High-profile news announcements are constantly used by online scammers to steal crypto, empty bank accounts, and steal personal data. So, when Elon Musk announced that SpaceX would launch a Starship Mission to Mars crewed by Tesla’s Optimus robot, cybercriminals saw an opportunity.
As a result, a multitude of fake Tesla Optimus robot preorder sites have popped up online.
Founder of the Internet Storm Center sounds the alarm on fake Tesla Optimus scam
On August 10, Dr. Johannes Ullrich, Dean of Research for SANS Technology Institute and founder of the Internet Storm Center, reported that scammers are abusing Google Ads to drive traffic to fake Tesla Optimus presale sites.
This technique is not new. Known as malvertising, cybercriminals often abuse the Google Ads platform because it is an effective way of reaching large audiences.
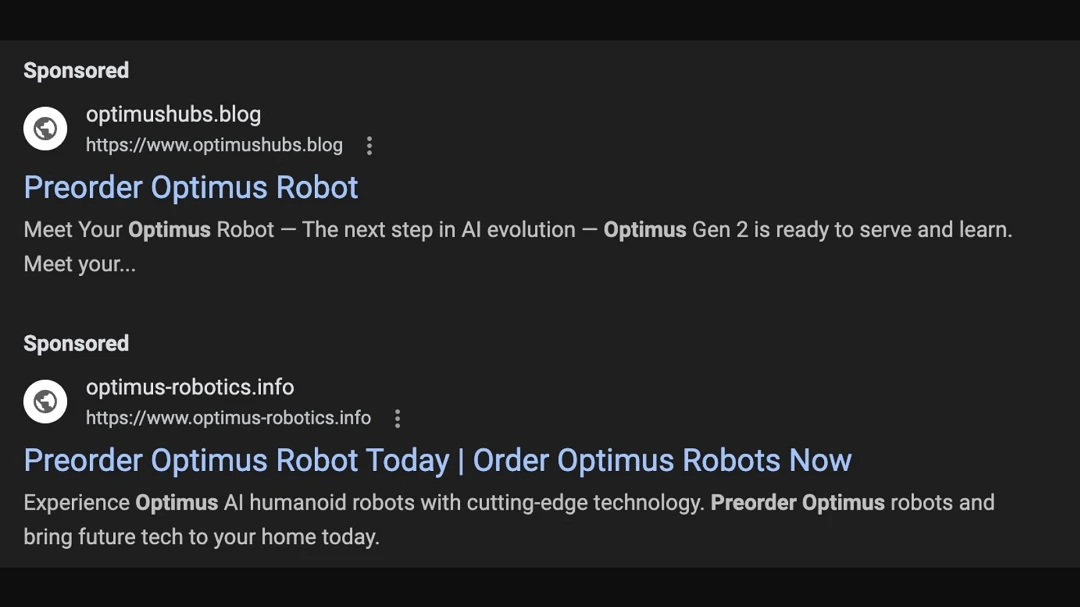
Dr. Ullrich searched online for “Optimus Tesla preorder” and found 2 sponsored ads for the new robot — listed above the official Tesla site. To date, Tesla does not offer an official preorder option for the humanoid robot. These sites, however, do.
Distribution: Scammers abuse the Google Ads platform (again) and lure organic traffic with keywords
Dr. Ullrich shared a screenshot of the malicious ads that bypassed Google Ads’ security policy (once again).
We checked to see if those ads were still running or if any fake ads had appeared on Google Search related to Optimus. We could not replicate the results that Dr. Ullrich had found. Nor did we find other malicious ads. However, this does not mean that new ads won’t emerge.
Most likely, the scammers who were running these ads discontinued them when the report from Dr. Ullrich was made public. Another possibility is that Google Ads, which plays catch-up and is in a constant game of “Whac-A-Mole” with these kinds of threats, shut down the ads for policy violations.
