With Lockbit disrupted by law enforcement and ALPHV (BlackCat) staging its own exit to escape mounting pressure from international agencies, the ransomware underground is in a state of flux. The question has been which cybercriminal group will emerge as the main RaaS operator contender. And now, that question has been answered.
On May 10, the FBI and Cybersecurity and Infrastructure Security Agency (CISA), released a #StopRansomware joint Cybersecurity Advisory (CSA) that points the finger at Black Basta.
As a ransomware-as-a-service (RaaS) operator, Black Basta has supported and enabled its partners and affiliates to attack more than 500 organizations around the world. In the United States, the group has been tied to attacks affecting 12 out of the 16 critical infrastructure sectors, including the Healthcare and Public Health (HPH) Sector.
CISA and FBI issue warning after Black Basta ransomware attack on Ascension
Just days after Black Basta launched a successful ransomware attack against Ascension, a St. Louis-based nonprofit health network that operates over 140 hospitals in 19 states, CISA and the FBI issued a joint advisory to help organizations defend their infrastructure against the group.
The recent attack on Ascension led to ambulances being diverted from hospitals. I also affected electronic health records and communication systems. Plus, the attack disrupted back-end health systems used for medical tests, procedures, and medications.
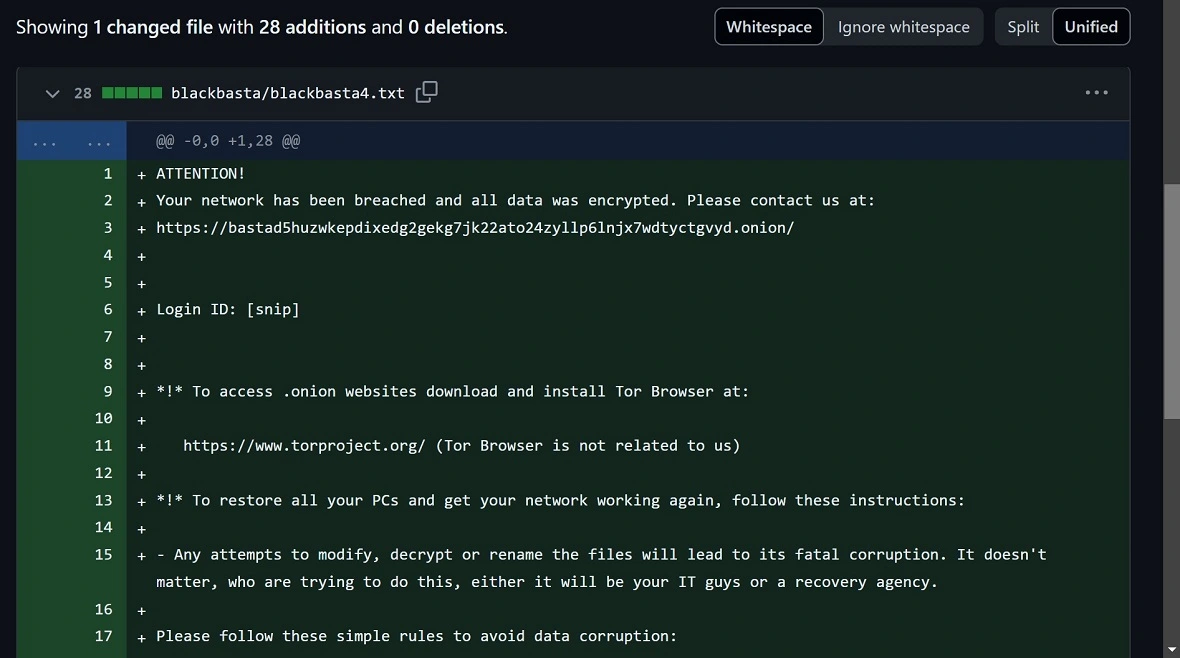
Black Basta claimed responsibility for the attack in its “Wall of Shame” onion site, listing the attack with a countdown running down from 10 days until they release the data they stole on the dark web. Mounting pressure and double extortion are what Black Basta is known for.
Operating since 2022, the group is historically among the most prolific ransomware criminal operations in the world, along with Lockbit and BackCat.
Black Basta’s playbook exposed: Techniques, technologies, and mitigation strategies
The FBI and CISA detailed in the joint advisory the techniques, technologies, and methods Black Basta uses in its ransomware attacks. Based on historical and digital forensics analysis, this detailed information can help organizations from any sector fortify their defense and gain awareness of the group and how it launches attacks from start to finish.
