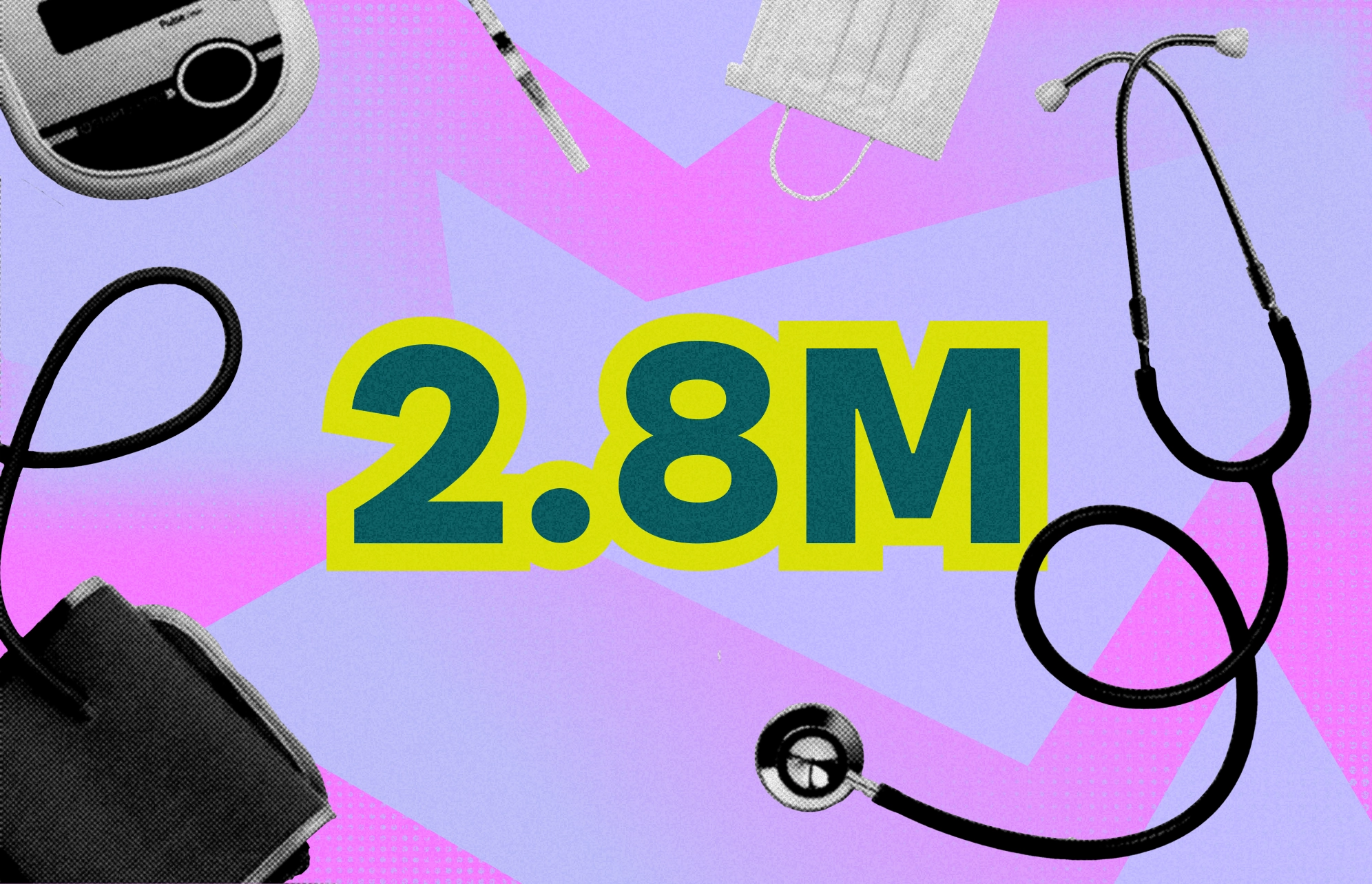
Cybercriminal operations have relentlessly hit the American healthcare sector this year. Often linked to Russian-state-supported groups and hacktivists, these attacks have continued to intensify. And a new cyberattack targeting the US healthcare sector managed to get away with personal data from 2.8 million Americans.
