In the world of cybercrime, the objective is usually financial gain. Cryptojacking is just one example of the many types of cyberattacks in which the perpetrator steals money while keeping the victim completely in the dark. But this is one category of threat where the victim may not be personally affected in a major way. Rather, they are used as pawns in a larger game of theft.
What is cryptojacking? The meaning explained
Cryptojacking is a crime where a hacker installs cryptojacking malware onto your device to use it to mine for cryptocurrency. It can be accomplished using computers, servers, tablets, and even mobile phones. Once installed, the malware can affect your device’s performance. It hijacks resources such as bandwidth, memory, and drive space.
How cryptojacking works
Transactions between individuals involving cryptocurrency, digital money often referred to as “coins” or “tokens,” are facilitated using a database technology called blockchain. The blockchain is a record of transactions, but no names or identifying data are used, so it is considered anonymous.
The blockchain requires an enormous amount of energy to sustain it. Accordingly, it relies on people to supply the necessary computing power; they are referred to as “miners.” Someone who allows companies to use their devices for mining receives cryptocurrency as payment.
Criminals who want to receive the rewards of mining without supplying any of the resources (computers, electrical power, etc.) will hijack hundreds or even thousands of devices to use for the blockchain, mining millions in cryptocurrency for their efforts.

Examples of cryptojacking attacks
Some examples of real-life cryptojacking include the following.
Coinhive
In 2017, Coinhive was launched as a cryptocurrency mining service that allowed website owners to make money without ads. They installed a bit of JavaScript on their website that used visitors’ computers to mine cryptocurrency without their consent or knowledge. It was shut down in March 2019 due to new regulations and lack of interest.
FacexWorm
FacexWorm is another notable cryptojacking scheme. It uses Facebook Messenger to trick users into clicking on fake YouTube links. The user then downloads a Chrome extension, which is actually malware that hijacks their Facebook account and spreads FacexWorm among the user’s Facebook friends. It also begins to mine cryptocurrency. Plus, the worm steals credentials for specific sites like Google or MyMonero, demanding cryptocurrency payments.
WannaMine v4.0
Another cryptojacking example is WannaMine, a piece of malware first seen in 2018. It spread through a phishing email with a malicious attachment. If a user clicked on the attachment, it installed the malware onto their device and began mining for Monero cryptocurrency. Another feature of the attack vehicle is that it was designed to copy itself to other network devices to boost the mining operation’s computing power. Discovered by security experts in 2020, this threat is adept at avoiding detection and can steal sensitive information from the victim’s device.
Understanding cryptojacking
The trick to protecting yourself from cryptojacking is to understand it fully. Below, you’ll find answers to some of the most common questions asked about cryptojacking.
How common is cryptojacking?
According to the 2023 SonicWall Cyber Threat Report, cryptojacking is increasing by 43% each year. In 2022, it reached an all-time high of 129.3 million attacks.
Who is affected by cryptojacking?
Individuals and companies alike may be affected by cryptojacking. In all cases, victims will suffer from decreased device performance, increased power usage, and sometimes stolen credentials or personal information.
Is cryptojacking illegal?
Yes. Even in cases where victims of cryptojacking are not personally harmed in any considerable way, the unauthorized use of their devices and resources is illegal.
Why is cryptojacking increasing?
Cybercrime gangs are always looking for new ways to make more money with less effort and reduced risk. Security experts theorize that cryptojacking is increasing due to the low level of risk associated with it.
Signs that your Mac is being used for cryptojacking
Cryptojacking is not an obvious crime, so it may be more challenging to detect. Some signs that your Mac is being used to mine cryptocurrency include the following.
Decreased performance
The most significant sign that your Mac is being used for cryptojacking is decreased performance. Watch for a slow response when you click an icon to open a program or file. If you use a laptop, you may see the battery drain quickly.
Overheating
Cryptojacking is a resource hog that could cause your device to overheat or shut down. Regular overheating can cause damage to the internal electrical components. If you hear the fan running incessantly, it could be a sign.
Increased electricity usage
If you notice a steep increase in your electricity bill, it could be a sign that your devices are running 24/7 to mine cryptocurrency.
