Cooperating international law enforcement agencies are stepping up their game in the fight against cybercriminal gangs. Recently, the United States DOJ and the FBI, working with the United Kingdom National Crime Agency’s (NCA) Cyber Division, along with other agencies from 10 countries, dismantled and shut down LockBit.
Capitalizing on this momentum, the US Department of State issued a $15 million reward for another infamous cybercriminal gang: ALPHV/BlackCat.
According to the FBI, ALPHV/BlackCat has compromised thousands of businesses and organizations around the world, generating damages of at least $300 million in ransom payments. This gang has been highly active in the past couple of years, targeting big companies and corporations and increasing their ransomware demands.
Why should Mac users care?
While ALPHV, aka BlackCat, is known for targeting US and international government entities such as municipal governments, defense contractors, and critical infrastructure organizations, the group recently pivoted toward the Apple environment.
As Moonlock recently reported, the group has been linked to a new backdoor malware that specifically targets macOS. The backdoor was discovered in the wild by BitDefender in February 2024 and is believed to have been operating in the dark, compromising Mac computers, for 3 months prior to its discovery.
While it is unclear what exactly ALPHV’s plans are for this macOS backdoor, one thing is certain. Once this backdoor compromises a Mac, it can remain undetected in the OS for long periods of time while it communicates with the criminals’ controlled servers.
Using this new backdoor — which poses as a fake Visual Studio update — ALPHV can remotely make changes to the macOS, as well as steal files and credentials.

ALPHV’s move toward the Mac environment is part of an ongoing recent trend. Criminals are coding and adapting malware used to target Windows or Android systems specifically to breach MacOS and iOS devices.
The alarming new development picked up speed in 2023 and is only accelerating in 2024. This new era of Apple device attacks is fueled by the growing popularity and higher rates of adoption of Apple devices and Mac computers around the world, especially among enterprises.
ALPHV’s Rust macOS backdoor should be considered extremely aggressive and dangerous. It has the potential to launch damaging attacks, including ransomware, stealers, spyware, and more.
Breaking down the $15 million reward
While ALPHV has been linked to Russian hackers, the US Department of State believes that members from different nationalities and varying citizenship may be involved in the group’s criminal activities.

The US Department of State is offering a reward of up to $10 million for information leading to the identification or location of any individual or individuals who hold a key leadership position in the ALPHV/BlackCat group.
