend that all users be extra cautious when receiving messages, SMS, or emails from unknown sources, and always double-check the web addresses of the sites that you are visiting. By following these recommendations and updating all your Apple devices, your security and privacy will be improved.