Cyble Research and Intelligence Labs (CRIL) has recently discovered a new malicious campaign that uses DarkTortilla, a complex .Net-based malware. It has been active since 2015 and specializes in delivering stealer malware and remote access trojans (RAT), such as AgentTesla, AsyncRAT, and NanoCore.
How does DarkTortilla spread?
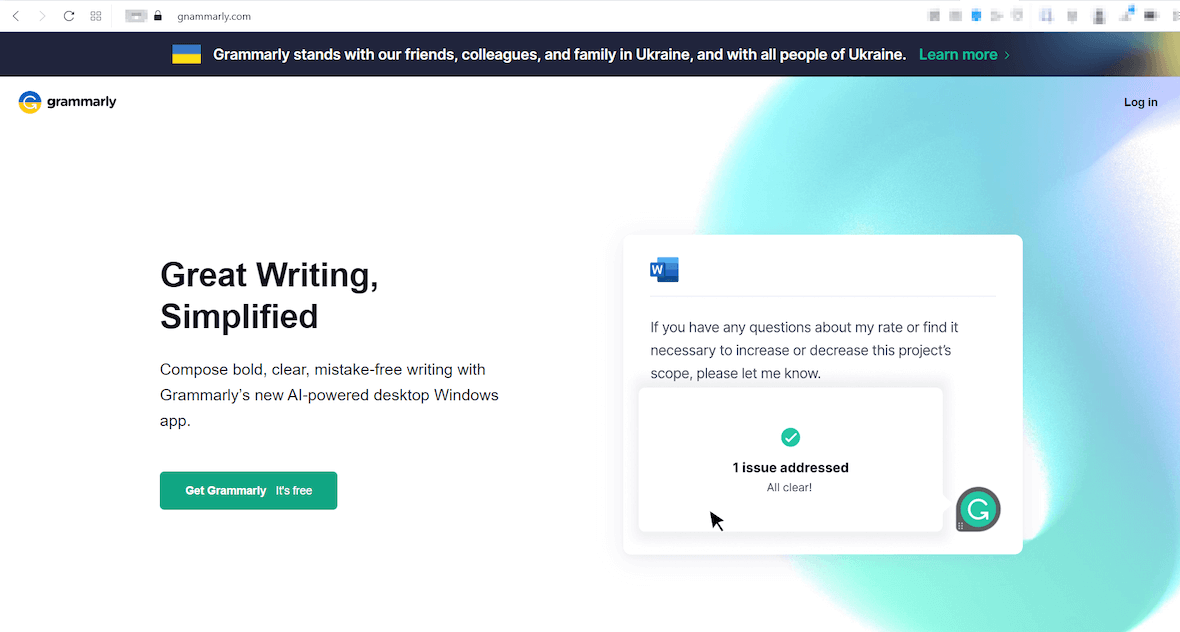
The primary method used by hackers to deliver DarkTortilla has been phishing emails. However, the recent malware campaign uses phishing websites masked as Grammarly and Cisco sites. Attackers created numerous fake websites by misspelling legitimate domain names to trick unaware users into trusting and downloading the malware. An example of a phishing website used for this purpose is https://gnammarly.com. When you click on “Get Grammarly” button, the spoofed Grammarly website will download a malicious file named GnammanlyInstaller.zip containing the malware.
What makes DarkTortilla especially dangerous is its robust design. It uses advanced anti-analysis and anti-tamper controls that make detecting and analyzing its source code challenging. This allows the malware to remain hidden in infected systems for a long time and be later used to download other types of payloads into compromised systems, such as:
- Cobalt Strike
- Metasploit
- Benign decoy documents
- Executables
According to Cyble researchers, the files downloaded from the phishing sites use different infection techniques. This shows the ability of the attackers to customize their malware source code according to their needs.
It is worth noting that DarkTortilla is used as the first attack phase to introduce more malware into the target system. For instance, hackers have used DarkTortilla to deliver different types of malware such as Remcos, BitRat, WarzoneRat, Snake Keylogger and LokiBot.
How to protect yourself from DarkTortilla
There are several security measures end users can follow to avoid DarkTortilla and similar malware. Below is a list of the main ones.
- Pay close attention to the domains you visit. Make sure the domain address is correct before you take any action on a website.
- Do not download software or other executable files from unfamiliar websites.
- Do not click on links in emails received from strangers. The same is true for email attachments: avoid downloading email attachments from unknown senders.
- Do not click on pop-up windows that randomly appear on a website. Reputable websites have stopped using this marketing method to attract visitors, but it’s still widely used by cybercriminals to guide unaware users to download malware or go to malicious destinations.
- Do not attach unknown USB devices to your computer.
- Use a reputable antivirus app and make sure to keep it current.
- Use a non-administrator account when browsing the internet or doing regular work that does not require administrator privileges.
- Keep your operating system and all installed applications up to date.
Hackers are always pursuing new techniques to develop malware that evades detection by modern security software. DarkTortilla is one of the threats that use advanced techniques to evade detection and is used as the first attack phase to introduce other malware into the target system. The aim is to steal confidential information and use it to conduct more attacks.
For end users, following the steps above should be enough to avoid falling victim to malware attacks. Cybersecurity awareness is also essential, so be sure to regularly check this Emerging Threats column to stay informed.