Recently, we saw a suspicious file in our sandbox. After some research and analysis, we found the following post on the X social media platform. The post mentions a macOS backdoor known as SpectralBlur, a file that wasn’t previously detected by antivirus vendors.
At first glance, the file looked like the new variation of a SpectralBlur. We took a closer look at this file for further analysis.
What we know about the SpectralBlur backdoor so far
Generally, a backdoor has capabilities that allow it to get remote access to an infected Mac, execute shell commands, and take other actions, such as gaining access to personal data or creating persistence.
The first thing we did was check this file on VirusTotal for detection by AV vendors. You can see the details of what we found on SpectralBlur in the screenshot below.
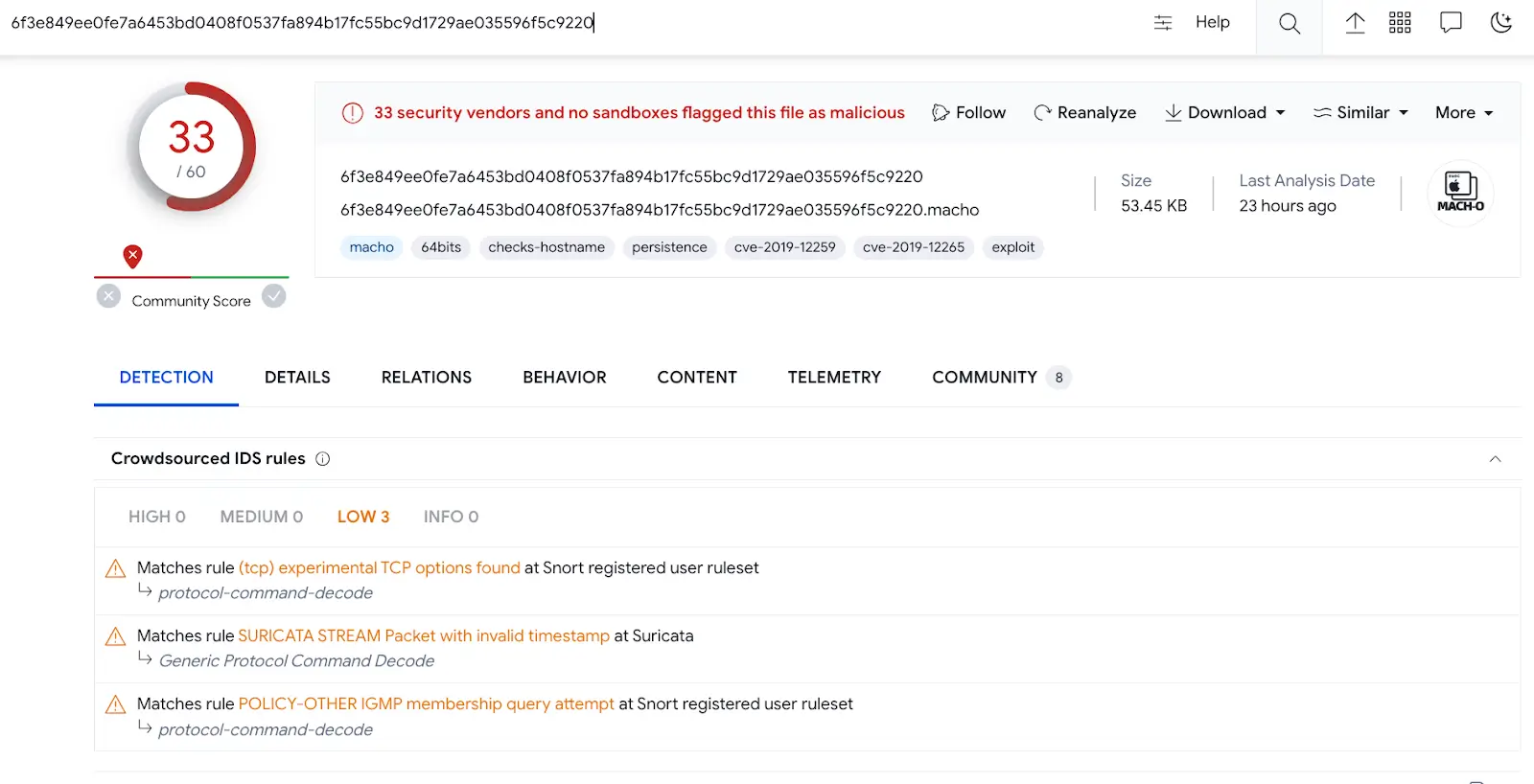
As you may already know, VirusTotal allows users to check suspicious files for malware detection and shares the results with us.