CPU usage uptick
Cryptojacking uses a lot of computing power, and if you view your CPU usage logs, you may see a considerable spike. You can check CPU usage by opening the Activity Monitor on your Mac and looking for anything that uses high amounts of resources.
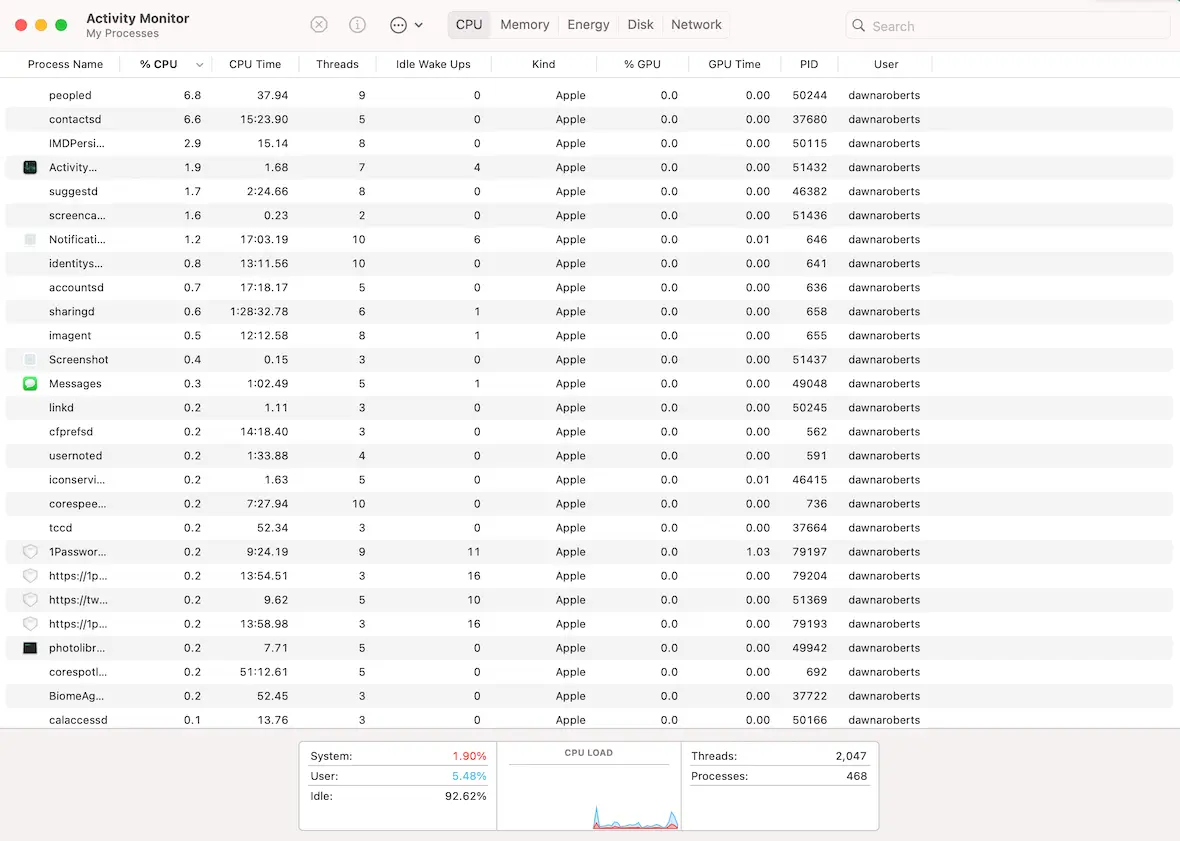
How to protect your Mac from cryptojacking
Cryptojacking usually occurs in one of two ways: through a phishing email with malicious links or through a visit to a corrupted website that installs malware automatically. While no one is 100% immune to online threats, there are some ways to help keep you and your Mac safe.
1. Watch for phishing emails
Never click links in unsolicited emails. You never know where they might take you, and there’s a chance that the link is a tool to install malware on your machine.
2. Use good antivirus/anti-malware software
Install and use reputable anti-malware software on your machine. You’ll need something that runs frequent deep scans to search for any virus, spyware, or vulnerability that could be hiding under the surface.