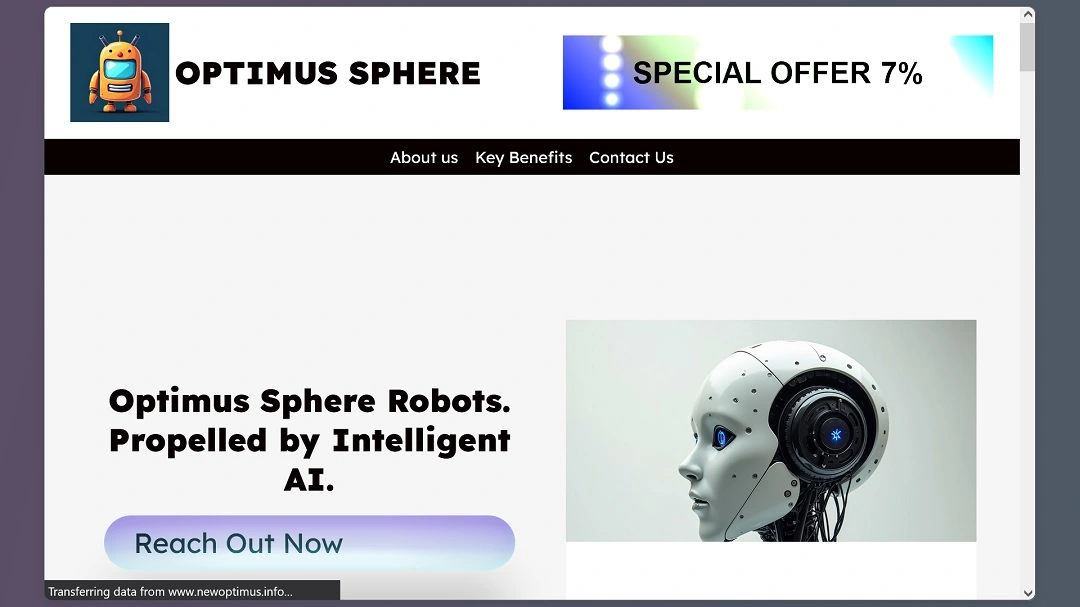
We checked out the fake websites that Dr. Ullrich identified in his investigation and can corroborate that the sites are indeed fake impersonation sites or suspicious at best. Some are active, while others are no longer available. Several seem to have changed and have deactivated functions and elements, such as contact buttons.
The technical details
Going deeper into the issue, we also found several other sites that are not listed in Dr. Ullrich’s investigation. The other fake Optimus sites use the same overall concept, the same text, and the same technique to lure users. They also have some technical traits in common, such as hosting, DNS, and red flags (more on this in the following sections).
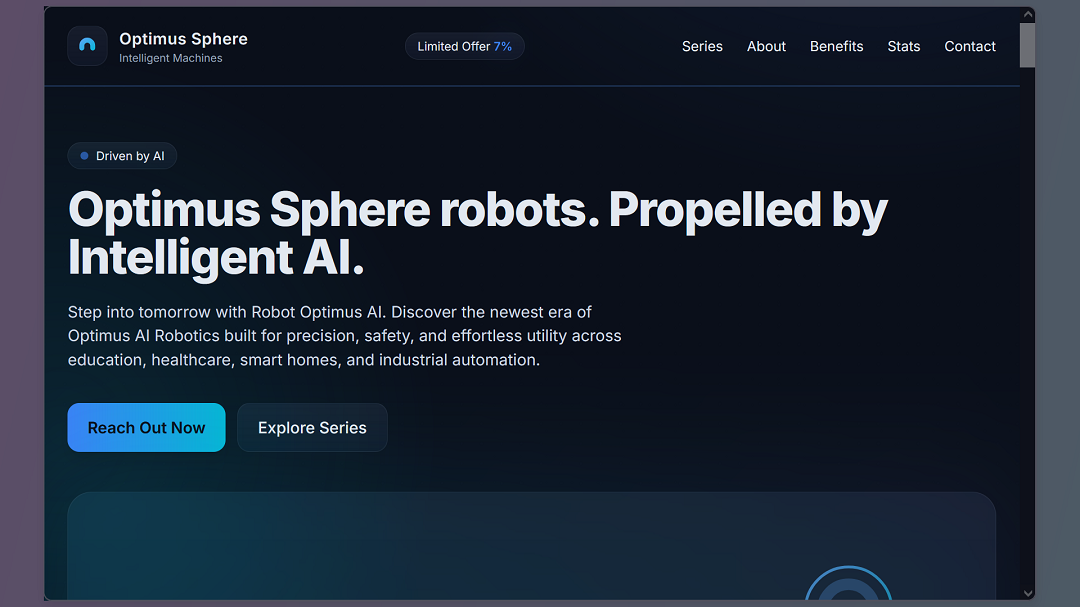
When examining the source code of www.optimushubs[.]blog, one of the sites that Dr. Ullrich discovered, we found that the site had been SEO-optimized to rank in organic search engines using keywords. The threat actor(s) used keywords including “Optimus pre-order,” “reserve humanoid robot,” and “robotic launch system,” as the image below shows.
