There are so many terms used in cybersecurity that it’s sometimes hard to keep them all straight. Most people have heard about “exploits,” but some of us may not fully understand what they are and how they work.
An exploit is not malware. Rather, it is a process used to distribute malware or ransomware. It may also be part of a larger attack plan. Keep reading to learn all about these online dangers.
How do you define an exploit in cybersecurity?
An exploit is a piece of code or a program that takes advantage of existing vulnerabilities within a system, hardware, software, or application.
Hackers spend a good deal of time looking for vulnerabilities to exploit. Once identified, they often share this information with other attackers to spread the damage.

What is an exploit attack?
When a bad actor uses one of the vulnerabilities explained above, such as an insecurity in a program or app, to infiltrate a computer, device, or network, it’s known as an exploit attack.
Attacks like these are sometimes performed in steps. First, the attacker might test the waters to see if they can get in. The next step may be to install malware. Later, that malware may be used to steal data or take files hostage for ransom.
Make sure your Mac settings are tight
Is a vulnerability the same as an exploit?
No. A vulnerability is a weak spot in the software program or hardware that allows the bad actor to get in. An exploit is the method the hacker uses to take advantage of the vulnerability to launch an attack. The vulnerability supplies the opportunity; the exploit is the execution of the attack.
What is a zero-day exploit?
The term “zero-day exploit” refers to a situation when hackers learn of a vulnerability before the developer is made aware of it. Thus, the developer has “zero” days to fix it.
Simply put, a zero-day exploit occurs before a developer can fix the vulnerability. Companies often scramble to fix zero-day vulnerabilities before more attackers learn of it. Unfortunately, however, these attacks are often reported in the media, making it nearly impossible to fix them before additional users become victims.
Are zero-day exploits rare?
Although thousands of software and hardware vulnerabilities exist at any given time, zero-day exploits are relatively rare compared to other types of attacks. Zero-day vulnerabilities are difficult to detect, making it rare for them to be exploited.
What is the most famous zero-day exploit?
Among the many infamous zero-day exploits, there are 2 noteworthy examples that stand out above the rest.
3 billion Yahoo accounts seized
In 2013, roughly 3 billion user accounts were exploited due to a vulnerability within the Yahoo system. Unfortunately, cybercriminals were able to access personally identifiable information like users’ names, ages, phone numbers, and passwords. This data was sold on the dark web for $300,000.

92% of LinkedIn accounts exploited
In another famous zero-day exploit, 92% of all LinkedIn accounts were compromised in April 2021. Some of the information stolen included users’ names, phone numbers, email addresses, and job titles. The data was sold on the dark web and resulted in phishing attacks.
What is a drive-by exploit?
A drive-by exploit is an attack where malicious programs are installed on your device without your consent. You don’t have to click any links or install anything for it to happen. If you use a piece of software or a device with a zero-day vulnerability, all you have to do is open an app or visit an infected website.
These attacks aim to hijack your device, install malware to spy on you, or steal data. Sometimes, the goal is to destroy your device and render it unusable.
What is an example of a drive-by attack?
If you’re browsing the web and suddenly you see a pop-up saying you won a prize or offering you the chance to play a popular game for free, you’re just a few clicks away from falling victim to a drive-by cyberattack. All you have to do is accept the opportunity, and suddenly, a malicious program will be installed on your device.
What are the effects of drive-by exploit attacks?
Once the malware is installed on your computer or mobile device, that’s when the trouble begins. You may become a victim of identity theft. Or, if the hacker can access your bank accounts or other credentials, you could lose money or access to your online accounts. Your device could be damaged or suffer performance-wise. Or all your files could be lost or ransomed. Plus, any information the attackers steal could end up on the dark web.
What are your options for exploit protection?
Reading about all the potential dangers online makes it easy to feel discouraged. However, zero-day exploits are less common than other types of attacks, and you can take precautions to protect yourself. Some options for exploit protection include the following.
Update hardware/software
Always update your hardware and software when a new version becomes available. Many times, these updates include security patches to prevent exploits. Updates are issued regularly for macOS.
