We’ve all heard the term “hacker,” but did you know there are many different types? The most common types of hackers are black hat hackers. But there are also white hat, gray hat, and even red hat hackers. So, what’s the difference? Find out what each type of hacker is and how they operate in this comprehensive guide.
The definition of a black hat hacker
In the old days, bad guys typically wore black hats, and good guys wore white or light-colored hats. That is where the term black hat hacker comes from.
Black hat hackers are cybercriminals with nothing but malicious intent on their minds. They break into networks and even personal devices to steal information or money and damage digital assets and company reputations.
Black hat hackers are typically motivated by financial gain, revenge, or destruction. Others are state-funded and aim to wreak havoc on another country’s resources. And in some cases, they are dedicated to a cause and use their hacking skills to damage the opposition.
The best safeguard against hackers? Layers of security!
How are black and white hat hackers different?
While black hat hackers are interested in their own personal gain, white hat hackers are the opposite. In fact, white hat hackers break into networks and secure digital fortresses in order to reveal weaknesses so the owners can repair them.
These hackers typically work for companies or governments to exploit systems, looking for vulnerabilities to patch before the black hat hackers find them.
White hat hackers use pen-testing (penetration testing) tools and other sophisticated software to breach networks. Some resources are acquired from the dark web from known hacker groups.
Overall, the main difference between black and white hat hacking is that white hat hackers have permission from the company to perform the testing. Black hat hackers are uninvited.
Black hat hacking vs. red hat hacking
On the other end of the spectrum, red hat hackers are black hat criminals’ worst enemies. Unlike white hat hackers, red hat hackers aim their efforts squarely at cybercriminals. These specialized hackers are the vigilantes of the digital world. They target nefarious hackers or groups to destroy their organizations and stop them from doing any further damage.
Along with hacking into criminal networks, red hat hackers also destroy files, tools, resources, and backups, making it impossible for the bad guys to continue working.

Infamous hacker organizations
Most people think of hackers as individuals sitting behind their computers, secretly breaking into networks. But these days, many have joined forces, forming large, well-organized crime organizations responsible for insurmountable damage. The following are a few notable hacker groups.
Lazarus Group
The Lazarus Group is a black hat hacker group that has been active since 1998 and is suspected to be from North Korea. They are responsible for the Sony Pictures hack in 2014, which cost the company $15 million. This group also released the WannaCry malware, infecting 200,000 computers and costing $4 billion in damage.
Tailored Access Operations (TAO)
TAO is another hacker group that has been around since 1998. The group is a United States National Security Agency (NSA) cyberwarfare unit. They infiltrate foreign company networks and are most notable for Edward Snowden leaking their files to the public to expose the United States government’s spying tactics.
Morpho
Morpho is a more recent threat perceived to have begun operations around 2011. The group is known for cyber espionage and targets large corporations for their data. Their goals are always financial. In 2013, the group was the source of substantial data breaches at Microsoft, Apple, Twitter, and Facebook.
Lizard Squad
Lizard Squad was a hacker group that targeted entertainment and video game companies using DDoS attacks. The group is alleged to have operated between 2014 and 2015. Not only did they shut down the internet in North Korea in 2014, but they are also known for hacking PlayStation, Xbox, Malaysia Airlines, and Facebook.
What techniques do black hat hackers use?
Black and white hackers alike use various techniques to do their work, and all hackers use similar tools and methods to breach networks. Some of the more common techniques include the following.