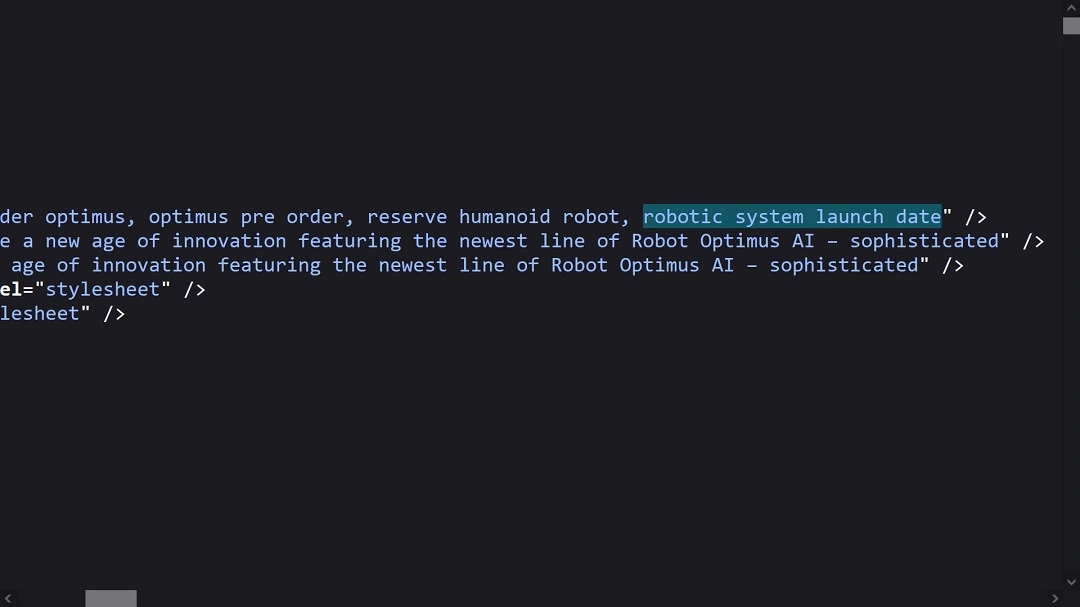
Cybercriminals’ use of keywords that align with news announcements made by public figures like Musk is intended to divert organic traffic to scam websites. The keywords “robotic launch system,” for example, attempt to take a bite out of the global traffic generated by users who are going online after Musk announced that the 2026 Starship mission to Mars, crewed by Optimus.
What do the fake Optimus preorder scammers want?
The goal of this campaign is probably phishing. Cybercriminals use generic website designs to lure victims into clicking on the “preorder” button.
As far as we can tell, there are no credit card forms on these sites. The preorder button leads victims to a “contact us” form, which we found was no longer functional in most cases but appeared to have once been active.