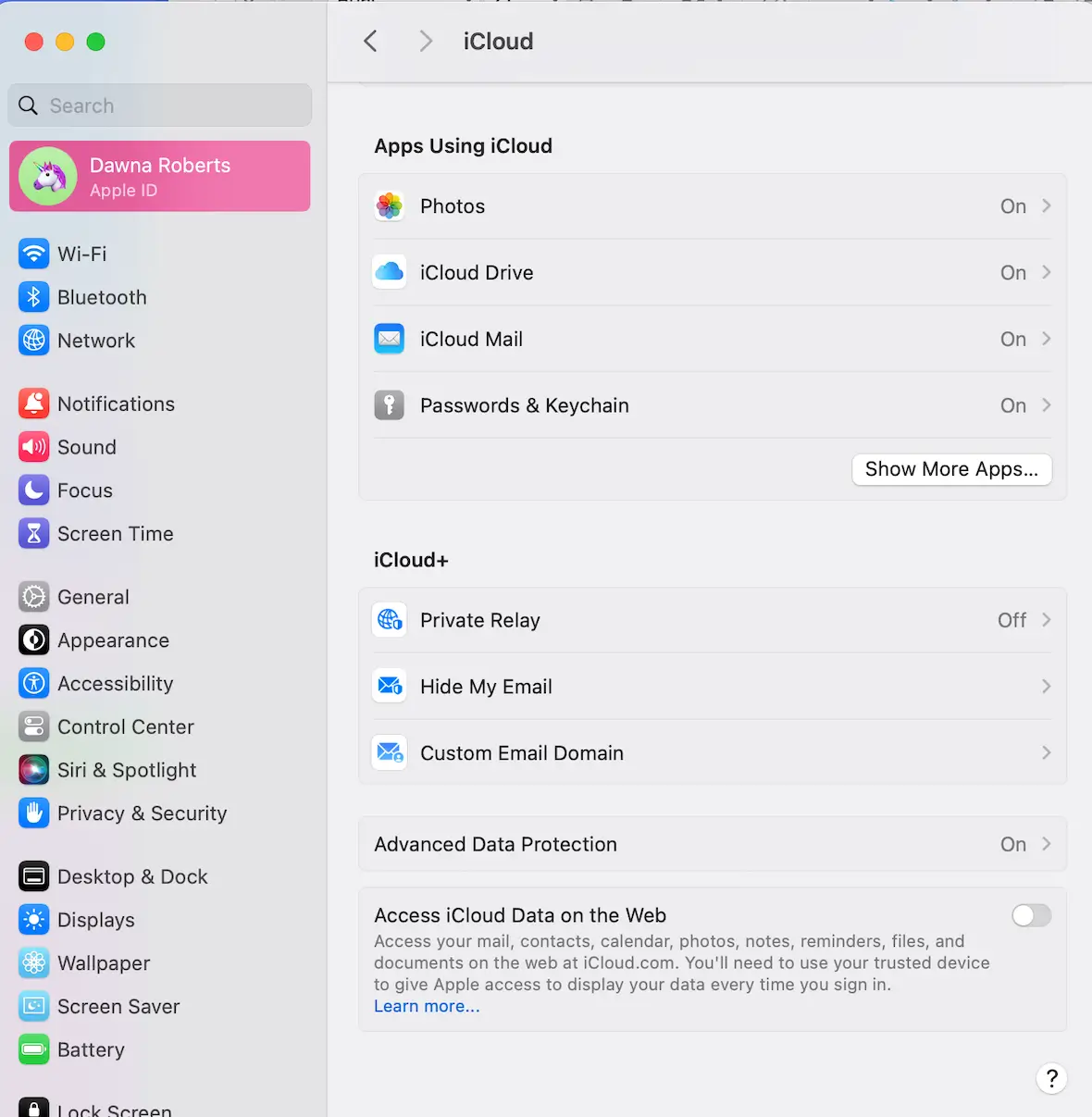
Use built-in macOS tools
With a Mac, you can encrypt your entire hard drive to protect your data against intrusions or theft. Turn on Advanced Data Protection in macOS System Settings to secure your data.
Only download safe apps
Never download or install third-party apps on your Mac. Only download verified programs from the App Store or a trusted software vendor.
Never click links
If you see pop-ups offering you something for free, clicking on them is dangerous. Links can lead to malware or worse, so don’t click on links in emails or texts. Instead, visit the site by manually typing in the address.