From diverting ambulances and shutting down emergency care services to the Change Healthcare ransomware attack that caused nationwide prescription delays, cybercriminals are going after health providers due to the potential for disruption. When such attacks are over, the aftermath often reveals vast personal patient data leaks.
Recently, the US pharmacy benefit manager (PBM) Sav-Rx, which provides essential health services for more than 10 million American workers and their families, warned users that an October 2023 breach resulted in data from 2.8 million patients being exposed.
Sav-Rx warns users that their personal data was exposed
It took Sav-Rx about 8 months to send out notices of breach to impacted customers. When those affected finally got letters from the company, they learned that their full names, dates of birth, social security numbers, email addresses, home addresses, phone numbers, insurance IDs, and eligibility data had been successfully exfiltrated by the attackers.
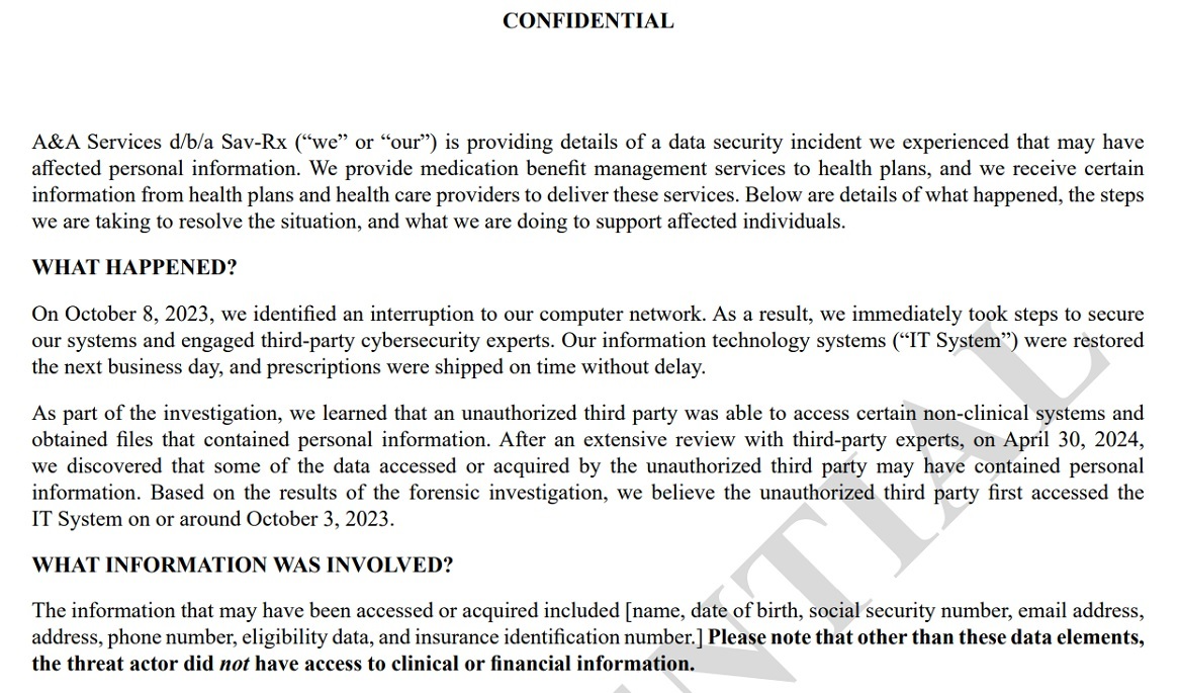
While the company did not provide details of the type of cyberattack that impacted its operations, it reassured the public that no financial or personal health history data was breached.
The incident did not affect the company’s pharmacy systems or mail-order pharmacy services.