Additionally, US authorities released a series of mitigation recommendations for security teams to consider in an effort to deter and shut down attacks from Black Basta operators.
How Black Basta breaches to gain initial access
To gain initial access, Black Basta leverages phishing campaigns and zero-day vulnerabilities. Zero-day vulnerabilities have been on the rise as the pace of new OS updates, apps, and software rollouts dramatically increase, giving bad actors an extended digital attack surface to find weaknesses.
For example, starting in February 2024, Black Basta affiliates began exploiting ConnectWise vulnerability CVE2024-1709. In some instances, affiliates have also been observed abusing valid credentials.
The FBI explains that Black Basta continues to employ its classic double-extortion technique. In this technique, they encrypt systems and data, delete backups to prevent recovery, and pressure companies with leaks (releasing all data onto the dark web).
Ransomware notes forensics
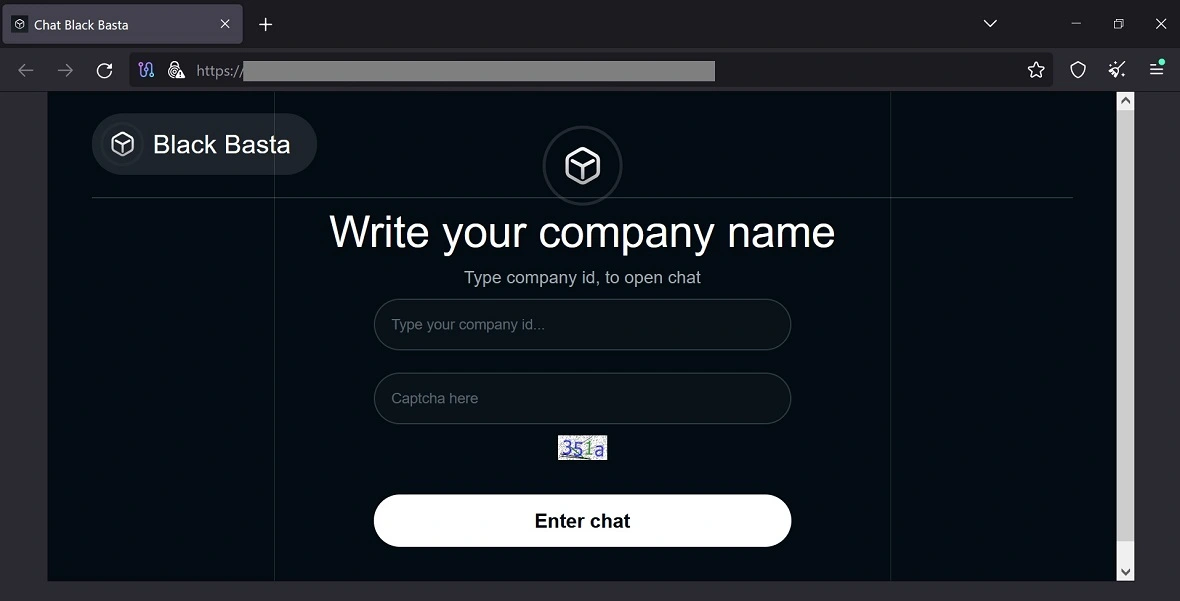
The Russian-speaking group also keeps a low profile when it comes to initial contact with its victims. Its ransomware notes are simple and to the point, and they do not contain any payment instruction details. Victims are urged by the group to log in to an onion (dark web) site and are given a link and login ID to contact Black Basta. The onion site can only be accessed through the Tor browser.
Typically, the ransom notes give victims between 10 and 12 days to pay the ransom before the ransomware group publishes their data.
Black Basta has also been observed to use Qakbot during the initial breach. Qakbot is a remote access trojan and a worm. This malware allows criminals to take over systems and expand thanks to the self-propagating characteristics of the code. The malware can also be used to exfiltrate data from breached devices.
Black Basta’s main targets
Black Basta entered the scene in early 2022. The group soon rose to the top, targeting businesses and driven by financial gains. However, in the past year, the group — along with others in the ransomware industry, such as ALPHV — have been going after other sectors (healthcare, hospitals, water, and other critical infrastructure).
Attacks on these sectors, which used to generally be perceived by the criminal underground as “no-go” operations, are now becoming increasingly popular for bad actors due to the potential for disruption.
CISA and the FBI spoke about why criminals target healthcare industries and urged the sector to take action to secure their architectures.
“Healthcare organizations are attractive targets for cybercrime actors due to their size, technological dependence, access to personal health information, and unique impacts from patient care disruptions.”
Health providers who have IT environments connected to their OT should take special precautions.