There is also a $5 million reward for information that leads to the arrest and/or conviction in any country of any individual conspiring to participate in or attempting to participate in ALPHV/BlackCat ransomware activities.
The US Department of State also set up an onion site, a site that can only be accessed using a Tor browser (also known as an onion dark web browser). Through this new site, the Department of State is accepting information on ALPHV. The site is located at: he5dybnt7sr6cm32xt77pazmtm65flqy6irivtflruqfc5ep7eiodiad.onion
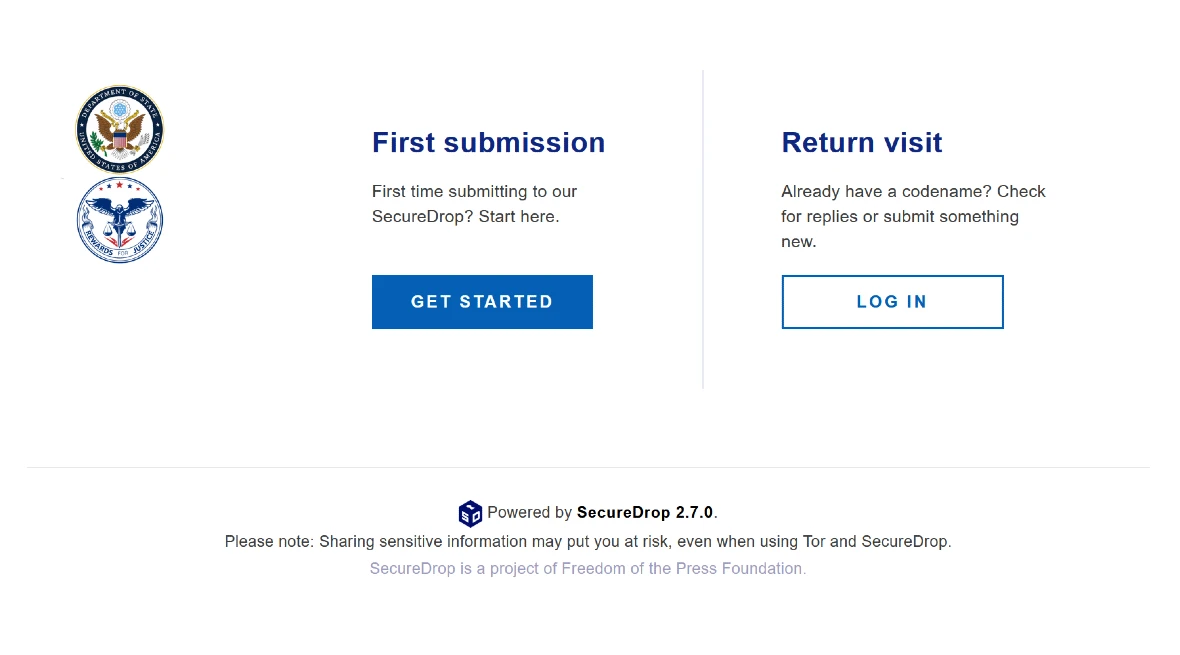
The US Department of State assures that the identities associated with all incoming information and tips submitted via the onion site will be kept strictly confidential.
How dangerous is ALPHV/BlackCat?
ALPHV/BlackCat operates in a ransomware-as-a-service (RaaS) format. They specialize in triple extortion, demanding multiple payments from those infected with their ransomware in exchange for decrypting data, not leaking the info, and not launching denial of service (DoS) attacks to crash a live website.
The group has even gone as far as using more bizarre and extreme extortion pressure techniques. They use these to leverage the US government’s new regulations, specifically the new SEC rule, which requires that companies report security incidents within a certain period of time.
ALPHV offers its ransomware services to affiliates to carry out attacks. In return, the group takes a cut of the ransomware payment. Most of its malware is written in the programming language Rust. This language is relatively new and presents a challenge to cybersecurity officers, as there are few security tools designed for the Rust language.
An escalating battle with the FBI
BlackCat has been engaged in a high-stakes chess match with agencies like the FBI for some time now. The new $15 million reward offered by the US Department of State can be considered the latest move by US law enforcement in this ongoing battle.
ALPHV broke into the scene in 2022, but experts theorize that the group is a rebranding of the DarkSide and BlackMatter ransomware operations.
DarkSide and BlackMatter have both been linked to the Colonial Pipeline attack and scandal. Their operation was shut down by law enforcement actions in May 2021 after extensive investigations of the Colonial Pipeline incident.
The criminal gang was shut down again in November 2021. However, by February 2022, it was back in the game, operating under a new name: ALPHV/BlackCat.
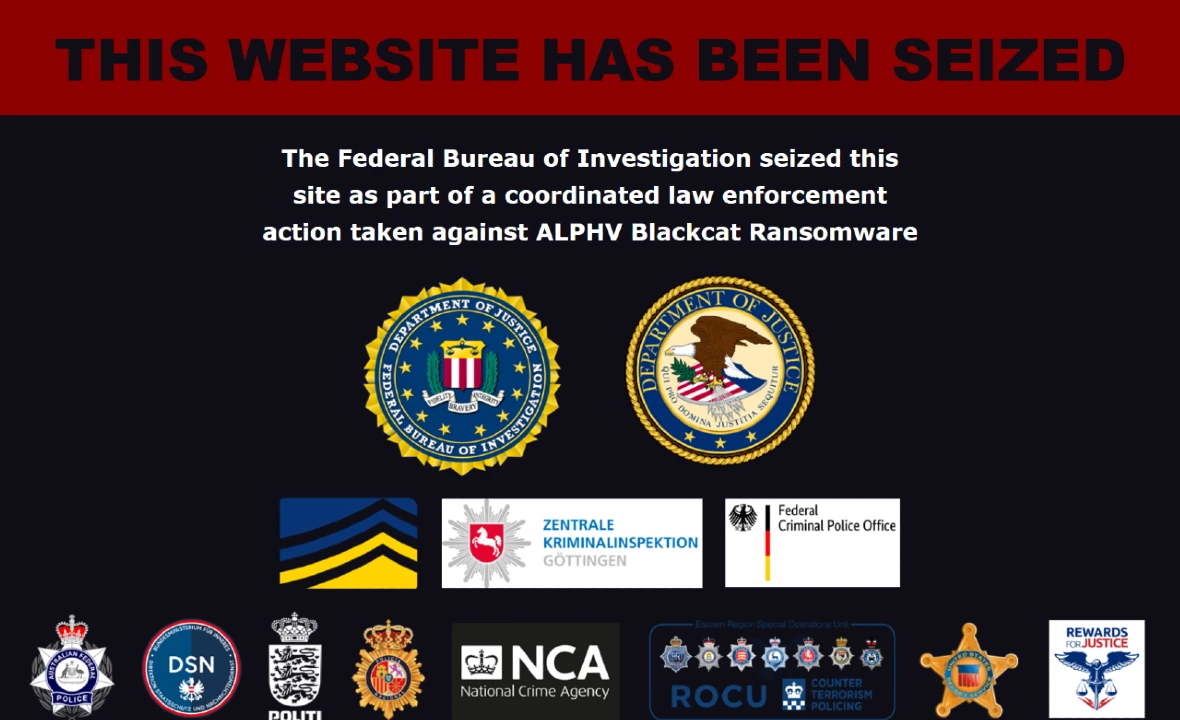
In December 2023, the FBI seized ALPHV’s onion leak site, which the criminal group “recovered” a few days later.
ALPHV/BlackCat didn’t roll over after the FBI attempted to shut down its sites. On the contrary, the group escalated its battle against the US.
ALPHV/BlackCat raises the stakes