Dr. Ullrich did find a fake Tesla site with active preorder credit card forms, but after testing them, he noted that they appeared not to be working either.
It is likely that there are several fake Tesla Optimus preorder sites active in the wild; some may be promoted via ads. Others could be getting pushed via social media and other channels.
Looking into the domains that Dr. Ullrich identified, most of these sites would instantly raise a red flag to any user. These sites are poorly designed and are noticeably low-quality. However, during our research, we found other URLs using the same text and overall idea for the scam campaign. These appear more carefully crafted, resembling more professional webpages, resulting in a higher chance of tricking victims.
Given that there are several of these sites online, we can conclude that whoever is behind this new Musk-impersonation campaign is using automated dev tools, AI, automated web creation, and hosting tools to scale their reach.
Some indicators of compromise: Sites to stay away from
Dr. Ullrich identified the following suspicious and fake Tesla Optimus sites:
- optimushubs[.]blog
- optimus-robotics[.]info
- offers-tesla[.]com
- exclusive-tesla[.]com
- prelaunch-tesla[.]com
- private-tesla[.]com
- corp-tesla[.]com
- www-tesla[.]com
- hyper-tesla[.]com
- auth.cp-tesla[.]com
Additionally, we found several more, which we believe to be more dangerous because they are more professionally crafted. Here are 2 examples:
- newoptimus[.]info
- Gen-robotics[.]info
Shady phishing contact forms, Cloudflare hosting for obfuscation, and fake credit card forms
Evidently, the threat actors behind this campaign are more skilled at web development, content farms, and marketing than they are at malware and cybersecurity.
Inspections of the resources found on these sites show no malicious code running in the background, no shady JavaScript, and no links to malware downloads or other more dangerous elements. As previously mentioned, some of the elements of the page, such as the “Send” option in the contact forms, were either deactivated or never worked in the first place.
All of the sites in question, those identified by Dr. Ullritch and those discovered in our follow-up research, use Cloudflare for hosting and DNS to manage the domains. Cloudflare hosting is often used by cybercriminals because it allows them to obfuscate their identities and IPs, preventing cybersecurity researchers from conducting proper attribution.
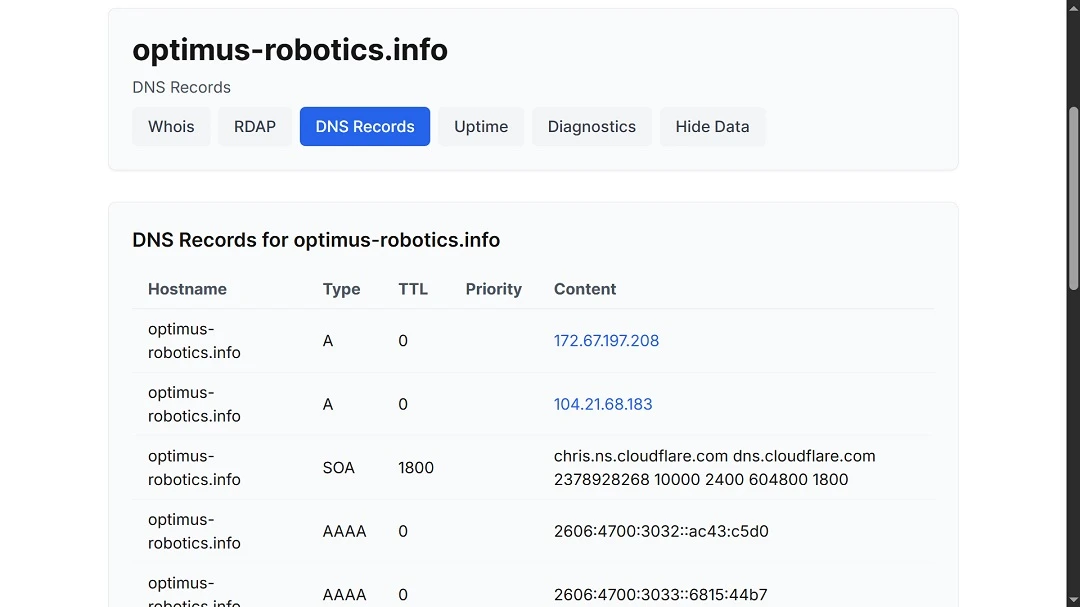
It is possible that these sites once had, or will have in the future, malicious credit card forms.
