Mac malware is on the rise, and the trend is only accelerating. A new Bitdefender investigation has uncovered a new backdoor that has been operating undetected for the past 3 months in macOS environments.
The new malware is linked to none other than the ransomware operators BlackBasta and ALPHV/BlackCat — a group heavily engaged in a battle with law enforcement that “unseized” their dark web leak site from the FBI in late 2023, as Bleeping Computer reported.
Moonlock spoke to Bogdan Botezatu, Director of Threat Research and Reporting at Bitdefender, to help determine why Mac users are under fire and to better understand the findings of this recent malware discovery.
How the new Mac backdoor works
Bitdefender explained that the backdoor Trojan.MAC.RustDoor is a previously undocumented family of malware. While the security company cannot confidently attribute this new campaign to known threat actors, several factors suggest that the new Mac backdoor is related in some way to BlackCat and BlackBasta.
The malware is coded in Rust, a programming language used by BlackCat. Additionally, 3 out of the 4 command and control servers were previously associated with ransomware campaigns targeting Windows clients, BitDefender said.
What the backdoor can do
This new backdoor is designed to breach a Mac device without user knowledge and persist in the system for long periods of time. It can also communicate with bad actors’ servers, access specific files, archive them, and upload them to the command and control center.
Because the backdoor is written in Rust, it is difficult to detect and very evasive. The Rust language and its security tools are still relatively new compared to more established programming languages. This means there are fewer specialized analysis and detection tools available to identify suspicious activity in Rust-based malware.
Rust also compiles directly to machine code, unlike languages like Python, which rely on interpreters. This makes the code more compact and harder to reverse-engineer, obscuring the malicious intent for security analysts.
More concerningly, Bitdefender has identified several different versions of the backdoor since November 2023, revealing that it is being updated and enhanced. In short, it is evolving.
How the new Rust backdoor tricks you into installing it
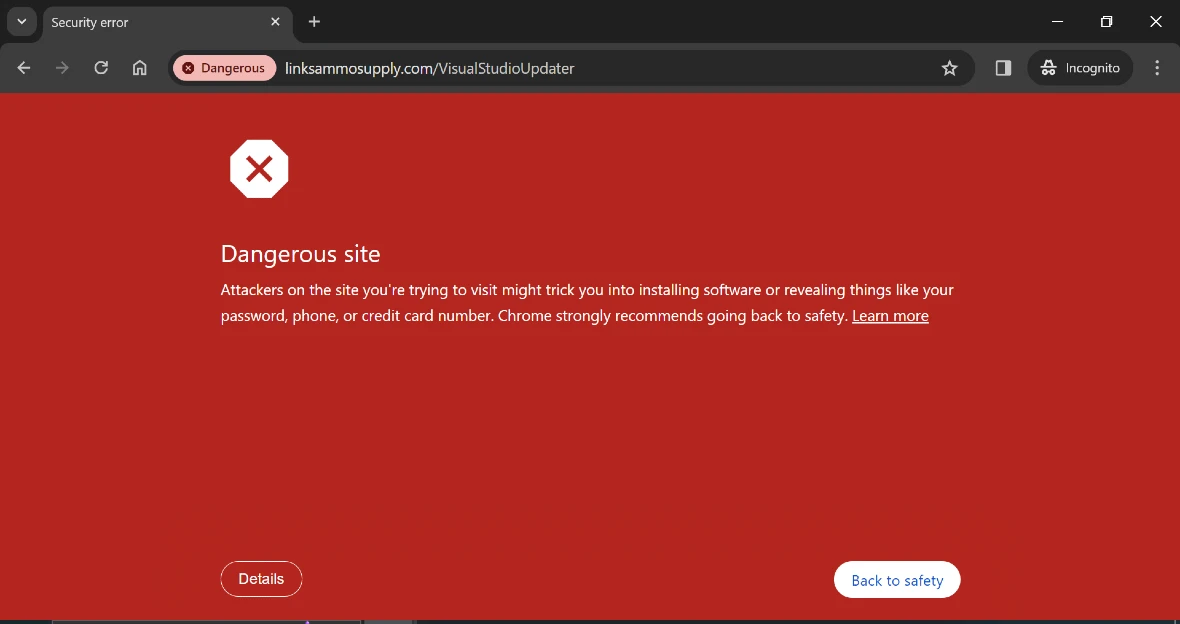
Criminals are distributing the new Mac Rust backdoor using a form of social engineering and phishing that impersonates legitimate software. In this case, attackers have set up several malicious websites that attempt to convince users to download a fake Visual Studio update.