In the case of SpectralBlur, we discovered that this backdoor had been detected in most of the presented antivirus programs.
How the socket connection function works in SpectralBlur
During malware analysis, we found cross-references with functions that use sockets.
As you can see in the screenshot below, connection with a remote C2 (command-and-control) server is being carried out by sockets. This allows computer interactions over the network using system APIs.
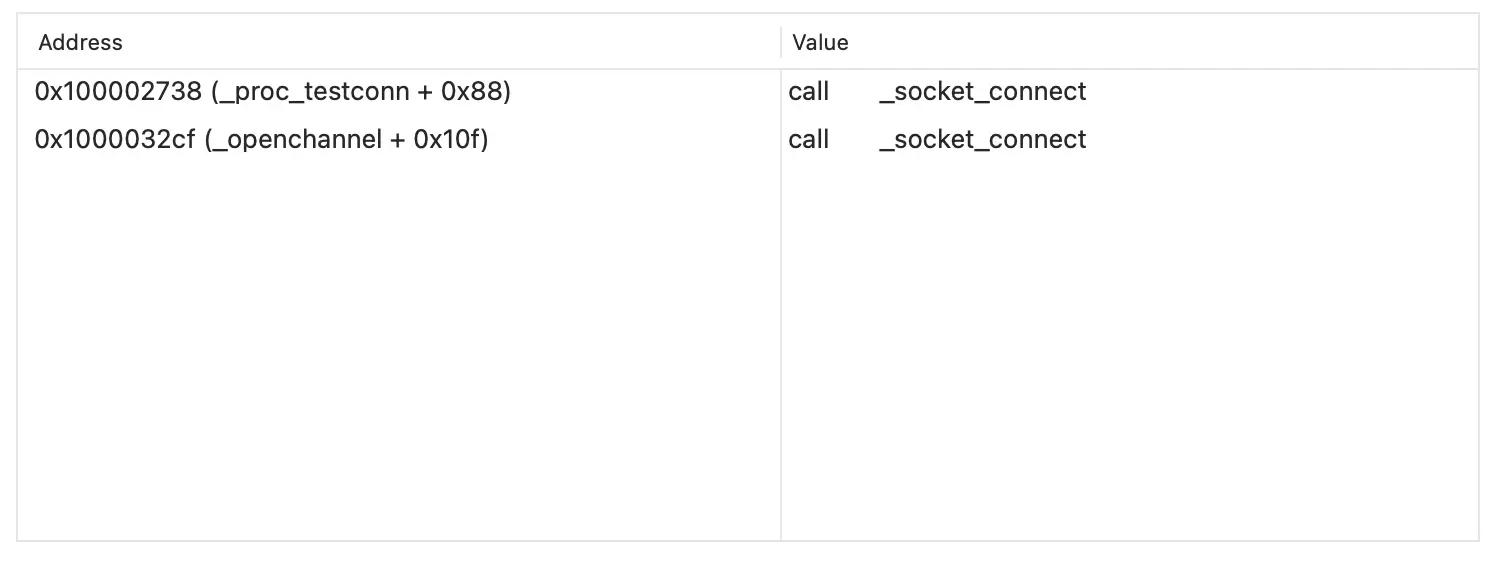
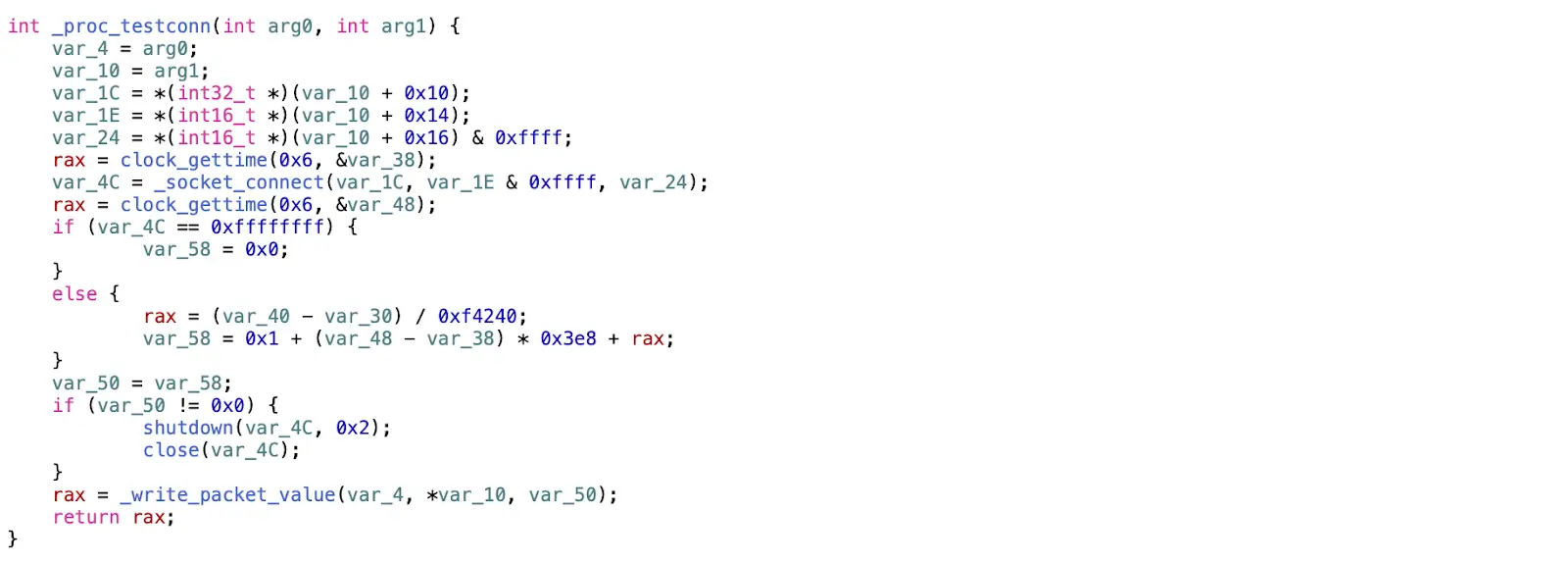
The connection via sockets was presented in _proc_testconn and _openchannel. For a better understanding of how this works, let’s take a closer look at _proc_testconn.
Basically, the _proc_testconn function is designed to create a test connection via socket initialization.
An in-depth look at SpectralBlur’s capabilities
Static analysis has given information about the table of imports for the current executable Mach-O file.
The following is a list of presented commands in the backdoor:
