If you are one of the millions of workers who use Confluence — a popular team workspace platform — the following news is something you don’t want to ignore.
Since October 4, when Confluence first announced the Data Center and Server zero-day vulnerability CVE-2023-22515, cybersecurity organizations have been warning that sophisticated nation-state threat actors are dangerously exploiting it. In this report, we’ll look at what’s happening with Confluence. Here’s how this vulnerability affects end users and what you can do to stay safe.
What’s happening with Confluence?
Confluence is a widely used enterprise team workspace platform provided by Atlassian. It is used by more than 80% of Fortune 500 companies.
Of the three plans offered by Confluence (Cloud, Data Center, and Server), the last two are exposed to this new, previously unknown vulnerability. Uptycs Threat Research’s own investigation reveals that what makes this zero-day exploit dangerous is that it is extremely simple to use.
“With just three HTTP requests, an unauthorized attacker can effortlessly craft a new administrator account on any exposed Confluence Server,” the Uptycs Threat Research report says.
Using CVE-2023-22515, attackers can create unauthorized Confluence administrator accounts. This opens the door for all types of malicious activities and damages. Atlassian ranked this vulnerability as “Critical,” giving it the highest CVSS score available of 10.
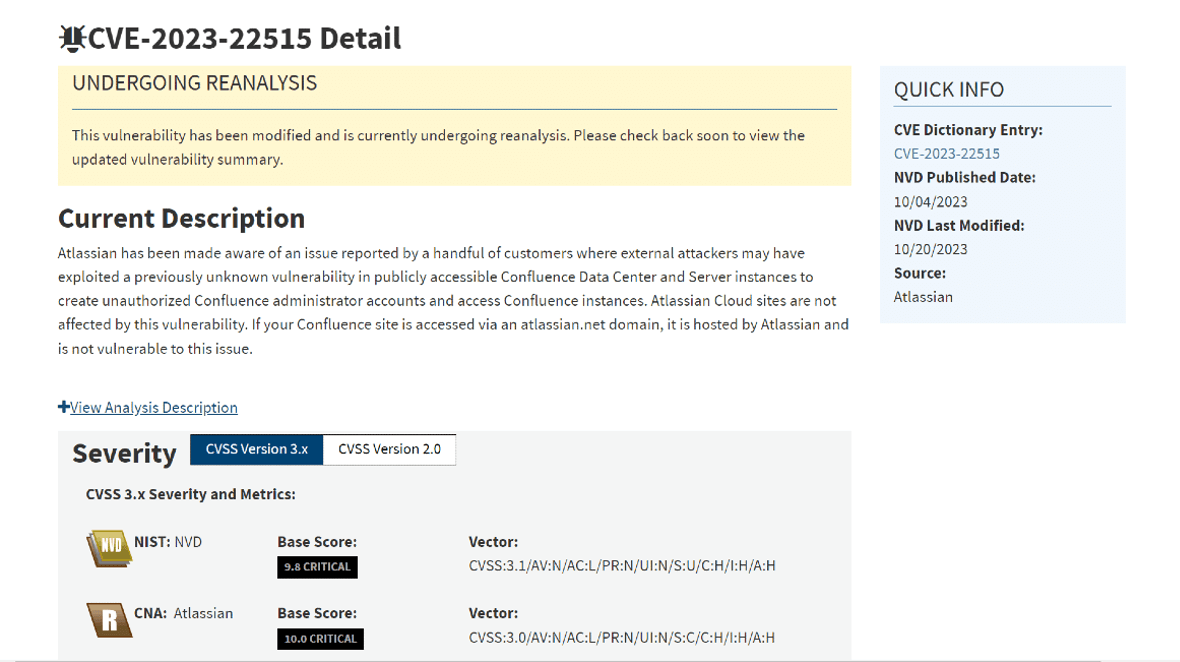
The affected Confluence Data Center and Server versions include all those ranging from versions 8.0.0 to 8.5.1. Atlassian urged customers to immediately upgrade to Confluence Data Center and Server versions 8.3.3, 8.4.3, 8.5.2, or any subsequent release.