If you develop apps, web or desktop applications, games, or native macOS experiences, or if you work in software development, you have probably heard of Visual Studio.
If a user falls for this new campaign and clicks on the fake Visual Studio update, the malware will install itself on the computer without the user’s knowledge. Some of the malicious websites will automatically trigger a prompt for the user to download files. Samples identified by Bitdefender in their research include:
- zshrc2
- Previewers
- VisualStudioUpdater
- VisualStudioUpdater_Patch
- VisualStudioUpdating
- Visualstudioupdate
If you see any of these names, do not download the file.
How the backdoor talks to the hacker
Like any backdoor, this new malware sets up a line of communication between the attackers and the infected machine. Bitdefender broke it down in their report.
Here’s how it works. The malware installer runs an extraction with the sysctl command and the output of two other commands (pwd and hostname). These are then submitted to the Register endpoint of the Control and Command server to assign and receive a Victim ID.
Using this Victim ID, the malware on the infected macOS will communicate between the C&C and the backdoor. The established communication then allows hackers to gain information on the infected system, establish contact in short time intervals, send and receive payloads, exchange information about tasks executed on the breached device, and extract files.
The malware steals files of specific extensions and specific files from Documents and Desktop folders, as well as the notes of the user. To do this, it copies the files to a hidden folder. It then compresses them into a ZIP file and sends it to the C2 server controlled by the cybercriminals.
Several malicious sites have been identified in this campaign, including:
- https://sarkerrentacars.com/zshrc
- https://turkishfurniture.blog/Previewers
- http://linksammosupply.com/zshrc2
- http://linksammosupply.com/VisualStudioUpdaterLs2
- http://linksammosupply.com/VisualStudioUpdater
Most of these sites are now defunct or flagged by Chrome.
Why are criminals going after Mac users?
Botezatu explained why macOS malware is proliferating.
“As macOS has steadily gained ground in market share over the past few years, it has become much more attractive for cybercrime groups,” Botezatu said.
Mac malware is not only on the rise but is becoming much more aggressive, with backdoors, stealers, and trojans breaching what were once considered the most immune digital systems of the world.
“Traditional macOS threats such as potentially unwanted apps (PUA) or aggressive adware have been surpassed in numbers by more devastating trojans,” Botezatu said.
Botezatu highlighted Bitdefender’s latest macOS Threat Landscape Report, which concludes that trojans are the biggest single threats to Macs, accounting for more than half of threat detections.
“Apple finds itself consistently having to patch actively exploited vulnerabilities as threat actors employ social engineering vectors and spray-and-pray techniques,” the report reads.
Cybercriminals are creating more aggressive Mac malware but still depend on user actions
Bitdefender says that threat actors are becoming more successful in their attacks on Macs and design threats to exploit unpatched flaws and lax cybersecurity hygiene. However, these attacks have a weak point: Mac users.
Trojans can only breach macOS if a potential victim manually downloads and executes it. So, to carry out these attacks, criminals impersonate legitimate Mac applications. Plus, while Apple is continually releasing new updates, making it hard for everyone to keep up, users who don’t keep their Mac up to date are at higher risk of exposure.
“Macs have unfortunately become valuable targets because of their increased penetration in the enterprise,” Botezatu said. “Some cybercrime groups are now attempting to carve a niche for themselves in the Mac space to move into other ecosystems because of fierce competition in the Windows landscape.”
Final thoughts
The rise of new Mac malware is of serious concern. It’s a trend that is becoming more aggressive every day. However, Mac users still hold all the cards. None of the attacks that are targeting macOS systems use zero-click malware. This means that users play a major role in the overall outcome.
Trojans, backdoors, ransomware, and other types of Mac malware can’t just magically install themselves onto a computer. As long as you do not download and execute these fake updates, fake software, or fake apps, absolutely no harm can come to you.
While always being vigilant is easier said than done, it is once again time to level up your guard. Be extra cautious with links, only download files from legitimate, verified sources, and stay away from sites with strange URLs.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.