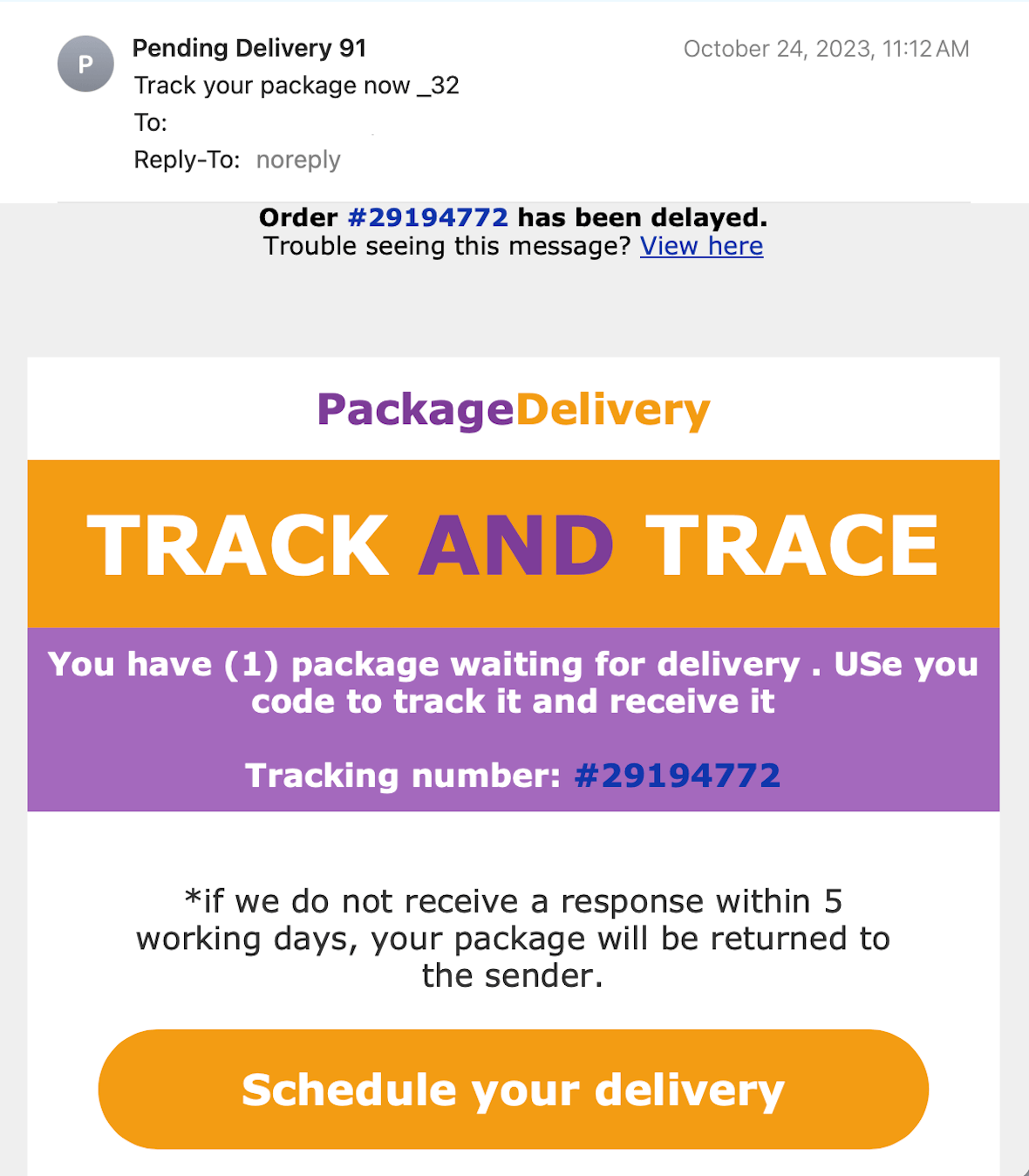
1. Phishing
Phishing has become a black hat hacker’s most prominently used tool. Hackers send legitimate-looking emails to unsuspecting victims, tricking them into clicking a link that infects their device with malware or ransomware. Their goal may also be to get the user to enter credentials into a fake website and steal their identity.
To keep yourself safe, never click a link in an email from someone you don’t know. Verify the email and ensure that the sender shown is, in fact, who sent it. And never give out payment information or credentials unless you know who you are connecting with.
2. Spyware and keylogging
Hackers often use spyware or keylogging software, which they install on your device remotely or get you to install through freeware or other tactics. Once they have control of your device, they can copy passwords and spy on all your account logins, calls, texts, etc.
Never download apps unless they come from a safe source like Apple’s App Store. Also, monitor your device for performance, battery, and heat issues, as these are signs that someone may taken control of it.
3. Ransomware
Ransomware has become the resource of choice for many hackers because it usually leads to a big payout. Hackers install software on a (typically corporate) network, taking files hostage and demanding a ransom. They execute this in many different ways. Sometimes, they promise to unlock the files if the ransom is paid. However, most victims never see the files again, or they end up leaked on the dark web.
Keep antivirus/antimalware software running on all your devices, and hire specialists to evaluate your security, scan for vulnerabilities, and then fix them.
4. Social engineering
Social engineering is responsible for many data breaches. This is when a hacker tricks employees into providing them with access, information, or corporate funds. Usually, they pretend to be a boss or someone higher up the company chain.
Before providing any credentials, money, or information, always verify that the message came from the real person.
5. Malware
Malware can be used to damage digital assets or steal information over a long period of time, as opposed to disabling files and holding them for ransom.
Be very cautious about any software you install on your device. Watch out for phishing emails and social engineering tactics to avoid malware.
Educating yourself on the many varieties of cybersecurity threats, the bad actors themselves, and their techniques is one of the best ways to stay safe. Do all you can to protect your digital assets by learning as much as possible about cybersecurity.







