A new Chinese platform is taking phishing to the next level by providing cybercriminals with advanced technologies and resources to launch attacks.
On March 27, Netcraft reported that the platform “darcula” is a new sophisticated phishing-as-a-service (PhaaS) platform. This new PhaaS is used on more than 20,000 phishing domains and offers cybercriminals easy-to-use social engineering technologies.
Let’s dive into how darcula operates, how it avoids detection, and how users can keep themselves safe.
Darcula: The new phishing-as-a-service platform
Netcraft research revealed that the darcula phishing-as-a-service platform has been active for the past year and has already been used in numerous high-profile phishing attacks. By using this platform, cybercriminals can target Apple and Android devices.
The platform offers several templates to build phishing messages as well as fake landing pages to trick users. Reddit’s phishing posts show, for example, how darcula attackers are impersonating known and trusted services. One such service is the United States Postal Service (USPS).
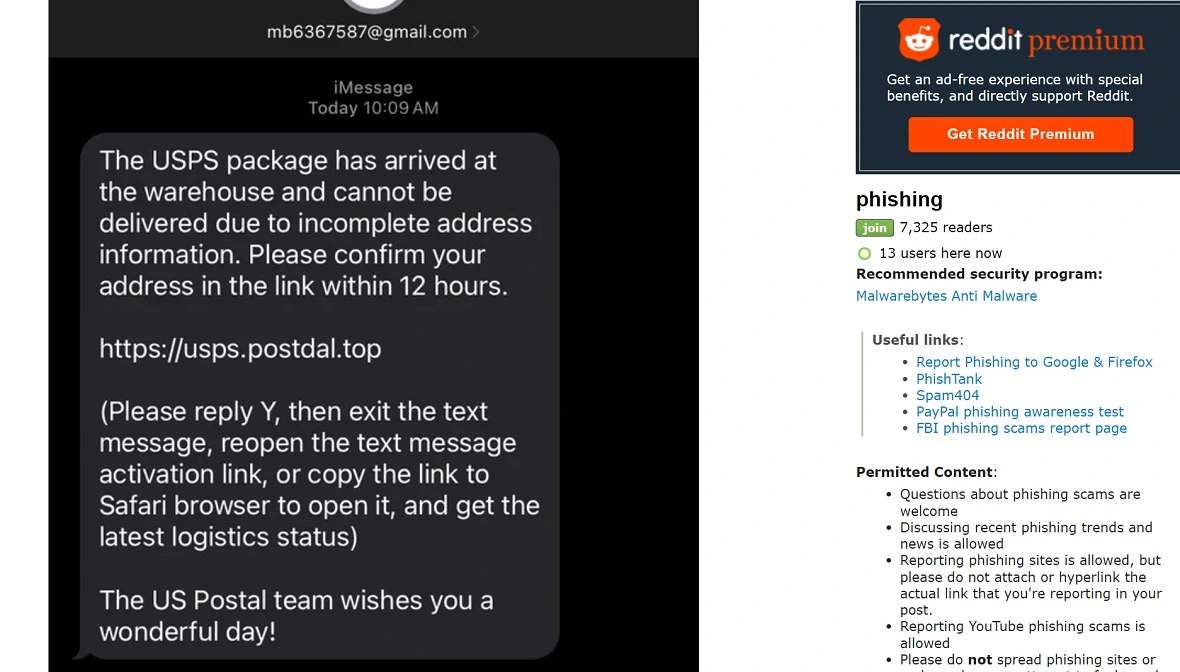
“In total, Netcraft has detected more than 20,000 darcula-related domains across 11,000 IP addresses, which target 100+ brands,” Netcraft said. “Since the start of 2024, Netcraft has detected an average of 120 new domains hosting darcula phishing pages each day.”
Darcula phishing-as-a-service platform: Technical challenges
The darcula platform is part of the growing malware-as-a-service (MaaS) trend, a business model that cybercriminal groups use to generate revenue.
The MaaS process consists of selling or licensing easy-to-use all-in-one cyberattack platforms. These platforms, offered via messaging channels such as Telegram and the dark web, lower the technical bar required for attacks, making malicious tools dangerously accessible.