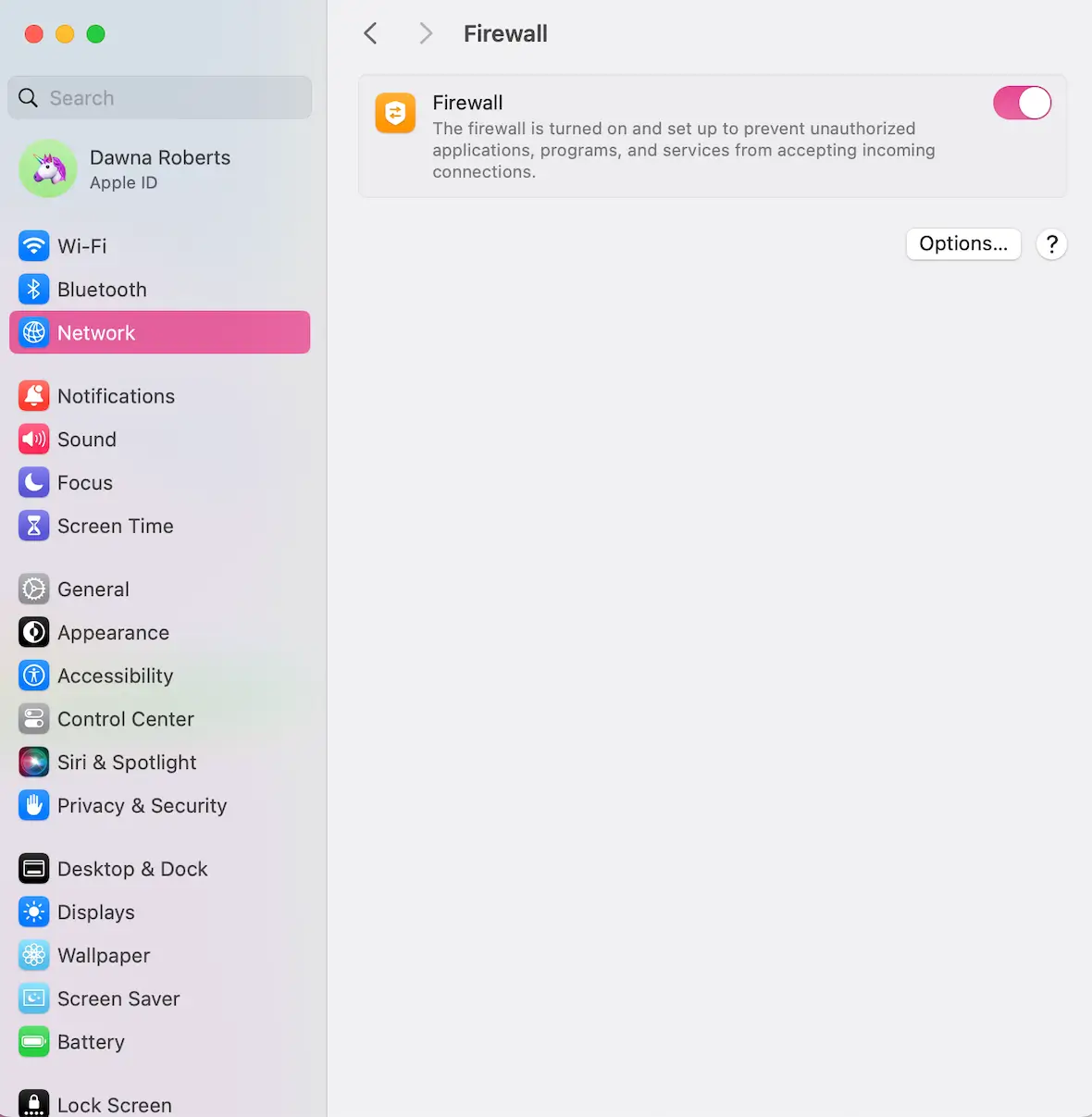
Turn on your firewall
Use a hardware or software firewall to add an additional layer of security against exploits. Most routers come with a firewall, and macOS includes a built-in firewall that you can configure in System Settings.
Educate yourself on cybersecurity
Finally, take the time to learn about cybersecurity best practices and err on the side of safety. If a tempting online offer seems too good to be true, it probably is. No deal is worth the risk of unwittingly downloading malware or ransomware on your Mac.
Exploits are just another one of the many online dangers that you need to be aware of and prepare for in order to keep yourself safe. Protect your hardware and your data, and you may avoid many hassles down the road.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac and macOS are trademarks of Apple Inc.