The contact form used by these sites asked victims for their name, email, and phone number. The level of data extraction isn’t very high. However, we do not know how many victims have filled out those forms, and what happened to their data once the forms were filled in. The data could have been sold or used for further scams, such as email phishing, identity theft, financial fraud, and cyberattacks.
Amateur opportunistic scammers or sophisticated hackers?
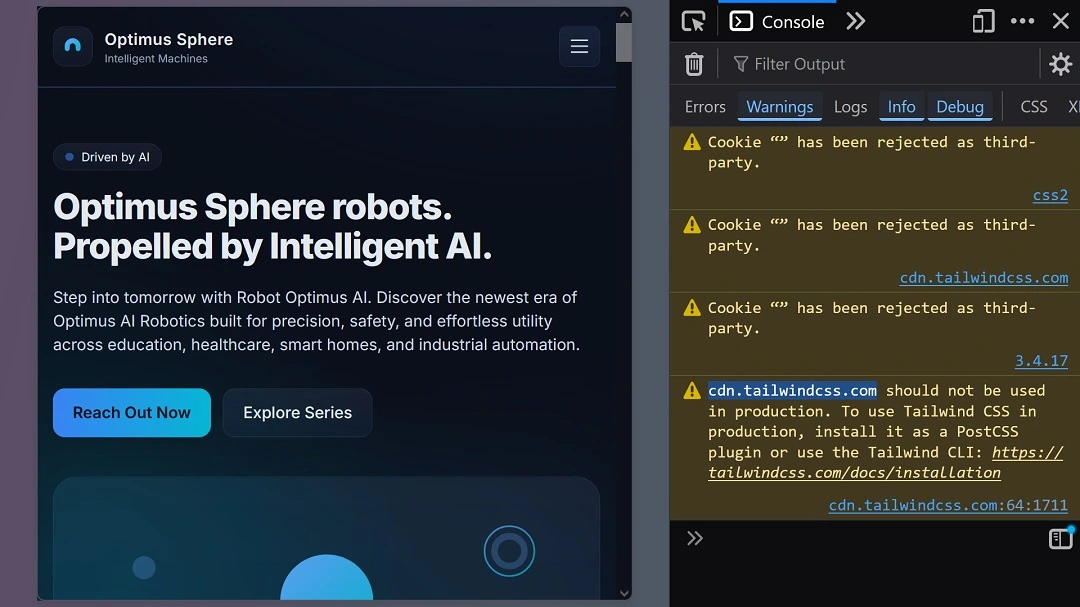
Other notable findings include the incorrect use of cdn.tailwinds.com.
Tailwind’s CDN is a version of the Tailwind design framework delivered through an edge network. Using this framework, web designers can load styling tools from servers that are close to the user who visits these websites. This type of edge infrastructure is commonly used around the world to enable webpages to load faster. But they come with a problem.
In theory, abusing Tailwind’s CDN would allow black hat hackers to load malicious code onto a site or modify elements in real time. In 2023, Moonlock found that cybercriminals were using Discord’s own CDN edge network to distribute the Lumma Stealer.
As seen in the image below, in the Optimus preorder scam, those behind the scam were either meddling with Tailwind’s edge infrastructure and servers or simply did not know how to use Tailwind CSS.