How bad is the Confluence zero-day vulnerability?
The zero-day Confluence exploit has caught the attention of leading technology companies, security specialists, and cybersecurity law enforcement agencies.
On October 4, Microsoft warned via Twitter that a nation-state threat actor known as Storm-0062 has been exploiting the vulnerability since mid-September 2023.
Microsoft added that the vulnerability could be exploited using “any device” as long as it has a network connection. Microsoft explained that Storm-0062 is also known as DarkShadow or Oro0lxy.
Oro0lxy is an alias created by Li Xiaoyu, a Chinese hacker who was accused by the U.S. Department of Justice (DoJ) in 2020 of targeting hundreds of companies in the high-tech manufacturing sector, medical device industry, general business, education, gaming, software development, energy and pharmaceutical — including the coronavirus vaccine research developer Moderna. These attacks were described as politically and financially driven.
CISA and the FBI also expressed their concern about the vulnerability. On October 16, CISA, the FBI, and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA) report detailing the zero-day exploit and offering guidance.
CISA warns that cybercriminals leveraging the exploit can create unauthorized Confluence administrator accounts. Plus, they can obtain access to victims’ systems and continue active exploitation.
How the Confluence attack works
The Confluence attack works in three easy steps, running three HTTP requests:
- The attacker requests to initiate the setup of an administrator account for Confluence. This usually happens during the installation time.
- The attacker creates a new administrator account.
- The attacker logs into the victim’s Confluence platform using the newly unauthorized administrator account they created.
The real damage that unauthorized administrators can do
There are endless possibilities as to what an unauthorized administrator can do once they get access to a victim’s workspace platform.
Unauthorized administrators can:
- Access a company’s confidential documents and data
- Access workers’ personal data
- Leverage the access to launch more convincing inside-phishing campaigns
- Deploy malware
- Delete and create new users
- Attach malicious links to company pages or documents
- Access all team members’ files and folders, including private messages, documents, and other sensitive information
- Control team settings and permissions, such as changing roles and permissions and managing team channels
- Send messages and impersonate any team member
- Modify team data, which could cause significant disruption to the team’s work
In addition, cybercriminals could use their administrator privileges to gain access to other systems and resources that are connected to the team workspace software. For example, if the platform is integrated with a cloud storage service, a cybercriminal could gain access to all of the team’s files stored in that service.
It is important to note that the specific capabilities of a cybercriminal will vary. The degree depends on the specific team workspace platform that is targeted. However, in general, any administrator account will give the attacker a high degree of control over the system and its data.
I am a regular worker, not an administrator. What can I do?
The first thing you should do if your company is using Confluence is talk to your leader, IT support, or security team. Make sure administrators are on top of the issue. Send them the official links included in this report if necessary to access official guides and upgrade information.
The FBI and CISA urge organizations to hunt for malicious activity on their networks. If you aren’t a cybersecurity expert, pass this message on to the appropriate channels.
It is highly recommended that you run a trustworthy antimalware scan on all your devices. It is also a good idea to change your personal account passwords, make sure your security and privacy settings and notifications are set to the highest level, and enable multi-factor authentication.
Be on the lookout for new and unknown administrators on the platform. Verify messages that look suspicious, even if they come from coworkers, your team leaders, your boss, or executives. And watch for suspicious emails, messages, or changes in the workspace platform, as well.
Here are some tips to help protect your team workspace platform from cyberattacks:
- Keep your software up to date with the latest security patches.
- Use strong passwords and enable multi-factor authentication for all administrator accounts.
- Be careful about what permissions you grant to team members.
- Talk to team members and leaders.
- Contact the vendor of the team workspace platform for support.
Overall, always be cautious of what information you share on your work platform. Sensitive information such as passwords, financial data, or customer records could be used by cybercriminals. Fortunately, you can stay safe by following the recommendations in this guide.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Atlassian Corporation. Confluence is a trademark of Atlassian Corporation.