The new FBI-CISA joint advisory has highlighted the risk that Black Basta poses to the healthcare sector. It also outlines mitigation recommendations specifically for the sector.
Today, the main targets of Black Basta include:
- Critical infrastructure sectors: Targets lie within 12 out of the 16 sectors designated by the US government as critical infrastructure. These sectors are essential to the functioning of a society and include things like healthcare, energy, and transportation.
- Businesses: Black Basta also targets businesses, particularly those in North America, Europe, and Australia. They seem to prefer targeted attacks rather than mass campaigns.
Is Black Basta politically motivated? The unspoken Russian rule
While there is no direct evidence that can link Black Basta as being a nation-state-supported group, and while its attacks seem to be financially motivated, there are several factors that contribute to the idea that Black Basta’s criminal activities align with Russian interests.
Not only are Black Basta’s main attacks mostly directed to the US and Europe, with no attacks on Russian soil, but the group is known to speak the language. Additionally, researchers believed Black Basta is in some way a rebranding of the infamous Conti ransomware — a group that expressed support for Vladimir Putin and Russia in the invasion of Ukraine and vowed to attack enemies of the country.
The unspoken rule in the ransomware world for Russian-based or Russian-speaking operators is that as long as they align with the Russian agenda and do not run attacks within the country, Putin and the government will turn a blind eye.
Black Basta’s tools and tech
Black Basta technologies were also revealed in the new joint advisory. These include the following.
Discovery and execution: Black Basta affiliates use tools such as SoftPerfect network scanner (netscan.exe) for network scanning. Researchers have also observed reconnaissance techniques that use utilities with innocuous file names like Intel or Dell, left in the root drive C:\.
Lateral movement: For lateral movement, the group leverages tools such as BITSAdmin and PsExec, along with Remote Desktop Protocol (RDP). Some affiliates also use tools like Splashtop, Screen Connect, and Cobalt Strike to assist with remote access and lateral movement.
Privilege escalation: Credential scraping tools like Mimikatz for privilege escalation have been linked to the group. Black Basta has also exploited ZeroLogon (CVE-2020-1472), NoPac (CVE-2021-42278 and CVE-2021-42287), and PrintNightmare (CVE-2021-34527) vulnerabilities for local and Windows Active Domain privilege escalation.
Exfiltration and encryption: Black Basta affiliates use RClone to facilitate data exfiltration prior to encryption. Prior to exfiltration, cybersecurity researchers have observed Black Basta affiliates using PowerShell to disable antivirus products and, in some instances, deploying a tool called Backstab, which is designed to disable endpoint detection and response (EDR) tooling. Once antivirus programs are disabled, a ChaCha20 algorithm with an RSA-4096 public key fully encrypts files.
Command and scripting interpreter: Black Basta affiliates have used PowerShell to disable antivirus products.
Inhibition of system recovery: The vssadmin.exe program is used by the group’s operators to delete shadow backup copies.
The FBI warns that these tools by themselves should not be flagged unless they are determined to be actively in use for malicious purposes. Black Basta also operates a long, ever-changing list of public websites to support their phishing and ransomware operations.
Mitigation actions: Strengthening security postures
Black Basta ransomware poses a serious threat, but there are steps you can take to protect yourself. Here’s what you can do.
Always prioritize installing the latest updates for your operating systems, software, and firmware as soon as they are released. This is especially important for known exploited vulnerabilities (KEVs), as they are prime targets for attackers.
Whenever possible, enable phishing-resistant multi-factor authentication for all your online services. This adds an extra layer of security beyond just a password, making it much harder for attackers to gain access even if they steal your login credentials.
Phishing emails are a common way Black Basta spreads. Educate yourself and others in your organization to recognize phishing attempts and how to report them. If you use remote access software for work or personal use, be sure to follow the recommended security measures.
Regularly backing up critical systems and device configurations creates a safety net. In the unfortunate event of an attack, backups allow you to restore your systems and data quickly, minimizing downtime and damage.
For additional guidance and best practices, refer to the CISA-FBI #StopRansomware Guide. This comprehensive resource offers a wealth of information on how to protect yourself from ransomware attacks.
Remember, cybersecurity is an ongoing process. Stay vigilant and keep your defenses up to date.
The FBI, CISA, and HHS do not encourage paying ransom as payment. Promptly report ransomware incidents to the FBI’s Internet Crime Complaint Center (IC3), a local FBI Field Office, or CISA via the agency’s Incident Reporting System or its 24/7 Operations Center ([email protected] or by calling 1-844-Say-CISA [1-844-729-2472]).