However, according to Moonlock’s research, the darcula platform still requires users to have some technological knowledge. Additionally, while the platform offers video tutorials and capabilities such as automated messaging templates, it is entirely in Chinese. This makes the platform very user-friendly for Chinese-speaking criminals but creates a translation nightmare for bad actors who do not know the Chinese language.
Moonlock analyzed several tutorials offered by the creator of darcula through its still active Telegram channel and found that while following the steps in their guides is possible, knowledge of messaging, domain building, coding, and programming languages is necessary.
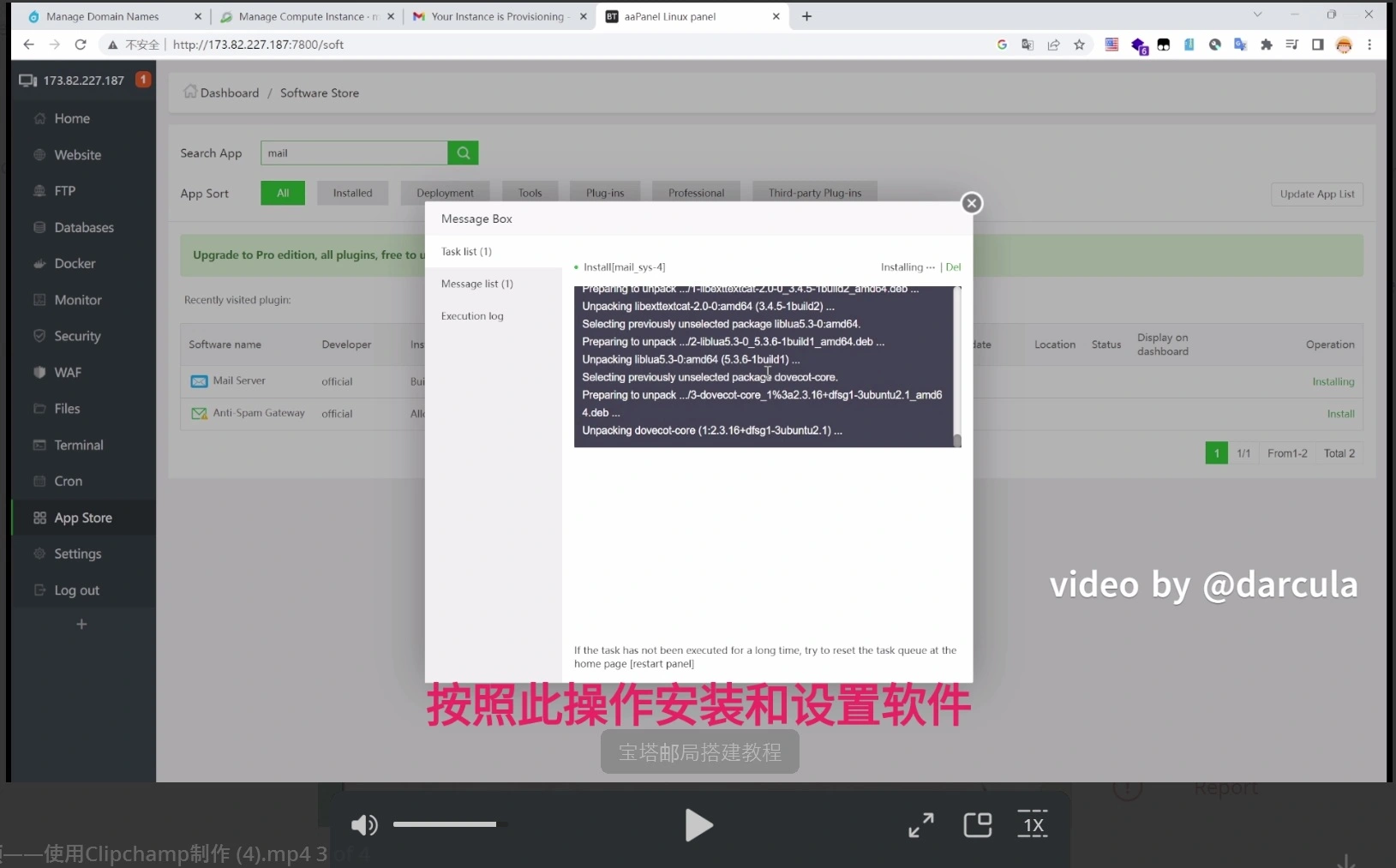
The darcula platform technology is associated with high-tech startups, including JavaScript, React, Docker, and Harbor.