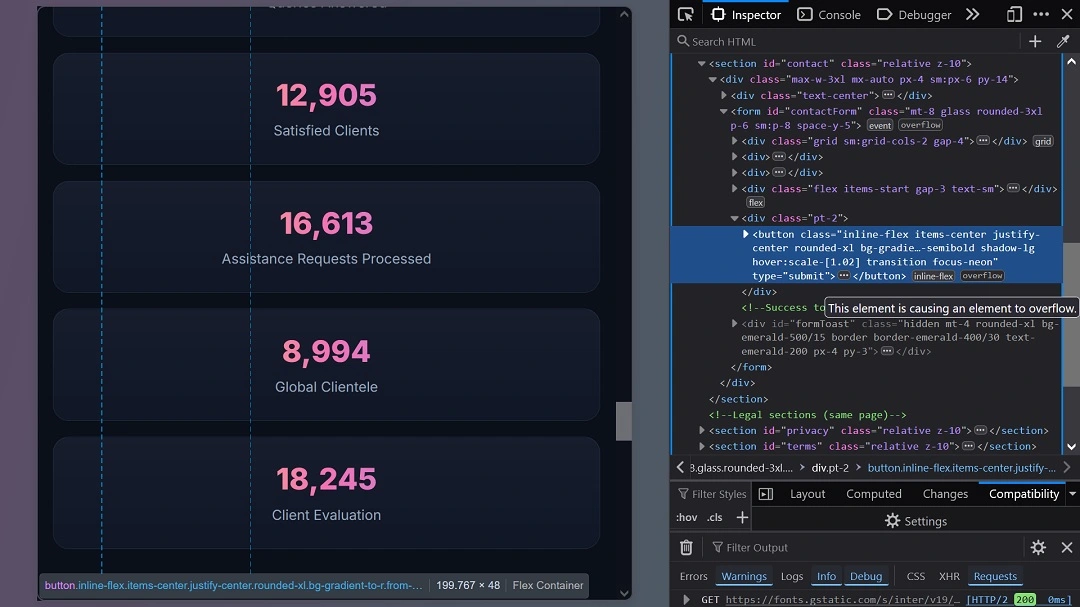
We also found, on the most professionally-looking sites, Stack Overflow warnings, shown in the image below.
Low-quality web design and unconvincing sites
Cybercriminals often leverage Stack Overflow vulnerabilities to overload the assigned memory and gain access to device resources to run scripts, load malicious payloads, crash systems, or bypass security checks.
However, in this case, given the low-quality level of web design impersonation used by the threat actors, the red flags may simply be caused by amateur-level knowledge of the hackers.
As mentioned, because most of these sites are not very convincing and, as far as we can tell, are distributing no malware, we conclude that the threat actor(s) are low-level online scammers who are skilled with web tools.
Our tips and advice to stay safe from these types of scams
To keep away from these kinds of online scams — which are likely to remerge every time a high-level public figure makes an announcement — we advise users not to click on Google Ads. Always double-check URLs and be extra cautious with preorders, credit cards, or other types of data entered into forms.
If you do find anything interesting on Google Ads, instead of clicking it, try searching for the official, verified channel of the sponsor. Then, engage with the product or service they are selling through their legitimate website.
You can also:
- Check for misspellings or extra characters in website URLs, which often indicate fake sites.
- Look for HTTPS and a valid security certificate before entering any personal or payment information.
- Avoid deals or offers that sound “too good to be true,” especially those tied to sudden news events.
- Verify company legitimacy by cross-referencing multiple trusted sources before engaging.
- Use browser security tools or ad blockers that flag or block known malicious ad networks.
Remember that scammers are constantly looking for announcements made by famous public figures to craft their impersonation scams.
Final thoughts
As mentioned, this is not the first time threat actors have leveraged announcements made by famous people and spread by global media, nor will it be the last.
By using this technique, scammers can cast a wide, global net to lure in victims in great numbers. Remember, if it’s a giveaway, a preorder, a crypto scheme, or anything linked to the current news cycle, think twice to make sure that you aren’t being scammed.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Google LLC. Google Ads is a trademark of Google LLC.