- shell
- dir
- upload
- upload_content
- download
- rmfile
- testconn
- getcfg
- setcfg
- hibernate
- sleep
- die
- stop
- restart
In other words, this backdoor is capable of a number of key functions. It can access the shell, upload and download data, extract a file, check the internet connection, get and install a configuration file, and execute system commands via /bin/sh.
Let’s quickly look at loading the configuration for this backdoor.
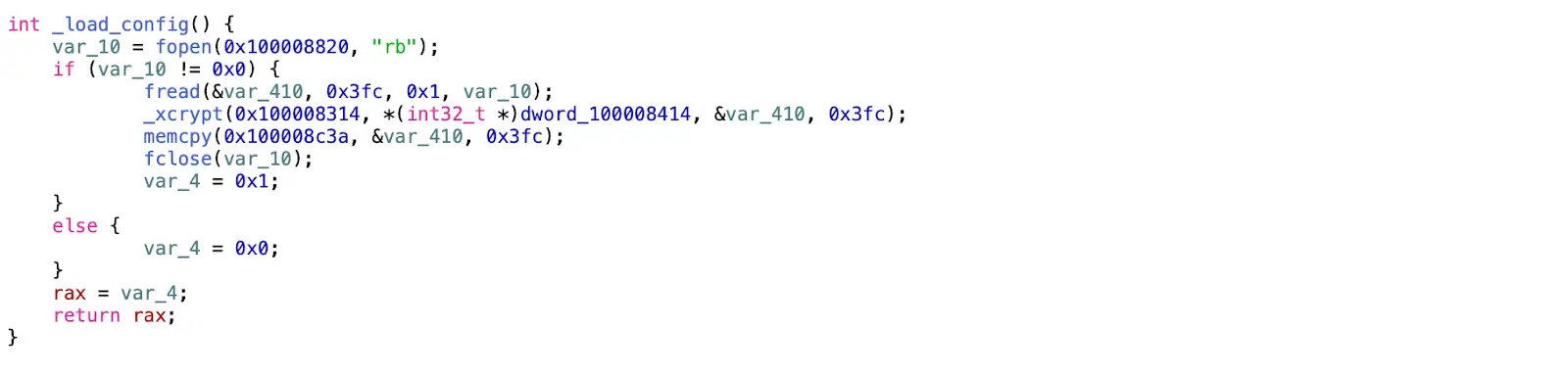
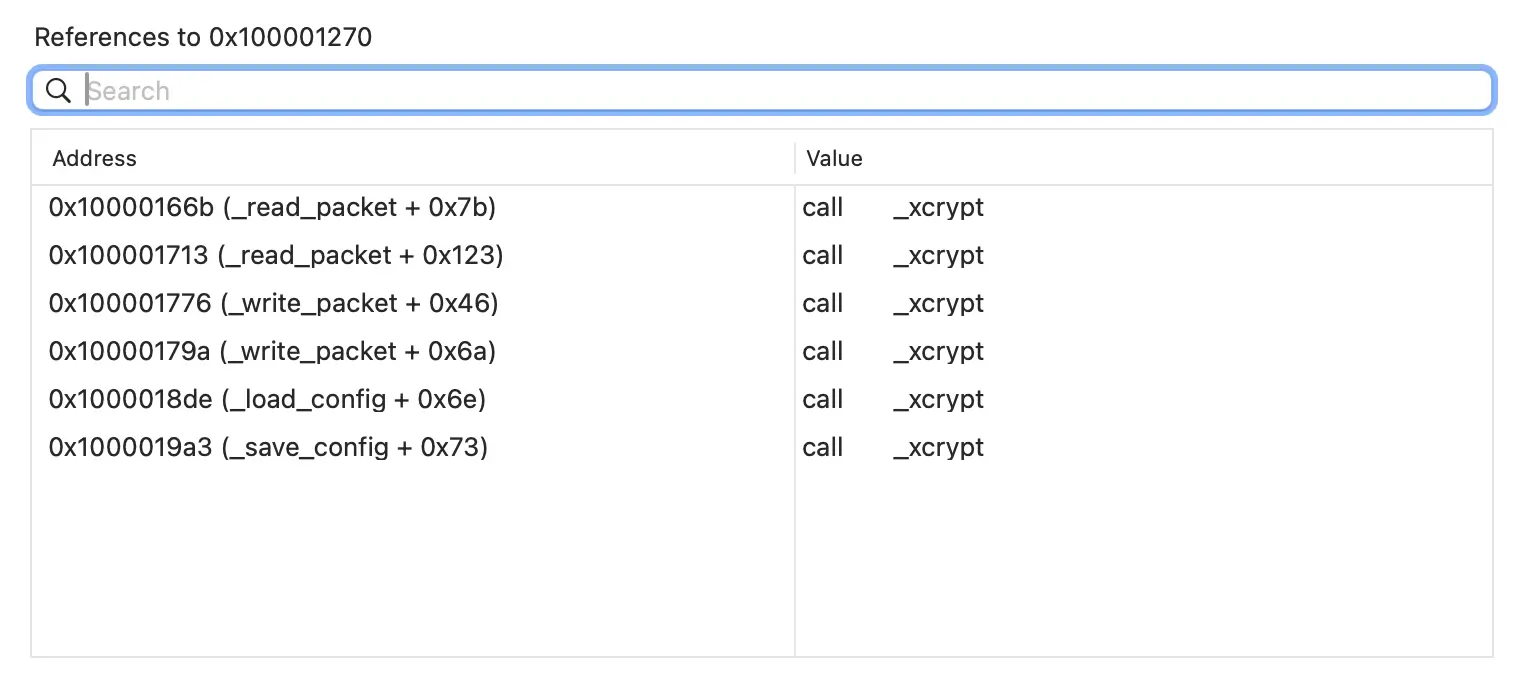
In the runtime of the backdoor, we received a configuration file from a remote server provided by the function _load_config. In this case, the xcrypt function is being used to work with encrypted data from a file, which implements the data encryption and decryption algorithm.
If we look at the xrefs table, we can see that this function is linked to read and write packets, as well as load and save configurations.
How to stay safe from SpectralBlur and other backdoors
The SpectralBlur backdoor has been linked to KandyKorn malware, which is connected with the Lazarus hackers group from North Korea. KandyKorn, which attacked the financial and cryptocurrency sectors, had mechanisms to avoid detection. Plus, it enabled remote access and monitoring of infected devices.
Lazarus is known as the APT group for using sophisticated attacks on the government and other cyber-espionage activities. Most of them are aimed at Windows, but the latest malware includes macOS backdoors.
To prevent malware infection, we highly recommend installing apps only from trusted sources. In addition, keep your OS updated so it is prepared to handle the latest vulnerabilities.
MITRE ATT&CK® Matrix:
Persistence (TA0003)
Privilege Escalation (TA0004)
Defense Evasion (TA0005)
Credential Access (TA0006)
Discovery (TA0007)
Collection (TA0009)
Command and Control (TA0011)
IoCs
6f3e849ee0fe7a6453bd0408f0537fa894b17fc55bc9d1729ae035596f5c9220 (SHA-256)
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