Sav-Rx and the “Big 3” American pharmacy benefit managers
The Big 3 American PBMs (CVS Caremark, Cigna-Evernorth-Express Scripts, and UnitedHealth-OptumRx) hold about 80% of the PBM share. Sav-Rx, however, operates differently.
Sav-Rx doesn’t control a significant portion of the market, but it does play a vital role in managing prescription drugs that benefit millions of union workers and their families in the US.
The company prioritizes the interests of plan sponsors (employers/unions) and members (employees) working in its own niche. Its day-to-day operations have a major impact on the healthcare of American workers thanks to its union connections.
Why Sav-Rx took so long to notify customers
In the company’s FAQ page, Sav-Rx explains that they launched a full investigation with the support of third-party cybersecurity experts after the October 23 security incident. The main focus of the investigation was to determine the number and identities of affected individuals. It also aimed to uncover what “elements of each individual’s personal information” were exposed.
The company responded to concerns about the delay between breach and notification. “We prioritized this technological investigation to be able to provide affected individuals with as much accurate information as possible,” Sav-Rx said. “We received the results of that investigation on April 30, 2024, and we promptly sent notifications to our health plan customers whose participant data was affected within 48 hours.”
Breached pharmacy benefit manager offers credit monitoring to those affected
In the notification letter sent to those affected, Sav-Rx offered individuals complimentary access to 24 months of credit monitoring and identity theft restoration services through Equifax.
The company also recommended that breached individuals remain vigilant for any sign or suspicious activity that could result from incidents of fraud and identity theft, including reviewing account statements and monitoring free credit reports.
Affected customers who notice suspicious activity should report it to their bank or financial institutions, as well as authorities such as state attorneys general and the Federal Trade Commission (FTC). Individuals also have the right to obtain a police report.
Data breaches at an all-time high in 2024
2024 is already proving to be the year of data breaches. In January 2024, cybersecurity experts named one breach “The Mother of All Breaches,” as new breached and exfiltrated data leak hit the dark web. The breach offered a shocking 26 billion records of personal information.
Cybersecurity experts have confirmed that a significant portion of the data of this breach was compiled from previous data leaks. Nevertheless, the list also included new data.
This breach set the tone for cybercriminals. Bad actors are increasing their monetization efforts by selling byproducts of their attacks. Breach data leak lists on the dark web can be sold over and over, in bulk, by criminals. Such data can be used to pressure companies into paying ransoms. It can also be leveraged to carry out more attacks.
Additionally, stolen databases can be used for phishing. When leaks include credentials (usernames and passwords), they drive file-less attacks. These are incredibly difficult to detect, as the criminals pose as users with legitimate access.
In December 2023, an Apple-commissioned study found that threats to consumer data stored in the cloud have grown dramatically. A staggering 2.6 billion personal records were compromised by data breaches in the past 2 years.
Apple explains that the number of data breaches has more than tripled between 2013 and 2022.
What can users do to protect their data?
As threats to personal data increase, companies are urged to deploy more robust cybersecurity and privacy measures. These include cloud security and end-to-end encryption, data encryption, and advanced protections.
The harsh reality for the average user is that they are at risk even when observing cybersecurity best practices. Using a strong and unique password, enabling MFA or biometrics, and even using authentication apps or passkeys are no longer enough to protect their data. Cybercriminals are determined to spend time and resources to get their hands on personal data. And they don’t have to go inbox to inbox to do so. Instead, they just breach companies that have large customer bases.
Data leaks can also be a sign of a bigger plan in motion. For example, attackers might be going after a larger organization linked to the supply chain of Sav-Rx or its partners.
Final thoughts
Sav-Rx explains that only those who received a notification letter have had their data exposed by the security incident.
If you think you have been the victim of this breach or other leaks, check sites like Have I Been Pwned. Through a simple search, you can learn whether your data is already out there on the dark web.
Changing the passwords of all accounts, enabling MFA, and staying vigilant are vital next steps for anyone directly or indirectly involved. We expect that personal data breach lists will continue to emerge, with more intensity and more potential damage throughout 2024.