Netcraft reported that the darcula setup is designed to “be easy for the fraudster” and uses the open-source container registry Harbor to host Docker images of phishing websites written in React.
The darcula price list
The process to create a phishing campaign on darcula is relatively straightforward. Criminals select a brand to target, then run a setup script that installs the phishing website specific to that brand and the associated admin panel in Docker. The darcula platform also offers support.
According to research from Oshri Kalfon, an automation engineer and security researcher who managed to access the darcula admin platform using default admin credentials, prices on darcula start at $11.13 per week for the common source code.
Prices listed by Kalfon were converted assuming that the prices that darcula lists are in Chinese Yuan (approximately 0.14 USD):
- Common source code: 249u/month, 80u/week ($34.66/month, $11.13/week)
- Synchronized source code: 288u/month, 88u/week ($40.08/month, $12.25/week)
- E-commerce source code: 500u/month ($69.59/month)
- Switch source code: Free
- Normal: 388u ($54.00)
- Sync: 588u ($81.84)
- E-commerce: 888u ($123.59)
- Sending script: 188u, upgrade 100u ($26.17, $13.92)
How darcula is different: The use of iMessage to target Apple users
Researchers found that criminals who use darcula distribute fake landing page URLs using RCS and iMessage. This stands out from traditional phishing attacks that use standard SMS-based messages.
Not only are these types of messages free to send, but they are designed to target Apple iPhone users who trust in the security of iMessage. Additionally, by using iMessage, the hackers evade detection and bypass scam and spam SMS messaging security controls.
It can only be assumed that darcula is set up as an international operation, as the malicious platform offers more than 200 phishing templates to impersonate organizations and brands in more than 100 different countries.
The darcula templates include fake content to impersonate organizations that have already established a high level of trust among the population, such as:
- Postal services
- Public and private utilities
- Financial institutions
- Government bodies (tax departments, etc.)
- Airlines
- Telecommunication organizations
The iMessages from darcula also trick users into replying to their first message. This is a way to bypass an Apple security control that forbids iPhone users from clicking on a link on an iMessage unless they have already engaged with that user.
How to stay safe from darcula
While darcula can target Apple and Android devices alike, iPhone users are specifically vulnerable due to the platform’s exploitation of iMessage.
To stay safe, it’s a good idea to look for red flags and warnings such as:
- Suspicious iMessages: Be wary of unsolicited iMessages, especially those urging you to click on links.
- Unfamiliar senders: Do not reply to messages from unknown contacts or numbers.
- Impersonation attempts: If a message appears to be from a trusted organization like your bank or utility company but something feels off, contact the company directly through a verified phone number or website (not through any links in the message).
- Urgent tone: Phishing messages often try to create a sense of urgency to pressure you into clicking a link.
- Misspelled words and grammatical errors: Phishing messages may be more likely to contain typos or mistakes in grammar, especially if the content has been translated from other languages.
How to protect yourself from phishing attacks
Follow these essential security tips to stay one step ahead of phishing attacks:
- Never click on links from unknown senders: This is the golden rule when it comes to avoiding phishing attacks.
- Verify sender identity: If you’re unsure about a message’s legitimacy, contact the sender through a trusted channel.
- Enable 2-factor authentication: 2-factor authentication (2FA) adds an extra layer of security to your accounts. This makes it harder for hackers to gain access to your account even if they steal your password.
- Update your iPhone regularly: Keeping your iPhone software up to date ensures you have the latest security patches.
- Report phishing: If you receive a suspicious iMessage, report it to Apple so they can take action.
Remember to never ignore browser warnings. You might also consider using a security app that can help identify and block phishing attempts.
By following these steps and remaining vigilant, iPhone users can significantly reduce their risk of falling victim to darcula phishing attacks.