Like any RaaS operator, ALPHV sets rules for the members or affiliates that use their ransomware malware to launch attacks. These rules often specify what sectors or nations are off limits.
In the case of ALPHV, one of its rules was that members could not launch ransomware attacks against critical infrastructure sectors. These sectors include defense and government, dams and water and sanitation, emergency services, the energy sector, the health sector, and others.
After the FBI shut down the ALPHV site and the gang “recovered” it, however, they released a communication that removed the ban for its members to go after the critical infrastructure sectors.
Their message in Russian, translated by SCMedia and other international news outlets, read:
“Because of their actions, we are introducing new rules, or rather, we are removing ALL rules, except one, you cannot touch the CIS (critical infrastructure sectors), you can now block hospitals, nuclear power plants, anything, anywhere.”
On December 19, days after ALPHV cleared all its rules — signaling possible cyberattacks on critical infrastructure in the US — the DOJ and the FBI announced that in cooperation with an international group of law enforcement agencies from the United Kingdom, Australia, Germany, Spain, and Denmark, they were conducting a disruption campaign against the notorious ransomware gang ALPHV/BlackCat.
So far, the FBI has helped dozens of victims in the US and internationally by disseminating an ALPHV decryption tool. The tool allows victims to restore and recover their systems, data, and files.
The FBI assures that these operations have prevented about $99 million in ransomware payments from falling into the hands of BlackCat members.
Final thoughts
It is still too early in the game to know how the saga between international law enforcement agencies and BlackCat will end, or if it will end at all. One thing is certain: Law enforcement actions against notorious ransomware gangs have been intensifying since late 2023.
That said, the prospect of shutting down an entire international criminal organization — one with a global infrastructure and a complex network, rich in illegally obtained financial resources, with members throughout different countries — is a monumental task.
Time and time again, even after arrests are made and sites are shut down, law enforcement agencies see old cybercriminal organizations resurface under new names. But as US, UK, European, and other law enforcement agencies around the world get better at collaborating and enforcing actions, BlackCat’s demise becomes a possibility.
The world will likely hear from ALPHV/BlackCat soon. In this ongoing chess match against law enforcement, for every move the FBI makes, BlackCat makes another. And it seems that their ransomware attacks won’t stop until the game is finally over.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