It’s recommended that you use an anti-malware tool made specifically for your device type. Moonlock is a comprehensive protection app designed for MacBooks.
Moonlock not only searches for malware during a scan but takes a more proactive approach to ensuring your security. It keeps an eye on all endpoints, making sure nothing malicious sneaks in. It inspects everything from email attachments in the system Mail app and all external drives to browser extensions and launchers.
Start a free trial of Moonlock and download the app. Then launch Moonlock, go to Malware Scanner, and click Scan to run an in-depth examination of the health of your device. And if it finds anything suspicious, Moonlock will alert you and take care of fixing it.

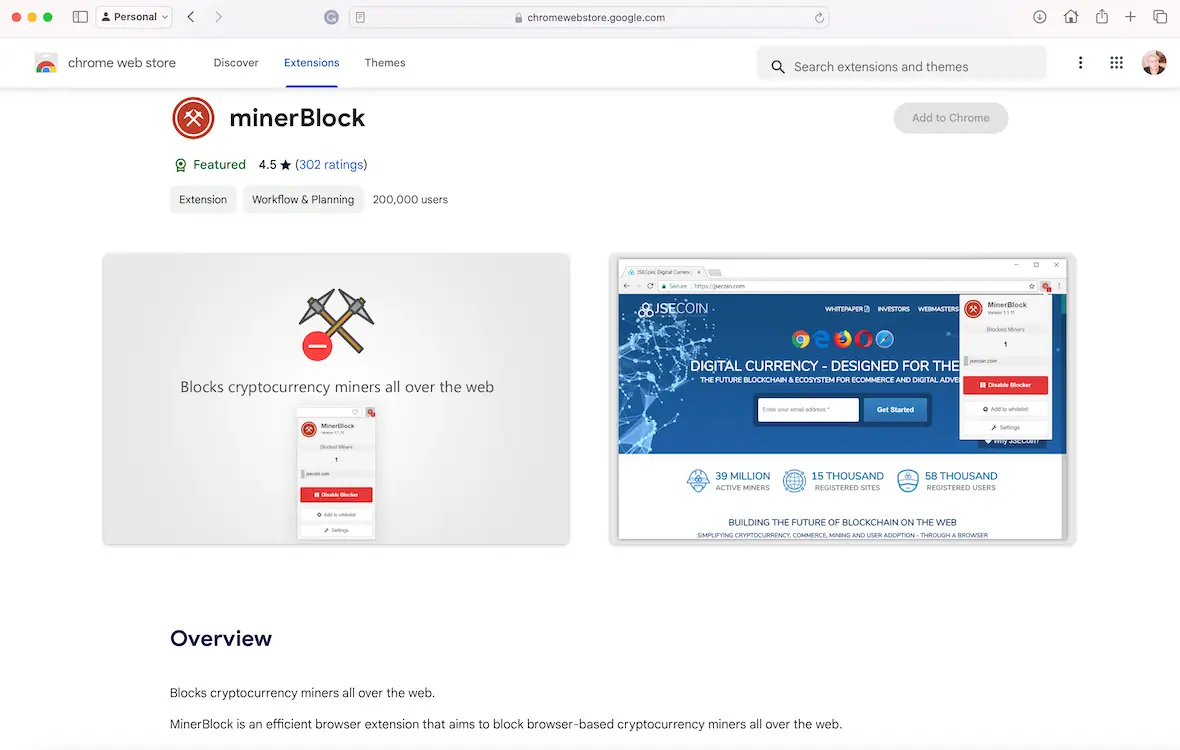
3. Use browser extensions to block cryptojacking
You can install and use browser extensions like minerBlock, No Coin, and AntiMiner to prevent anyone from using your Mac to mine for cryptocurrency.
4. Disable JavaScript and ads
Disable JavaScript on your browser to prevent drive-by installations of cryptojacking malware. Turn on ad blockers to prevent criminals from infecting your device through corrupted ads.
Protecting yourself from threats should be your number one priority when it comes to cybersecurity. Although the consequences of cryptojacking are more irritating than damaging, it does open the door for additional attacks and can compromise your personal information.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.






